Welcome to another week of our Triage Thursday blog series! In this series we go over the detection and feature updates deployed during the course of the week. This week will be a fairly short one so let’s dive straight in:
- New configuration extractor for Lucastealer
- New signatures and configuration extractor for XWorm RAT
- Updates for SnakeKeylogger to handle a new variant
- Updates for Erbium stealer to add detection and extraction for recent samples
Luca Stealer
Luca is an infostealer written in Rust which popped up around the middle of 2022. We initially added support for the family back in August - you can find more details about the family in the relevant Triage Thursday blogpost, in the technical breakdown by Cyble, or in analysis by Blackberry.
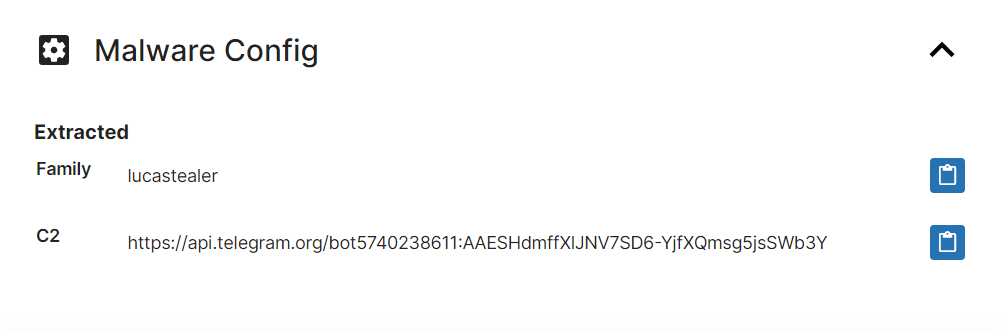
The support we added in August only covered basic behavioural detections to ensure that samples were properly tagged, but as the family has continued to be active since then we have revisited it to build a full configuration extractor. This is intended to dump out the C2 URL in use, which with this family is generally either based around Telegram or Discord.
Analyses:
XWorm RAT
XWorm was first brought to our attention this week by Twitter user 0xToxin.
The family was identified by researchers at Cyble, as part of an investigation into the EvilCoder project. During their research they identified several families/tools developed by seemingly the same group/individual and available for sale through the dark web, with XWorm being one of these payloads. Users purchase access to a malware builder which can generate a payload to their preferences.
The family has quite a wide range of functionality covering RAT, stealer and even ransomware operations. Among other things it can download and launch files, carry out DDoS attacks as part of a botnet, and provide a remote desktop connection; steal browser data, FTP credentials, log keystrokes, and intercept cryptocurrency wallet addresses with a clipper; and encrypt/decrypt files on the system.
It also includes quite a few measures to try and prevent analysis in automated tools and sandboxes especially VMWare, VirtualBox, Sandboxie and Any.Run. None of these are able to detect the Triage VMs though so execution continues.
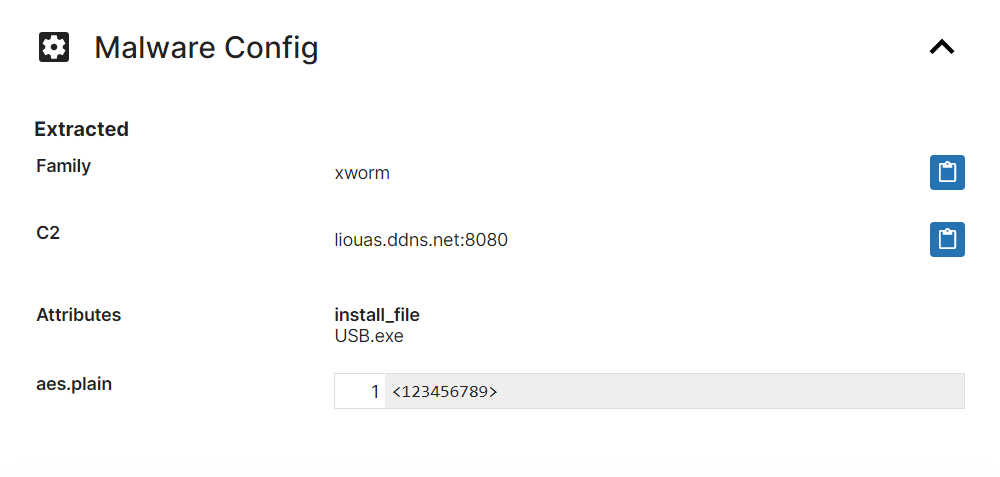
We have reviewed samples made available by Cyble and researchers like 0xToxin and implemented both standard detections and a configuration extractor. The extractor can dump out C2 information as well as the mutex in use (where relevant) and the name of the file as defined internally for persistence etc. (if the file had been delivered by a loader as intended).
Analyses:
