We’re back this week with another Triage Thursday blogpost, detailing all the major changes that have happened on the platform recently. We missed a blogpost last week meaning today we have a few more families than usual to go over, so let’s get right into it!
In the news today:
- Expanded detection to cover new Amadey version
- Added a new configuration extractor for Arkei stealer
- Added signatures for MetamorpherRAT
- Tweaked Qakbot configuration extractor to dump salt value
- Added detection for SakulaRAT family
- Updated Racoon configuration extractor
- Improved Danabot detection
- Added family classification for Colossus ransomware
- Updated Cryptbot detection/configuration extraction
As always, if you come across anything unexpected while using Triage please do send us feedback - it’s very valuable in letting us know what’s currently important to users. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Amadey Trojan
Amadey was first reported back in early 2019. It is a trojan/botnet which targets non-Russian users and is available for sale through online forums.
Infected machines are incorporated into a botnet which is then used for spam email campaigns and carrying out DDoS attacks. The family can also deploy additional payloads on a system - for example in May 2020 ZScaler reported that it was being used to push the Remcos RAT.
Earlier this year a new version was observed which has added some new features, including harvesting details from Microsoft Outlook and a piece of software called MikroTik Winbox - a GUI tool for administration of MikroTik routers and network devices. Cisco Talos also recently published a blogpost reporting that it has been seen dropping the ServHelper RAT in 2021, along with Raccoon.
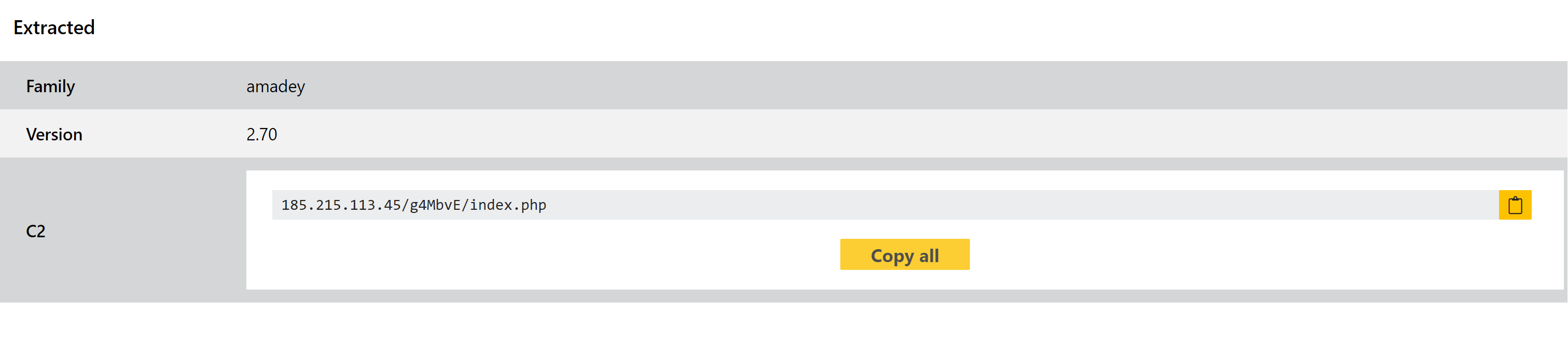
We have now reviewed these new versions and updated our detections and configuration extractor as necessary. Some examples of the variant are provided below.
Analyses:
Arkei Stealer
Although not hugely common on its own these days Arkei has led to multiple forks of the original project which have been quite successful in their own right, and the family itself is still regularly used in the wild. The Vidar and Baldr infostealer families were both developed from the source code of Arkei.
The family is a fairly standard infostealer, having first gained attention in mid-2018 embedded within legitimate software packages available on Github. It focuses on data stored on the local filesystem, exfiltrating browser information (saved passwords etc.) and cryptocurrency wallets.
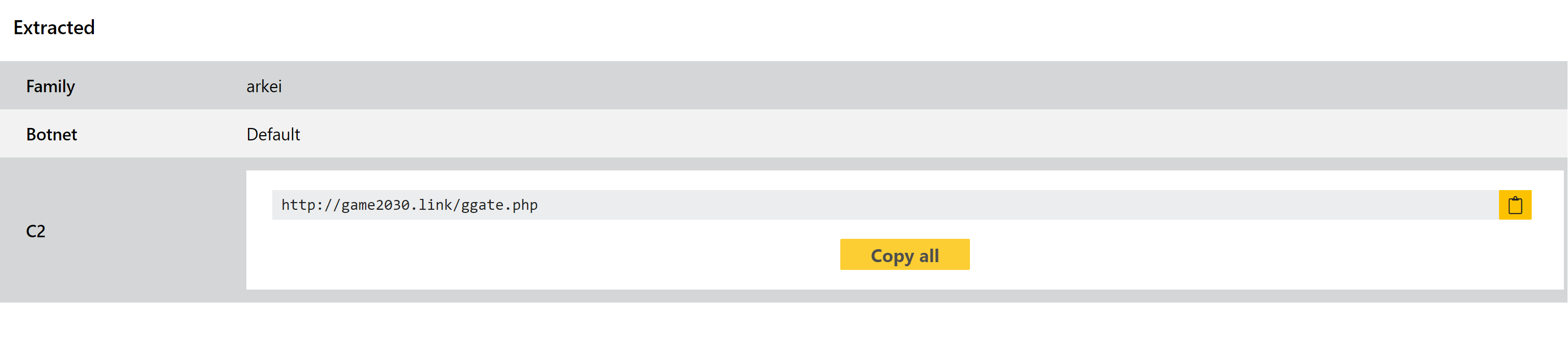
Triage has long supported detection of the family, and a few weeks ago we made some changes to account for new variants, but this week we are extending this to also include a full configuration extractor.
You can find an example with the new extractor below. For other samples of the family you can use the search function on Triage - i.e. family:arkei.
Analysis:
MetamorpherRAT
Metamorpher RAT - or to give it its full title Imperium Metamorpher RAT - is not new to the online scene having been first observed on hacking forums as far back as 2013. Since then its source code has been leaked, enabling anyone to easily modify and update it as needed. As such it is still a relevant threat today, although now much changed from its original incarnation.
Its functionality is fairly typical for this kind of threat. Among other things it can capture screenshots or images using attached webcams; download and execute additional payloads; steal login credentials from local software like web browsers and FTP clients; and use the infected machine’s browser to navigate to specific webpages.
We have observed samples being uploaded to Triage in recent months, so this week have implemented family detection to properly classify them.
Analyses:
Qakbot
Qakbot has been something of a regular visitor to this blog, so we won’t go into detail about the family here. We made some changes just a few weeks ago to better handle a new Qakbot variant - you can find that blogpost here.
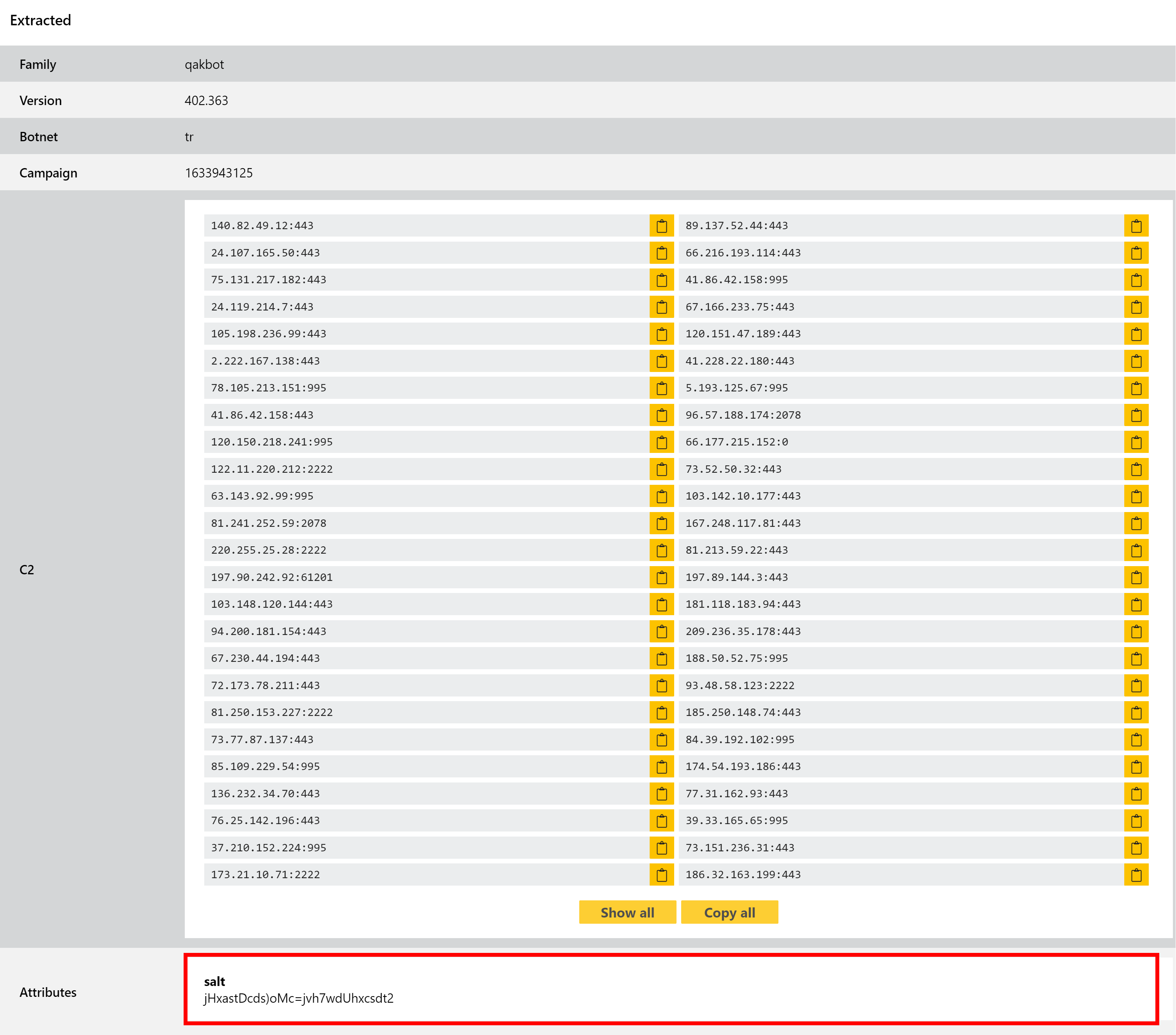
This week’s change is fairly minor, involving a tweak to our configuration extractor so that it now also dumps the salt value used by the family in its C2 communications. This should help with tracking and identifying new versions going forwards.
You can find examples of the family using the search term family:qakbot.
Tofsee
Tofsee is a botnet which has been around in the wild for many years, going back to at least 2013. It is modular in design with each component being intended to carry out a different roles such as clickfraud or cryptocurrency mining. Its main goal however is to build a botnet which can be used for mass spam campaigns to expand the network and dsitribute both Tofsee and other payloads.
Up until 2016 Tofsee was mainly distributed via exploit kits like RIG, but in that year Cisco Talos reported that this was changing as exploit kits began to fall in popularity. With the disappearance of the Angler kit the landscape changed significantly, and Tofsee moved to relying far more heavily on its own spam campaigns to continue distribution and enable the botnet to grow.
We added basic detection for Tofsee early on in the development of Triage, but this week have revisited the family to implement a full configuration extractor.
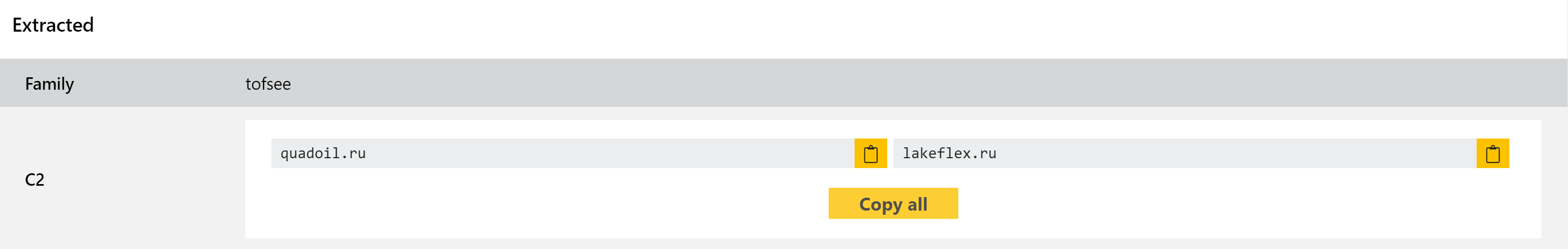
You can find examples using the search term family:tofsee
SakulaRAT
Sakula is another family with a fairly long history, this time going back to 2012. However it really rose to prominence in 2015 after being used in a series of targeted attacks on companies throughout that year. Dell SecureWorks published an in-depth blogpost about the family in July 2015 following this spate of activity.
The family is fairly straightforward, mainly being used to provide remote access to machines to enable an attacker to run commands and/or download additional payloads as desired. It communicates with its C2 servers using simple HTTP GET/POST requests which are XOR encoded. It does not seek to steal data or perform other actions itself.
We recently took a look at the family and implemented initial family detections - you can find some examples below.
Analyses:
Raccoon
Raccoon is becoming another fairly regular sight in these blogposts. Initially reported in the wild in April 2019, it is a fairly simple infostealer which has proven very popular with threat actors due to its low cost and high reliability. It has been used widely since it released and remains active in 2021, regularly being among the most common submissions to Triage.
In terms of functionality it mostly limits itself to harvesting credentials stored by local web browsers and stealing any cryptocurrency wallets available on the infected machine. It is most often distributed via phishing emails leveraging malicious Office documents for initial infection.
We made some improvements to our configuration extractor recently, and this week we are revisiting the family to make some more tweaks which should improve the quality of the output. In the background the rules which trigger the configuration extractor have been updated to support a wider range of variants - for example we observed some samples which now contain multiple C2 URLs (named url4cnc in the samples). In addition the data produced by the extractor now includes the sample’s version number to help with tracking future changes.
Analyses:
Danabot
Danabot is a banking trojan/stealer which has seen widespread usage since it appeared in mid-2018. The family is modular with functions for things like browser injection/sniffing, stealing credentials stored locally by various software like browsers and email clients, and full remote access.
The family has gone through quite a few changes over the years, with some significant new versions being spotted throughout 2021. It has featured in our blogposts a few times lately as we’ve updated signatures to account for these changes, and this week we have reviewed some additional samples and made a few tweaks to our configuration extractor to better handle the entire family.
Analyses:
Colossus Ransomware
The Colossus family is yet another new addition to the ransomware scene in 2021, initially being reported by ZeroFox in late September.
Unlike many of the ransomwares which pop up on forums etc., Colossus appears to be setting itself up as a serious new offering in the ransomware-as-a-service market with a number of features to increase its stealth like Themida packing and various sandbox evasion techniques. It’s also following the trend set by some of the big players like REvil/Sodinokibi in that they steal data before encrypting, and then use it as leverage to ’encourage’ payment.
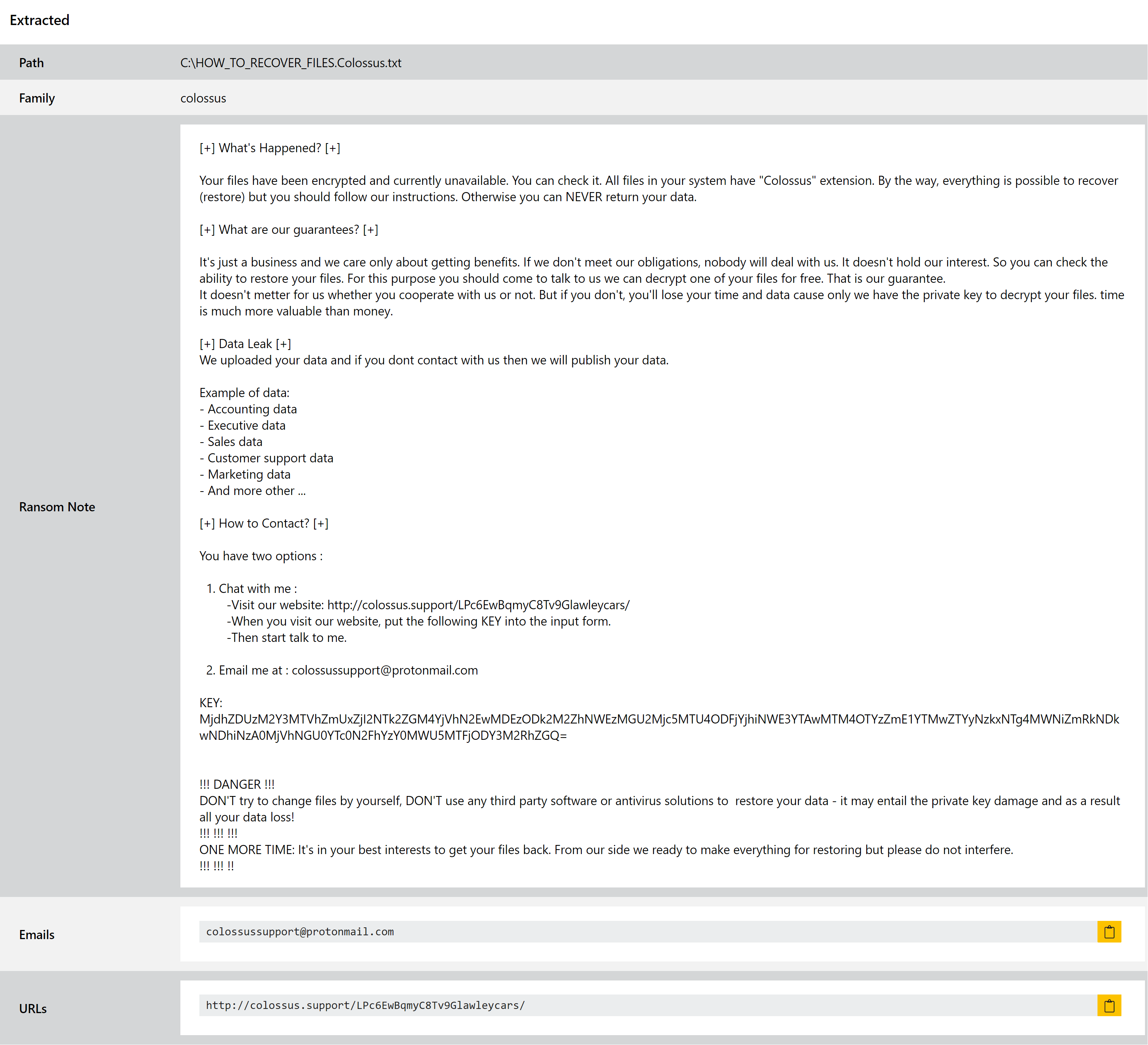
The ransomnote, as shown above, bears quite a bit of similarity in layout to those commonly used by REvil/Sodinokibi. The family’s name also comes from this note, with the extension for the file including the word Colossus.
According to ZeroFox’s investigation, the family has successfully breached at least one company which it is currently in ransom negotiations with.
Our parser dumps and extracts the ransomnote, and we have added detection to ensure the family is correctly identified.
Analysis:
Cryptbot
CryptBot is an info-stealer which was first seen in the wild in early 2019, and has been active fairly constantly since then. It is often distributed bundled alongside legitimate software which acts as its lure, generally affecting users who have downloaded cracked versions of common programs.
Triage has had support for the family since very early on in the platform’s development, but as an active family new variants often pop up which require some tweaks to properly work with our configuration extractor. This week is no different, as we recently noticed some new versions on Triage which weren’t being handled correctly. We have now made the necessary changes to ensure config extraction works as expected.
Analysis:
