We’re back to Triage Thursday this week after a short break, with plenty of detection updates for you to take a look at. You may already have noticed some of the changes we’ll go over today, as we’ll be covering things which were deployed last week as well, but we’re sure there will still be a few things in here you haven’t spotted yet!
The focus is on detection updates this week, with the following changes available:
- Added signatures for Neshta file infector
- New detections for XtremeRAT
- Added rules for SOVA Android banking trojan
- Improved handling of Arkei stealer
- Updated configuration extractor for AsyncRAT
- Added static detection for AmmyyAdmin
- Added additional signature for Elysium Stealer
- Added rules for Darkcrypt and Lockfile ransomwares
- Updated Danabot signature
If you discover any issues or missing detections while using Triage, please do send us feedback - it’s a big help in deciding what we should be prioritising. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Neshta File Injector
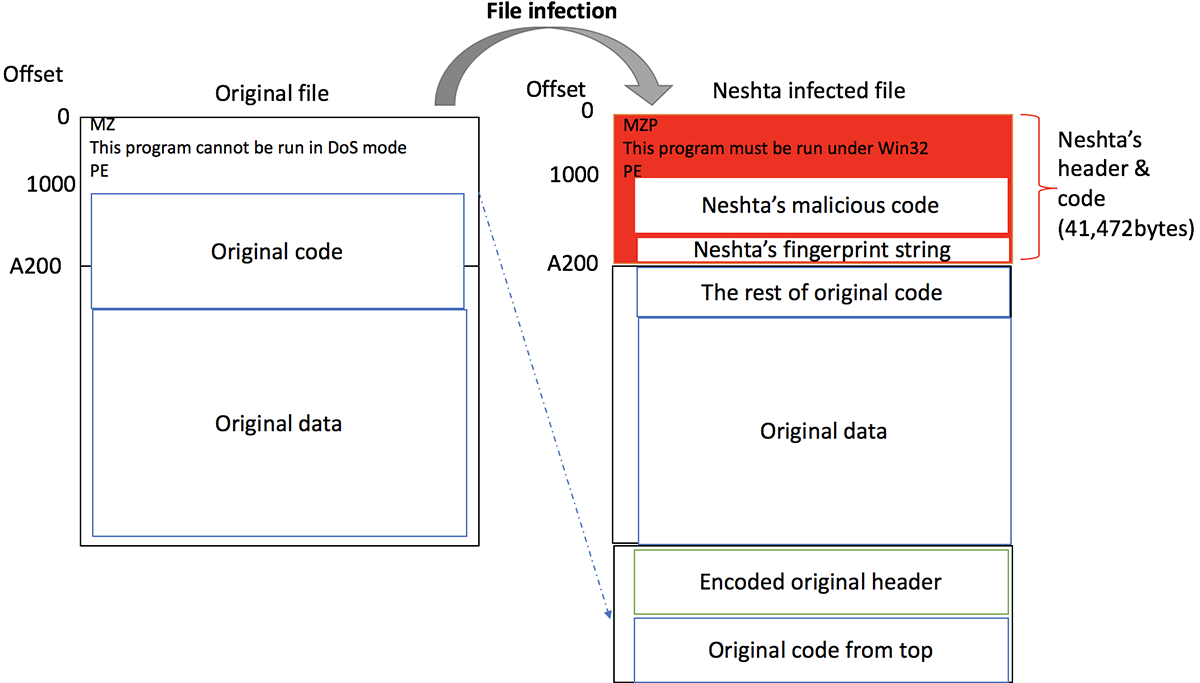
Neshta belongs to a class of malware which is fairly unusual these days, having been mostly replaced by more up to date infection methods. Known as file infectors, they overwrite sections of executables on the targeted system so that the malware is run every time one of these legitimate binaries is executed.
Nestha itself goes all the way back to 2005 and was created by developers in Belarus using Delphi. It overwrites the first 41,472 bytes of infected files with its own code, effectively completely overriding the original functionality.
Credit to Blackberry Cylance/Tatsuya Hasegawa: https://blogs.blackberry.com/en/2019/10/threat-spotlight-neshta-file-infector-endures
In addition to the file infection functionality, Nestha also ensures persistence by adding a registry entry which causes Windows to launch the malware binary whenever an executable file is run. It renames itself to svchost.com and enters a registry key to abuse the “Open With” functionality of Windows to sideload itself before any executable is run. To avoid multiple instances of the malware being active simultaneously it creates a mutex to track when a copy is already running.
Analyses:
XtremeRAT
XtremeRAT is another family written in Delphi, and shares sections of its code base with some other families which popped up around the same time such as SpyNet, Cerberus and Cybergate.
Thought to have first appeared around 2010, XtremeRAT is a fairly standard stealer with functionality you’d generally expect from this kind of family:
- Direct interaction with infected systems via remote shell
- Upload or download files
- Terminate running processes and services
- Capture screenshots
- Record audio and/or video from connected webcams and microphones
A detailed analysis of the family can be found in Fireeye’s 2014 blogpost about it. It is still actively used in 2021, and we have this week taken a look at some recent examples in order to implement detections to properly classify them using static and behavioural signatures.
Analyses:
SOVA Android Banker
Earlier this month ThreatFabric announced a new Android banking trojan they had detected in the wild in early August. They named it SOVA based on the name its own creators use, and which was found in the C2 panel by researchers.
Believed to still be in the early stages of development SOVA follows many of the patterns now common in Android malware, centred around using overlay attacks to intercept information being entered into certain sensitive apps like mobile banking and payment programs. It additionally deploys a keylogger to intercept credentials more widely, and can use fake notifications to encourage infected users to take additional actions and grant further access. In addition to this, ThreatFabric reports that it includes a more unusual capability to dump and steal session cookies, granting access to valid sessions without needing credentials at all.
According to the roadmap set out by the developer of SOVA, future updates will see it expand its functionality to also include ransomware modules, DDoS support, and man-in-the-middle network interception.
We have taken a look at the samples identified by ThreatFabric and implemented our own initial detections. Bearing in mind that this appears to be early in development we’ll also be monitoring for any new samples in future and will make adjustments as required.
Analyses:
Arkei Stealer
Arkei is not a hugely common sight these days, having been mostly surpassed by its younger spinoffs Vidar and Baldr. However it still shows up from time to time, and we recently observed a sample on Triage that wasn’t properly detected which prompted us to include it in this week’s updates.
The family is a fairly typical infostealer, having first gained attention in mid 2018 embedded within legitimate software packages available on Github. It focuses on data stored on the local filesystem, exfiltrating browser information (saved passwords etc.) and cryptocurrency wallets.
Analysis:
AsyncRAT
AsyncRAT is an open-source RAT available on Github. It claims to be for legitimate remote administration purposes only, but is commonly used by criminals looking for an easy to use, adaptable RAT.
We added a configuration extractor for the family back in October 2020, but we recently observed a slight change in samples submitted to Triage which was causing it some issues. We have now reviewed it and made some changes which should make it far more reliable, especially regarding the extraction of botnet IDs. These samples also included a change to the way they handle their salt values, used in C2 communications, so we have adjusted to now extract these dynamically to better support the new approach.
Some examples of the new variant are listed below for reference.
Analyses:
AmmyyAdmin
AmmyyAdmin is a remote administration toolkit which has, for many years, been developed as an easy-to-setup solution for individuals and companies. Quite unusually for RATs, this one actually is intended for legitimate use and over the years the developers have attempted to take steps to curb malicious usage, but this has not stopped it seeing widespread popularity as a tool for cold-call scams and similar. It is also sometimes used on its own as an automated payload.
The codebase has also formed the foundations of other malware families like FlawedAmmyy, which used leaked sourcecode to build a stealer using some of the advanced features contained within the original software.
We are generally more interested in genuinely malicious software, and Ammyy’s design means that unmodified versions of the software are rarely used as-is in malicious campaigns, but we have this week added some static detection based on recent submissions to Triage in order to clearly mark when it is identified in an analysis.
Analyses:
ElysiumStealer
Elysium Stealer - previously known as Zeromax - was reported via Twitter in July 2020 by @3xp0rtblog.
It is mainly oriented towards the theft of financial information, targeting web logins for common banking and ecommerce websites.
We recently noticed some samples being shared on Twitter which resembled Elysium but with a few minor changes that were evading our signatures. We have now addressed these and the family should be properly detected again.
Analysis:
Lockfile Ransomware
Initially reported by researchers at Sophos, LockFile was first observed in July 2021 leveraging the ProxyShell vulnerability in Microsoft Exchange servers to gain initial access to networks. After a foothold has been gained, it then uses an NTLM relay attack to spread throughout the domain.
The family includes a number of interesting features which somewhat set it apart from many other ransomwares, which have a tendency to be rather straightforward. Chief among these is a unique encryption system designed to evade common ransomware protection solutions: instead of encrypted the entire file contents, LockFile only encrypts every other 16 bytes. Sophos refer to this technique as ‘intermittent encryption’, and as the end result is far more similar to the original document than if the whole thing had been encrypted it can allow the family to slip by ransomware protection which checks the entropy of file buffers during writing.
It also attempts to minimise the file operations carried out during encryption by leveraging a technique called memory mapped input/output, which effectively allows the encryption to take place entirely in memory with just a single write operation to flush it to disk once complete. This approach is still unusual but has been observed before in families like WastedLocker and Maze.
Finally, LockFile also operates entirely in isolation without and C2 communications. This again helps it avoid detection by reducing the general noise it makes during infection and limiting the places it could be detected by analysts or monitoring solutions in a live environment.
A detailed breakdown of the family can be found on Sophos’s blog here.
Analyses:
Darkcrypt Ransomware
The exact ancestry of DarkCrypt is a little foggy, but it seemingly goes back to WannaCryFake samples seen in early 2020. According to Michael Gillespie - the creator of ID Ransomware - it and several other minor families are little more than reskins of a family which imitated the well known WannaCry campaign, with only minor changes around the encryption and key generation functions.
We have added some initial signatures to classify the family, and ransomnotes etc. should be extracted as normal.
Analysis:
Danabot
Danabot is a banking trojan/stealer which has been seen in widespread usage since mid-2018. The malware itself is modular including functions for browser injections/network sniffing, stealing credentials stored locally by a range of software, and remote access capability.
The family has gone through a few changes over the years, with some significant new versions being observed throughout 2021. It has featured in our update blogposts a few times recently as modifications have meant we’ve had to update our signatures and configuration extractor, and it’s back this week with some more minor tweaks to make our support more robust and reliable. We’ll continue to monitor samples and make any changes as required.
Analyses:
