Welcome back to our Triage Thursday blog series, where we introduce all the changes made to the platform over the last week.
Today we have a few significant feature updates to share along with our usual detection changes:
- Added language options for analysis VMs
- Extend or terminate analyses while they’re running
- New geoIP mapping for extracted C2 URLs/IPs
- Updated DJVU ransomware detection
- New signatures for Sidoh family (aka Ryuk Stealer)
- Mespinoza ransomware detection
- Updated Vidar rules
In other news we are still looking for a Go developer to join the Hatching team. If you’d like to be involved in the next steps of Triage’s journey - or know someone who might be - you can find the full job listing here. Feel free to reach out with any questions.
If you discover any issues or missing detections while using Triage, please do send us feedback - it’s a big help in deciding what we should be prioritising. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Language VM Options
Many malware samples out in the wild use geolocation checks to limit the machines they will infect. The most common of these - and the easiest to get around - involve a blocklist for Russia and other former Soviet states which prevents the malware running there at all. The more interesting ones are where the malware has a list of countries of interest, and will not run if it detects that it’s in any other region - for example they may only target Italy or South Korea. These are a bit trickier to carry out automated behavioural analysis on, as unless their list includes the Netherlands (or the country you have your own on-premises environment set up) the malware will simply exit almost immediately.
To get around these limitations, we have for some time been planning a series of features which will allow users of Triage to ‘pretend’ that the analysis is being run in a specific country. This week we are pleased to be releasing the first part of this, allowing our users to select the language settings for a virtual machine before analysis begins.
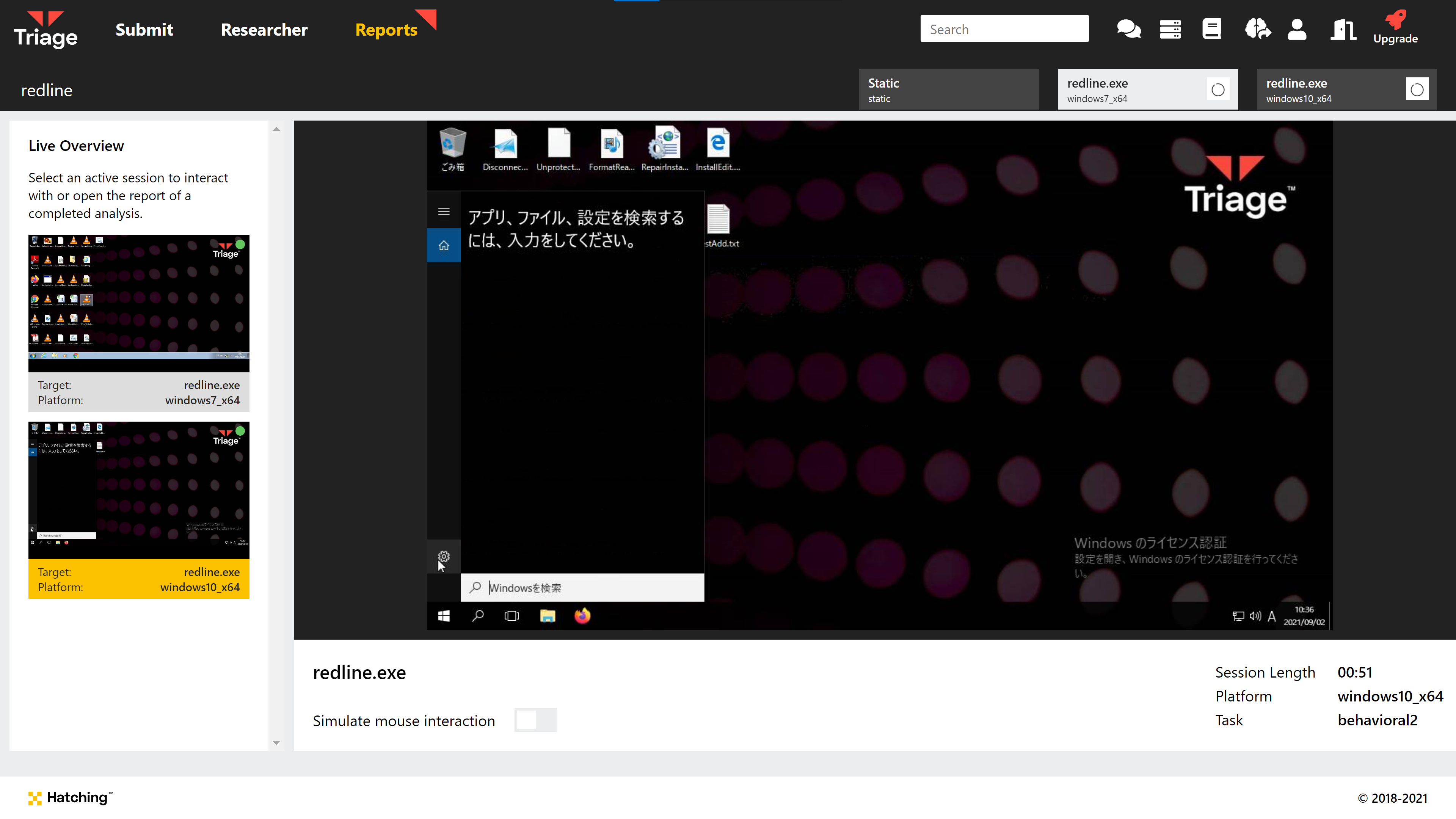
In this initial release we are only making support for German, French and Japanese language settings available, but we will be extending on this in the weeks to come. We’ll also be looking to add additional features - such as network proxying - to allow better location spoofing.
If you have specific requests or use-cases feel free to send us some feedback - the more samples we have to test against the better.
How to use VMs with different languages
The option to select a different language has been added to the VM selection options, which can be accessed either directly during the submission process or included in Profiles.
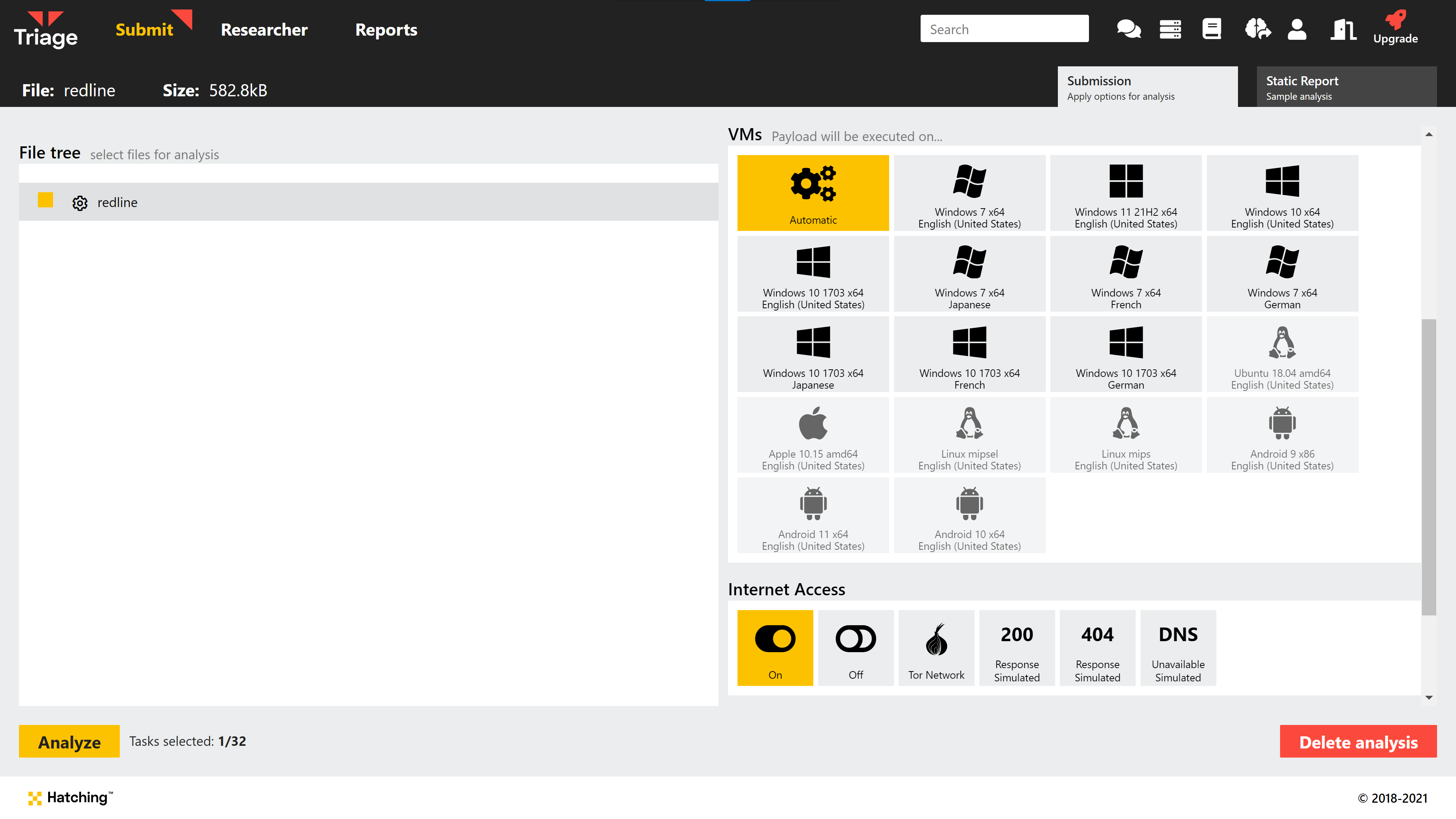
As usual with VM selection, you can choose multiple different versions/languages and each will spawn a separate task within the analysis.
Extend or Terminate Running Analyses
A common feature request we receive is to allow customisation of the duration of analyses while they are actively running. It was previously possible to terminate an analysis early simply by shutting down the VM via the guest OS, but this was not necessarily evident and is not really optimal regardless. There was also no way to extend the duration once a file had been submitted.
We have now addressed this with some additions to the user interface in the Live Monitor, where users can interact with the VMs during analysis. While the sample is running there is now the option to extend the timeout by 1 minute, or terminate the task immediately. Note that these buttons affect each task individually, so if a sample is being run in more than one operating system each can be controlled independently.
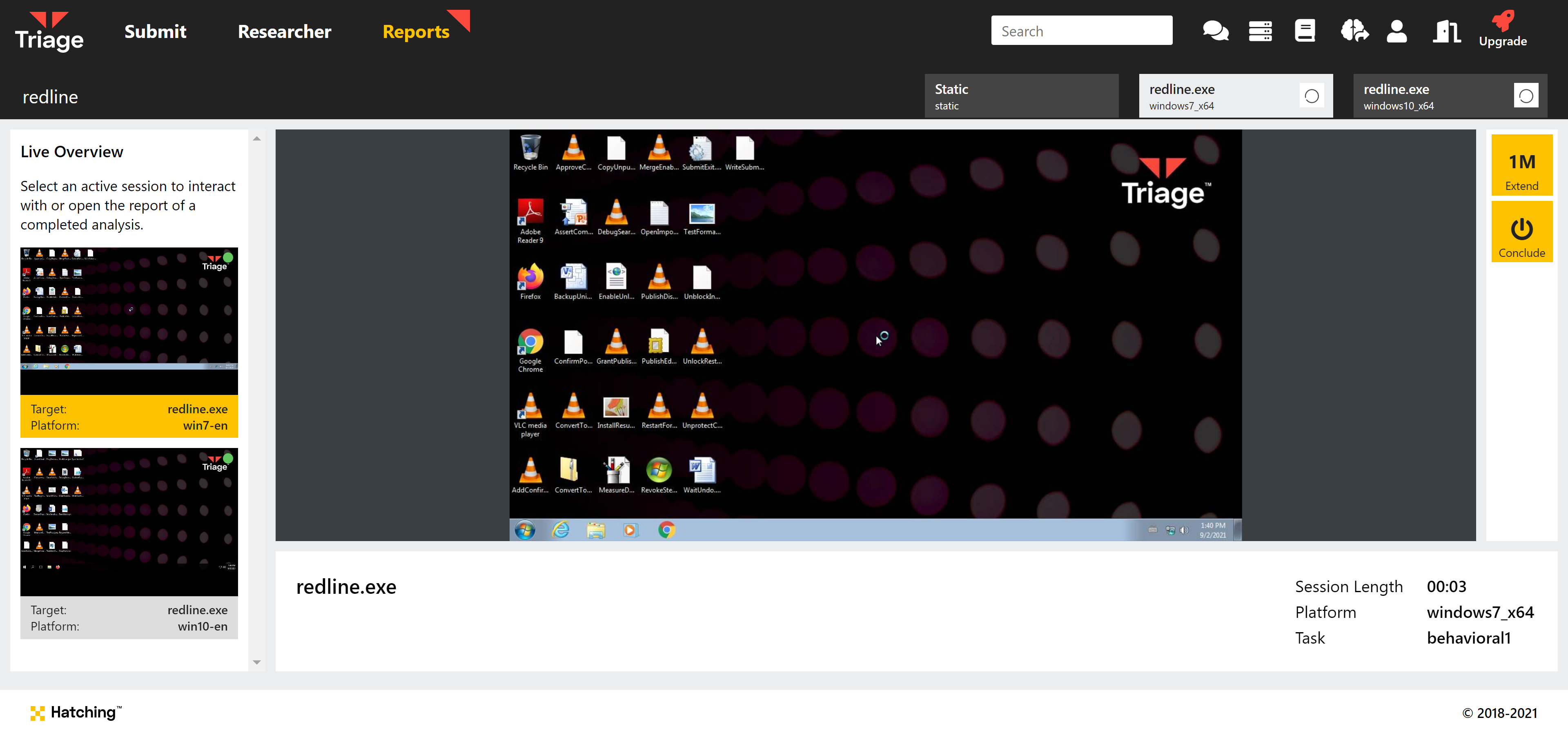
GeoIP Mapping of C2 URLs/IPs
Another aspect we’re keen to work on in the coming months is improving the way we display data in the UI. One of our main goals with Triage is to ensure that reports remain concise and uncluttered, but even so we feel there are areas where we could make better use of the information available to improve its usefulness to end users.
As part of this we are today releasing a new visualisation for all extracted C2 URLs/IPs, mapping them based on geographical location to give an overview of the countries hosting malicious infrastructure for these campaigns.
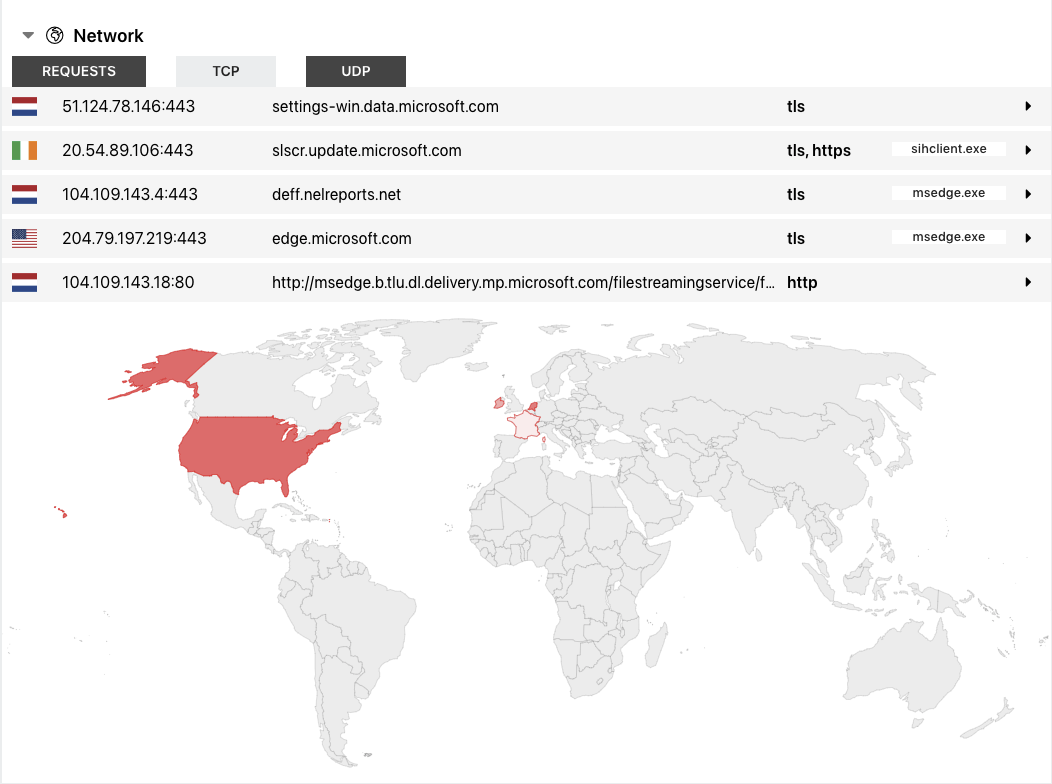
This feature is powered by our new partners at ipinfo.io, who provide a range of powerful lookup services for IP addresses. We are currently only leveraging their geoIP checks but that is only part of the information available through their APIs.
DJVU Ransomware
DJVU is a huge ransomware family which, although it’s never achieved quite the mainstream fame of the likes of REvil or Gandcrab, has reliably been one of the most widespread and successful families observed in the wild. First seen in December 2018, only around a year later Emsisoft reported that the family included 160 variants with a confirmed total of around 116,000 victims globally (and an estimated total of nearly half a million).
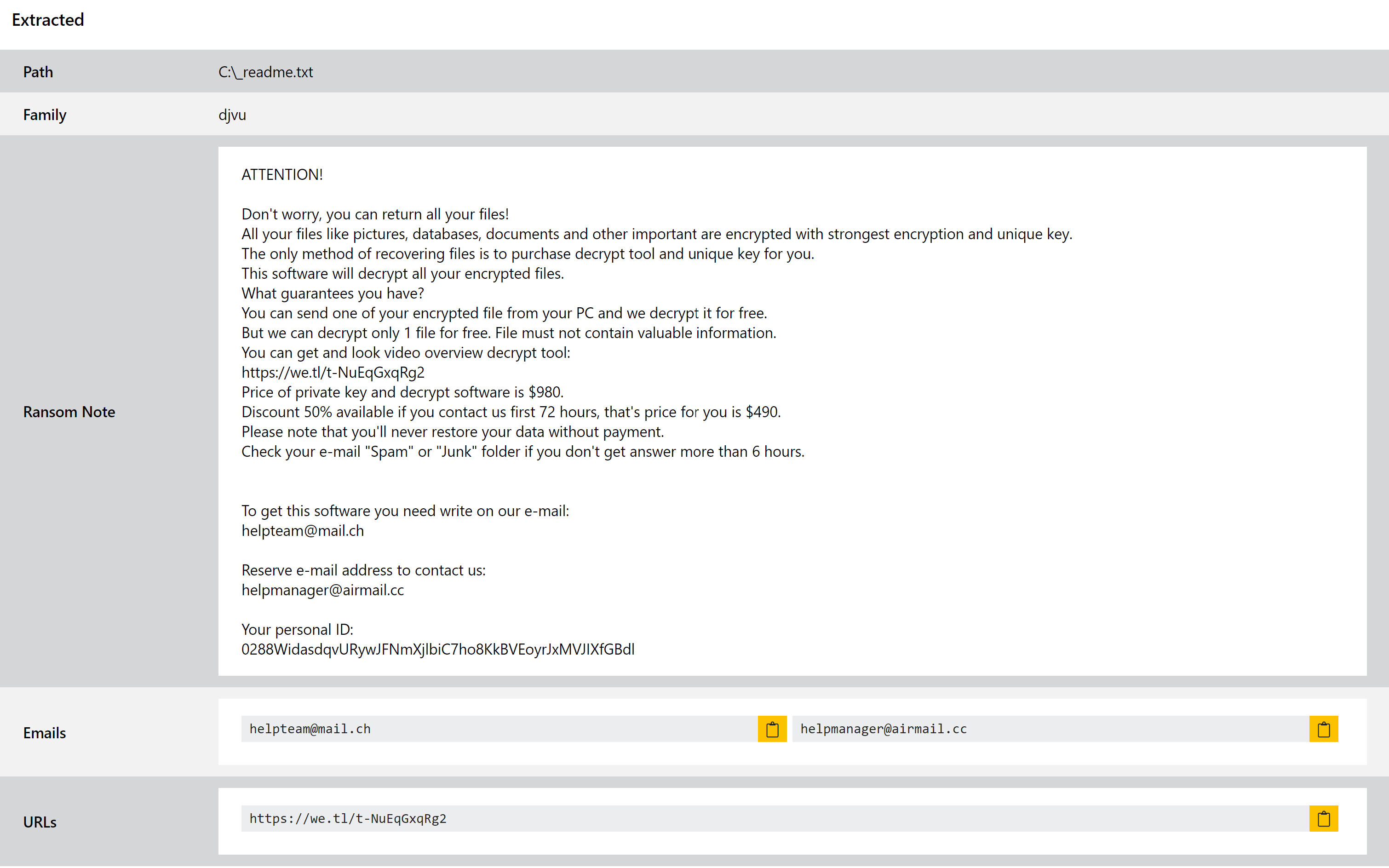
The family is itself a variant of the STOP ransomware. Early versions had flaws which enabled victims to often decrypt their systems without paying the ransom. Emsisoft published a decryptor in late 2019 which had good coverage on versions up to that point, but since then the creators have make some updates to strengthen the encryption routines.
Triage has included detection for DJVU for some time, but this week we’ve made some tweaks to better handle some variants observed in the last few weeks.
Analyses:
Indicators of Compromise:
| Indicator |
|---|
| managerhelper@airmail[.]cc |
| manager@mailtemp[.]ch |
| helpteam@mail[.]ch |
| helpmanager@airmail[.]cc |
| hxxps://we[.]tl/t-ykQaS2tRyB |
| hxxps://we[.]tl/t-NuEqGxqRg2 |
| hxxps://we[.]tl/t-B0FsLNO3fN |
| *.orkf |
Sidoh Stealer
Sidoh - otherwise known as Ryuk Stealer - is a toolkit generally observed alongside Ryuk ransomware infections. Reportedly created by the WIZARD SPIDER APT group (to whom the popular Trickbot banking trojan is also attributed), the family searches infected machines looking for files containing keywords matching a predefined list. Once a match is identified the relevant file is exfiltrated to the attackers via FTP upload.
According to Crowdstrike the keywords identified suggest an interest in government, military and financial sectors. Although no direct link to ransomware-related extortions has so far been identified it’s use - and the fact that its codebase appears to borrow extensively from the Ryuk ransomware family - suggests that this may be at least one use for the malware.
We have analysed some example of the malware observed recently on Triage and implemented some initial detections.
Analyses:
Mespinoza Ransomware
Mespinoza, often called Pysa, first popped up in the wild around October 2019, although its activity remained quite low until about a year later. Like many modern ransomware families it carries out exfiltration of sensitive data as well as the usual encryption activities, using this as leverage in ransom payment negotiations. A public leak site is run where files are published in the event of non-payment.
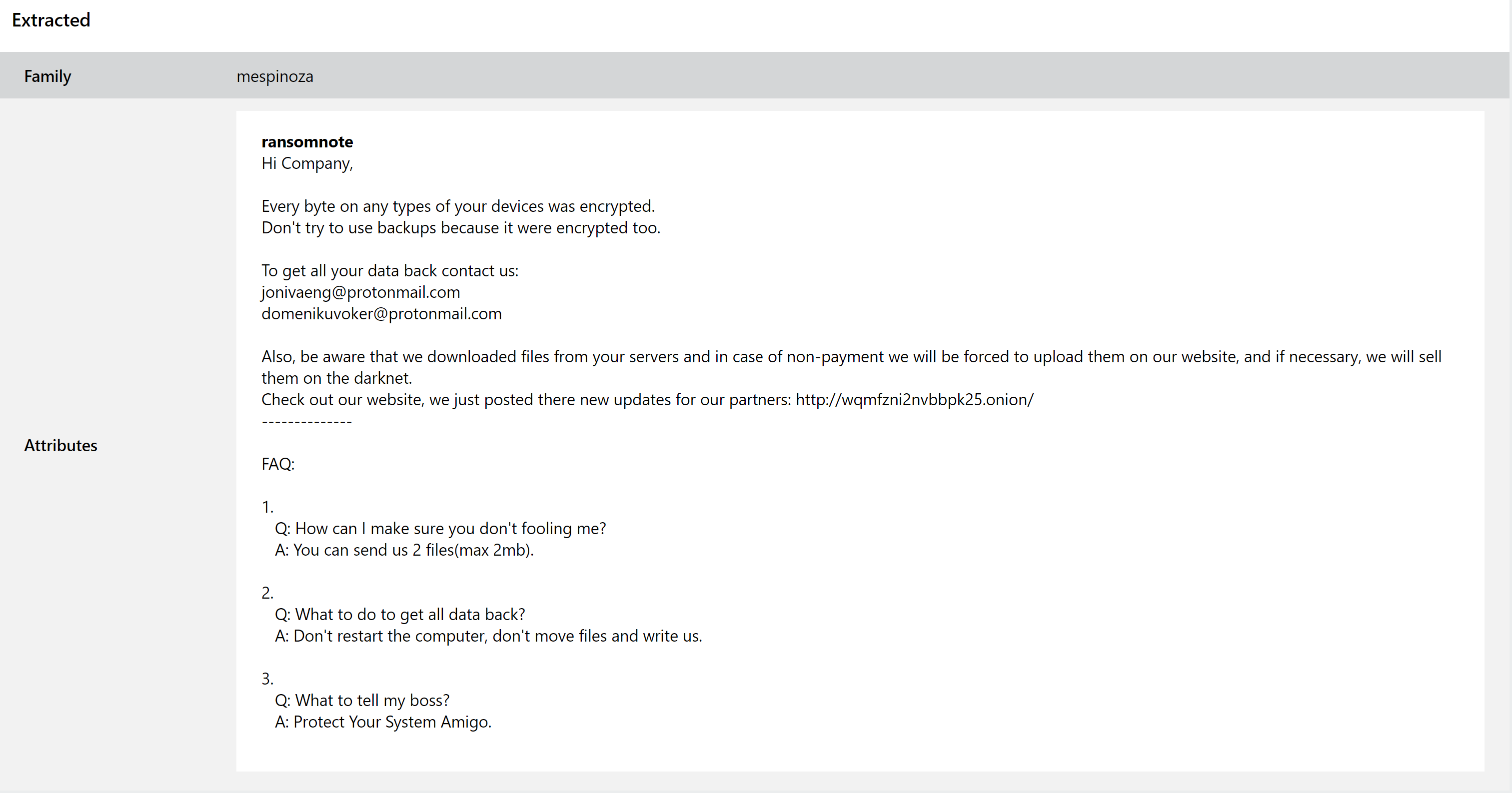
According to PaloAlto the operators also commonly install a backdoor - known as Gasket - to maintain access to infected systems/networks as an additional insurance policy to try and force payment.
We have added detection for the family, as well as a configuration extractor to reliably dump the ransomnote as configured within the executable. You can find some examples below.
Analyses:
Indicators of Compromise:
| Indicator |
|---|
| *.pysa |
| jonivaeng@protonmail[.]com |
| domenikuvoker@protonmail[.]com |
| \REGISTRY\MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\legalnoticetext |
| \REGISTRY\MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\legalnoticecaption |
Vidar Stealer
Vidar is a widely used stealer family which was first discovered in late 2018. It began as a fork of the popular Arkei stealer and bears significant similarities in terms of code and string reuse.
The family is still very active in 2021, with new versions appearing regularly. It is often deployed alongside other threats, as well as being used in its own campaigns. In mid-2019 Crowdstrike reported that it was being dropped with Gozi IFSB payloads by malicious Office documents.
In July 2021 we added a configuration extractor for the family, and this week we are just making some minor tweaks to this to properly handle recent variants observed among Triage submissions.
Analyses:
Indicators of Compromise:
| Indicator |
|---|
| hxxps://lenko349[.]tumblr[.]com/ |
| hxxps://bandakere[.]tumblr[.]com/ |
| hxxp://49[.]12[.]198[.]69/ |
| hxxp://49[.]12[.]198[.]69/1008 |
| hxxp://49[.]12[.]198[.]69/freebl3.dll |
| hxxp://49[.]12[.]198[.]69/mozglue.dll |
| hxxp://49[.]12[.]198[.]69/msvcp140.dll |
| hxxp://49[.]12[.]198[.]69/nss3.dll |
| hxxp://49[.]12[.]198[.]69/softokn3.dll |
| hxxp://49[.]12[.]198[.]69/vcruntime140.dll |
