Welcome to this week’s Triage Thursday update blogpost! This week the following changes have been deployed to Triage:
- Added support for XLL files (Microsoft Excel Addins)
- Updated Emotet configuration extractor
- Implemented CPU emulation for BazarLoader
- Added support for x64 and ELF variants of SystemBC
- Updated public key extraction for Gozi RM3
- Minor updates to Vidar C2 dumping
- Updated Arkei configuration extractor
As always if you have any feedback on Triage or particular samples please do get in touch! You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account, or reach out to us using the contact form on our website to find out more about our commercial options.
Emotet
You’re probably already aware that Emotet remerged this week after a long absence, with a new and improved version being delivered in campaigns since Monday. If you’re not already aware, then thank you for taking the time to read our blog during your current spell on the ISS.
The first public announcement of the return appeared on Twitter from GData Analytics, reporting that the family was active again and being distributed by Trickbot.
The initial samples were referred to as Epoch 4, delivered via infected .docm, .xlsm, and encrypted ZIP archives.
Since then they have moved on to a new campaign, called Epoch 5 (based on the public key contained within samples), following the same methodology.
In terms of functionality the new variants are very similar to those used earlier in the year, prior to the family’s long hiatus. There are some minor modifications, such as the use of 2 distinct encryption keys in the communication protocols, but the overall flow is almost identical. We have analysed many of the samples available early this week and updated our configuration extractor to properly work with these new variants. Triage can now dump both encryption keys when available - ECS1 and ECK1 - and has been tweaked to account for other changes in the codebase.
We’d like to say a huge thank you to all those who sent us samples and feedback on Emotet as the news was breaking - your support was a great help in getting this turned around quickly.
Analyses:
- Search ‘family:emotet’
BazarLoader
We’re always looking for ways to improve our detection for major families like BazarLoader, and this week we are deploying a new approach leveraging our in-house CPU emulation to carry out static decryption/deobfuscation of the payload. This process was written up earlier this year by Jason Reaves of the Walmart Global Tech team, and you can find that blogpost here
If you haven’t come across our emulator before, we initially implemented it to handle things like Metasploit payloads but it can also be a useful tool in handling a wide range of other payloads, to circumvent techniques intended to make detection difficult. You can find writeups from the original release in our 2-part blog series on Metasploit here and here.
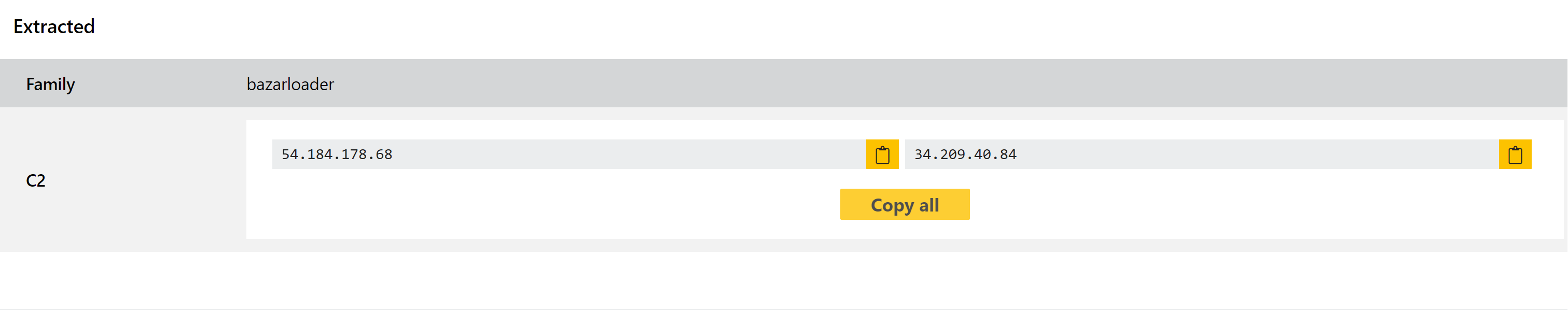
By taking this approach, we are able to directly access stored strings and accurately dump the C2 information.
Analyses:
SystemBC
The SystemBC RAT is often used as a loader stage for other threats - most recently being a common distribution method for ransomware. It provides a number of features useful to those looking to deploy their own payloads, including the secure download of remote files and a wide range of automated remote administration functions to access and exfiltrate data.
We added family detection in February 2021 and a configuration extractor in June, and this week we are giving some attention to its variants on other architectures and platforms. We have updated the configuration extractor to also work with ELF variants of the family (for Linux systems), and an x64 variant of the Windows payload which was reported to us.
At the request of the reporter we cannot share the samples of these we currently have, but if you have any samples that match these types then they should now be properly dumped by our extractor.
Gozi RM3
Back in June we made some changes to our handling of public keys dumped by our configuration extractor. However we’ve recently noticed that some versions are now getting incorrect values extracted, so we have revisited the family again this week to apply a fix to correct that for all the variants we have observed.
This should cover Gozi thoroughly but it is a very large family with a huge number of variants and forks, so if you notice anything not behaving as expected please do let us know. Of course we will also continue to keep an eye on the family ourselves to ensure we keep it up to date.
Analyses:
Vidar
Last week we deployed some updates to our Vidar handling to properly dump some new C2 services being used by recent samples. Since then we have observed some more variations on the C2 services in use, so have made some more changes to properly handle those. You can find examples below.
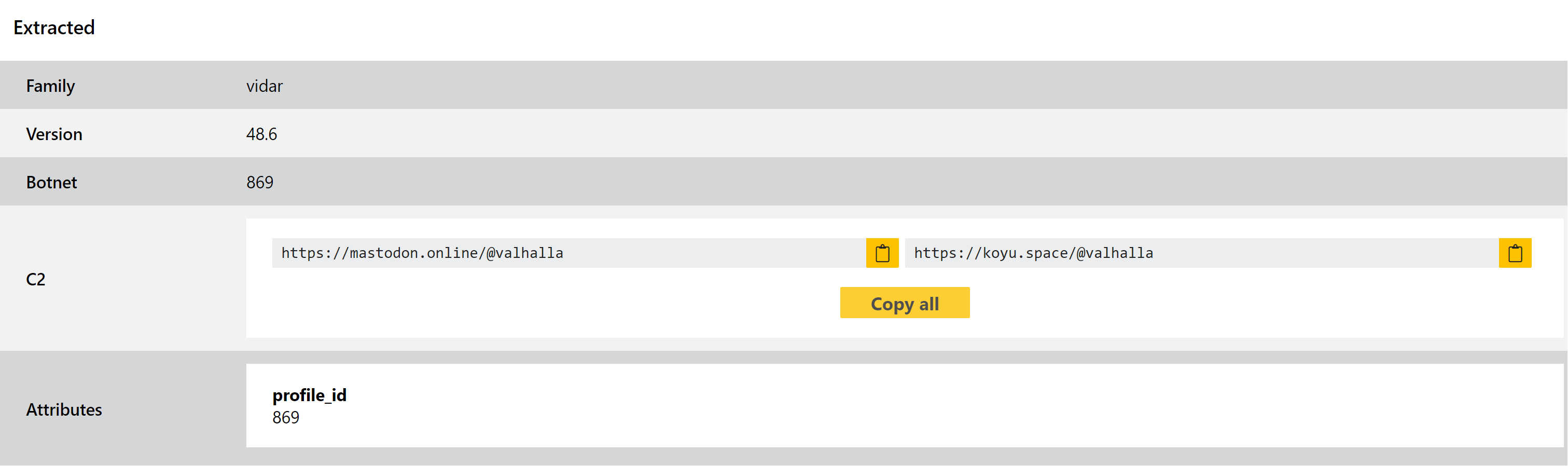
If you’re not familiar with the family and would like some background, you can check out our previous posts about the family last week and back in September.
Analyses:
Arkei
Arkei is the predecessor to Vidar, first gaining attention around mid-2018 distributed through compromised software packages available on Github. It has not become widely popular itself, but has led to several other families which have been extremely successful in their own rights.
The family is a fairly standard infostealer, focussing on extracting data from the infected filesystem like browser profiles (saved passwords etc.) and cryptocurrency wallets.
We added a configuration extractor for Arkei recently, and have revisited it this week to improve support for recent samples uploaded to Triage.
Analyses:
