After last week’s look at our new macOS support, we’re back to our usual format today taking a look at all of the changes to Triage over the last couple of weeks. We have a wide range of topics this time, with the normal selection of signature updates as well as UI changes and new TOR network support. Check out the full content list:
- Multiple UI updates
- TOR network routing
- Updated Snake keylogger configuration extractor
- New Family signatures for Magniber and Prometheus ransomware
- Updated Revenge RAT detection and configuration extractor
- New SystemBC configuration extractor
- New signatures for common packer frameworks
- Updated Orcus RAT detection
- Family detections for selection of skidware RATs
If you missed it over the last few weeks, we are also currently hiring a Go developer to join the Hatching team and help build the future of Triage. If you think this might be of interest to you or someone you know, the full job listing can be found here - feel free to reach out with any questions.
You can also contact us with any feedback or suggestions about Triage or the analyses it produces - we’re always keen to hear from you. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
UI Updates
If you use the public Triage server regularly, you’ll probably have noticed a few changes to the user interface over the last week or 2. These are part of a larger revamp of the platform to prepare for some of the planned features we have coming later in the year - more on those in future blogposts!
For now though, there are a several nice tweaks to make the user experience a bit smoother. We’ll introduce a couple of the main ones below. There are also minor appearance changes to the site as a whole
New Submit Screen
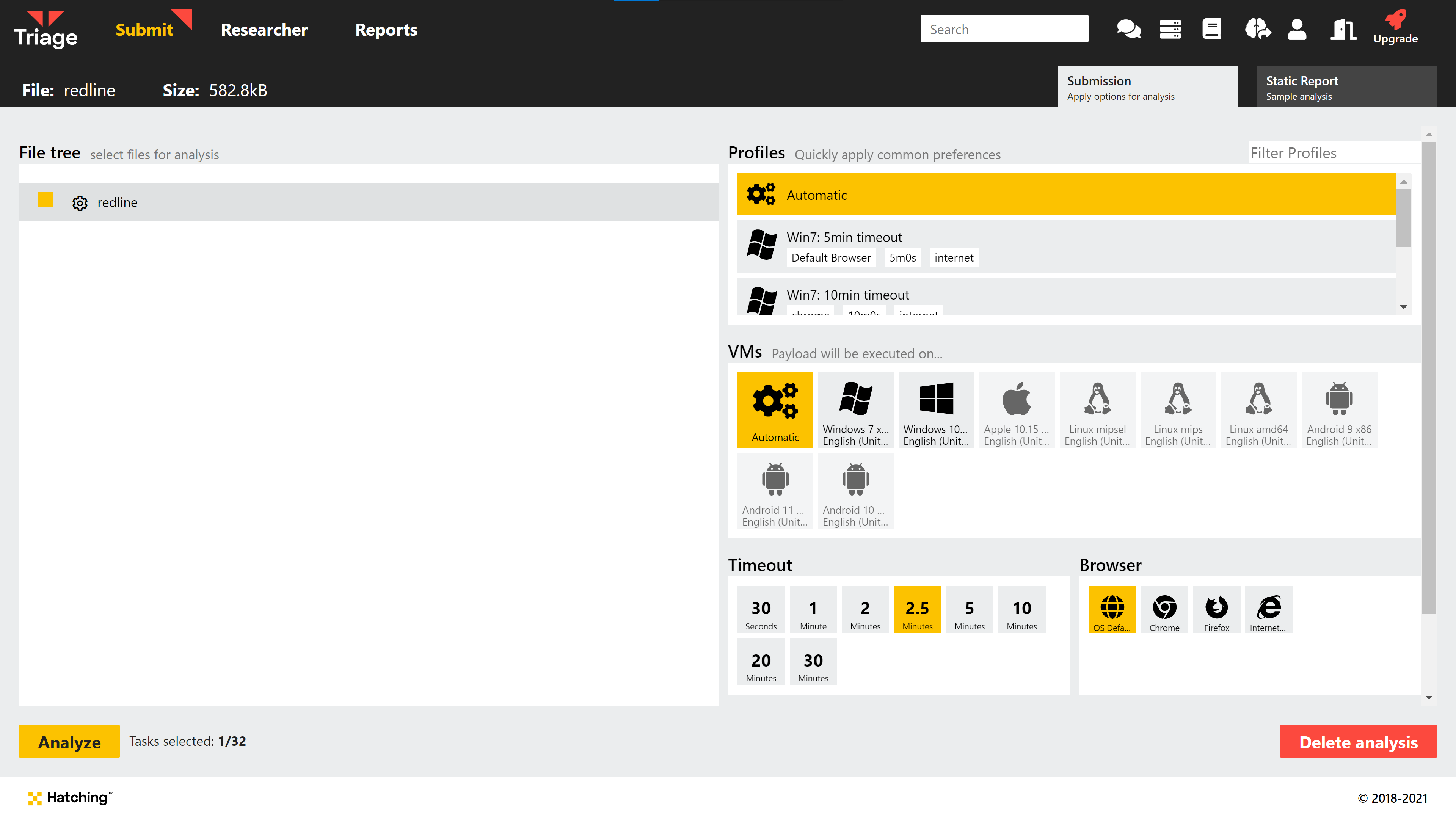
We have begun the first steps towards a more advanced and flexible submit process, with a new file picker window as shown above. This now gives you the option to customise the analysis parameters directly at the time of submitting a file instead of having to use preset Profiles - though of course these are still available as a way of saving common configurations.
Currently the available options are the same as before, but we’ll be making additions to these in the coming months.
Updated Replay Monitor
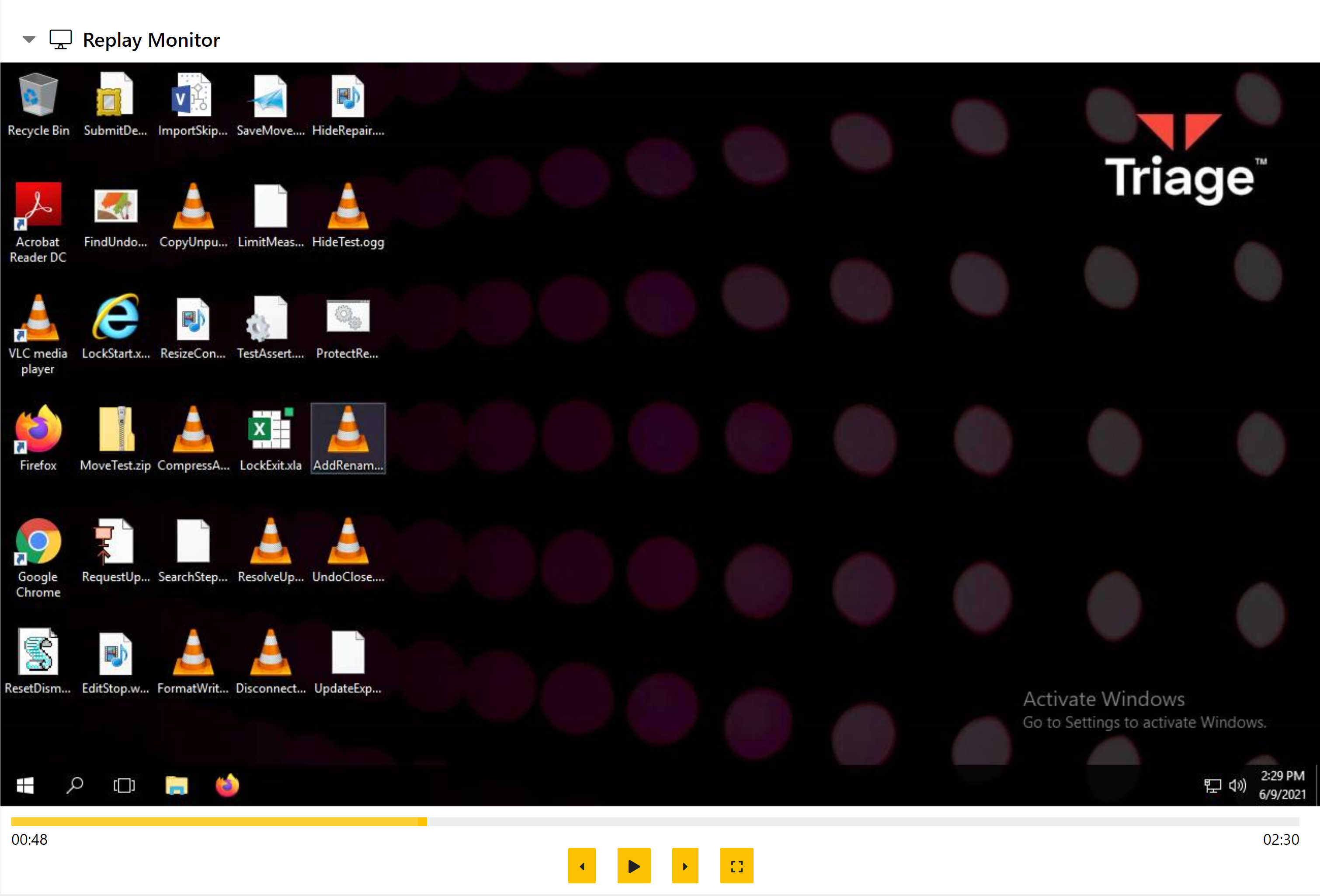
Following some requests from users, we have improved the Replay Monitor in reports to be a little more visible and responsive.
The playback resolution will now adapt to fit the available space better, and we have added a ‘Fullscreen’ option to view the replay recording more easily.
Cleaned Up Machines Listing
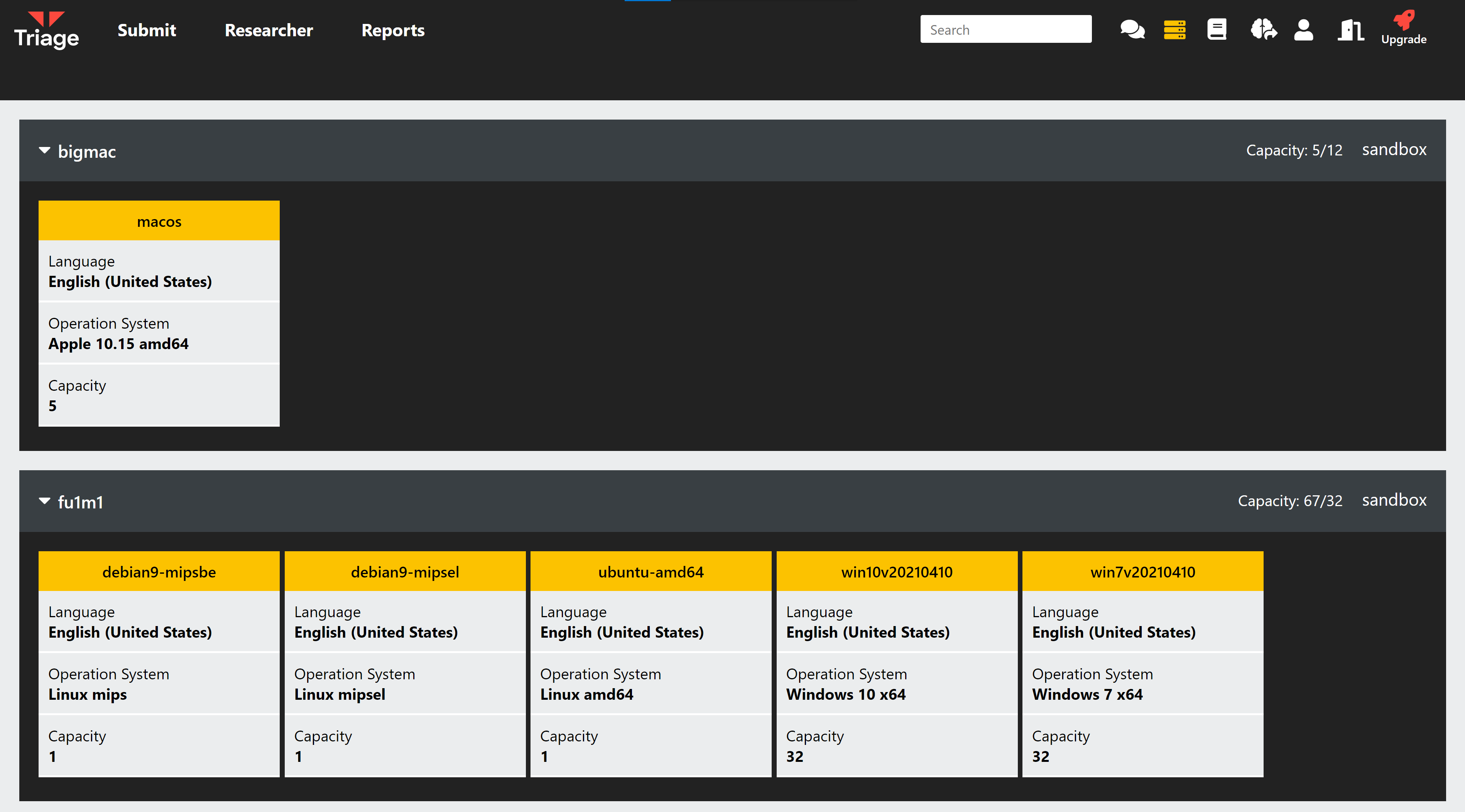
This one will mainly be useful to those using the Private Cloud, but users on the Public accounts also have read-only access to this page. Here you can find information on the available VM configurations, and how many Triage can run in parallel for sample analyses.
TOR Network Routing
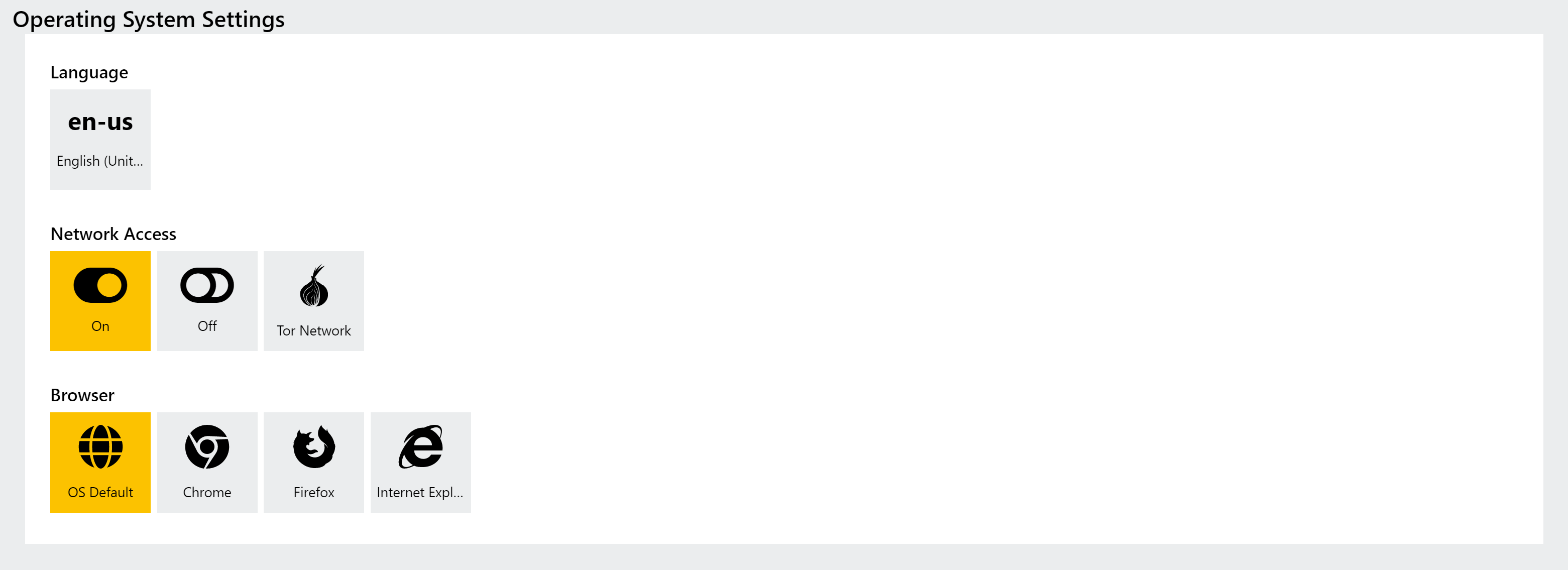
The ability to route VM traffic through TOR has been a common request since Triage launched, and this week we’re happy to make this feature available for the first time.
TOR can be enabled in the Network Options section of Profiles (or the new Submit screen mentioned above), and will direct all traffic from the Triage VM through the TOR network. This is currently intended for the selection of cases where it would appear that our servers have been blocked by malware operators, causing various HTTP errors when attempting to reach out to C2 or download additional stages. Using TOR, we are able to mask the true source of the request and add some resiliency to our network traffic.
Currently the TOR options are not configurable, and will simply use the settings defined by us internally. We’ll be continuing to expand on network support in the future with things like geolocation proxying so keep an eye open for more news on this front.
New Ransomware Family Signatures
This week we’ve deployed initial detections for a couple of additional ransomware families - Magniber and Prometheus. We have analysed samples available through Triage and built preliminary family signatures to correctly classify them on top of the existing behavioural results and ransomnote dumping.
You can find more information on each family and some example analysis links below.
Magniber Ransomware
Magniber has been around for a few years, initially solely targeting users in South Korea and then expanding to cover additional South-East Asian countries. The malware is generally spread via the Magnitude Exploit Kit, which like many recent EKs also mainly operates in the APAC region, but the ransomware itself also included extensive checks to ensure that it only ran on machines in that area.
The family’s name comes from this relation with the Magnitude EK, and some code similarities to the successful Cerber ransomware.
Recent samples appear to have done away with the geolocation checking, likely marking a move away from dependence on exploit kits for distribution as these are normally not as successful in Western countries.
Analyses:
Prometheus Ransomware
Prometheus was first observed in the wild in early 2021, and has been identified as a new variant of the Thanos ransomware family which appeared during 2020.
The developers are claiming to be part of the REvil threat group, but according to reports by the likes of PaloAlto Networks it seems likely that this is a lie being used for marketing purposes - the REvil name carries some weight in the ransomware scene.
The group claims to have breached several dozen organisations in the first half of 2021, but reports show that so far only 4 have paid up. However it appears the family is quite active, and will likely remain so for some time.
Analyses:
Updated Snake Keylogger Configuration Extractor
Snake is a relatively straightforward keylogger which is sold through forums rather than being used by a single actor. As is common with modern keyloggers it also includes some functionality of a stealer, being able to gather stored credentials from browsers, take screenshots, and extract the contents of the clipboard.
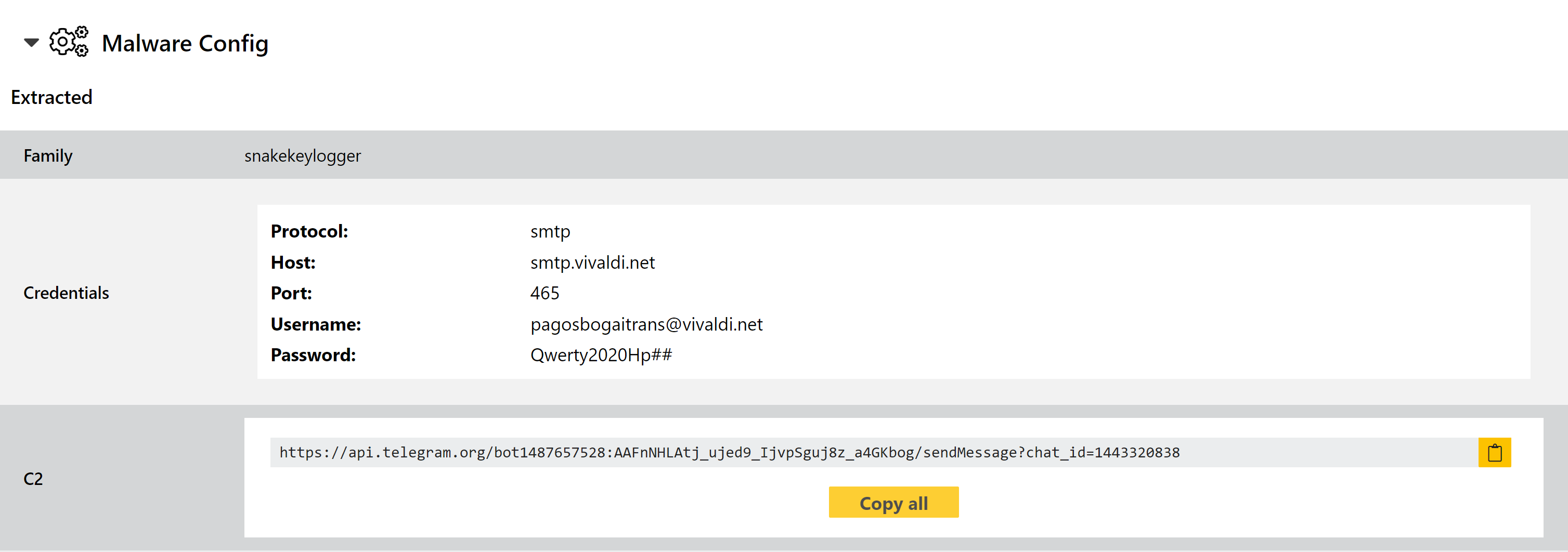
We added a configuration extractor for the family back in March but recently observed a new variant which was getting past it. We have analysed the available samples and updated as required. As usual we’ll continue to keep an eye out for any further changes and will make tweaks if needed. In the meantime you can find examples of the new variant below.
Analyses:
Updated RevengeRAT Configuration Extractor
RevengeRAT is an old face in town, with the original versions dating back to 2016. It is a full-featured remote access tool providing complete control of any machine it is installed on. The source code was leaked early on, meaning that it has become a popular choice for building custom versions by various threat actors. Nowadays there are lots of different variants floating around making reliable detection a challenge at times.
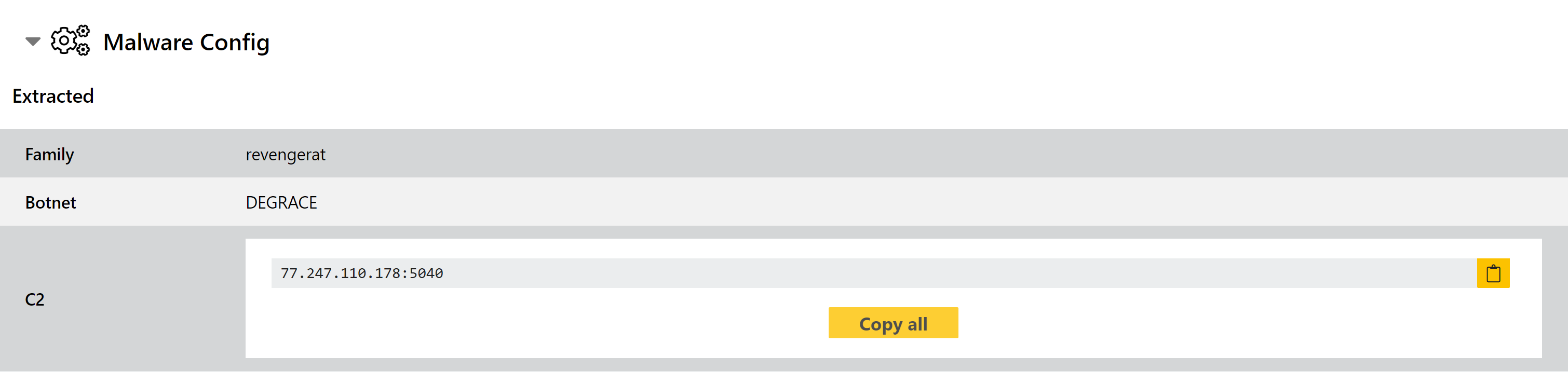
We have previously added and modified detections for the family based on samples observed on Triage, and this week we’re back with a minor background tweak to support some more versions observed recently. We doubt it will be the last time RevengeRAT appears in one of these blogs, but it should cover all current samples of the family.
Analyses:
New SystemBC Configuration Extractor
SystemBC is a RAT which is commonly used as a loader stage for other threats - most recently ransomware families. It provides secure download of remote files, as well as its range of remote administration options, making it a powerful tool for ransomware gangs looking to carry out targeted infections with manual control over data gathering and deployment.
We added family detection back in February 2021, and since it has continued to see widespread use we’re revisiting it this week to add a full configuration extractor. We have carried out reprocessing of all recent samples to properly reflect this change so you can find analyses simply by searching family:systembc, but a few examples are also linked directly below for reference.
Analyses:
Detection for Common Packer Frameworks
Whilst not always malicious in and of themselves, the presence of a packer can be a sign that a sample is attempting to make itself harder to analyse using static methods. Triage already features detection for a few different packers, providing a fallback to suggest that additional analysis is required in case execution fails for some reason and prevents behaviour being captured fully.
This week we are adding rules for a few more frameworks seen in use recently. All of the below target solely .NET assemblies - some examples are provided for each as a reference:
.NET Reactor
CustAttr
Core1
Between them, these 3 have been used in many thousands of samples uploaded to Triage over recent months. To provide more detail on them and help with any further manual analysis, we have added rules which will provide informational feedback about the presence of the packer.
Updated Orcus RAT Signatures
Orcus is a relatively advanced remote access trojan with an extensive feature set. It is sold through forums for use by varied actors looking for a stealer/backdoor solution, and includes support for custom plugins enabling users to easily extend or target its capabilities to their use case.
This week we’ve made some minor additions to our detection for the family, adding fallback rules to catch samples which slip by our existing detections. Some examples from the last couple of months can be seen below.
Analyses:
Family Detections for Recent Skidware RATs
There are always dozens of families coming and going which barely last long enough to be worth building detections for. Small, poorly made trojans and ransomware samples which make a single phishing run and then vanish; or the new ’next big thing’ which turns out to be worse in every way than its existing competitors and never gets off the ground.
This week we noticed a few RATs that seemed worthwhile looking into, so we have pushed detections for them despite their low technical complexity and poor implementation. Some relevant links for each of these are given below.
