Welcome back to our Triage Thursday blog series, where we take a quick look at the updates deployed during the week. Today we’re focusing on mostly configuration extractors, with a couple of more general family detections included as well:
- Updated detections and added configuration extractor for BlackGuard stealer
- Added configuration extractor for PurpleFox
- Updated AsyncRAT configuration extractor to widen support
- Added support for Talisman variant of PlugX family
- Added support for Rust language variants of Hive ransomware
In case you missed it, last week we published a job advert for a Compliance Officer to work with us on various aspects of the business related to contracting, ISO27001 and privacy laws like GDPR. If you or someone else you know might be interested in this - experienced or new to the field - you can find the full listing on our website.
If you discover any issues or missing detections while using Triage, please do send us feedback. It’s a big help in deciding what we should be prioritising. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account!
BlackGuard Stealer
BlackGuard is a new family which has popped up during early 2022, reportedly forked from the 44caliber stealer (covered in our blogpost from the first week of March). We added support for BlackGuard as well the following week, but as an active family since then we have spotted a few samples which were not being properly detected. Also, since it seems to be here to stay for the foreseeable future we decided to add a configuration extractor as well to augment the previous behavioural and static detections.
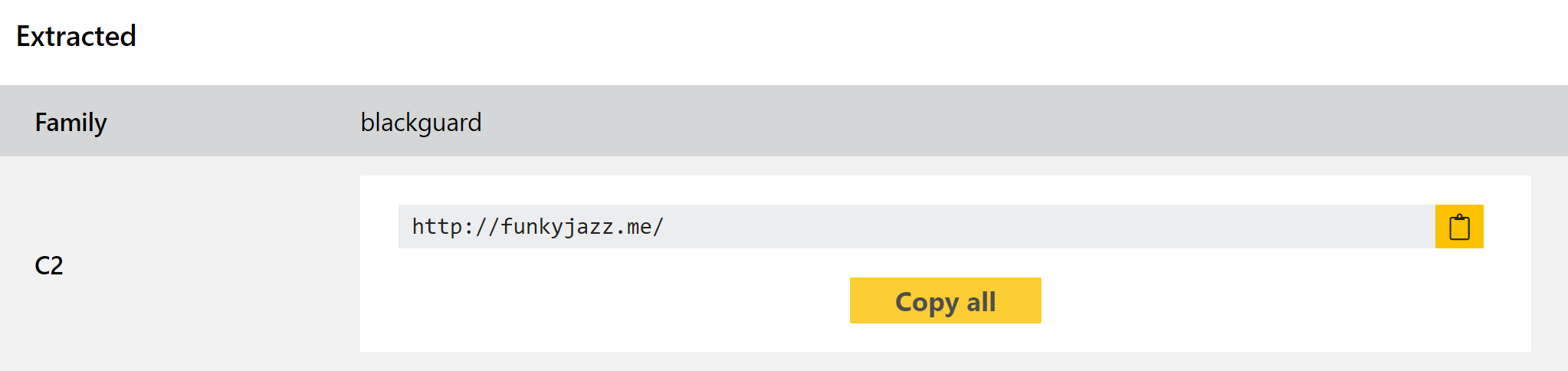
When we wrote the initial blogpost very limited information was available online regarding the origins and background of the family, but since then multiple blogposts have been published by analyst teams which shed some more light its background. According to reports by S2W and ZScaler it first appeared on cybercrime forums in January, advertised for sale at around $200 per month as malware-as-a-service.
AhnLab reports that BlackGuard is often seen being distributed via fake software downloads, especially those pretending to be hacks for popular games like Valorant. The links to these cheat programs are included in Youtube comment sections showcasing the supposed exploits in-game, leading to users downloading and installing the software. This is quite an effective lure since most users will ignore any anti-virus or other warnings from their machine, as by their nature even ’legitimate’ hacks/game cheats are often flagged as malicious anyway.
The family includes a few anti-VM and anti-analysis checks, as well as the common location query to ensure that it does not run on devices located within Commonwealth of Independent States (CIS) countries. The anti-VM checks are fairly simple in nature but include attempts to kill and antivirus or sandbox-related processes; string obfuscation to make static analysis more difficult; and a block on all mouse and keyboard input to make it difficult for an analyst to debug or otherwise interact with the malware in a safe environment.
Based on ZScaler’s excellent blogpost from March 30th (which you can read in full here the stealer targets data from the following files/applications:
| Application Type | Names/Extensions |
|---|---|
| Browsers | Chrome, Opera, Firefox, MapleStudio, Iridium, 7Star, CentBrowser, Chedot, Vivaldi, Kometa, Elements Browser, Epic Privacy Browser, uCozMedia, Coowon, liebao, QIP Surf, Orbitum, Comodo, Amigo, Torch, Comodo, 360Browser, Maxthon3, K-Melon, Sputnik, Nichrome, CocCoc, Uran, Chromodo, Edge, BraveSoftware |
| Cryptocurrency Wallets | AtomicWallet, BitcoinCore, DashCore, Electrum, Ethereum, Exodus, LitecoinCore, Monero, Jaxx, Zcash, Solar, Zap, AtomicDEX, Binance, Frame, TokenPocket, Wassabi |
| Cryptocurrency Wallet Extensions | Binance, coin98, Phantom, Mobox, XinPay, Math10, Metamask, BitApp, Guildwallet, iconx, Sollet, Slope Wallet, Starcoin, Swash, Finnie, KEPLR, Crocobit, OXYGEN, Nifty, Liquality, Auvitas wallet, Math wallet, MTV wallet, Rabet wallet, Ronin wallet, Yoroi wallet, ZilPay wallet, Exodus, Terra Station, Jaxx |
| Email Clients | Outlook |
| Messengers | Telegram, Signal, Tox, Element, Pidgin, Discord |
| VPN Clients | NordVPN, OpenVPN, ProtonVpn |
| Other Applications | Totalcomander, Filezilla, WinSCP, Steam |
Analyses:
PurpleFox
We added behavioural detections for the PurpleFox family back in February, and although these seem to be holding up well and covering the samples we see in the wild we decided to revisit it this week to add a configuration extractor.
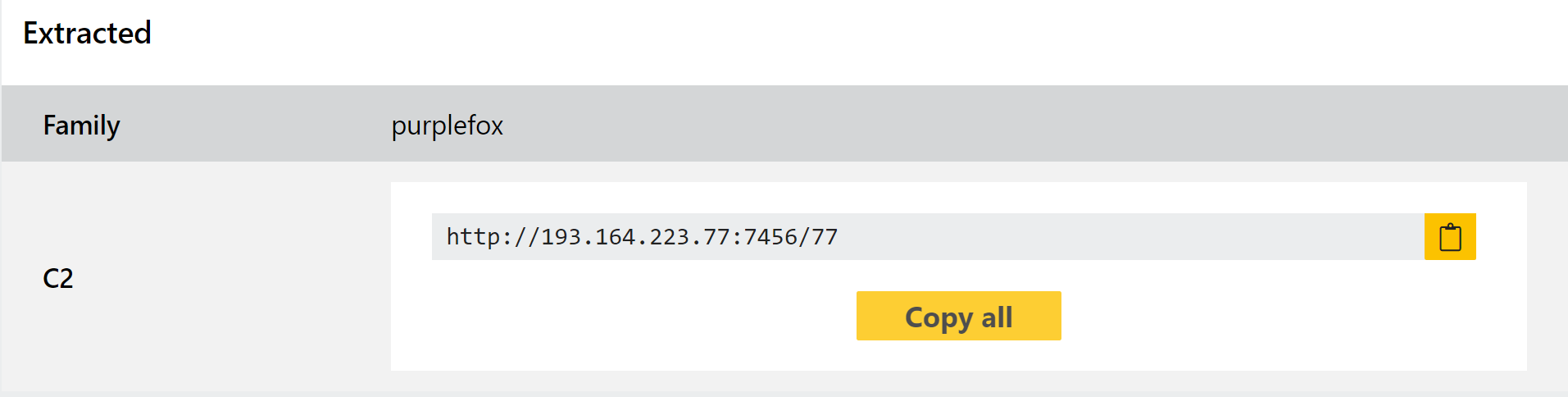
The family can carry out a full infection with its own custom dropper being used to deliver the actual rootkit. It is extremely modular, breaking the infection chain into small pieces which are, on their own, often quite unlikely to be detected by standard AV tools.
As an additional step in its attempt to appear legitimate, most samples observed so far drop an actual installer for the Telegram desktop app along with the malicious payload, and the loader itself uses icons and file information to try and imitate Telegram.
You can find a detailed write up of the family and its various stages in a blogpost by Minerva Labs here, published in early January.
Analyses:
Stage 1 payload:
- 220114-hz1grsfbbm (32 bit)
- 220104-f5fcnsaean (64 bit)
- 220104-f5195saear (64 bit)
- 220114-mye7nagacj (64 bit)
Stage 2 payload:
AsyncRAT
AsyncRAT is an open-source RAT available on Github. It claims to be for legitimate remote administration purposes only, but is of course commonly used by criminals looking for an easy to use, adaptable RAT.
We initially added a configuration extractor for the family back in October 2020, and revisited it in September last year to improve support for some new variants which had appeared in the meantime. This week we are checking in on it again due to a few more recent samples which, although were being detected and scored properly, were not quite working with the parsing logic of our configuration extractor.
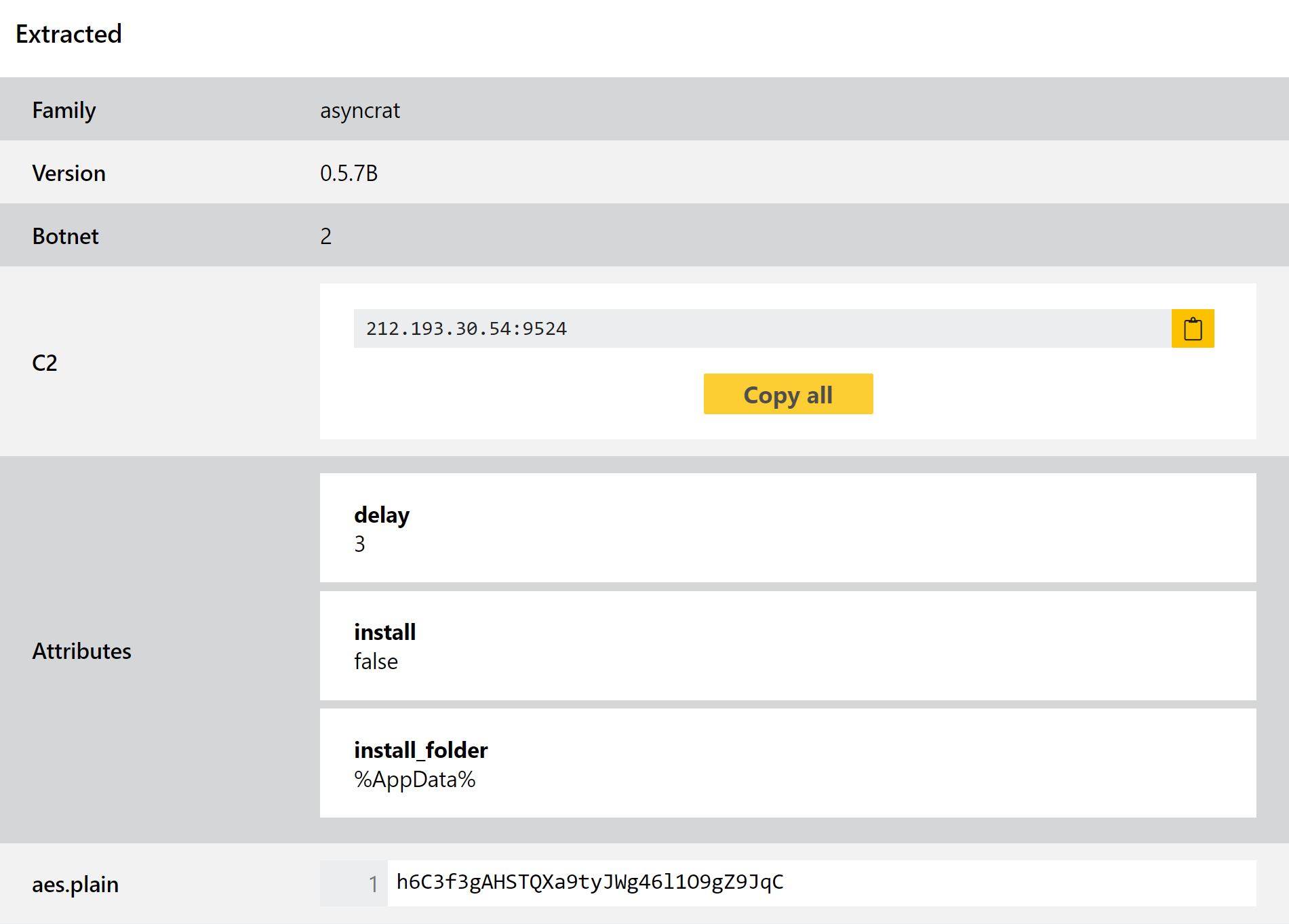
This has now been addressed, and with the update comes support for a couple of additional attribute fields available in some samples. As usual we’ll keep an eye on the family in future and will continue to update as needed.
Analyses:
Talisman PlugX Variant
Having languished in relative obscurity for a couple of years PlugX seems to be undergoing something of a renaissance, with multiple new updates and variants popping up recently. We have already addressed a few of these in recent blogposts, including last week’s where we fixed some issues with the configuration extractor to widen support.
This week we have added static detection for a more distinct variant of the family which has been observed in the wild, referred to as ‘Talisman’. The functionality and general layout is pretty similar to PlugX, but it is still distinct enough that we have provided specific identification for this strain within our reports.
It seems we aren’t quite done with PlugX yet though, and are currently looking into a couple of other recently observed variants. Hopefully we’ll have more information on those in the coming weeks.
Analysis:
Hive Ransomware
The Hive ransomware family appeared in June 2021 and rapidly established itself as one of the major players in the ransomware-as-a-service scene. Like most families like this is makes use of the double-extortion approach, first exfiltrating data before encrypting it so that the files can be used as leverage in any future ransom negotiations. The developers run a centralised leak website, the contents of which show that it has had a fair amount of success at gaining access to companies around the world.
It was recently brought to our attention that the family has begun to move to the Rust programming language, with new payloads for both x64 and x86 Windows operating systems as well as a couple of examples for Linux platforms. Although the end goal and overall activity is still the same, this change was impacting some of our detections so we have created some new signatures for this version.

Analyses:
Windows x64:
Windows x86:
Linux:
