Welcome back to another Triage Thursday blogpost! This week we have a collection of family tweaks and updates to introduce:
- Review of CobaltStrike
- Tweaked Gozi Configuration Extractor
- Updated CryptBot signatures
- Updated Ostap rules
- Updated SLoad signatures
- Updated Tinba signatures
We have also added detections for several new families that weren’t previously supported:
- HelloKitty Ransomware
- SystemBC
- Glupteba
- KPOT Stealer
- VjW0rm
- HiveRAT
- SectopRAT
- STRRAT
- BlackNET
- RunningRAT
If you have any comments, suggestions or other feedback about Triage feel free to get in touch with us. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
CobaltStrike Review
We have carried out an extensive review of CobaltStrike payloads in order to review our detections and add detail to the extracted IoCs. Some samples have also been incorrectly triggering Metasploit detections instead, and today’s updates also address this.
Alongside the family review, we have also created a new extractor for the family which can obtain the malware’s stager from the reflective DLL loader.
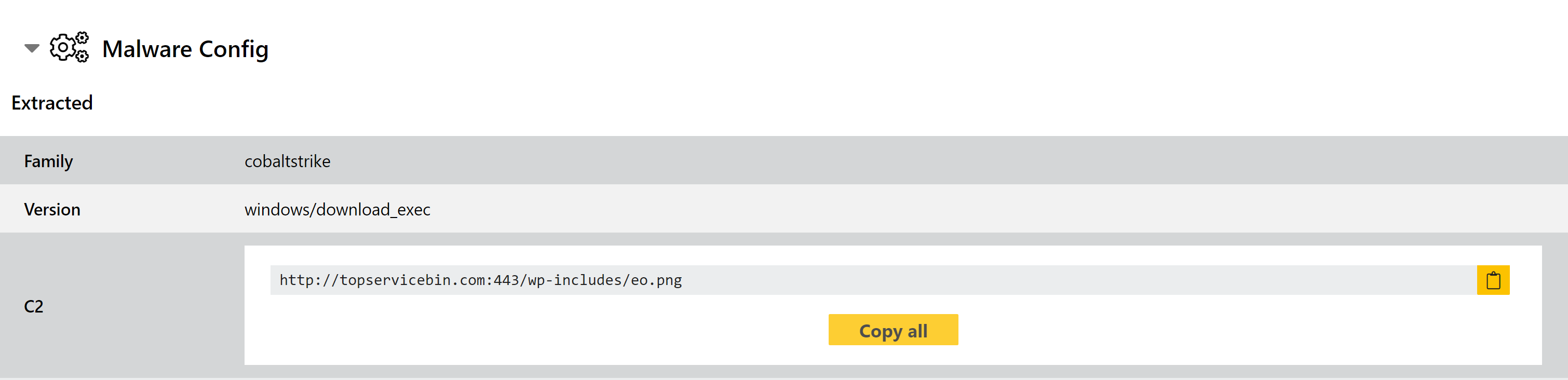
Analyses:
Updated CryptBot Signatures
CryptBot is an info-stealer which was first seen in the wild in early 2019, and has been active fairly constantly since then. It is often distributed bundled alongside legitimate software which acts as its lure, often affecting users who have downloaded cracked versions of common programs.
Signatures for the family were added to Triage early on, but over time it has accumulated minor changes and differences that have made those detections less reliable. We reviewed the family taking into account more recent samples, and have pushed updated detections.
Analyses:
Updated Gozi Configuration Extractor
We have covered some updates to Triage’s Gozi family detection and extractor in recent blogposts, and this week we have made some more minor changes to improve the information that is displayed.
The configuration extractor for Gozi RM3 will no include fields for the URL path of the main C2 server and the locale settings defined in the malware which will halt its execution if detected on the system. We have also add a server_id field for all Gozi variants, to aid with campaign/version tracking.
Analyses:
Updated Ostap Signatures
Ostap is a JavaScript downloader which has been around for several years. Triage has included family detection for some time, but based on recent submissions to Triage we have reviewed and updated it to better support the current versions.
Analyses:
Updated sLoad Signatures
sLoad is a loader family which has been used in campaigns since 2018. It came to prominence in 2020 after releasing a new and more effective version known as sLoad 2.0.
We introduced family signatures for the sLoad family back in September last year, but as usual changes have meant that these have become less effective over time. We have reviewed recent samples and updated our detections, and added static detection to act as a fallback if a sample does not run fully for any reason.
Analyses:
- 210111-63kw6gpz7j
- 201130-hvly2vhsjs
- 201123-tcqt2tttye
- 201123-m56x24578n
- 201123-74ry3th6la
- 201123-5h9cfn9wsn
Updated Tinba Signatures
The Tiny Banker Trojan, or Tinba for short, is a trojan targeting financial information which has been around since at least 2012. As the name suggests, initially it was designed to be as small and discreet as possible, although functionality has been added in the years since.
The source for Tinba was leaked around the time it was initially discovered by the anti-malware community, meaning that it has seen many new versions and spinoffs over the years and has stayed reasonably active. We have updated Triage’s detection for the family to take the recent variants into account.
Analyses:
Initial HelloKitty Ransomware Signatures
HelloKitty has been around since late 2020, having achieved its first publicly disclosed breach against a Brazilian power company in November. It recently rose to fame after reportedly compromising the large game studio CD Projekt Red this week.
We have obtained some older samples of the family and added initial family signatures to classify it correctly. We are currently looking at improving this with other detection methods to cover the modern versions, and will be keeping an eye on developments to ensure our detection stays up to date.
Analyses:
New SystemBC Family Signatures
SystemBC is a proxy malware and RAT which has been deployed on its own and in conjuction with other threats. It includes remote access features like file download and remote command execution, as well as secure C2 communications. Initial versions handled this via a SOCKS5 proxy, but this has since been replaced by use of the Tor network.
This week we have added detection for the family to Triage, including both behavioural signatures and static rules.
Analyses:
New Glupteba Family Signatures
Glupteba is a malicious remote access tool with a range of advanced capabilities to help it evade detection and target multiple different types of devices on a compromised network, including common routers and other Linux devices.
The family has been around for a long time, with initial reports going back to 2011. We have examined recent samples and implemented family detection for them, and will continue to update them if required by future changes.
Analyses:
New KPOT Stealer Family Signatures
KPOT is an infostealer which mainly targets locally stored credentials from things like web browser, email clients and instant messengers. It was first observed in September 2018, and in 2019 released a new version referred to as KPOT v2.0.
In late 2020 it was reported that the REvil ransomware group had bought the source code for KPOT at an auction held on hacking forums.
Analysis:
New VjW0rm Family Signatures
Vjw0rm is a worm which can infect removable storage devices which are connected to an infected system, using this as a mechanism to spread further. It also has remote access and infostealer capabilities, able to receive commands from a C2 server and harvest data from local applications.
The code for Vjw0rm is publicly available free of charge, meaning that it is extremely accessible and has seen widespread use since it was reported in 2019. The malware is modular, giving users a lot of flexibility in the type of attacks they carry out, ranging from acting as a zombie for DDoS attacks to more typical information stealing.
The fact that this worm is open source means that we will likely see many variants of it develop, but we have built Triage detections based on recently observed samples and will continue to update them as required.
New HiveRAT Family Signatures
HiveRAT is a remote admin tool and stealer which was reported in mid-2020 by @James_inthe_box on Twitter.
It includes common stealer behaviour, such as stealing stored browser credentials and targeting messaging clients like Discord.
We have reviewed samples observed on Triage and implemented family detection.
Analyses:
New SectopRAT Family Signatures
SectopRAT was first reported on Twitter back in November 2019 by @malwrhunterteam.
The RAT contains some unusual stealer tactics, including the ability to stream the system’s desktop to a remote server. Most notably though it also has the ability to create a 2nd desktop which is hidden from the system’s user, and is then able to launch and control web browsers through this session including disabling security restrictions.
The initial version was thought to be a testing build, as it did not include any particularly malicious behaviour besides basic profiling of an infected system. However in early 2020 a sample was observed which appears to be a new, weaponised, version of the family.
We have reviewed the available samples and implemented family detection for them.
Analyses:
New STRRAT Family Signatures
STRRAT is a family built in Java which acts as a stealer and remote backdoor. It was first reported in mid-2020, observed stealing credentials through direct file access and keylogging. It was also reported to include a fake ‘ransomware’ module, which added the .crimson extension to files - no actual encryption took place however.
Analyses:
New BlackNet Family Signatures
BlackNet RAT appeared in early 2020, exploiting CoronaVirus-based lures to encourage people to download and install the application. Once installed it has a wide array of stealer and trojan activities it can perform including DDoS attacks, capturing screenshots, stealing stored browser data and cryptocurrency wallets, and keylogging.
It has seen consistent updates since it’s initial discovery, with a report at the end of 2020 listing the current version as v3.7.
Analyses:
New RunningRAT Family Signatures
RunningRAT is an implant associated with the OlympicDestroyer campaign against the 2018 Winter Olympics in Pyeongchang. The core functionality of the RAT is reported to be keylogging, although it was also noted to contain code for additional functionality which did not appear to be in use.
