Welcome back to another week of our Triage Thursday blog series, where we introduce all the main changes over the past week.
It’s a fairly short one today, but we have some nice updates to configuration extractors to go over as well as the addition of some new families:
- Improved AgentTesla extractor to include email_to field
- Improved GoldDragon detections
- Added detection for Blackcat ransomware
- Added detection for Trickbot’s NWorm module
If you discover any issues or missing detections while using Triage, please do send us feedback. It’s a big help in deciding what we should be prioritising. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account!
AgentTesla
AgentTesla has taken something of a backseat in the last year or so, with more attention going to some of its younger, flashier competitors. However it hasn’t really gone anywhere and is still heavily used by different threat groups as a powerful infostealer with quite a bit of flexibility.
Although the payload hasn’t changed significantly since we last featured the family all the way back in April 2021, we recently received a request to expand our configuration extractor to include an additional field. As such, in today’s set of updates we have tweaked our handling to also dump the email_to field available in certain versions of the malware. This is part of the SMTP C2 mechanism employed by some of the more recent variants and dictates the address exfiltrated data is sent to. Previously we had only covered the login credentials used to access the sender account.
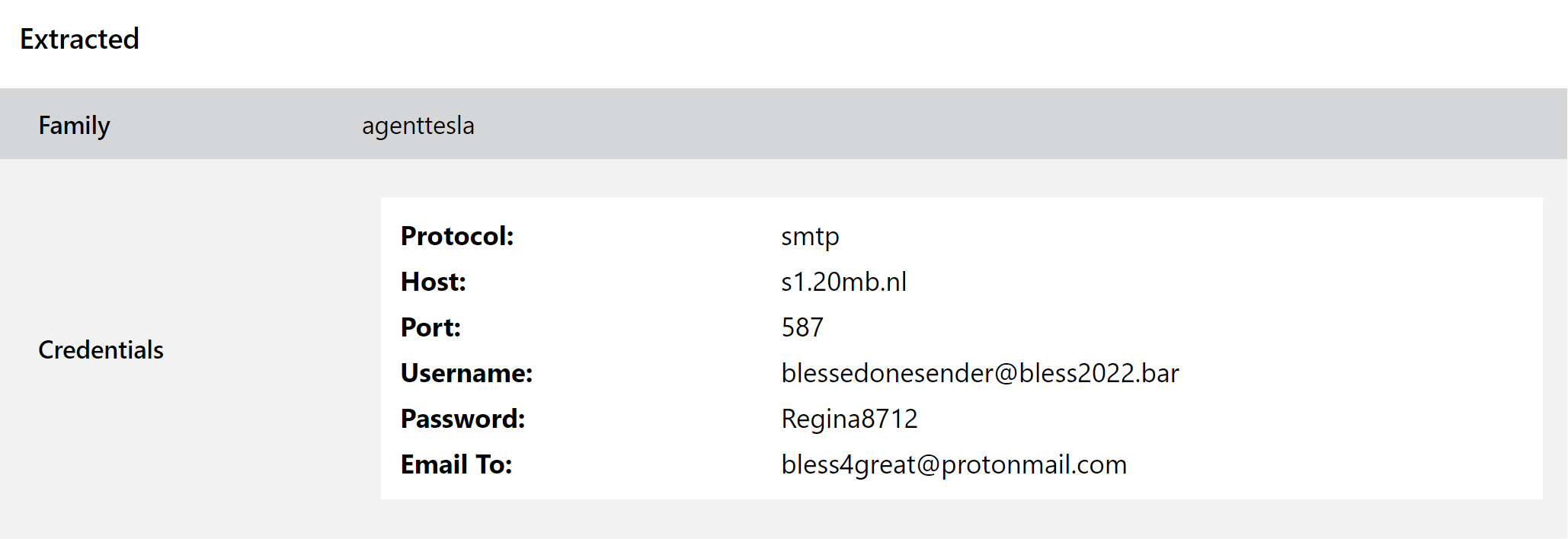
We hope you find this useful in tracking campaigns and actors. If there are other improvements we can make to this or other configuration extractors feel free to get in touch.
Analysis:
GoldDragon
GoldDragon is a backdoor and loader generally attributed to the Kimsuky APT group from North Korea. Activity is mostly aimed at various companies and government organisations in South Korea, and the family normally forms just one part of a much larger infection and exploitation chain. It was part of the series of attacks carried out against the 2018 Pyeongchang Winter Olympics - more details of that can be found in McAfee ATR’s blogpost on the campaign.
The family’s functionality is fairly limited due to its use as just one link in the infection chain, but it is capable of automatically downloading and installing additional payloads as well as providing direct backdoor access for the attacker if needed.
We added initial detections back in July last year and this week we’re revisiting the family to update our signatures and improve coverage.
Analyses:
BlackCat Ransomware
BlackCat was first reported on at the tail end of 2021, with MalwareHunterTeam being the first to point it out in early December. According to them, it had been carrying out attacks since mid-November.
Symantec followed this with a full analysis of their own, which can be found here. Also referred to as either Norberus or ALPHV, the family is the first professional and publicly used ransomware to be written in the Rust programming language. Like many of its modern compatriots BlackCat uses the double-extortion approach, targeting specific companies to exfiltrate sensitive data before deploying the ransomware itself to encrypt files.
It appears that, leveraging one of the advantages of a language like Rust, the family also has both Linux and Windows versions - we have seen a number of both being submitted to Triage recently. According to BleepingComputer the ransomware has been tested and deployed for the following platforms (taken from their article here):
- All versions of Windows from 7 and higher (tested on 7, 8.1, 10, 11; 2008r2, 2012, 2016, 2019, 2022); XP and 2003 can be encrypted over SMB.
- ESXI (tested on 5.5, 6.5, 7.0.2u)
- Debian (tested on 7, 8, 9);
- Ubuntu (tested on 18.04, 20.04)
- ReadyNAS, Synology
Based on the complexity and quality of the observed samples it seems likely that the operators of this family are aiming to set up shop long term, so we have reviewed it and implemented some initial detections. We’ll keep an eye on it and make any changes needed if/when it comes out with new updates.
Analyses:
Windows:
Linux:
Trickbot NWorm
Trickbot is back on the menu this week with an improvement to our handling of the family - or to be more precise, one of the modules it uses to enable propagation to and exploitation of vulnerable domain controllers from an infected client.
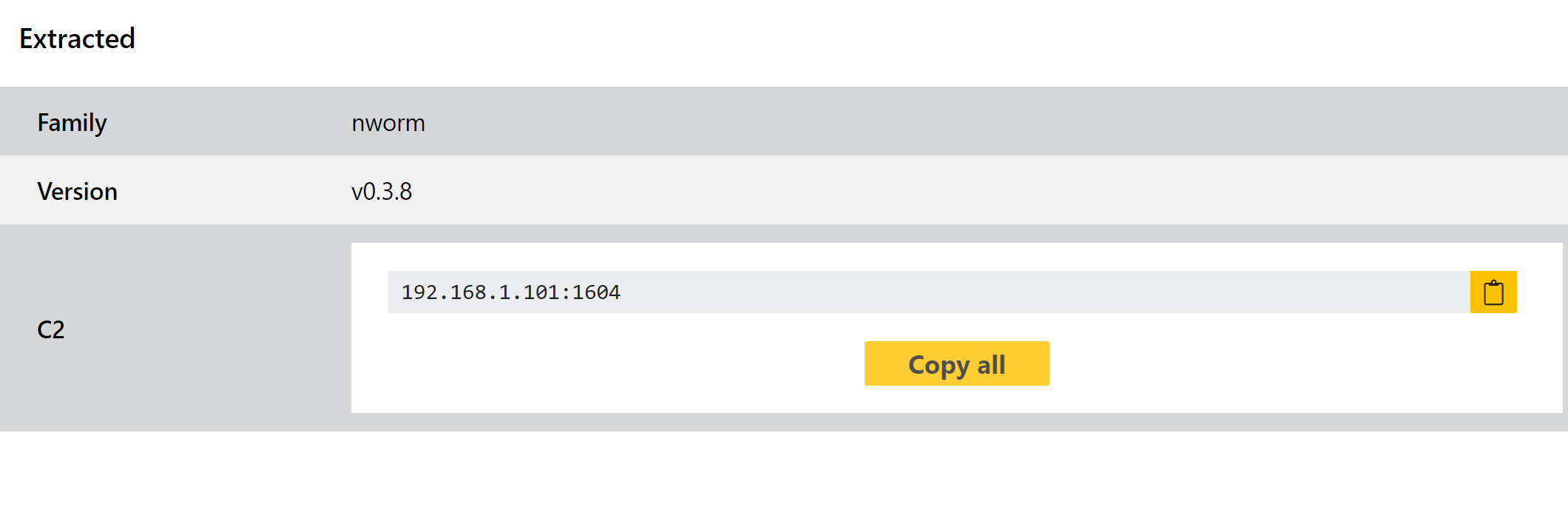
This module first appeared around April 2020, replacing an older version of the same module called MWorm. It brought many improvements over its predecessor, especially in relation to stealth. Infections of a DC using NWorm leave no obvious indicators, and completely disappear after a reboot or shutdown.
Its purpose is to exploit the vulnerability and then deploy an actual Trickbot payload, so its functionality is limited. However based on requests from users we have decided to separate this out from our overall Trickbot handling, and we have added a new configuration extractor for it.
Analyses:
