Welcome back to our Triage Thursday blog series! We didn’t have an entry last week as we were busy with other things, so in today’s post we’ll go over all the major changes made since our last blog on the 14th. As always we have a bunch of new and updated detections across all sorts of families to go over:
- Updated Emotet handling for x64 variant
- Updated Vidar rules for another new version
- Tweaks and extended report for BlackGuard stealer
- New detections for ffdroider stealer
- New configuration extractor for ModiLoader
- Improvements to CryptBot IoCs/detections
- Fixed C2 issues in BumbleBee configuration extractor
- Added support for Gimmick macOS malware family
If you have any feedback, questions or issues about Triage feel free to reach out to us any time - we do our best to respond to all feedback but even if we can’t get back to you straight away your files will go into our list of things to review and help us prioritise tasks. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Emotet x64
It’s been nearly 2 whole months since we last mentioned Emotet on this blog and clearly they were starting to feel left out, so we’re back this week with updates to address a new version that popped up in the wild around Easter. For the first time the family has started using 64-bit versions of both the loader and stealer modules - as reported by @Cryptolaemus below x64 architectures had previously been seen only in very limited use.
It seems like for now this is limited to the Epoch4 variants and not the newer Epoch5 payloads, but the Cryptolaemus team suggest that this might change in future once the new version has been fully tested out.
The base functionality of the stealer is seemingly unchanged, so we have updated our detections and handling to properly support these new versions. As always we’ll continue to update this as needed, and a huge thank you to everyone who reached out with samples and feedback as this version began to appear online.
Example:
Vidar
Vidar is back again this week, this time with a couple of new versions at once which needed some detection updates. The changes are mainly internal but mess with our extractor’s parsing of the configuration sections, although we have also observed a change in behaviour for one of them. Vidar uses additional DLLs alongside the main executable, and previously would download these one by one during execution; these latest versions seem to fetch them all at once as a zip archive, extracting them on the machine instead.
We have made some tweaks to address the observed changes and ensure that IoCs are properly dumped for the samples.
If you’re not familiar with the family you can find more detail in our blogpost from July 2021 where we initially introduced the configuration extractor.
Analyses:
BlackGuard
BlackGuard is a new and currently quite active infostealer, built on the older 44caliber family codebase. We first added detection for it in early March but at the time limited information and samples were available to us for analysis. We revisited it in early April to add support for some samples we had missed originally, and this week it is back in our sights again with what appears to be new versions which were slipping past our detections.
You can find more details on the family in our blogposts linked above, or in ZScaler’s blogpost from the end of March which you can find here.
The base functionality does not seem to have changed or been added to, but some internal changes prevented our configuration extractor from properly handling the samples. We’ve now updated to fix this.
Analyses:
FFDroider
FFDroider is a new addition to the stealer landscape, first popping up online around the start of April 2022. Its base functionality is pretty familiar and in fact more limited than many of its competitors - it seems to restrict itself to stealing credentials stored on the infected machine by web browsers like Chrome, Firefox and Edge rather than the much more extensive target lists common in other stealers - but its end goal is a bit different to most.
Rather than just directly monetising data stolen from the victim, like stealing cryptocurrency wallets, this family is going after social media accounts specifically. These accounts are then accessed to extract information about them, with a focus on relevant advertising networks on those platforms which can then be used to run malicious ad campaigns using accounts already verified and setup to do so. Interestingly this process is mostly automated with the malware itself carrying out checks of credentials in real time from the victim’s PC, and extracting personal and financial information from any successful login attempts which is sent back to the C2 server for further use.
According to ZScaler’s report on the family FFDroider goes after credentials for the following websites:
- www[.]facebook[.]com
- www[.]instagram[.]com
- www[.]amazon[.]ca/cn/eg/fr/de/in/it.co.jp/nl/pl/sa/sg/es/se/ae/co.uk/com/com.au/com.br/mx/tr
- www[.]all-access.wax[.]io
- www[.]ebay[.]com
- www[.]etsy[.]com
- www[.]twitter[.]com
We have taken a look at the samples shared online and implemented some initial detections to cover the family. As a new threat we will of course keep an eye on it in the coming weeks and will release any updates as needed.
Analyses:
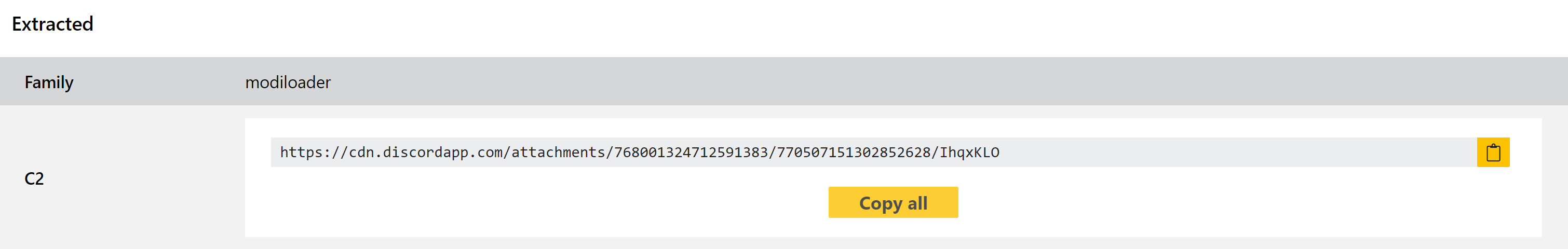
ModiLoader
ModiLoader, also known as DBatLoader or NatsoLoader, is a dropper first reported in June 2020. It is a 2 stage loader and has been observed deploying Formbook, Netwire and Remcos trojans.
We added initial support for the family back in September 2020, and it has stayed mostly unchanged since then except for a small update at the start of this year. However we recently started seeing some new versions for it with changes that needed addressing, so we have reviewed and updated our existing detections as well as adding a full configuration extractor
Analyses:
CryptBot
CryptBot is an infostealer which has been active in the wild since early 2019. Although its use has expanded over time it is regularly distributed alongside legitimate software which acts as its lure, often affecting users installing cracked versions of software downloaded from torrent sites.
The family was quite actively developed throughout 2021 with a few new versions and variants appearing over the course of the year, and has carried that into 2022 with a couple of new updates making it into this blog already. This week just sees a few minor changes which required updated behavioural detections for the family, and these have now been deployed to the public cloud. We do not currently have a sample to share publicly for this but it should provide better coverage for the family overall.
BumbleBee
BumbleBee is a loader which has been gaining a lot of attention recently. It has mainly been used by an Initial Access Broker group called EXOTIC LILY who gain access to networks which can later be leveraged to deploy additional malware families - this is then sold on to operators of other campaigns like Conti ransomware or CobaltStrike who can deploy their own payloads easily.
On a technical level it is a fairly typical example of its type, using WMI to harvest general information about the system and report it back to the C2 infrastructure which then issues commands for the next steps. This task can vary but mainly revolves around deploying code and payloads onto the system. You can find a full writeup of the family from Google’s Threat Analysis Group here.
We added detection for BumbleBee in our previous blogpost including a full configuration extractor, but since then have noticed a new version which required some additional tweaks. The issues were around the handling of C2 addresses which turned out to have a wider variety of possible formats and structures than we saw in the samples originally available, so we have now addressed this. As always with these active new families we’ll be continuing to push out updates as soon as possible for any new versions or variants, so if you come across anything you think should be BumbleBee but is not being tagged please send us feedback and we’ll look into it.
If you’re not familiar with the family, Proofpoint published a new analysis of it earlier today which you can find here.
Analyses:
Gimmick
Gimmick is a malware family which was originally aimed at Windows machines. Thought to be developed by a Chinese threat group it has been used in the past to attack organisations across Asia but up until now it has not really caught our attention which, due to our current user/customer base, is generally a bit more oriented towards US and European markets.
Recently though the developers have expanded to also include a macOS version of the implant, and some examples of this quickly made it into our sample set. This version does seem to be a custom rewrite rather than a port, written in Objective C instead of the .NET/Delphi versions seen previously on Windows, but the actual functionality is reportedly all but unchanged. It has quite a complex execution flow which attempts to bypass the main points of detection for persistence etc. - the image below taken from Volexity’s in depth report on the new macOS version attempts to break this infection process down:
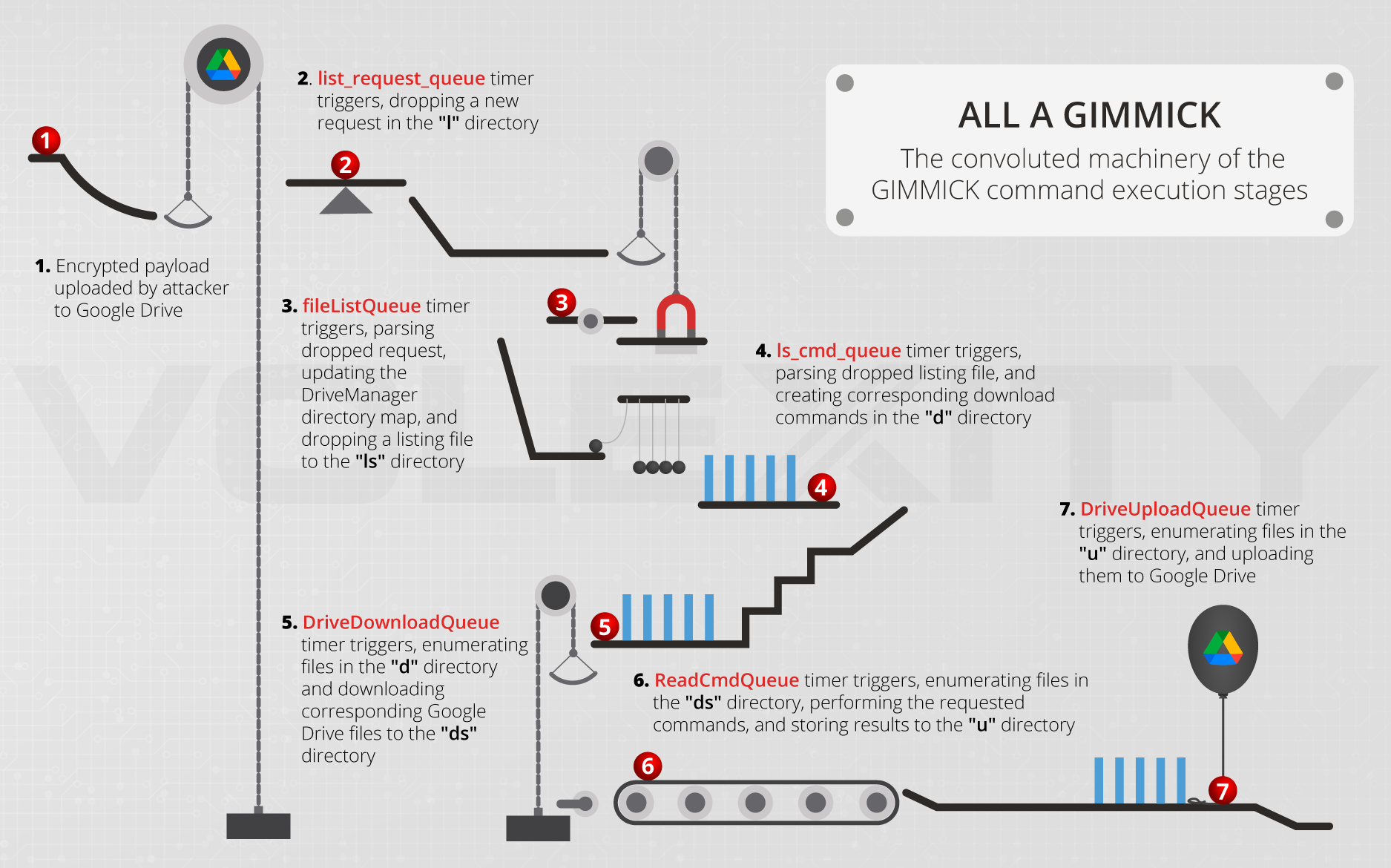
As can be seen Gimmick itself is something of a blank slate, capable of processing ’tasks’ that can cover a wide variety of purposes and goals. The C2 infrastructure has generally been seen as Google Drive but can be other legitimate hosting services to help the malware blend into normal network traffic - in fact it can be configured to only communicate with the C2 on work days to blend in even more neatly.
We have added some initial behavioural signatures for the family, and as always will revisit it as necessary.
Analysis:
