Welcome back to our Triage Thursday blog series! We have updates and improvements for quite a few families today, including a few we mentioned last week on Twitter but are including again here for those of you who don’t follow us there.
Let’s get straight into it:
- Added ’email_to’ field to Matiex and SnakeyKeylogger extractors
- Added support for PurpleFox
- Added support for MarsStealer
- Added extraction of authentication key for Redline stealer
- Expanded TargetCompany ransomware detections to cover other variants
- Added support for Koxic ransomware
- Updated DCrat detections for new variant
- Updated Matanbuchus loader rules for new variant
- Updated Vidar detections for new variant
As always if you come across any issues, have feedback about the platform and its detections, or just have some bright ideas for improvements, then you can always reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account!
Added email_to field extraction for Matiex and SnakeyKeylogger
In our previous blogpost we updated the AgentTesla configuration extractor to include the email_to field, which is part of the the SMTP settings embedded in certain variants.
Based on feedback our team has now expanded this support to 2 other families which also leverage SMTP for exfiltration and C2 communication. The configuration extractors for both Matiex and Snakekeylogger have been updated to include this data in their results, which should be a helpful IoC for easily tracking individual campaigns.
Remember that if you have access to the API, you can easily access the contents of any configuration extractor results under the extracted JSON key.
Analyses:
- 220128-zlgaeadef8 (Matiex)
- 220131-wgbmksaehp (SnakeKeylogger)
PurpleFox Rootkit
PurpleFox is a fairly new rootkit, samples of which were first picked out by MalwareHunterTeam and JAMESWT on Twitter.
The family can carry out a full infection with its own custom dropper being used to deliver the actual rootkit. It is extremely modular, breaking the infection chain into small pieces which are, on their own, often quite unlikely to be detected by standard AV tools.
As an additional step is its attempt to appear legitimate, the samples observed so far drop an actual installer for the Telegram desktop app along with the malicious payload, and the loader itself uses icons and file information to try and imitate Telegram.
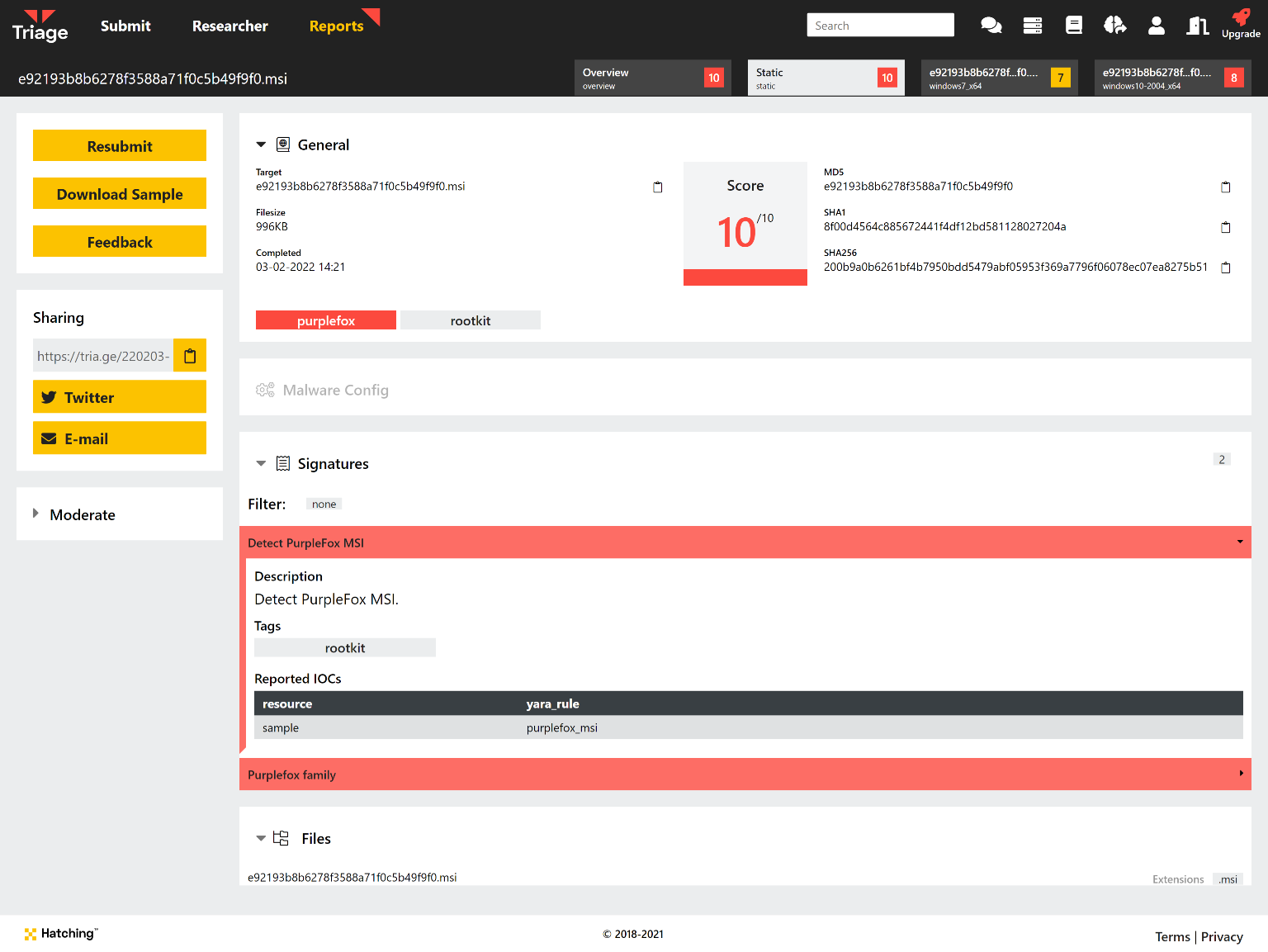
You can find a detailed write up of the family and its various stages in a blogpost by Minerva Labs here, published in early January. We have reviewed the samples available and implemented some initial detection for the dropper/loader and rootkit stages, and will continue to keep an eye on the family going forward.
Analyses:
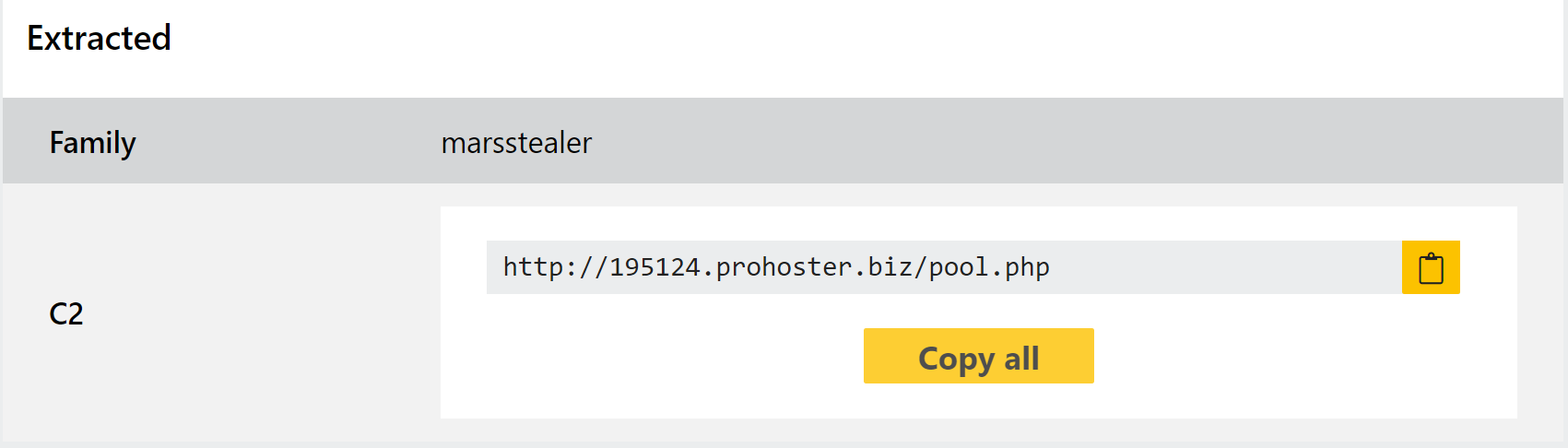
Mars Stealer
Mars Stealer was first spotted on Russian forums around the middle of 2021, being promoted as having the ability to steal saved credentials from a wide range of web browsers as well as a large number of cryptocurrency wallets.
The focus on cryptocurrency sets this family apart from many of the other infostealers currently available - although it is not unusual to steal some of the more common wallets when available, Mars covers a significant number of products and can bypass some of the techniques used to secure them.
According to a blogpost by the researcher 3xp0rt Mars Stealer is an updated version of the old Oski trojan which was shut down by the developers back in mid-2020. According to them the code base is very similar but with a few notable additions, like the extra cryptocurrency functionality and some more anti-debugging/anti-analysis checks.
We have reviewed the available samples and added detections and a configuration extractor for the family, which can dump the C2 URL being used.
Analyses:
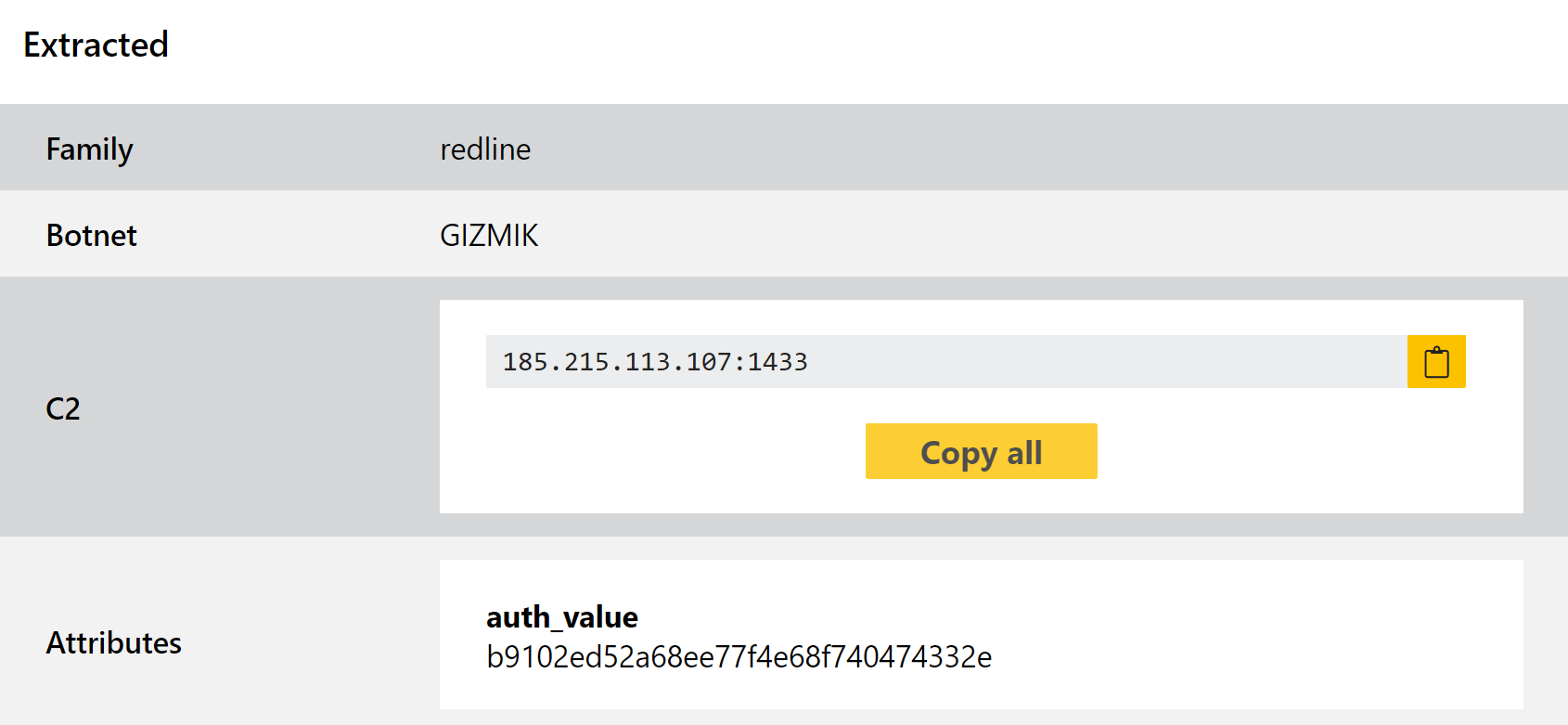
Redline Stealer
At this point Redline likely needs no introduction, as the infostealer has been one of the most widespread threats of the last year or more. We have mentioned it multiple times on this blog as new versions and variants have needed tweaks to our detections, most recently at the start of this year.
It has recently also gained attention in the news again as it ran a campaign around the end of January where the payload was presented as a Windows 11 upgrade installer. It was distributed via a website closely imitating the look, feel and URL of the actual Windows 11 upgrade page.
We aren’t introducing a new version today, but rather a small improvment to our extractor to add some new data output. In some of the newer variants a specific field is used in securing communications with their C2 infrastructure, functioning as a token to authenticate with the server before receiving commands, additional payloads, etc. Triage’s configuration extractor will now dump this along with the existing C2 fields.
Analyses:
TargetCompany Ransomware
At the end of 2021 we added support for the TargetCompany ransomware which had first been observed in the middle of the year. A fairly straightforward family it appears to be very much intended for manual, targeted attacks against companies rather than general distribution in large-scale campaigns.
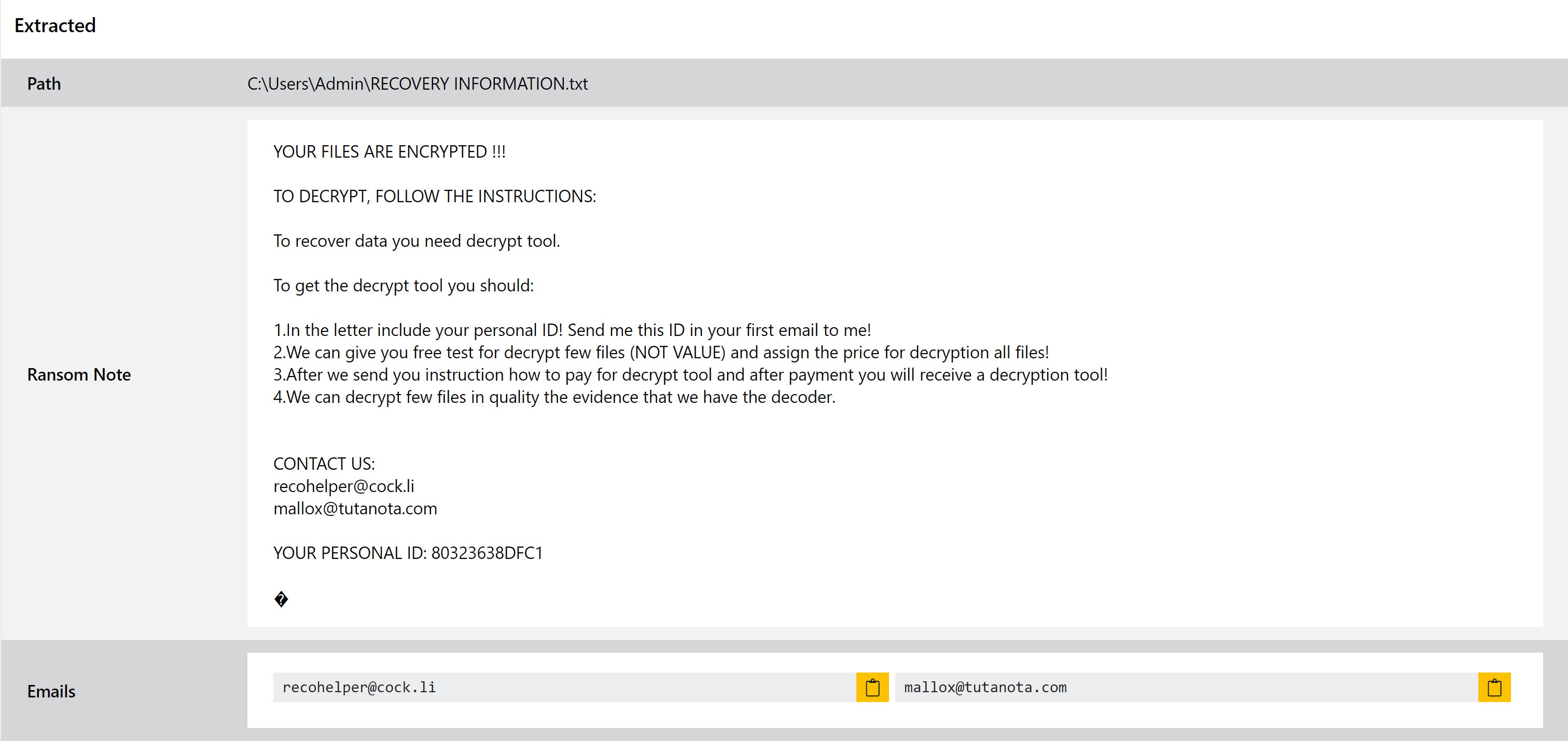
Since initially looking into the family the Mallox variant has also popped up, reported initially as a completely separate family but quickly identified as a new version of TargetCompany. This version is different enough that it was not being tagged by our family definitions, so this week we’re deploying an update to address a couple of the available samples and widen the detections to better support the whole family.
Analyses:
Koxic Ransomware
Koxic is a new addition to the ransomware landscape first reported on at the start of this month in a technical blogpost by Cyble.
It follows very familiar patterns for other families: disabling security features and software, deleting backups, shutting down any software that may interfere with file operations, and then encrypting the contents of the filesystem. Before encryption it also harvests system and user information from the infected machine.
We have checked available samples and made sure they are handled properly by Triage for ransomnote dumping and general behaviour. We have also added some specific family definitions to identify it easily.
Analyses:
DCRat
DarkCrystal RAT, more commonly known as DCRat, was first reported in late 2019. It provides an extensive set of remote administration functions triggered by specific commands received from the C2 server. These range from file upload/download, keylogging, and data theft, to gimmicks like opening and closing the CD drive or interacting with the Windows speech synthesizer. In addition to the built-in commands it can also run shell commands directly and pipe the output to the remote C2 server.
A detailed analysis of the family can be found in a report by Mandiant from May 2020, in which they breakdown some samples and all their supported commands.
We recently observed some samples of a new variant which were not being properly detected by Triage. We have now reviewed these and made some improvements to our behavioural signatures.
Analyses:
Matanbuchas Loader
In our very last blogpost of 2021 we introduced support for the Matanbuchus loader, a family which had been around on forums since February. Operated on a malware-as-a-service model it appears to have gained some popularity and we saw quite a few samples submitted through November and December 2021.
The family includes fairly standard loader functionality including loading and running executables directly in memory; using schtasks to add or modify tasks on the machine; and PowerShell execution of commands/scripts. In addition, if the user has no existing infection chain in place the developer can provide a standalone launcher for the malware to get it started.
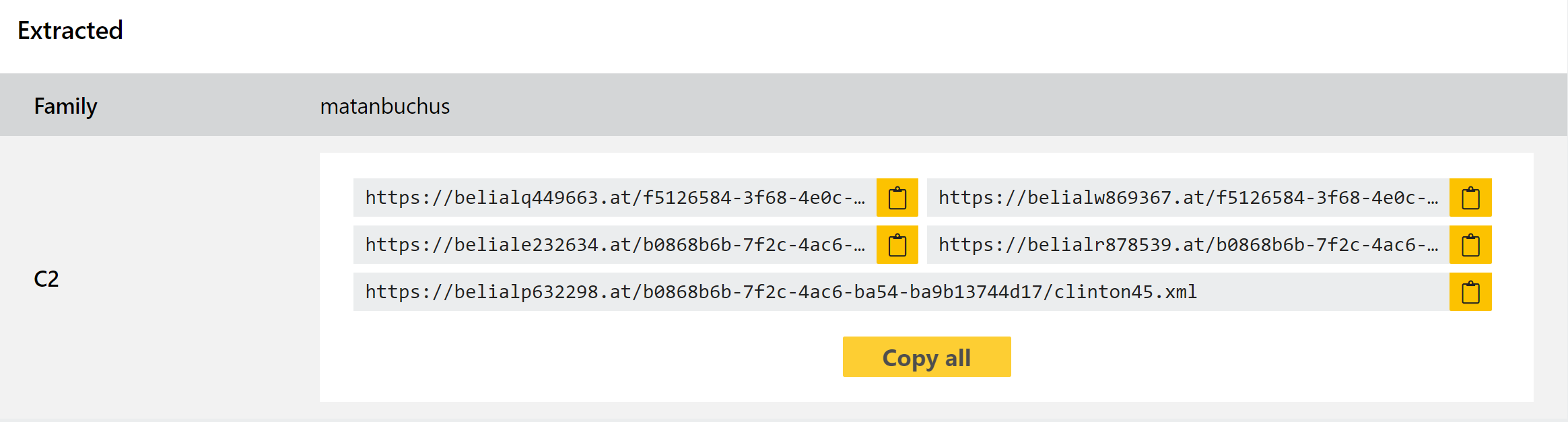
We added detections and a configuration extractor with that past blogpost but we recently observed a variant with some new modifications which were evading dumping. We have now addressed these and the family should be fully supported, but as always we’ll be keeping an eye open for any new updates.
Analyses:
Vidar
Vidar is back on the menu this week due to a new variant that’s been observed in the wild. It wasn’t working properly with our detections and extractor so we have made some tweaks that resolve those issues and ensure that the family is handled as expected. Some examples of this new version are provided below for reference, and others can be found by searching based on the family name and/or botnet ID.
If you’re not familiar with the family you can find more detail in our blogpost from July 2021 where we initially introduced the configuration extractor.
Analyses:
