Welcome to another week of Triage Thursday updates! We have another set of detection improvements to go over today mostly related to configuration extractors - read on below for more on those. We’ve also been working hard on some upcoming improvements to the UI which we’re looking forward to revealing in the coming weeks, so stay tuned for that!
In the news this week:
- Updated BazarLoader detection to improve coverage of x86 versions
- Updated Vidar configuration extractor
- Added static detection for ERMAC Android banker
- Added new configuration extractor for Jupyter trojan
If you come across any issues or missing detections while using Triage, please do send us feedback - it’s a big help in deciding what we should be prioritising. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
BazarLoader
BazarLoader appeared on the scene in April 2020 being used by the Trickbot gang as a successor to their long running family of the same name. Initially part of a 2 part infection with the BazarBackdoor module, these components have since been separated and are now commonly seen being used independently of one another.
BazarLoader has found widespread use as the initial access point for a variety of other families, including the Ryuk and Conti ransomware families. Indeed it has become one of the main vectors for ransomware infection over recent months.
As with their previous projects the Trickbot gang are very actively maintaining and developing their tool, with new versions appearing on a very regular basis in a constant effort to stay ahead of countermeasures. Triage has long included detections for the family but over time its lineage has become more and more complex and varied, and we have been made aware of some x86 variants which were not being correctly handled. This week we have done a deep analysis of a selection of these and have updated our detections accordingly.
We’d like to give a shoutout to community member Rony for bringing these samples to our attention.
Analyses:
Vidar Stealer
Vidar is an infostealer first discovered in late 2018 and which is thought to have released in October of that year. It started life as a fork of the older Arkei stealer, though it has seen many changes and evolutions since then.
The family is quite flexible in its operations. It fetches a configuration file from C2 at runtime and this dictates which features are activated and what information is gathered and exfiltrated. The way in which it gets hold of this config has changed over time - indeed it was recently observed using Tumblr as a C2 path for this purpose.
Vidar has been supported by Triage for some time, including with its own configuration extractor to dump relevant information. We recently observed a new variant however which was slipping by our detections, so we have carried out a bit of a review and applied some updates as needed.
Analyses:
ERMAC Android Banker
Earlier this month ThreatFabric published a report about a new Android banking trojan they had observed being advertised and sold through forums. Calling itself ERMAC, they report that it closely resembles the old Cerberus banker in terms of the codebase, with only a few aspects of the obfuscation and encryption algorithms showing any significant differences.
ThreatFabric also report that, based on overlap in the C2 servers and the forum accounts propagating the family, the new family is chiefly being operated by the former BlackRock stealer actor(s) who have been a long running threat group targeting mobile markets.
Like its predeccesor, ERMAC’s infostealer capabilities mainly focus around using overlays to trick users into entering sensitive information which can then be exfiltrated. However it also doubles as effectively a full backdoor, inheriting all of Cerberus’s other functionality too such as full control of texts and calls, installing/deleting applications, and dumping contacts.
We have reviewed a selection of samples available from both ThreatFabric and the community, and have implemented initial static detection to classify it correctly in Triage.
Analyses:
Jupyter Trojan
Jupyter was first reported in late 2020 in a blogpost by Morphisec. It is a relatively straightforward infostealer which targets data stored by the common Chromium, Firefox, and Google Chrome browsers. It also includes the ability to open a remote backdoor into an infected system giving operators the option of manual intervention if desired.
A couple of weeks ago Morphisec published another post about the family, reporting that it has developed a new infection chain with modules consistently receiving “very low to zero detections in the VirusTotal database”, meaning that it is slipping under the radar of most anti-virus solutions on the market. The new approach leverages MSI installers which are generally set up to resemble legitimate software, even reportedly going so far as to actually install a full version of the relevant software as well as the malicious payload - Morphisec report that all the examples they studied were presented as Nitro Pro 13, a commercial PDF viewer/editor.
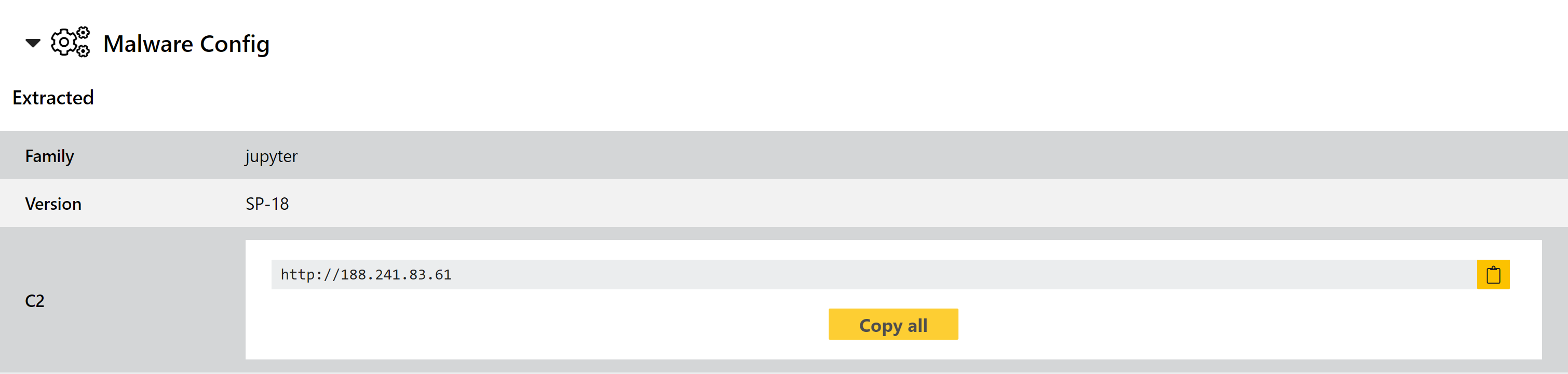
For full technical details of the latest version you can find the writeup on the Morphisec website here. We have reviewed available samples - of the new version as well as historic variants - and implemented both basic detection and a configuration extractor for the loader stage capable of dumping C2 addresses and version information.
Below you can find links to a selection of the samples, with a few examples of both the installer and payload modules provided for reference.
Analyses:
Main installer:
Payload only:
