Welcome back to our Triage Thursday blog series, where we give a quick rundown of any and all updates made to the sandbox over the last week.
We’ve got a good few families to go through today, as well as the addition of a new file format to the list of supported types:
- Fix for Emotet configuration extractor (mostly related to Epoch4)
- Updated Pony stealer configuration extractor
- Updated IcedID handling for changes to the loader component
- Added new detections for the Outsteel and SaintBot families which have been used against Ukraine recently
- Added detections for the 44caliber stealer
- Added support for MHT files
As always, if you discover any issues or missing detections while using Triage please do send us feedback - it’s a big help in deciding what we should be prioritising. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account!
Emotet Fix
Emotet has been making tweaks again lately so this week we’ve had to make some updates to handle samples where the keys and botnet IDs were not being properly extracted. These issues were mostly with Epoch4 samples and were due to some overly strict parsing on our end - this has now been updated to account for a wider variation.
As always with this family we’ll continue to update as needed. We don’t expect it’ll be too long before it makes another appearance in the blog, and in the meantime a massive thank you to everyone who passes us samples like this.
Analyses:
Pony Stealer
Pony has been a staple of the malware world for years, going back all the way to 2011 for its first versions. Also known as Fareit, it is consistently one of the main choices for those looking for a stealer even now with powerful credential theft capabilities built in.
Like most infostealers it covers a range of software targets including web browsers like Chrome or Firefox; email clients like Outlook; common FTP applications; and of course cryptocurrency wallets. With such a long history there have been many different versions and variants over the years - especially after the source code for one version was leaked online - with each bringing new fixes, improvements, and expansions on the supported software and credentials.
The family includes some functionality to deploy additional payloads, meaning that it can form part of a larger infection chain leading on to other types of malware. Infected machines are also incorporated into a botnet which can be leveraged to mount further attacks.
Last week we updated our configuration extractor to support more versions and correctly dump their C2. There are some further changes to come in relation to our memory dumping strategies which should improve this further - we’ll provide an update on that when available.
Analyses:
IcedID
IcedID has appeared on this blog a few times so we won’t go into the background today. You can find some quick details in our previous blogpost here.
Last week we revisited the family to improve our handling of the core loader component, which seems to have gone through some changes lately.
Since then, we have also noticed some versions using a known time delay technique, presumably to make sandbox analysis more difficult. As you can see from the screenshots in our tweet below it seems to be leveraging API and instruction hammering to prevent any significant activity from taking place for several minutes. Since most sandboxes - like Triage - default to a timeout of 5 minutes or less this tends to cause benign results since nothing malicious was observed, and it also bypasses the main countermeasures in place which can e.g. intercept and skip calls to the Sleep or similar APIs.
We’re looking into technical solutions for this, but in the meantime we still get good analysis results if you just turn the timeout up to 10+ minutes.
Analyses:
OutSteel Stealer
OutSteel is a new malware family which was first spotted in early 2022. It was deployed in targeted phishing campaigns against Ukrainian organisations in the lead up to the invasion by Russia, as a continuation of a prolonged campaign which had been running since at least March 2021.
According to an advisory published by the Ukrainian CERT the family was distributed using mass email spam pretending to be from the National Health Service of Ukraine (although other sources have also been reported, such as the national Police force), with the payload itself distributed from a Discord download link. The targets appeared to be Ukrainian state organisations in general.
OutSteel itself is a file stealer, but clearly with a different focus than most mainstream families. Whereas most are looking to automatically hoover up as many different sets of credentials, cryptocurrency wallets, and other easily monetisable bits of data this family is interested in actual files, based on their file type. We have observed samples looking for .doc, .pdf, and .csv files mainly. The intention seems to be to collect sensitive information about these organisations which can then be analysed at the attackers’ leisure.
We have taken a look at files available from the last few weeks and implemented initial behavioural detections for them.
Analyses:
SaintBot
SaintBot was also brought to our attention by the current war in Ukraine, although it actually goes back quite a bit further than OutSteel above. It was first reported on by MalwareBytes in April 2021 being used against Georgia, another common target for Russian state-sponsored actors.
The family is a downloader often used to drop stealers - it has recently been delivering OutSteel mentioned above, and is flexible enough to feasibly deploy any type of payload. More details on the recent usage can be found in PaloAlto’s blogpost.
As with many other families currently it tends to use Discord as the download point for additional payloads, abusing the fact that these URLs are often trusted by security platforms due to their legitimate uses.
We have added some static and behavioural detections for the family, and will make any updates as needed.
Analyses:
44Caliber
44Caliber is another stealer, but with a more standard set of functionality than OutSteel above. It is open-source, first being made available on Github back in February 2021 with the usual nonsense about being for ’educational purposes only'.
Again, the family uses Discord for its communications, this time not just for downloading files but as a full C2 communication channel. Logs are sent back to Discord via the webhooks functionality as shown in the screenshot below, taken from the project readme file.
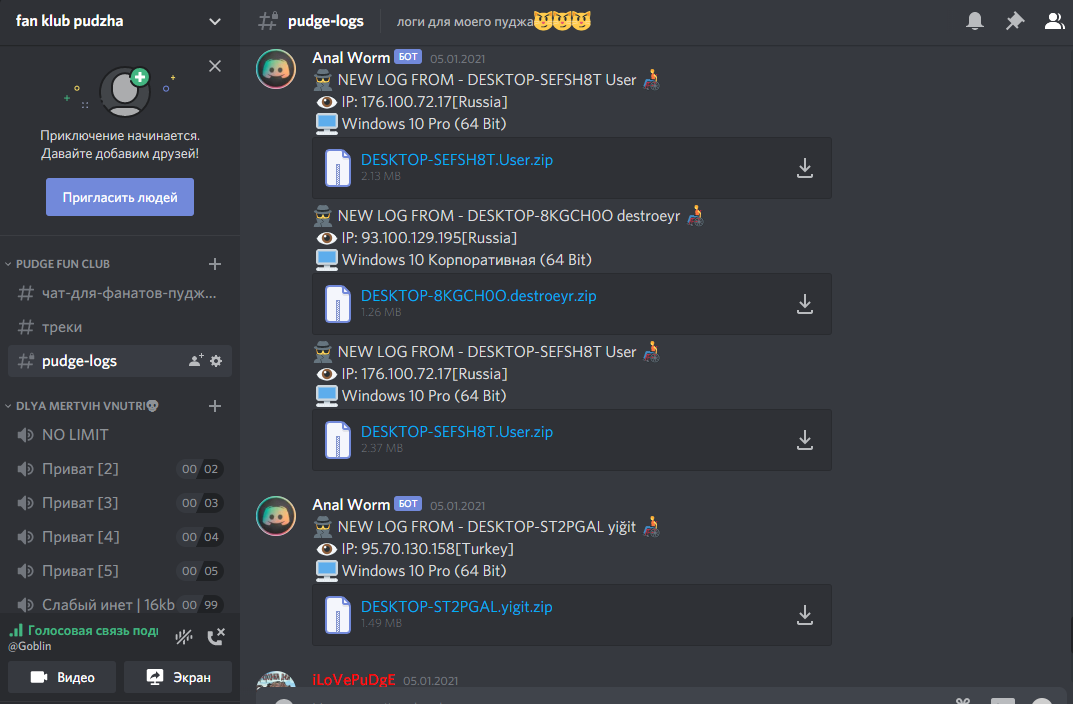
It is based on the older Reborn Stealer, which is also available open-source.
We have reviewed available samples and implemented detections and a configuration extractor which dumps the C2 details for quick access.
Analyses:
Added support for MHT files
MHT (or MHTLM) are a web archive format which can reproduce an entire webpage offline. It bundles up all resources normally accessed during page load like HTML files, images, CSS sheets etc. so that the page can be viewed at any time.
This format is generally used with a web browser or a dedicated HTML editor, but of more interest to us is the fact that they are also supported by Microsoft Word. This makes them a possible format for things like phishing attacks, which caused some of our users to request support for them to be added into Triage.
This has now been done, adding to the extensive list of formats already supported by Triage (you can find that list in our docs here - note that it hasn’t been updated for MHT yet but we will be fixing that soon).
