Welcome back to Triage Thursday! We have a smaller post this week introducing some new family classifications.
- Improved CobaltStrike configuration extraction
- Configuration extraction for new TrickBot samples
- ModiLoader signatures
- Ardamax signatures
- Family signatures for several ransomware:
Thanks to everyone who has been trying out the platform and sending us feedback. Since opening up registration last month over 250 new users have joined us, a fine increase from our earlier 100 registrations per month! We’ve released numerous updates over this time, the biggest being Android analysis support, but we have lot more planned to come. Watch this space!
CobaltStrike x64 Payload Support
Improvements have been made to Triage’s support for malicious CobaltStrike payloads, especially with regard to x64 versions. This should mean that configuration extraction works correctly on a wider range of variants than before.
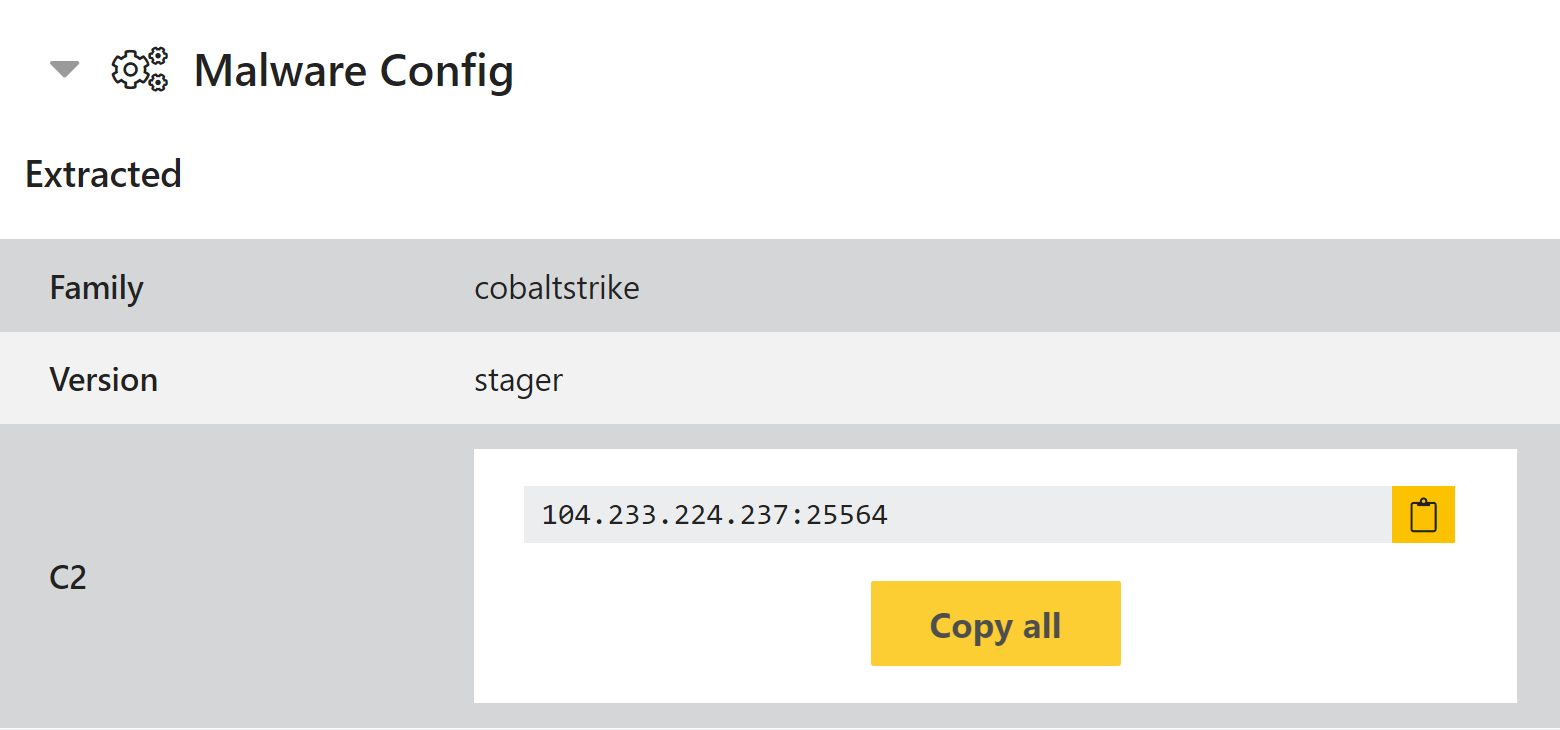
Analysis:
Configuration Extraction for New Trickbot
A new version of Trickbot was recently observed which had some changes which meant it didn’t trigger configuration extraction. This has been fixed and now supports the latest samples.
Analysis:
ModiLoader Family Signatures
ModiLoader, also known as DBatLoader or NatsoLoader, is a dropper first observed in June 2020. It is a 2 stage loader, and has been observed deploying Formbook, Netwire, and Remcos trojans.
A deep-dive on the first stage is available here.
Analyses:
Ardamax Family Signatures
Ardamax is a keylogger which can be bought for use through an ‘official’ website, presenting itself as a legitimate monitoring tool. It has limited capabilities compared to other stealers, only being able to capture keystrokes and screenshots, and is generally quite noisy.
Analysis:
Thanos Ransomware
Thanos is a ransomware-as-a-service which has been sold and marketed through underground forums since late 2019. It gained some attention in June 2020 when new versions added additional evasion and persistence techniques, including likely being the first to weaponise the RIPlace evasion technique to encrypt files without triggering anti-virus/anti-ransomware protections.
The ransomware itself does not run well in Triage, as it attempts to reboot the machine early in the process which ends the analysis before encryption takes place. However we have added static detection for the family.
Analysis:
Cyrat Ransomware
Cyrat was recently discovered by Karsten Hahn (@struppigel) posing as a DLL fixer tool for Windows. It is a compiled Python binary which includes a number of external resources, including the Fernet encryption library and the pyfiglet text rendering library.
A full breakdown of the sample can be found on the GData blog.
When submitted in Triage, the analysis fails due to missing the pyfiglet Python library. However we have added static detection for the family to circumvent this.
Analysis:
New Avaddon Version
Avaddon first appeared in June 2020, actively recruiting distributors through hacking forums to launch campaigns. A new version was recently observed which altered some of the characteristics and evaded our existing family signatures. These have now been updated to work correctly with this change.
Analysis:
HiddenTear Ransomware Variant
HiddenTear is an open-source ransomware which has been around in various forms since at least 2015. Another sample recently surfaced on Twitter which appears to be a modified version of the family - for example it does not appear to drop any ransom note like HiddenTear would normally.
Interestingly another version of the same binary was found a day later by @raby_mr. This appears to be the same file but packed using a demo version of Obsidium. Note that due to it being a demo version, a popup is shown during execution which must be closed to continue.
Family detection has been added for this variant, though due to the open-source nature of the ransomware it may have limited scope.
Analyses:
- 200903-xvmltld6ze (Non-packed)
- 200903-lr21ndnvna (Packed)
VashSorena Ransomware
VashSorena is a new variant of older ransomware families like Sorena and Ouroboros. A sample of VashSorena was recently submitted to Triage by @fbgwls245. Some initial signatures have now been added for the family to identify it.
Analysis:
