It’s been another busy week of updates for Triage, so join us for today’s Triage Thursday blogpost. Since the release of Search last week we have been working on a number of quality of life updates to help you get the most out of the platform, and have released improvements to static detection, IoC visibility in the UI, new integrations, and several more family detections.
The full changelog:
- Added URLScan Integration
- Added JA3/JA3S Support
- Updated DLL handling to support execution with regsvr32.exe
- Updated UI to show Campaign and Botnet tags
- Added new PlugX configuration extractor
- Added new AsyncRAT configuration extractor
- Added MountLocker detection
- Added NetSupport RAT Detection
- Added StrongPity Stealer detection
- Added Phoenix Keylogger detection
- Updated Dridex detection
- Updated Trickbot configuration extractor
- Updated SmokeLoader configuration extractor
- Updated Office yara rule causing false-positives on MSI files
- Updated M00ndev yara rule causing false-positives on some Hawkeye keylogger files
- Added fallback yara rule for DiamondFox
- Updated yara rule to improve Valak family detection
- Updated Raccoon stealer family signatures
- Added fallback yara rule for RevengeRat
- Added detection for CryptOne packer
If you discover any issues or missing detections while using Triage, please do send us feedback. It’s a big help in deciding what we should be prioritising. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account!
URLScan Integration
We announced in a previous blogpost that we were working on integrating URLScan reports into Triage. We are pleased to say that this is now available on the public server.
URLScan is a free service which carries out behavioural analysis targeted specifically at web pages. With this integration we hope to provide a more complete report on malicious webpages which may not exhibit behaviour we would associate with malware - for example exploit kits or fake login pages used in phishing campaigns.
How does it work?
Any analysis submitted as a URL - via the UI or API - will generate an additional task which contains the URLScan report.
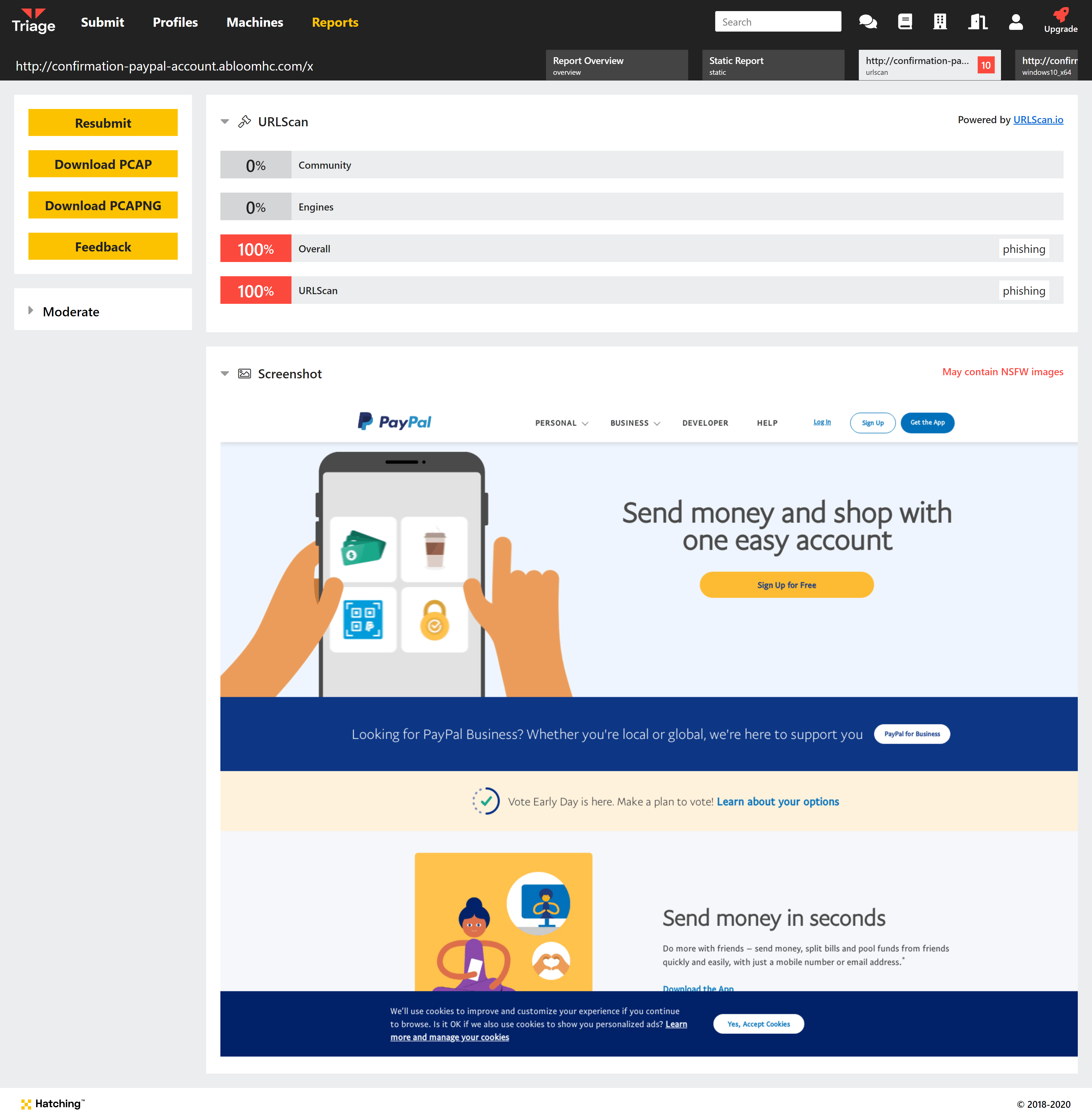
URLScan report for a fake PayPal phishing site
Triage will still run its own behavioural analysis of the URL alongside the URLScan output, and we hope that by combining these 2 sources we can provide much more robust reports covering a wider variety of web-based threats.
You can find an example URL analysis here: 201029-zrbh6kw9ca
Support for JA3/JA3S TLS Fingerprints
JA3 is a system for generating ‘fingerprints’ of SSL/TLS traffic which can be used to identify network communication where it follows repeated patterns, such as in malware C2. JA3 provides support for client-side fingerprinting, while its counterpart JA3S can do the same for server responses.
On the client side JA3 looks at the following data fields:
- TLSVersion/SSLVersion
- Cipher
- SSLExtension
- EllipticCurve
- EllipticCurvePointFormat
For server responses JA3S includes the following fields:
- TLSVersion/SSLVersion
- Cipher
- SSLExtension
The fingerprint for network communications is available in the network section of report_triage.json, which is accessible through the API. An example Curl command to view this directly is shown below:
curl -H 'Authorization: Bearer <YOUR_API_KEY>' \
https://api.tria.ge/v0/samples/201029-6tkmnbakx2/behavioral1/report_triage.json \
jq .network.flows
{
"id": 14,
"src": "10.10.0.90:51462",
"dst": "104.18.62.171:443",
"proto": "tcp",
"pid": 4164,
"procid": 75,
"first_seen": 10507,
"last_seen": 11177,
"rx_bytes": 435018,
"rx_packets": 331,
"tx_bytes": 8155,
"tx_packets": 169,
"protocols": [
"tls",
"http"
],
"domain": "enjoymylifecheryl.com",
**"tls_ja3": "3b5074b1b5d032e5620f69f9f700ff0e",**
**"tls_ja3s": "466556e923186364e82cbdb4cad8df2c",**
"tls_sni": "enjoymylifecheryl.com"
}
Now that this system is in place we will also be expanding on it internally in the future, implementing signature detections which take JA3 fingerprints into account.
RegSvr DLL Support
Up until now, if Triage detected a submission as a DLL file it would launch it using rundll32.exe. This worked fine in most cases, but we have been increasingly aware of examples which instead expect to be run via regsvr32.exe. These include many of DLLs associated with the Trickbot family, as well as others such as IcedID and ransomware like MountLocker.
We have now extended DLL detection to include a check of the exported functions - the presence of the DLLInstall and DLLRegisterServer exports indicates that the file is designed for execution with regsvr32.dll. Our VM agent will then take this into account and launch them using the correct handler.
Analyses:
- Trickbot: 201029-vsztnfplge
- MountLocker: 201029-wrhynhybq6
- IcedID: 201029-hwm8rpqmhx
UI Update: Botnet and Campaign Tags
Earlier this week we deployed an update for the web interface to display campaign and botnet tags directly through the UI.
These tags are assigned by our configuration extractors and family signatures based on the file contents. They are particularly useful for families such as Trickbot, Emotet and ZLoader where differentiating between campaigns can be useful for tracking.
The tags are also searchable. You can click on the tag in the UI to create a search directly, or use queries like:
Updated Trickbot Configuration Extractor
We observed a variation of Trickbot which was not being properly handled by our configuration extractor. We have analysed the sample and implemented some improvements to better support these variants and ensure that they are extracted fully.
Analysis:
Updated SmokeLoader Configuration Extractor
It was recently reported to us through feedback that some Smokeloader analyses were reporting incorrect values for the fields dumped by our configuration extractor. This has now been fixed, and all extracted information should be accurate. If you come across any further issues like this please do notify us and we will address it.
Analysis:
PlugX Configuration Extractor
PlugX, also sometimes called Korplug, is a RAT with a long history. It is known to have been around since 2012, although TrendMicro suggest that the developers have been running similar malware as far back as 2008.
PlugX has all the features of a remote access tool and stealer, capable of uploading and downloading files, keylogging, capturing images through attached webcams and running a full cmd.exe shell which can be used by the attacker to execute further commands.
We have implemented static detection for the family and added a configuration extractor which dumps C2 URLs and attributes.
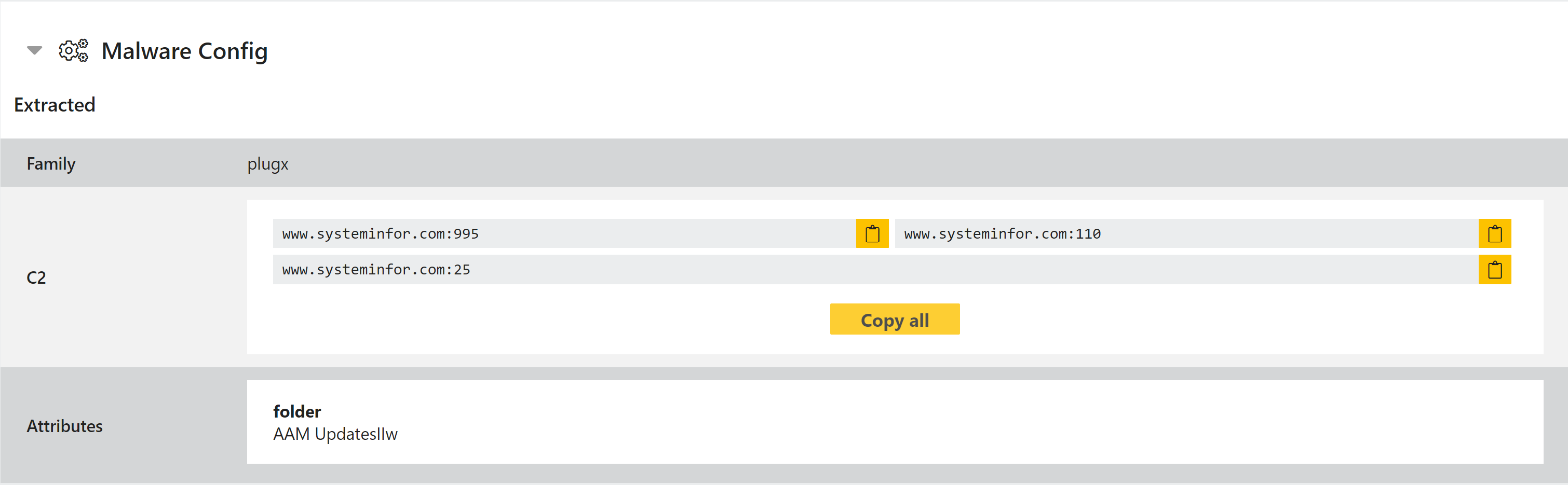
Analyses:
AsyncRAT Configuration Extractor
AsyncRAT is an open-source RAT available on Github. As is common with these, it claims to be for legitimate remote administration only and includes legal disclaimers about malicious use in the repository, but as usual this doesn’t prevent anyone from misusing it.
Triage has included general family detection for AsyncRAT for some months. However we have now also added a configuration extractor which dumps information like version number, C2 IP/URL, mutex name, installation path, and various module settings.
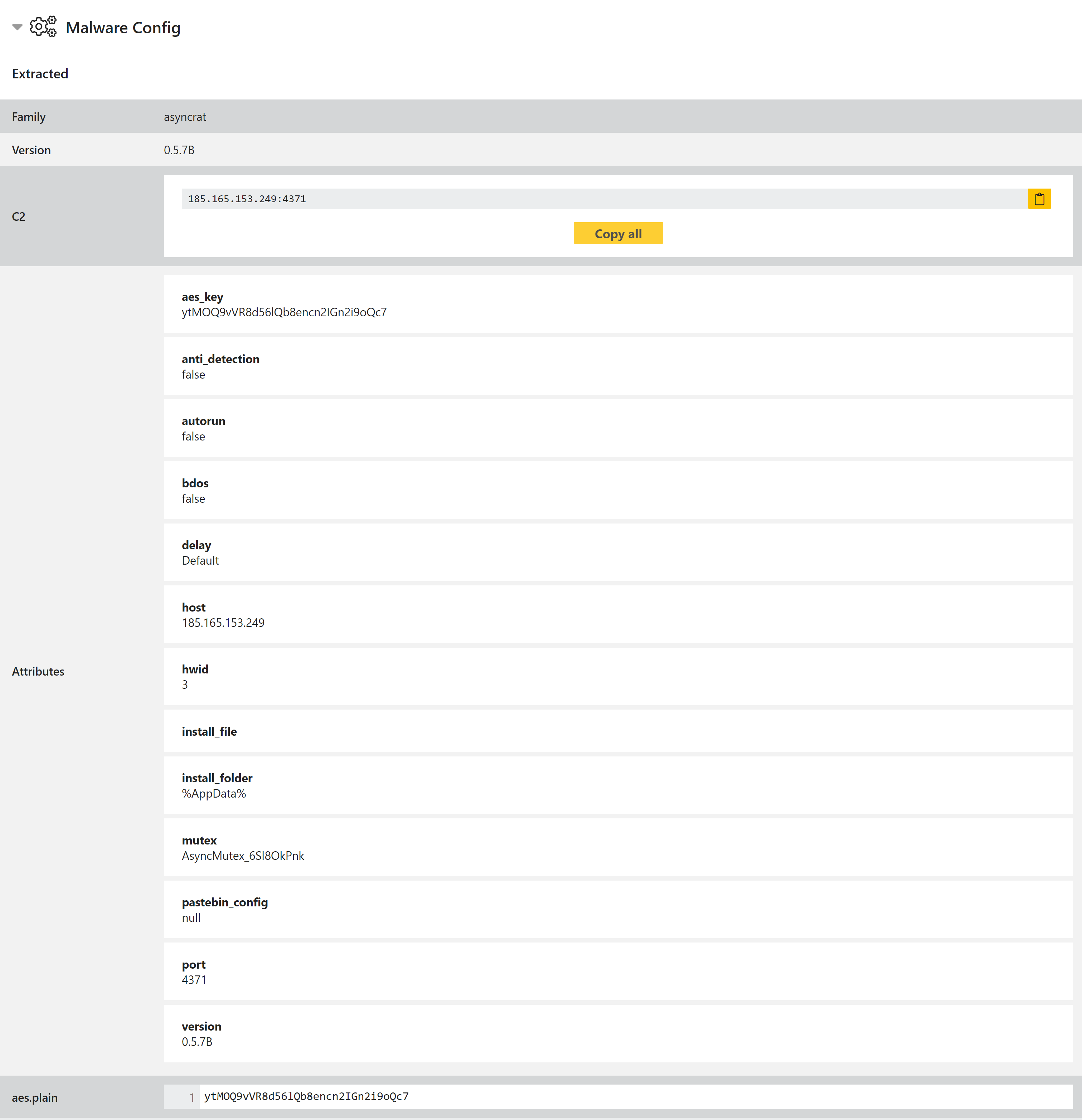
Analyses:
Updated Dridex Detection
We recently observed a version of Dridex which was evading our detection due to some differences in the file structure. We have now extended support to also catch these and process them correctly.
Analyses:
MountLocker Ransomware
MountLocker is a new ransomware family which was first spotted in July 2020. It follows the recent trend of including data exfiltration capabilities as part of its extortion method - data is released publicly through a web page if the ransom is not paid, in much the same way as groups like Maze.
This family was also affected by the regsvr32 change mentioned above as the sample obtained is a DLL not supported by rundll32.
Now that the family runs properly we have implemented detection for it at the static and dynamic stages, as well as extraction of the HTML ransomnote (note that for now the note is not dropped automatically here, but needs to be opened manually to trigger the extractor).
Analysis:
NetSupport RAT
NetSupport is a legitimate remote administration tool (strange how often I write that in malware-related blogposts) which is often abused for malicious purposes. It gained attention in May 2020 when Microsoft identified a large phishing campaign which deployed NetSupport, using COVID-19 related lures.
We have now added signatures to detect this family in Triage.
Analyses:
StrongPity Stealer {strongpity}
StrongPity is an APT which has been involved in many campaigns over the years. In 2016 they began to make use of an advanced stealer which was initially distributed through compromised software downloads.
We have added detection for a number of samples submitted to Triage recently, including a yara rule to cover samples which are unable to successfully contact their C2 infrastructure. We will continue to keep an eye open for new samples from this group and extend detection as required.
Analyses:
Phoenix Keylogger {phoenix}
Phoenix is a keylogger sold through hacking forums which was first reported in the summer of 2019. In its initial form it was a fairly limited keylogger but has since added a range of stealer functionality. This includes common activity such as dumping local passwords from browsers, email clients and FTP software. It also includes basic evasion by killing processes from a preconfigured list.
We have implemented family detection for the stealer, including static yara support.
Analyses:
