Is it too late to say Happy New Year? Probably, but Happy New Year anyway. We’re back this week with the first Triage Thursday update blog of 2021, and it’s a busy one. We have quite a collection of family tweaks and updates to look at, as well as a redesign of the main Triage dashboard.
- Updated Dashboard interface
- Dridex version update
- Updated Hancitor detection
- Qulab signatures
- SnakeKeylogger signatures
- CheetahKeylogger signatures
- Taurus Stealer
- Updated AgentTesla and Redline Stealer definitions
- ISRStealer signatures
If you have any feedback on Triage or particular samples please do get in touch! You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Updated Dashboard Interface
The main dashboard on Triage has been looking a bit empty for a while now, but we’ve been working on a new version to include a lot more information and act as more of a hub.
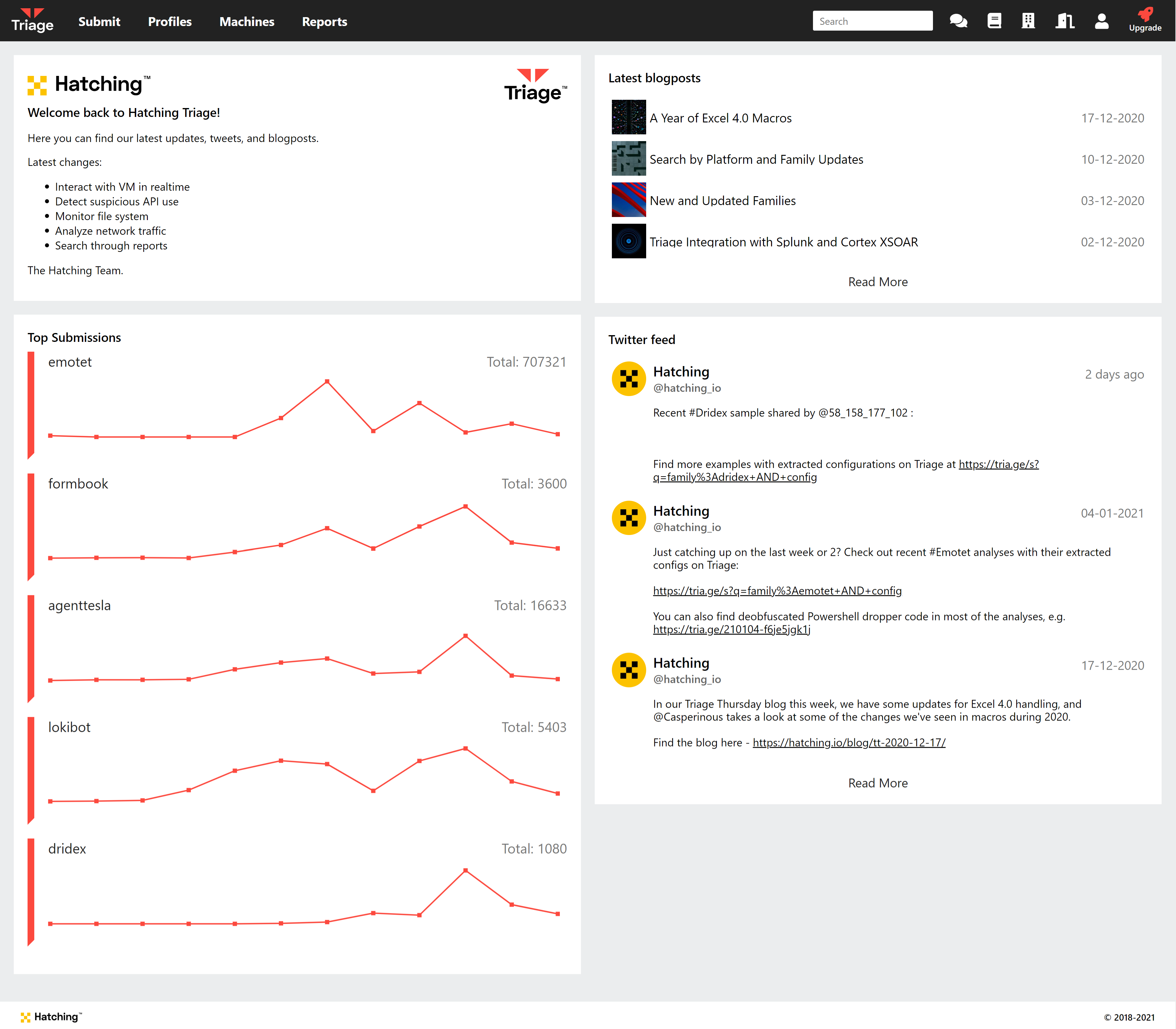
The new UI features:
- Direct links to our latest blogposts, including these Triage Thursday posts where we cover the latest updates to the platform.
- A view of our Twitter feed, where we post links to interesting samples and important Triage updates.
- Graphs showing the number of submissions for the 5 most common families on the public Triage server. Displays trends over the last 12 months.
We hope you like the new interface. As usual we’ll likely continue to iterate and improve on it over the coming months, so if you have any suggestions or feedback feel free to get in touch.
Dridex Version Update
A recent change in Dridex samples meant that our extractor was no longer handling some configuration fields correctly. This issue has now been addressed and the malware’ Version field will now display the right value.
Analysis:
Updated Hancitor Detection
Hancitor, often also known as Chanitor, is a loader which has been around since 2014. it is often seen being used to deploy the Pony trojan. It is not particularly complex or advanced, but the family includes a large number of variations created over the years.
Triage has had basic detections for common Hancitor samples for some time, but we had been aware that some were not being correctly identified. We recently reviewed these and updated signatures to cover more variations. A new configuration extractor has also been implemented to dump C2 URLs and the botnet ID to aid with campaign tracking.
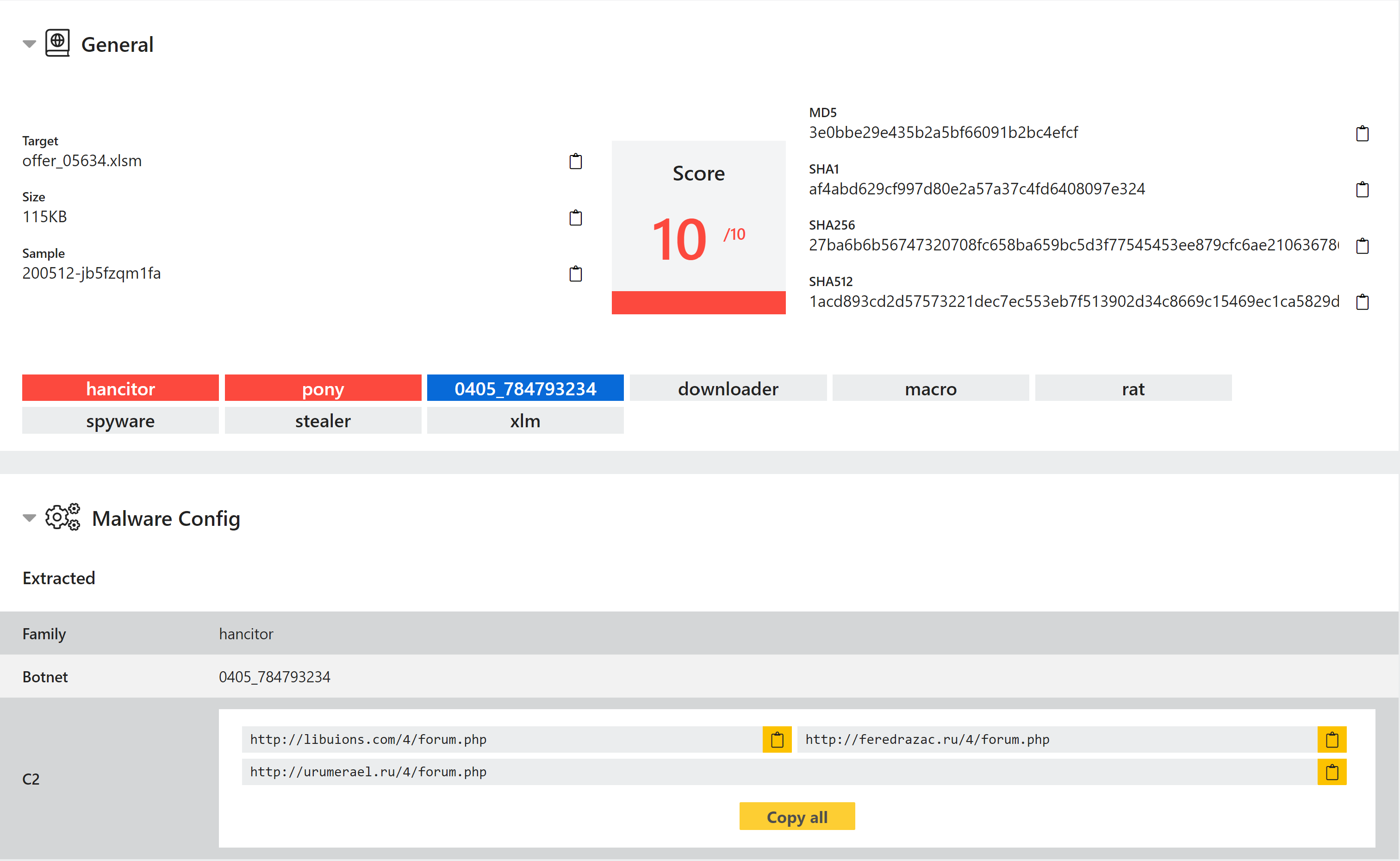
Analyses:
Qulab Signatures
Qulab is an infostealer created with AutoIT which is sold for general use on forums etc. It includes a range of functionality common to stealers including:
- Harvesting browser/FTP credentials
- Clipping cryptocurrency wallets
- Collecting chat logs for Discord/Telegram
The family is unusual for being entirely written in AutoIT, and features some interesting obfuscation techniques.
We have expanded Triage’s support for the Qulab family, adding behavioural detections for its common logging behaviour.
Analysis:
SnakeKeylogger Signatures
Snake is a relatively straightforward keylogger which, again, is sold through forums rather than being used by a single actor. As is common with modern keyloggers it also includes some functionality of a stealer, being able to gather stored credentials from browsers, take screenshots, and extract the contents of the clipboard.
Since the behaviour itself is fairly generic, we have added static Yara detection to classify the family on Triage.
Analyses:
CheetahKeylogger Signatures
Similarly to SnakeKeylogger above, Cheetah is a run-of-the-mill keylogger sold fairly cheaply through hacking forums.
The malware doesn’t appear to feature extra stealer functionality like many of its peers. Its most notable capability is the use of the SMTP protocol for data exfiltration.
We have added static Yara rules to classify samples of this family.
Analyses:
Taurus Stealer
Taurus is a stealer which was first observed in April 2020, a new project from the team behind an older stealer called “Predator the Thief”.
Taurus shares many features with its older brother:
- Steals browser data including passwords, cookies, autofill forms and browsing history.
- Accesses common cryptocurrency wallets.
- Steals credentials from FTP and email clients.
- Harvest system information and sends profile to the malware operator.
We have added new signatures to classify the Taurus family, including behavioural and static support.
Analyses:
Updated AgentTesla and Redline Definitions
We recently observed that in some cases our detections for the AgentTesla and Redline stealers were overlapping, causing some analyses to be incorrectly identified or to be assigned both family tags.
We have been gathering samples of both families over recent months and today pushed an update to improve the accuracy of detection for them. We will continue keeping an eye out going forwards and will make further updates if necessary.
Analyses:
ISRStealer
ISR Stealer is a keylogger and password stealer which has been around for some years, being reported in campaigns back in 2016. The family is a modified variant of the old HackHound stealer, reported to have been created all the way back in 2007.
We have implemented behavioural and static detections for the family and these are now available on tria.ge.
Analyses:
BitRat Updates
BitRAT was first observed in the 2nd half of 2020, being sold on HackForums as a new infostealer. Analyses have suggested that it was created by someone with limited technical ability, as it is extremely noisy and includes lots of copy-pasted code and 3rd party tools.
Analyses:
