Welcome back to another week of Triage Thursday updates! We’ve got a few family updates to go over, as well as a bit of an experiment for our handling of different file types.
In the news today:
- Expanded support filetypes
- Updated Cryptbot detections and configuration extractor
- Improved PlugX handling to cover more versions/variants
- Added detection and configuration extractor for Xenomorph Android banking trojan
- Added detection and configuration extractor for BlackGuard stealer
- Added detection and configuration extractor for Jester stealer
If you discover any issues or missing detections while using Triage, please do send us feedback. It’s a big help in deciding what we should be prioritising. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account!
Expansion to Supported Filetypes
So far with Triage we have always kept the supported file types to a limited list, based on those formats we think are relevant for behavioural analysis like executables, scripts etc. Although files like JPEGs or other image/video formats can be leveraged maliciously their use is normally limited to 1 of 2 options:
- A fake file which is not actually a valid JPEG, MPEG etc. These are generally either plain executables with the extension or some header fields changed, or an encrypted payload disguised as one of these files but which is actually totally useless without the associated loader to decrypt/unpack and deploy it. In the case of the former Triage already covers these, and for the latter we saw limited value in allowing them to run as standalone files since they won’t do anything anyway - we’re more interested in the loader file and the sequence of actions that carries out.
- An actual, valid media file with some embedded content intended to exploit a vulnerability in a particular piece of software. Whilst these are a legitimate threat, the fact they rely on very specific bits of software meant that we didn’t see much value in supporting them.
We’re using media files here as an example since these are by far the most oft requested additions, but the same is true of many other formats. Over time it has become clear that many of our users would still like the ability to submit files such as these regardless of the limitations, so this week we are rolling out an experimental feature to open up Triage and remove file type limitations altogether. For now this will remain on the public cloud only while we iron out any issues this brings up - we expect there may be some potential for false positives here for example - and if you come across any issues or file types not behaving properly please feel free to report those to us.
Note that this only affects the UI and not interaction via the API, which will work exactly as before. The idea here is not to accidentally burn up analysis quotas on invalid files since existing pipelines might not include any file type filtering. However you can force analysis of any filetype if you like by using the pick field in your submit API request - some more details on that can be found in our API documentation here.
Cryptbot
CryptBot is an infostealer which has been active in the wild since early 2019. Although its use has expanded over time it is regularly distributed alongside legitimate software which acts as its lure, often affecting users installing cracked versions of software downloaded from torrent sites.
The family was quite active throughout 2021 with a few new versions and variants appearing over the course of the year. It most recently appeared on this blog back in December when we made some tweaks to our configuration extractor, and it’s back on the menu today with some more improvements. We have recently observed an update for the family which wasn’t being properly parsed by Triage, so this has been addressed to ensure we cover as much of the family as possible.
Analyses:
PlugX
PlugX, also sometimes called Korplug, is a RAT with a long history. It is known to have been around since 2012, although TrendMicro suggest that the developers have been running similar malware as far back as 2008.
PlugX has all the features of a remote access tool and stealer, capable of uploading and downloading files, keylogging, capturing images through attached webcams and running a full cmd.exe shell which can be used by the attacker to execute further commands. Over recent years the family has often been associated with Chinese state threat actors by companies like RecordedFuture, forming part of a much broader toolset which includes other payloads like Sakula.
We added support and a configuration extractor for the family back in 2020 and haven’t really seen any significant changes since then, until we recently spotted some new samples which were slipping by our detections. In the process of addressing that we also found a small bug in the configuration extractor so have fixed that too. Overall you should find that coverage for PlugX has been improved.
We are going to continue working on PlugX - and a couple of the other families popular with Chinese actors - in the future, but this update addresses the immediate priorities. With regard to Sakula, we’re seeing some overlap in IoCs and detections with Redline stealer so we’ll be looking at ways to better differentiate these 2 in future.
Analyses:
Xenomorph
Xenomorph, otherwise known as the “Alien”, is an extraterrestrial hive-based endoparasitoid….wait, no, wrong page. Xenomorph is a new Android banking trojan discovered in February 2022 by ThreatFabric. It was observed being delivered directly from the Play Store having managed to get by the detection techniques in use there, and reportedly had over 50,000 downloads at the time ThreatFabric’s report.
The family is a new fork of an older Android banker called Alien. However it seems that, while sharing a lot of similarities, this is more than simply a new wrapper or slightly tweaked update. The available functionality is quite different, and it also reportedly includes a lot of logging and unfinished features which have led ThreatFabric to suggest that it is in fact the beginning of a new project from the original Alien developer rather than a rip-off or direct fork. One similarity between the 2 that has been seen is the sharing of the same loader component, known as Gymdrop.
The family has features fairly familiar to Android analysis:
- Gather and exfiltrate device information
- Harvest text messages, both from the device storage and via live interception over the wire
- Carry out overlay attacks against certain applications (mainly banking/finance related)
- Intercept and modify notifications
- Block attempts to uninstall the application
You can find a complete writeup in the detailed blogpost from ThreatFabric mentioned above. You can find that here.
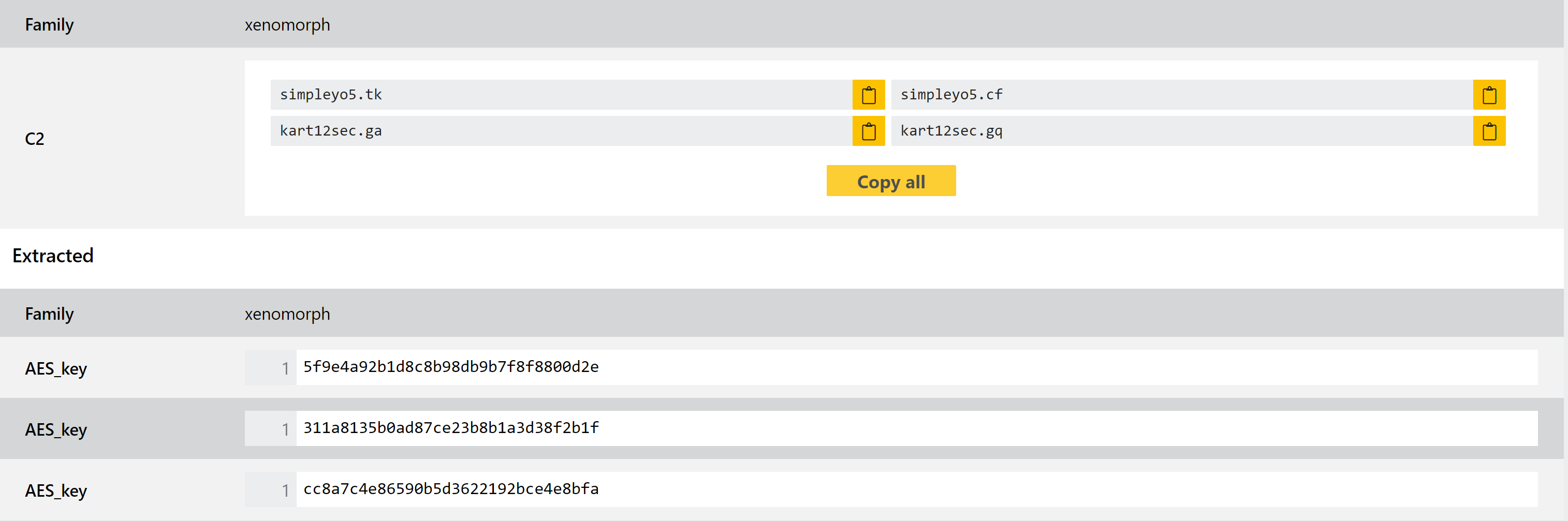
Currently there are not many samples publicly available, but we reviewed those made available to us and implemented detections and a configuration extractor. This can dump the C2 domains and relevant AES encryption keys used by the samples. An example is provided below - note that a UI update to improve the display of the configuration will follow shortly.
Analysis:
Blackguard
Last week we added support for the 44Caliber family of infostealers - you can check that out in our previous Triage Thursday blogpost. This week we’re bringing in detections for a new fork of this family with some modifications applied called BlackGuard.
As you can see above, the family was initially spotted by @3xp0rtblog on Twitter. The name is taken from internal naming conventions within the malware, and although has a lot of similarities to 44Caliber it does seem to feature a couple of differences. Chief among these is the move away from a Discord-based C2 channel, instead using either a dedicated web panel or a Telegram bot for this purpose.
We have reviewed quite a few samples which have been made available by researchers and implemented both detection and configuration extraction for the family - examples below.
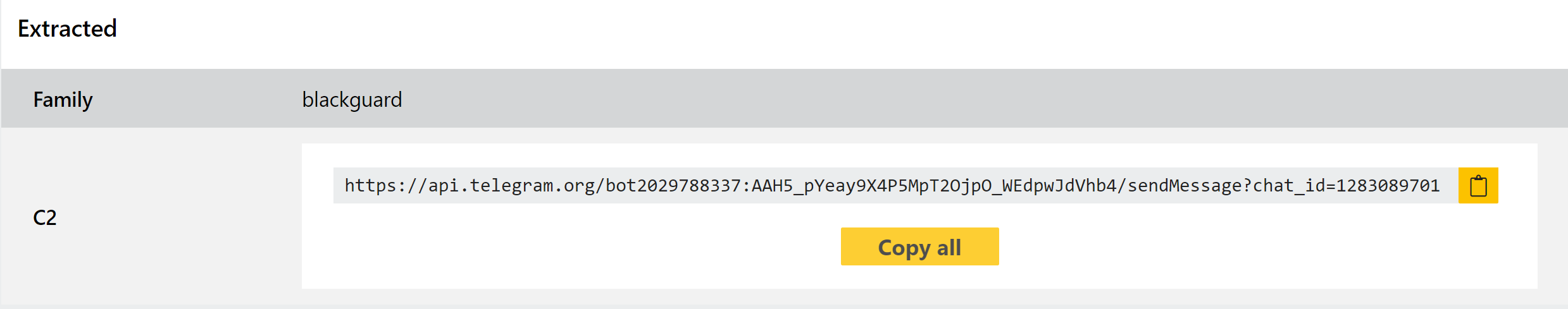
Analyses:
Jester Stealer
Jester stealer first popped up on underground forums in July 2021 but has taken some time to come to the attention of researchers. According to Cyberint this family is the ‘flagship’ malware for a group which has a whole portfolio of threats, from botnets through cryptominers to a full exploit building kit. Jester seems to have gained some more attention in early 2022, although it has been tracked since its first appearance.
The group behind it seems to have put quite some effort into marketing for their new malware, even going so far as to offer dedicated training courses with discounts for existing clients. Support and sales are mostly conducted via a Telegram channel, and are generally provided in Russian and/or English.
The stealer itself goes after data which is pretty familiar from other malware of this type - stored credentials and cookies from more than 20 browsers; data from email clients and messaging apps like Whatsapp, Discord and Telegram; system/network information and credentials; cryptocurrency wallets; FTP details from common clients. It also includes a few less common targets, like some VPN software and password managers. According to a report by Cyble it also includes some anti-VM/anti-analysis techniques.
Jester appears to be in active development, with a reported 7 versions being seen since it was initially released.
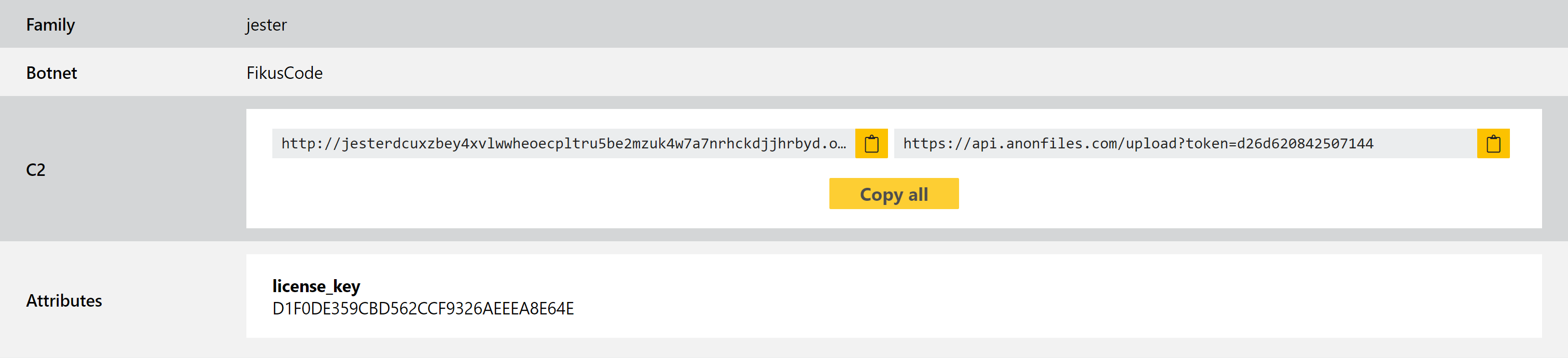
We have reviewed a number of available samples and implemented both detections and a configuration extractor - this can dump the C2 URLs, as well as the botnet name/ID and the license key associated with the sample. A number of examples are below, and you can find more using the family:jester search query.
Analyses:
