Welcome to another week in our Triage Thursday blogs, in which we go over the major changes from the last few days. Today we have a couple of new additions to Triage’s list of supported families, plus a few updates to existing detections. We also have a new addition to our static processing:
- Added UPX unpacking to static analysis
- Updated Redline rules to cover undetected samples
- Added configuration extractor for BumbleBee
- Added configuration extractor for MetaStealer
- Updated detections for new Qakbot variant with anti-analysis features
- Updated rules for new Industroyer2 payloads
- Updated rules for Matanbuchus loader
As usual if you have any comments, suggestions or other feedback about Triage feel free to get in touch with us. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
UPX Unpacking
In general our approach to packers so far has been to deal with them at the behavioural phase, letting them to the hard work themselves and then creating process dumps once the plaintext version is available in memory. This does mean that often yara or our configuration extractors won’t find anything at the static phase, but for a sandbox where almost all samples are submitted for static and dynamic analysis it’s never been much of an issue.
However we would like to improve and expand our static processing wherever possible, moving nearer to it functioning as a kind of pre-screening step which can inform the decision of whether to take the time for a live run as well. Some aspects of that have been mentioned on this blog already, such as our x86 emulator used for families like Metasploit or Bazar; and our XLM macro parsing. As part of this process we have been exploring ways to improve packer handling, and so this week are pleased to be able to release UPX unpacking on the public cloud.
This is not just vanilla UPX handling, although the core of the functionality is built around that of course. It’s pretty common to see samples using UPX with slightly modifications which break the default binaries/parsers so we have attempted to cover as many of these as possible, taking quite a flexible approach to enable Triage to handle small deviations in the normal algorithm. Hopefully this should be quite a robust handler which enables us to significantly increase the number of detections at the static phase, but of course UPX is only one of the many packers used in the wild.
We have tested this extensively internally and look forward to seeing how it works in the wild. It will be on the public cloud only for a while for us to evaluate its performance, but once everything looks good it will be making its way over to the private cloud as well.
Examples:
Redline Stealer
Redline is no stranger to this blog, so we won’t take up your time going over the background in detail again. In short, it is a potent stealer with capabilities to extract content from a wide range of browsers, email clients, cryptocurrency wallets and other local applications on any infected systems. We have covered it many times over the course of the last couple of years as it is very actively developed, and regularly pushes new updates which require some tweaking to our extractors etc.
This week we noticed a subset of Redline samples that were not being covered by our detections, so this update is just aimed at addressing that. The samples are recent but not necessarily new variants etc., just things which had slipped through the net so far since there are so many different versions of the family. As always, we’ll continue to watch out for any new versions or undetected samples and will bring out more updates as required.
Analyses:
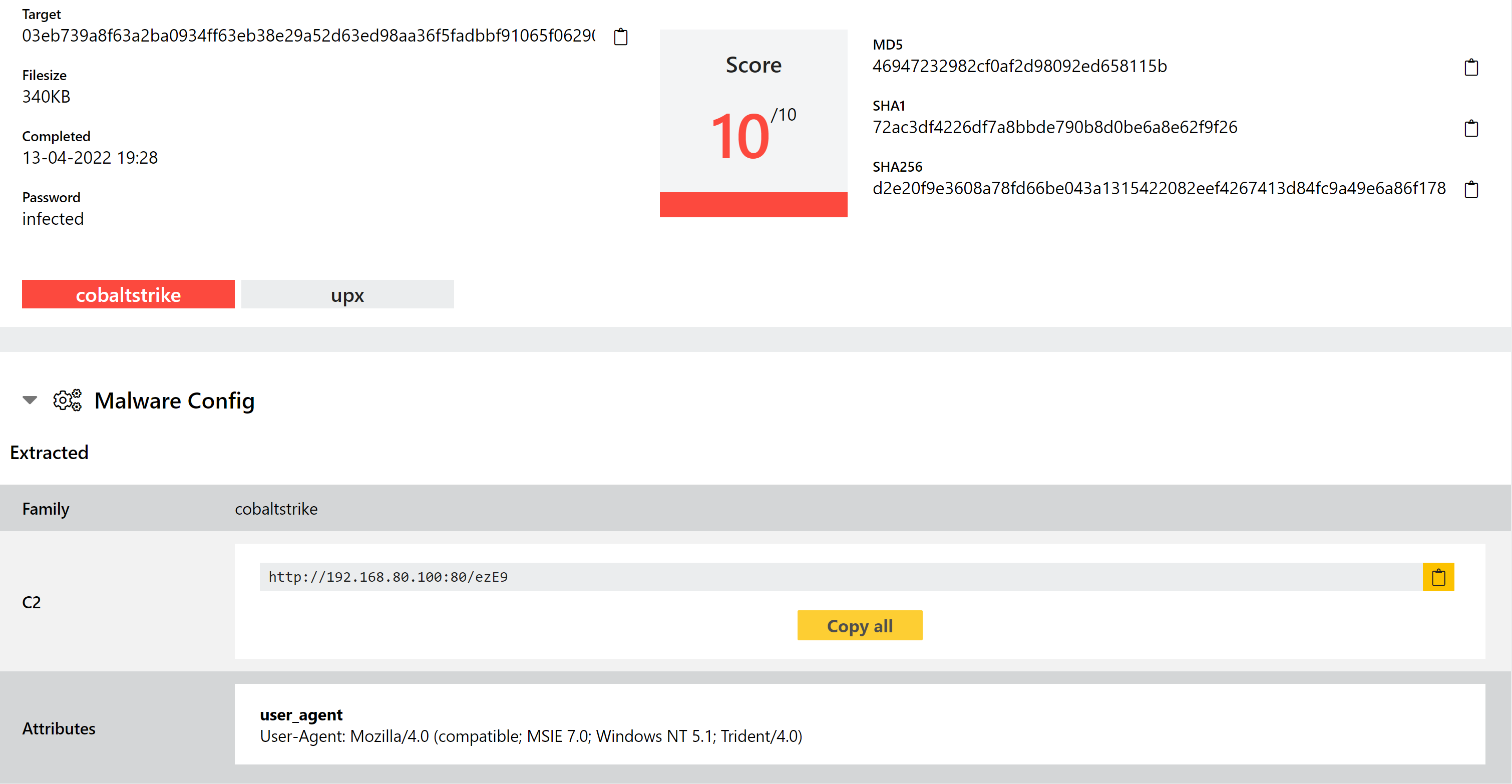
BumbleBee
BumbleBee - taking its name from the useragent string used in its C2 communications - is a loader component generally associated with an Initial Access Broker group who have worked with ransomware gangs like Conti. If you aren’t familiar with the term, and Initial Access Broker (IAB) is a group/person who makes the initial breach into a company, and then sells that access on to other groups to deploy their payloads. This is especially popular with ransomware groups as it reduces their wasted time and means they can tailor their own attack to the specific company and/or user to improve chances of receiving a ransom payment. In the case of EXOTIC LILY - the name assigned to this particular threat group - they seem to have ‘industrialised’ this process with a team of people carrying out manual (spear)phishing and social engineering to gain access to companies.
The family itself is a fairly typical loader - it uses WMI to harvest general information about the system and reports that back to the C2, which can issue it a task for the next stage. This task can vary but mainly revolve around deploying code and payloads onto the system. For a fuller writeup of the samples you can find a blogpost about it from Google’s Threat Analysis Group here.
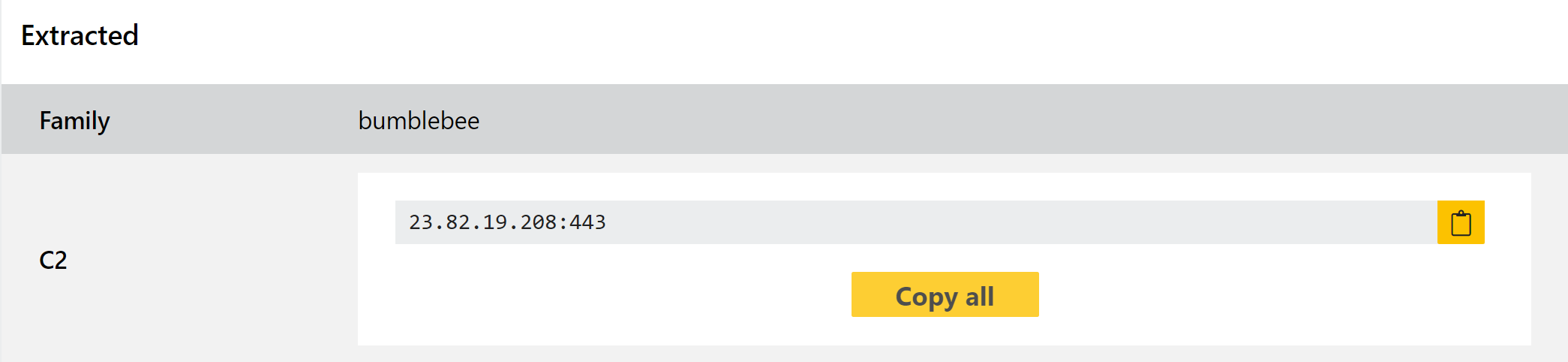
Although ransomware is certainly a focus of the group, they do deploy other things as well. Most recently BumbleBee was spotted distributing CobaltStrike payloads.
We have reviewed a number of available samples, and built out some detections and a dedicated configuration extractor to dump the C2 address.
BumbleBee
MetaStealer
Picked out by Brad Duncan of @malware_traffic fame, MetaStealer is an infostealer which is distributed via malicious Excel files sent as email attachments. The family uses the legitimate web services Github and transfer.sh to host and fetch the final payloads - an exe and DLL - to make the C2 traffic look more inconspicuous. The binaries are stored as data blobs which can be fetched quietly and converted into executables on the infected machine. You can find the full writeup on the samples here.
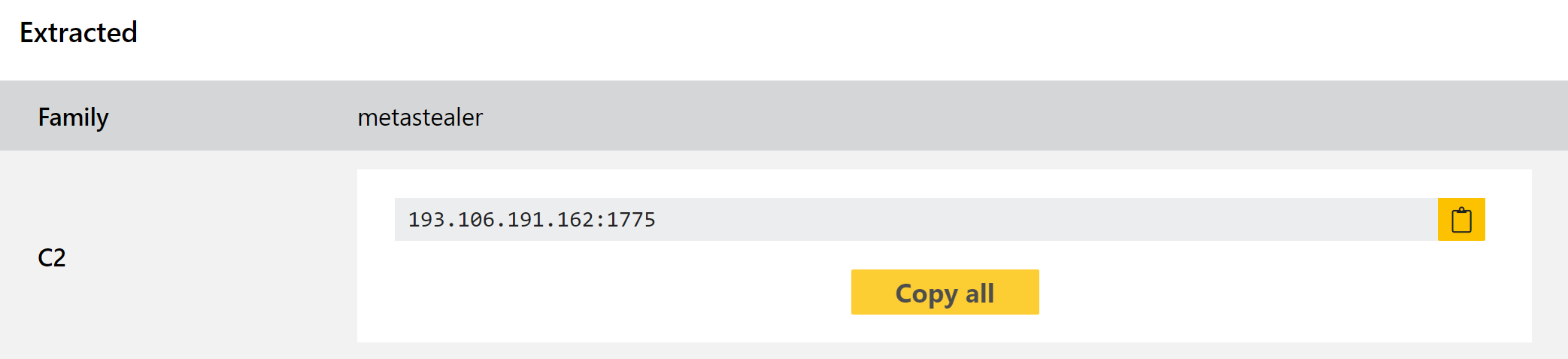
After gaining an initial foothold the samples appear to use the WinLogon registry keys for persistence, creating a new entry which launches the malicious payload via explorer.exe. It also checks the location as set in the registry, presumably to prevent executing on systems in CIS or other nations.
We have added detections and a configuration extractor for the family, which can dump out the C2 address being used.
Analyses:
Qakbot
Qakbot likely needs no introduction, but if you’re not familiar with the family it is a powerful infostealer/trojan which has been in use in various forms since around 2009. It has been repurposed for a few different roles over the years, including a banking trojan attacking Active Directory servers and a stint as a ransomware dropper.
Triage has long supported both behavioural detection and configuration extraction for the Qakbot family, but as an active and advanced threat it regularly requires minor tweaks to keep our signatures up to date. We recently spotted a new version that was taking some additional steps to complicate analysis, with garbage API calls to mislead investigations and some new IDs which weren’t covered by the configuration extractor. We’ve now updated to cover these properly.
Analyses:
Industroyer2
Triage has featured some static detection for Industroyer for a couple of years now, but the war in Ukraine has borught with it a whole raft of new variants and families, including some updates for Industroyer.
If you’re not familiar with the family it is a destructive piece of malware targeting certain industrial control systems (ICS), specifically those related to national energy grids. The initial version was revealed in late 2016 after an attack against a Ukrainian power company which cut of power to parts of Kyiv for a short period. Since the beginning of Russia’s full-scale invasion in February attacks like this have become more prolific, making use of a wide range of different wipers and other destructive malware including updated versions of the Industroyer payloads reported by ESET earlier this week.
We have reviewed the available samples and made some tweaks to our original rules to ensure they are correctly reported. Considering the active situation we expect to see more changes in future, so will continue to keep an eye on this and other families being used against Ukraine and will do our best to release new detections as soon as possible.
Analyses:
Matanbuchus
Matanbuchus appeared in early 2021, but only really began to make an appearance in the samples we saw around the end of the year. We added initial detections in our final blogpost of 2021 and revisited it again earlier this year when a new variant appeared, and today we’re checking in again to make a couple of minor modifications to cover a sample we found that was going unreported.
The family includes fairly standard loader functionality including loading and running executables directly in memory; using schtasks to add or modify tasks on the machine; and PowerShell execution of commands/scripts. In addition, if the user has no existing infection chain in place the developer can provide a standalone launcher for the malware to get it started. Advertised as malware-as-a-service, it can be rented out on a monthly basis by anyone looking to run their own campaigns.
Analysis:
