Welcome to another week of our Triage Thursday blog series! If you’re new here in these posts we go over all the changes made to Triage during the past week, and give a little bit of a breakdown of the various families. We’ve got quite a long list today so let’s get straight to it!
- Added support for Maui, Hades, and Surtr ransomware families
- Added signatures for Hermit Android spyware
- Added configuration extractor for Phorphiex/Phorpiex
- Added signatures and configuration extraction for Wellmess RAT
- Added signatures and configuration extraction for Ermac 2.0 Android banker
- Updated Danabot configuration extractor for recent samples
- Added signatures and configuration extraction for Vulturi stealer
If you have any feedback, questions or issues about Triage feel free to reach out to us any time - we do our best to respond to all feedback but even if we can’t get back to you straight away your files will go into our list of things to review and help us prioritise tasks. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Maui Ransomware
Maui has seemingly been around for some time but began to receive a lot of attention in early July 2022, after the Cybersecurity and Infrastructure Security Agency (CISA) published an advisory warning about its use by North Korean APTs against healthcare organisations in the US. Working in cooperation with Stairwell (who also published a technical analysis here), the FBI, and the Treasury Department, CISA assesses that the campaigns go back to around May 2021.
“North Korean state-sponsored cyber actors used Maui ransomware in these incidents to encrypt servers responsible for healthcare services—including electronic health records services, diagnostics services, imaging services, and intranet services.”
- CISA Joint Advisory
The malware appears to be intended for manual execution on an infected machine suggesting highly targeted attacks where the attacker will deploy the file to an already-compromised system and then use a command line interface to identify files to encrypt. The operator can also extract data from the system directly.
This manual execution complicates detection in a sandbox because when the file is run without any command-line arguments it will just print usage information and exit.
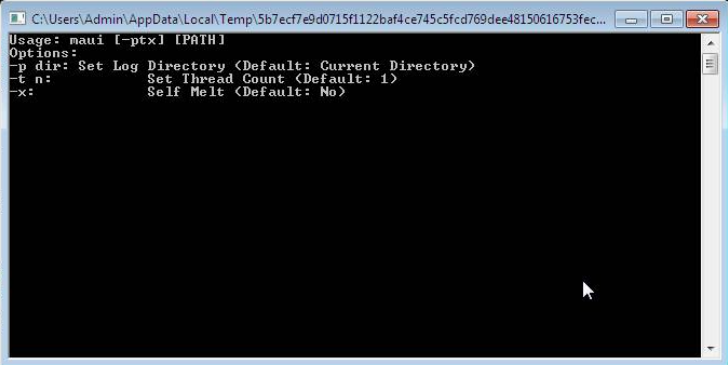
To try and ensure detection even when it doesn’t run fully we have implemented static signatures to cover the samples available to us.
Analyses:
Hades Ransomware
Hades ransomware has been active in the wild since December 2020, generally attributed to a single threat group rather than using a ransomware-as-a-service model. The exact attribution is a little hazy but Mandiant suggests that it is associated with the well known Evil Corp group (otherwise referred to as INDRIK SPIDER) due to significant code and infrastructure overlaps with their other projects.
Hades is reportedly a 64-bit variant of the WastedLocker family which was also developed and used by Evil Corp prior to the sanctions issued against the group by the US Treasury Department in late 2019. Following these measures the group went through a quiet period while they updated tools and methods to bypass the new countermeasures - Hades seems to have been part of this as they moved away from the now widely-detected WastedLocker.
Along with trying to reduce its detection the new family also added a few improvements and updates over the old functionality including more code obfuscation, a shift to system calls instead of standard Windows APIs for file and registry actions, and a new UAC bypass technique.
Generally speaking it seems that Hades has already been replaced by new ransomware families like PhoenixLocker and PayloadBIN, and more recently Mandiant reports that Evil Corp seems to be moving away from developing their own custom ransomware altogether in favour of existing RaaS payloads like Lockbit. However samples still popup in the wild so we have reviewed a few that were submitted to Triage recently and implemented basic detections to make sure they don’t go undetected.
Analyses:
Surtr Ransomware
Surtr popped up in late 2021 as a new ransomware-as-a-service. It includes limitations to prevent execution within CIS countries and contains a number of references to the REvil/Sodinokibi ransomware group (for example changing the system manufacturer name to Tribute to the REvil <3.). Analysis suggests it’s unlikely the developers are affiliated with those behind REvil but they may have been in the past or are just leveraging the name to try and gain some publicity.
The family has multiple anti-VM and anti-analysis techniques, and uses a few different persistence methods to make sure the malware is executed after any system reboot or login. It writes itself to the Start Up folder, creates scheduled tasks to trigger on user login, and backs it all up with registry Run keys.
We have added behavioural and static detection for the family, and also a ransomnote extractor.
Analyses:
Hermit Android Spyware
In June 2022 the Google Threat Analysis Group published a blogpost documenting a widespread spyware campaign against users in Italy and Kazakhstan. The implant is referred to as Hermit and is believed to have been developed by RCS Labs, an Italian provider of surveillance technology, and has versions for both Android and iOS.
Based on Google’s observations it seems that quite a bit of effort was put into many of the attacks. In order to infect victims the actors seemingly went as far as to get their ISP to disable mobile data connectivity completely, following up with an SMS pretending to be from the ISP and asking them to install an application from a URL to restore connectivity. In cases where the ISP could not be relied on the lure is generally a fake messaging application.
The iOS variant installs itself from a malicious webpage using Apple’s own itms-services protocol which is intended for distributing in-house apps to Apple devices. The resulting installation is signed with a legitimate certificate and satisfies all requirements due to the company being enrolled in the Apple Developer Enterprise Program.
The Android installation requires the user to take a few more manual steps, and the device must be configured to be able to install apps from outside the Google Play store.
We have reviewed available Android samples and added detection for the family.
Analyses:
Phorphiex/Phorpiex
Phorphiex/Phorpiex is a worm and loader which infects systems and incorporates them into a botnet. It also often deploys additional payloads to infected systems such as cryptojackers, miners, or ransomware.
Originally a major aspect of the family was building a botnet which could be leveraged for other malicious actions. Using a payload called Tldr, it could take over machines and build them into a network controlled by the attacker from a central C2 server.
However that changed after Phorphiex shut down its C2 infrastructure around mid-2021. As Checkpoint report in a blogpost from December 2021 the family was inactive for around 2 months before one of the developers attempted to sell the source code through underground forums. The exact outcome of this is unknown, but shortly afterwards the C2 servers came back online at new addresses and began to distribute a completely new bot called Twizt, which replaces the original Tldr.
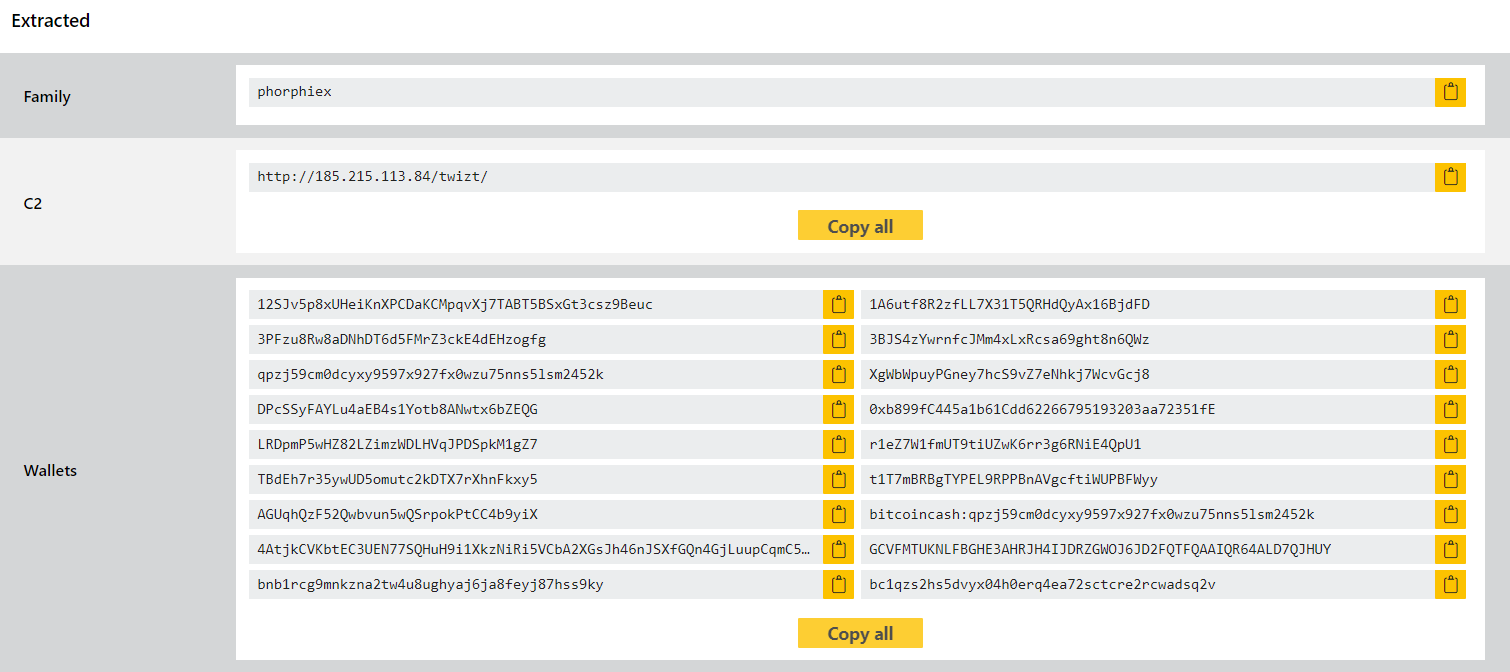
We made some updates to Phorphiex detections in our last blogpost of 2021 but since it has continue to pop up regularly we have revisited it this week to implement a proper configuration extractor to go along with the standard detections.
Analyses:
Wellmess RAT
WellMess is a remote access trojan which gives an attacker full remote access to download and execute additional files/scripts on an infected machine. It was reported in a CISA advisory from June 2020 when it was observed in use by the APT29 group (also known as Cozy Bear) to try and steal intellectual property from organisations working on COVID-19 vaccine development.
According to PWC the family goes back to 2018 originally but the 2020 version saw some updates, especially around expanding C2 methods. The latest versions can be configured to communicate over HTTP, HTTPS, or DNS protocols. It also has versions for both Windows and Linux operating systems and these use the Golang language to enable easy cross-compilation for both (though there also seem to be some variants for Windows only which use .NET instead).
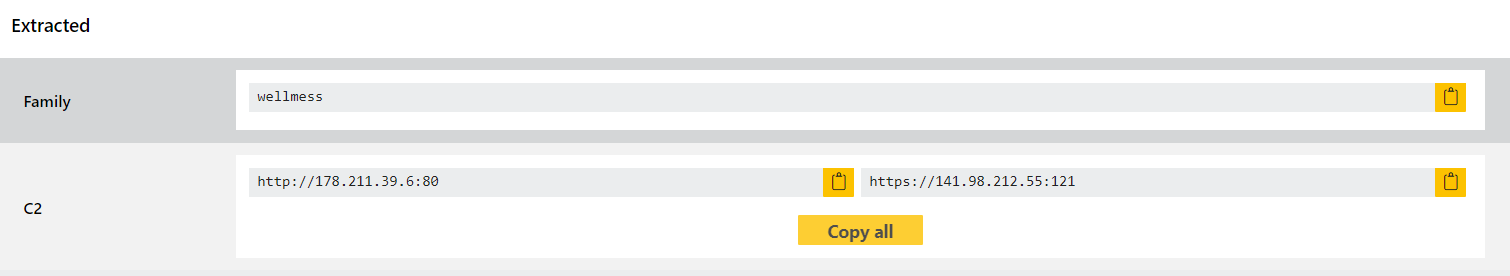
We have reviewed samples for both operating systems and implemented detections plus a full configuration extractor which can dump the C2 URL.
Analyses: Win samples:
Linux samples:
Ermac 2.0 Android Banker
In late 2021 ThreatFabric published a report about a new Android banking trojan they had observed being advertised and sold through forums. Calling itself ERMAC, they reported that it closely resembled the old Cerberus banker in terms of the codebase with only a few aspects of the obfuscation and encryption algorithms showing any significant differences. We visited the family not long afterwards and added some initial detections which covered the samples we’d observed.
A couple of months ago ESET Labs reported on Twitter they had come across a new Android trojan which they identified as an updated version of ERMAC. It comes with a significantly increased list of applications it can harvest data from but in general still shares the same functionality as the original - the main focus is stealing data relating to finance/banking and cryptocurrency apps. The campaign seen by ESET targeted users in Poland by imitating the popular Bolt food delivery service, and Cyble report that they have also seen it pretending to be a browser update delivered via malicious websites.
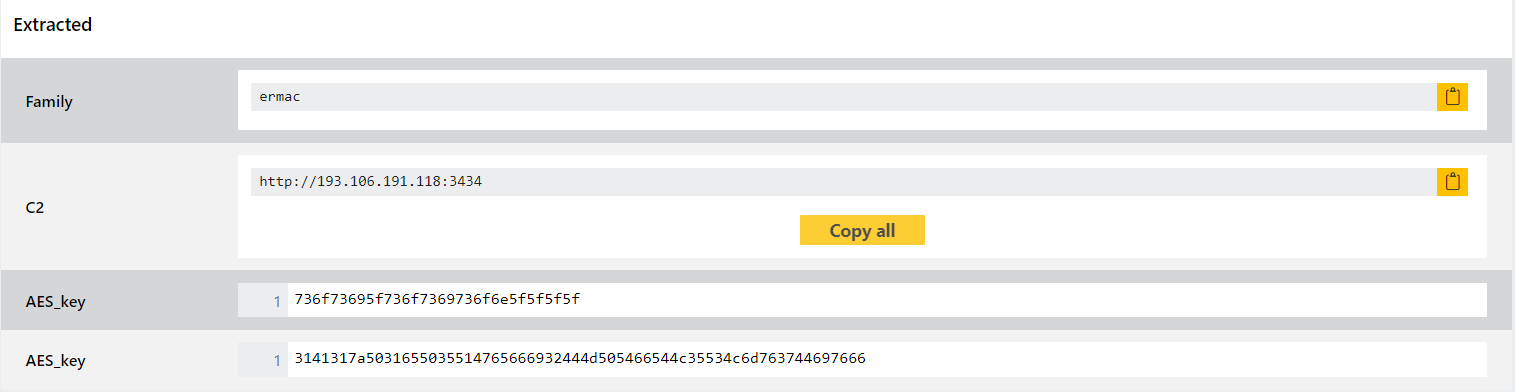
We have extended our existing detections for Ermac to cover the new version and to make sure the versions are marked clearly. We have also updated the configuration extractor.
Analyses:
Danabot
Danabot is a banking trojan/stealer which has been in widespread usage since mid-2018. The malware itself is modular including functions for browser injections/network sniffing, stealing credentials stored locally by a range of software, and remote access capability.
The family has gone through several iterations since it first released, and it has already appeared on this blog a couple of times in 2022. In this update we have addressed some issues with the configuration extractor we added back in May, in order to improve performance and address a couple of issues that popped up with some recent payloads.
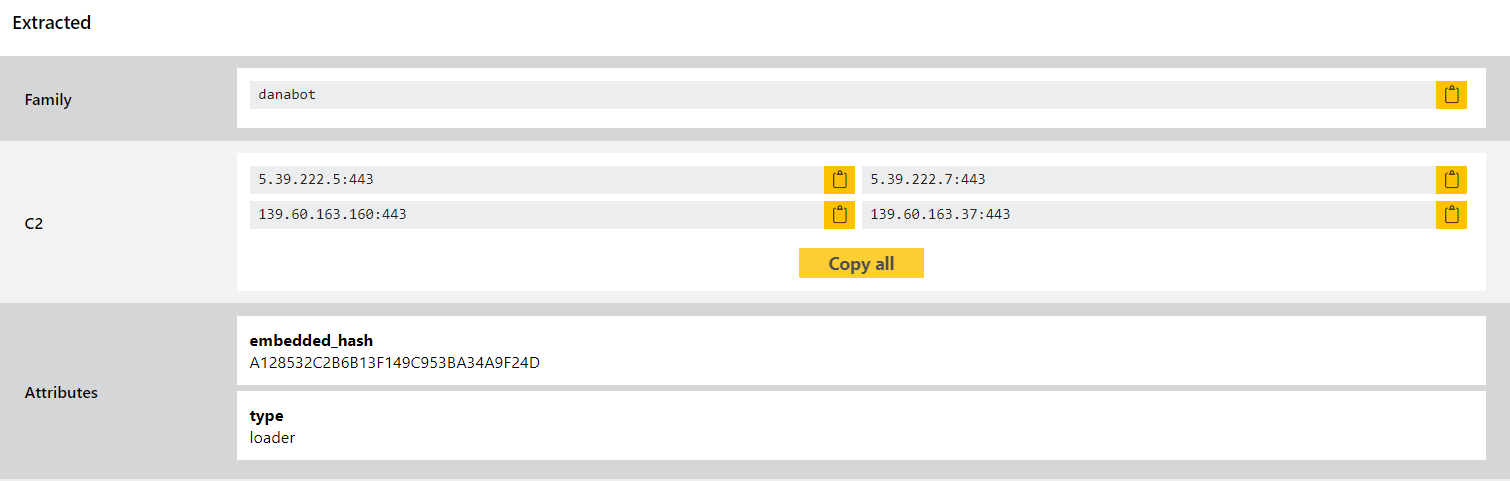
Analyses:
Vulturi Stealer
Vulturi is a straightforward stealer family that appeared in early 2021 and was reported by our friends over at SEKOIA.IO earlier this year. There is currently very limited public analysis of the family available but it seems to be a fairly typical infostealer capable of extracting data from a comprehensive list of software. It is sold through forums for anyone to use (or at least it was until the cracked version became available in June 2021).
We have taken a look at the samples shared by SEKOIA.IO and implemented detections and a configuration extractor.
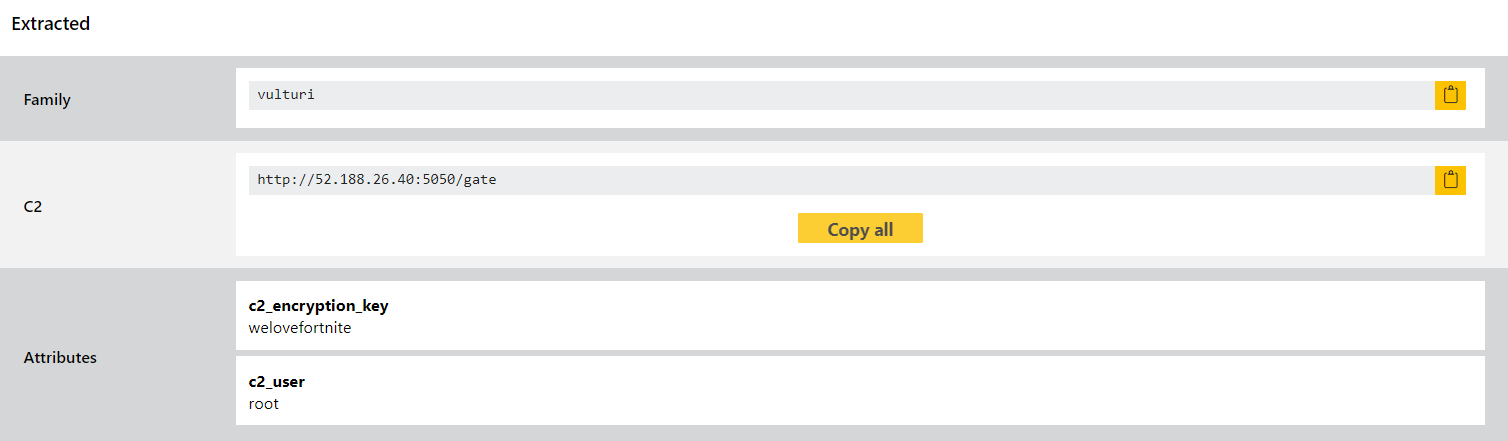
Analyses:
