Welcome back to another Triage Thursday blogpost! This week, alongside our usual updates, we’ll be taking a look back over the year at some of the major milestones and changes we’ve achieved with the platform.
Although 2021 may not have done too many favours for our social lives, it has been rather productive for us in terms of product development and the growth of Hatching as a whole, so we think it’s worth taking some time to reflect on what has been achieved with the help of our awesome community.
The year in review:
- 2021 in numbers - how things have changed and grown since this time last year
- Major milestones in 2021 - a look at the largest new features added over the year
Of course, we also have some regular updates to introduce too. These are:
- Further updates to Emotet Powershell parsing to cover new variations
- New Bitrat configuration extractor
- Updated C2 handling in XLoader configuration extractor
- Added dumping of Affiliate ID to Danabot configuration extractor
- Improved Flubot Android banker detection
- Updated Phorphiex detections for new version/botnet
- Added family detection for GlobeImposter ransomware
- Added family detection and a configuration extractor for Matanbuchus loader
We cannot thank you all enough for your support, not just this year but overall. Triage as a platform has come forward a tremendous amount this year and we could not have done it without your constant feedback and suggestions.
It’s a big old world of malware out there and keeping track of all of it is simply impossible without the support of our customers and users - seriously, Emotet had been back for about 30 minutes before we were emailed the first batches of samples and analysis findings by users!
We hope you find this somewhat nostalgic blogpost interesting and we can’t wait to see what we can achieve together in 2022!
For all our readers who celebrate it, the team here at Hatching wishes you the happiest of Christmases and a safe, healthy New Year!
A Year in Numbers
A lot has changed in one year and Triage has grown enormously - both in terms of users and features. We have plenty of plans for 2022 but let’s take a bit of a look where we are at now.
Users Count
Our public cloud has seen a huge amount of growth this year, with every week bringing new users to the platform. Our community is a great strength of ours as it gives access to a huge corpus of samples and data - both malicious and benign - with which to develop signatures and detections which then feed back into the free and paid versions.
Our public user base on tria.ge has nearly quadrupled in 2021 alone! Thank you to everyone for your support and interest in Triage, and for all the feedback and suggestions you send us which have shaped the product into what it is today - and will continue to do so well into the future.
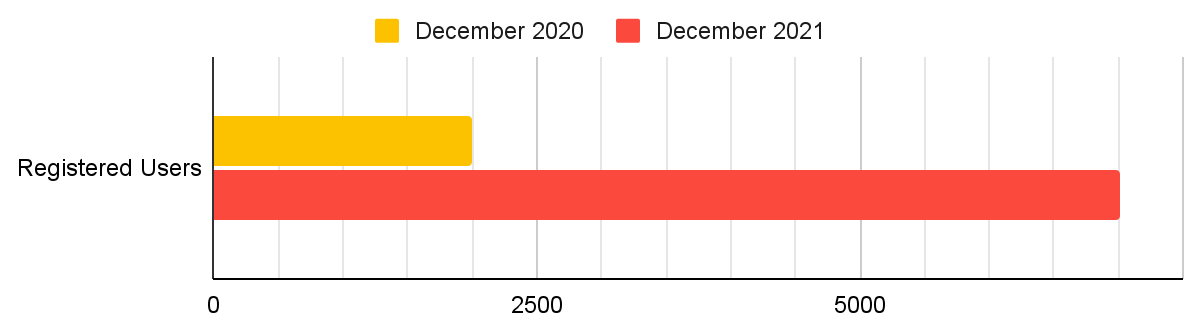
We have also seen a trend of more and more account registrations per month.
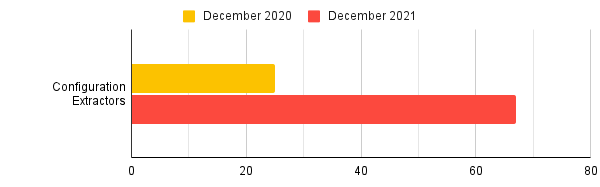
Configuration Extractors
If you’ve made much use of Triage you’ll be fairly familiar with our configuration extractors. Over time these have grown from being a nice addon for families like Emotet to being one of the core features of the platform, thanks to the hard work and innovation of our analysts and developers.
2021 saw a big step up in our focus on these, as can be seen by the rapid growth in numbers:
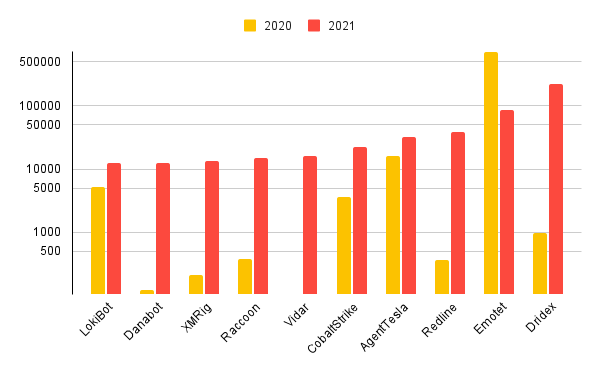
Most Common Families 2021
The families in use in the wild constantly shift and change. Below you can see a quick overview of the top 10 most common families submitted to Triage, with a comparison between the 2020 and 2021 statistics.
Note that we’ve had to use a logarithmic scale here not linear to make it show properly, thanks to Emotet and its 715,000 submissions in 2020!
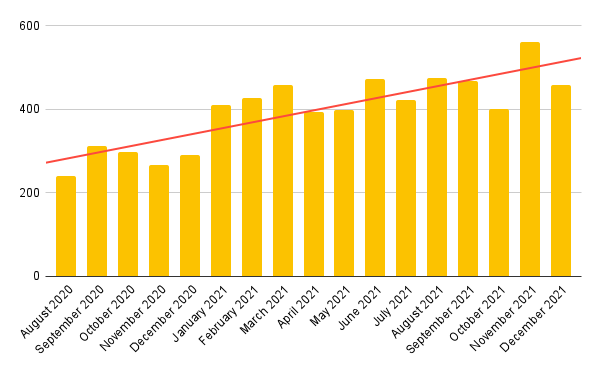
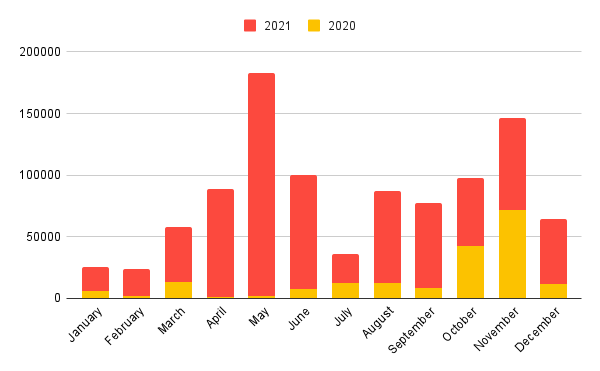
Submissions Per Month
We released Triage into full public access in August 2020, after initially working on an invite-only basis. Since then we have seen huge growth in users and this is well reflected in the number of submissions we have received per month over the course of 2020 and 2021.
In the graph below you can see the overall counts per month for each year, although we’ve removed Emotet as an outlier since it often accounts for more analyses than all other families combined!
Emotet or not though, it looks like May was a busy month for all you defenders out there!
Major Milestones of 2021
Looking back from our point of view, it’s hard to believe how much Triage has changed over the course of 2021. Features and components introduced earlier in the year already feel like they’ve been there forever, even accounting for Covid lockdown time dilation!
Below, we’ll pick out a few of the most significant milestones for the year.
Custom Yara Support
The first of our 2-part Yara support, custom yara rules were first introduced to the platform in March 2021. Using dedicated metadata fields you can integrate your own rules into the Triage reports and UI as though it was written and deployed by us, including having your own tags or family names indexed by our Search feature to make it easy to carry out your own threat hunting.
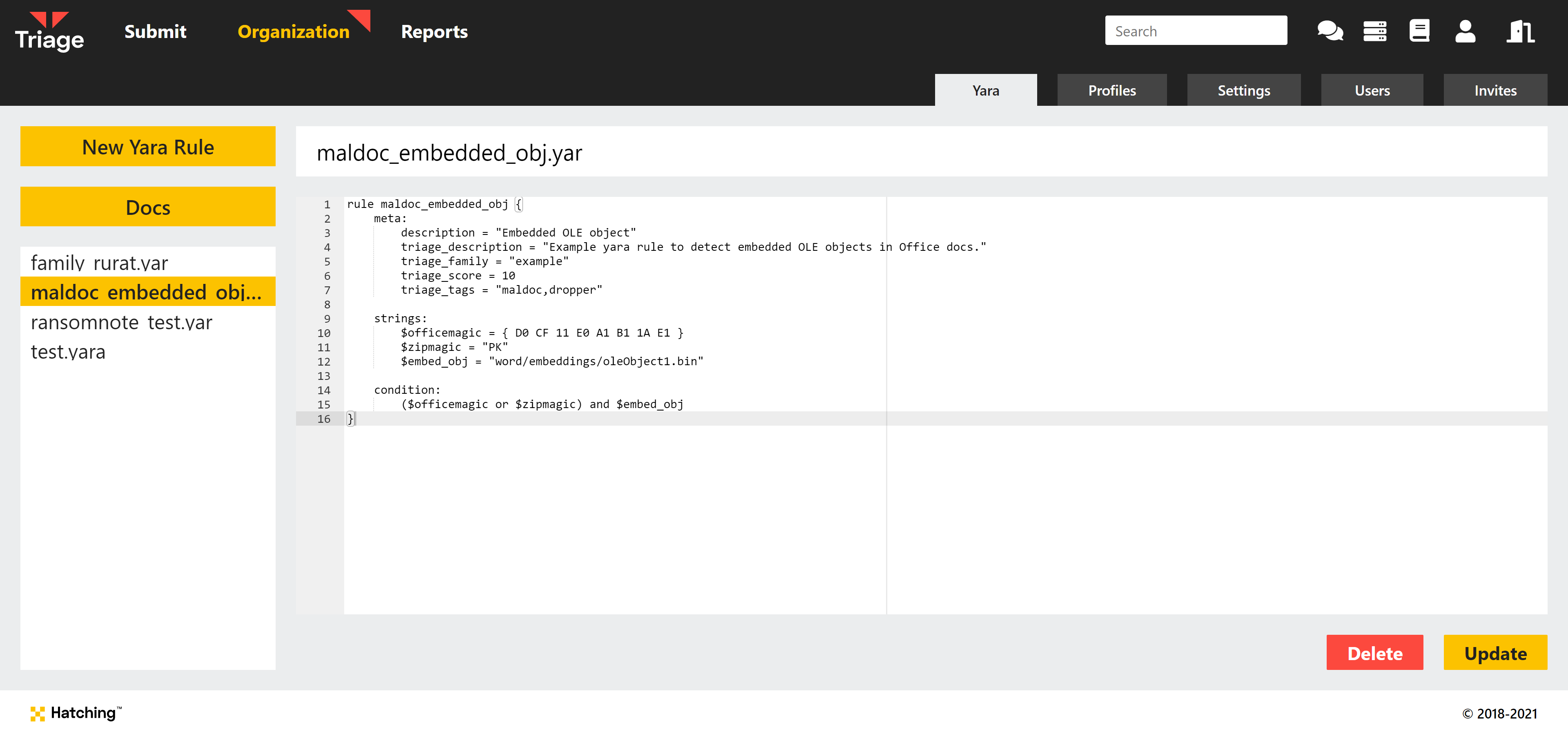
Today will also see the release support for managing and adding Yara rules to your account via the API, as this is currently only possible through the web interface. Watch out for that update later!
For more information on the functionality, check out the blogpost dedicated to this feature here.
Phishing Analysis
In April 2021 we released the first version of our dedicated phishing detection for Triage. Up until that point, the platform could only detect malicious actions on the host machine which did not support things like fake login pages aimed at credential theft.
In this new system, we can scan network traffic for indicators of abuse and suspicious pages and report these directly. Although a long term ongoing project, good progress has been made on fleshing out and improving this feature since release and we look forward to the future of this component as that continues.
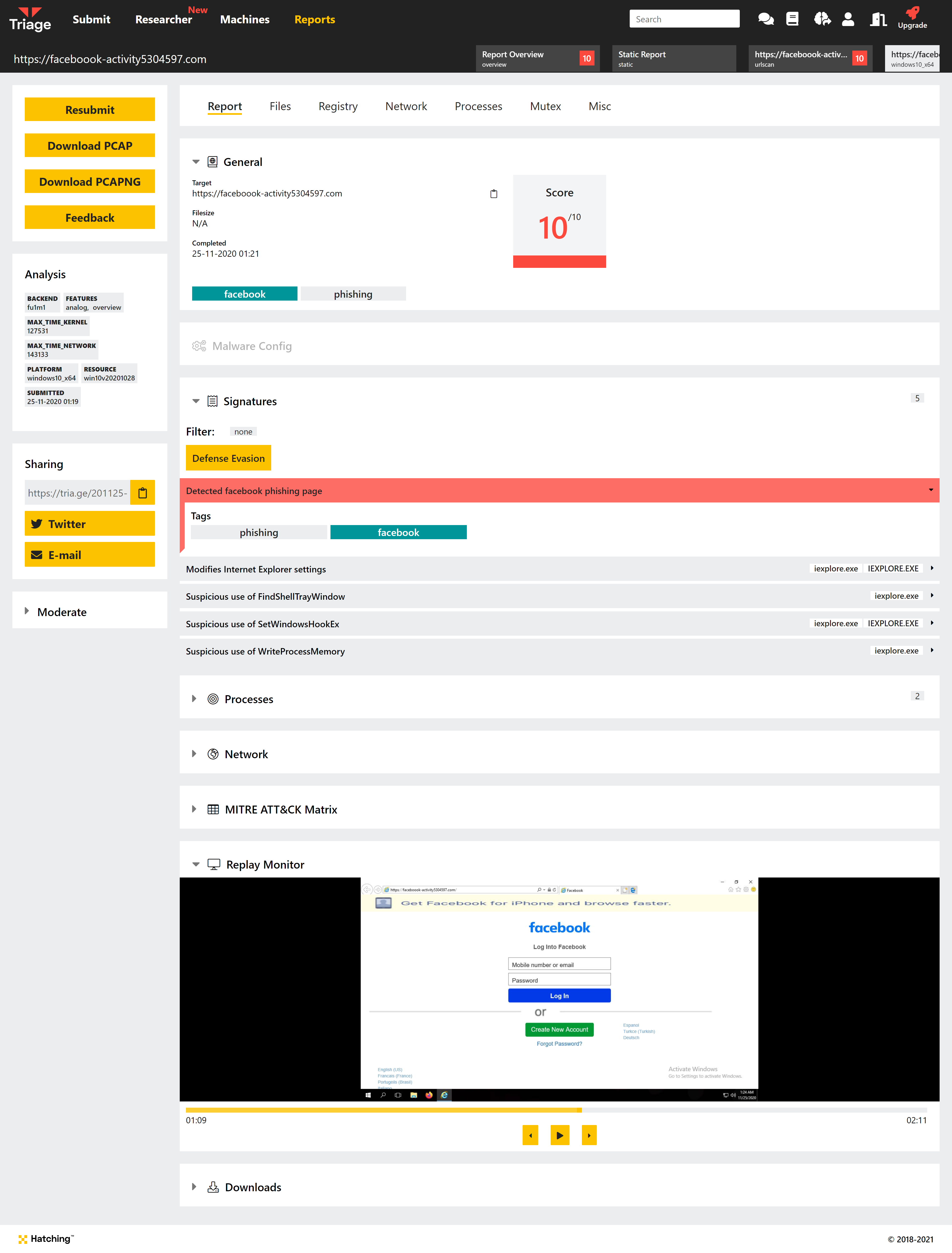
For more information, check out the relevant blogpost here.
macOS Support
When we first set out to build Triage we knew that we wanted to bring support for all the major desktop platforms - namely Windows, Linux, and macOS. Before we left early access in August 2020, we had already implemented support for Windows and Linux (with Android following quickly on the mobile side of things) but macOS presented some unique challenges which set it back somewhat in the development timeline.
However in June 2021 we finally released macOS for use in Triage, with 10.15 Catalina supported out of the box and our own custom kernel agent ready to go. This was a very significant milestone for us as it marked the end of the ‘base’ functionality - with a few minor exceptions, we were now ready to start adding bells and whistles and fleshing out the bones we had got in place already rather than focussing completely on core functionality.
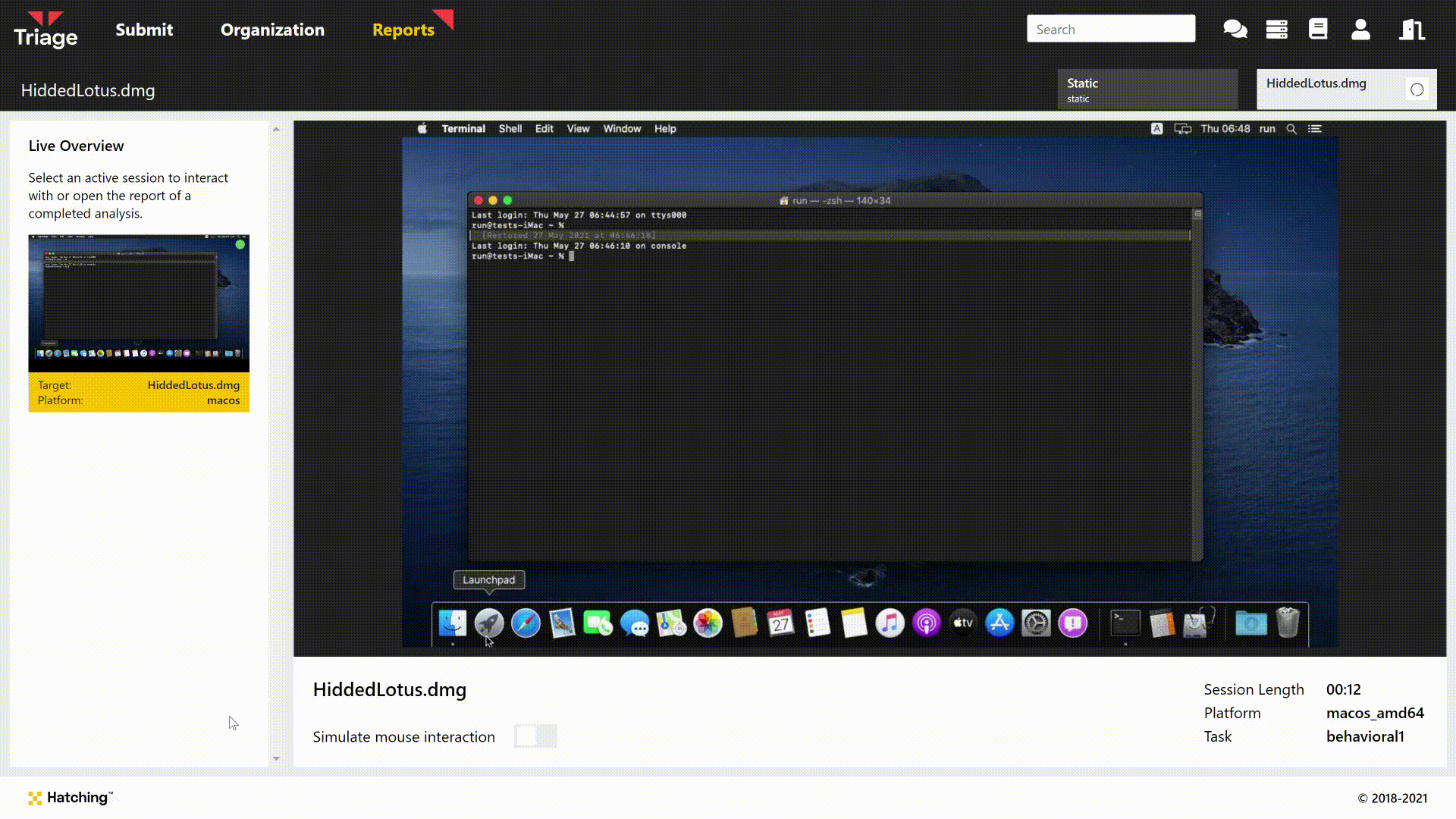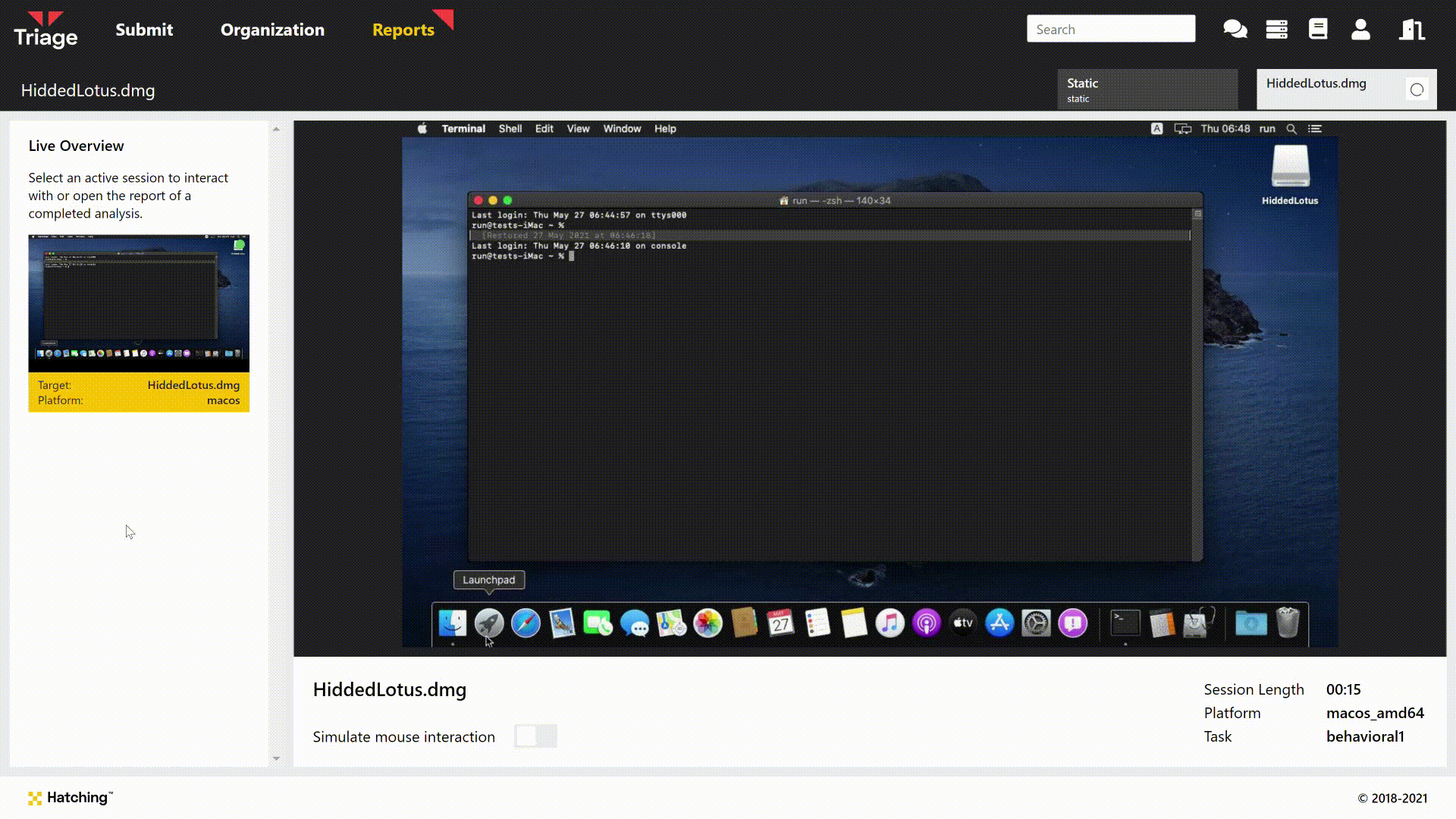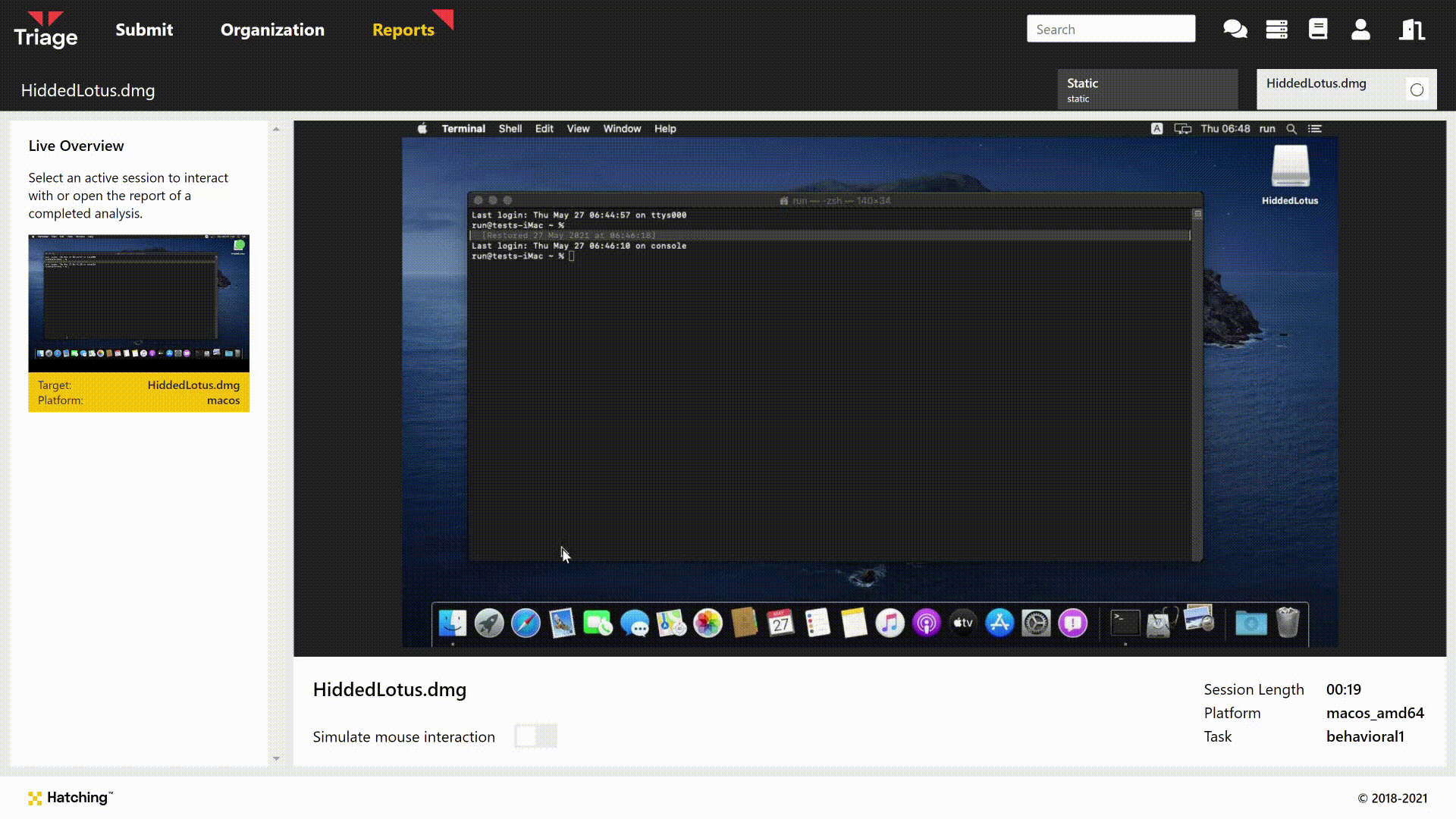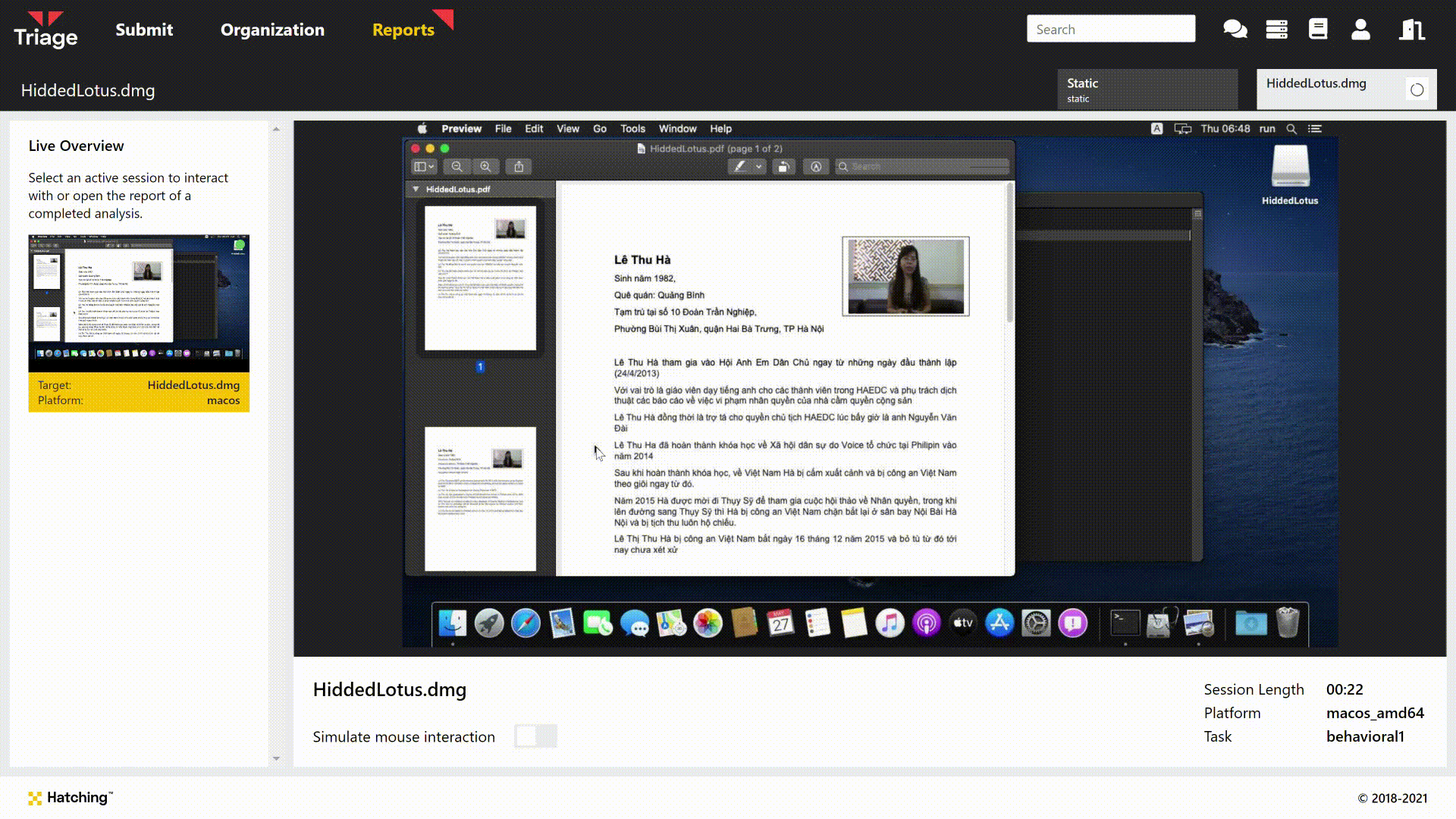
For full details about macOS support and the available features, check out the relevant blogpost here.
Suricata Integration
Suricata is a very powerful tool for detecting threats as they communicate over a network, and was something we were keen to bring into Triage to augment our own network detection capabilities.
This finally became a reality in July 2021, when we integrated Suricata into our backend and added the ETOpen ruleset as a starting baseline. It is run against the PCAPs generated by Triage after the analysis has finished, making the most of our ability to dump all SSL/TLS communications in plaintext.
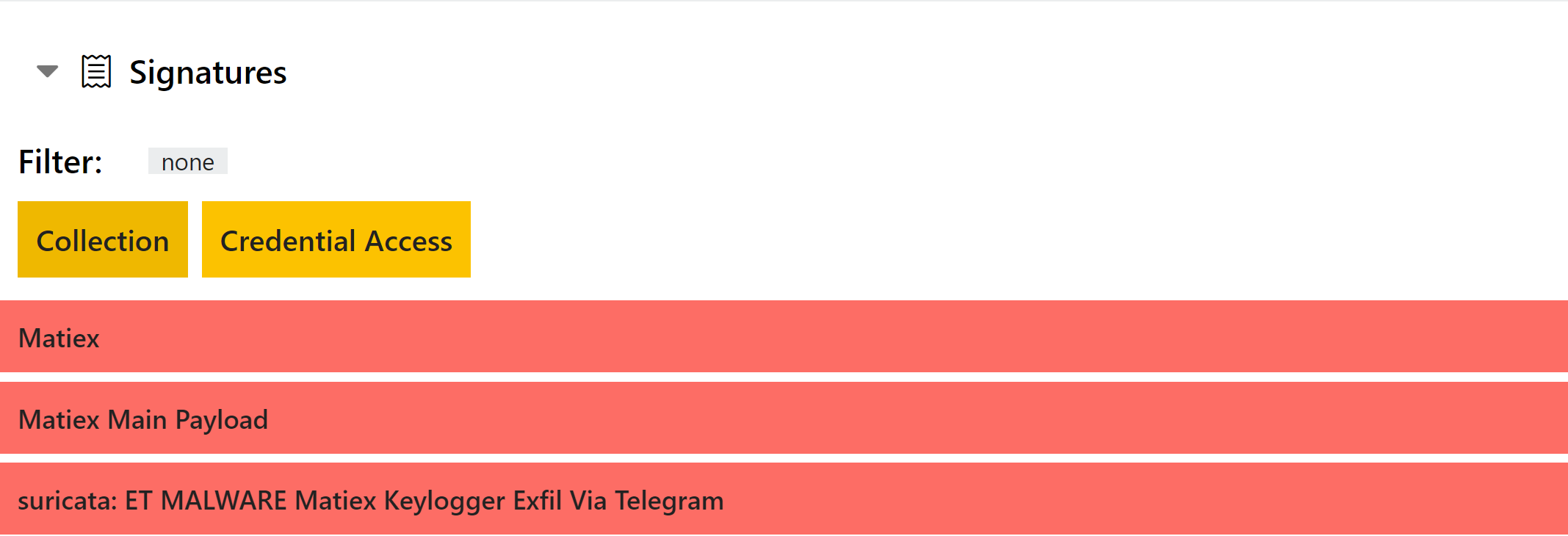
We hope to expand on this in the future and give you the ability to add your own rules, but for now to find out more about the feature check out the blogpost here.
Network Simulation
Controlling the network communications and endpoints of your sample are generally key to local, offline analysis in your own VM labs but is something of a trickier proposition in an automated sandbox environment.
However, after much planning and discussion on the practicalities our team implemented support for network simulation into Triage and we were able to release some basic support for it in August 2021.
Our network simulation plans work along the same lines as tools like INetSim for local analysis - disconnect the machine from the internet, and then provide fake responses to certain HTTP(S) requests to fool the malware into thinking its actually talking to its real C2 infrastructure. This can be very useful to tease a bit more activity out of a sample with inactive C2 domains, or for things like getting a full list of C2 URLs out of a sample that would normally exit at the first successful response.
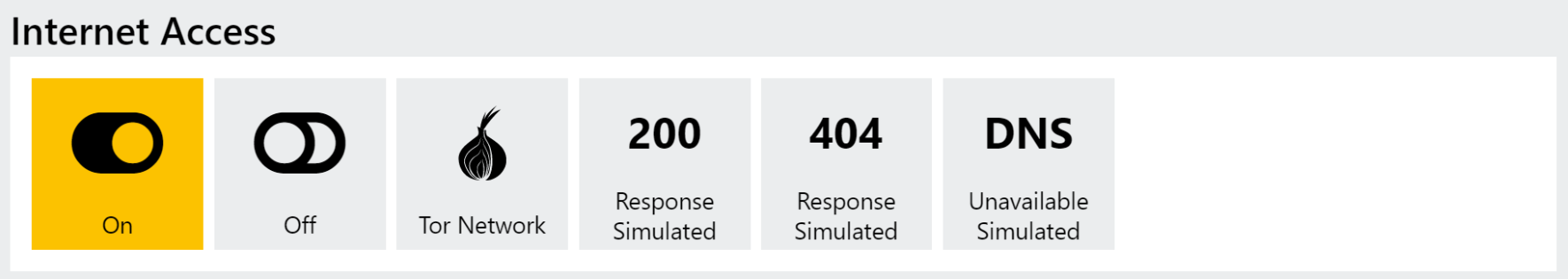
We have a lot of future plans to flesh out and improve on this feature in 2022, so watch this space! In the meantime for a detailed explanation of the current state and endgoals check out the blogpost here.
VM Language Packs
One of the most common and straightforward anti-sandboxing techniques is geoblocking, whereby samples can only run if they find themselves on a machine in a certain country or with their keyboard layout and system language set to a specific value.
As the first stage of our solution to this problem, in August we released support for different language packs on our analysis VMs. Currently supporting Japanese, Spanish and German we plan to extend this list in the months to come to provide much more comprehensive support here.
In future updates we hope to add in network support to provide much more flexibility when it comes to fooling these kinds of checks. For now, you can find a writeup of this functionality in our blog here.
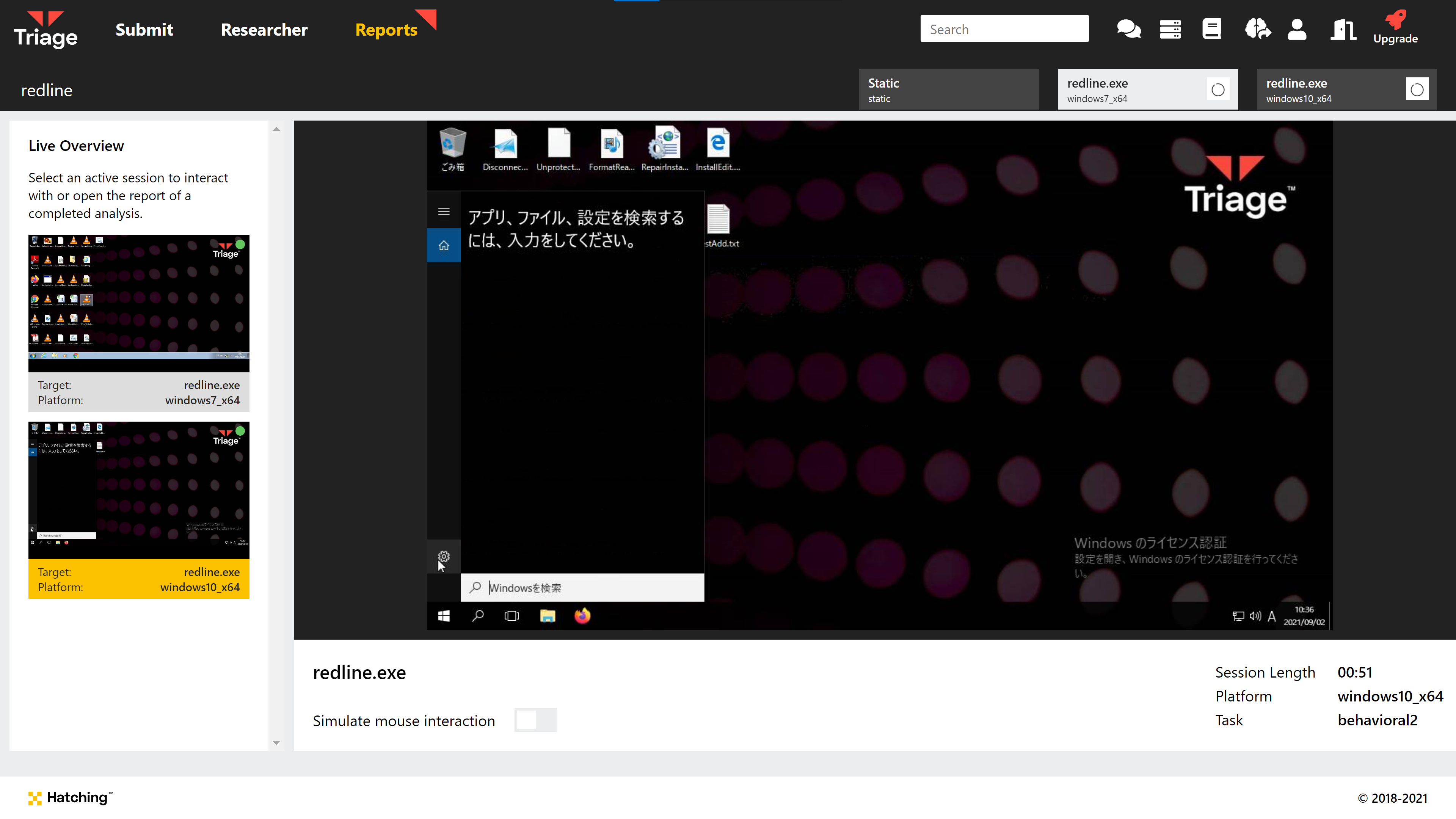
Advanced Submit
One of our most recent releases, our new Advanced Submit screen completely changed the way the submission process works through the web interface. This update served 2 main purposes - firstly, to better support features like profiles which we felt lacked utility outside of the API; and secondly to pave the way for the addition of new features in the future such as expanded network and language options.
We’re very proud of the new look, and hope you’ve been enjoying it too! Of course it also came with a few of its own completely new features as well, including a way to specify command line arguments for a sample during submission and a new submit method for scripts/code like Powershell or Javascript.
For more information and a detailed rundown of each new component, check out the blogpost on it here.
Emotet Powershell Parsing
A couple of weeks ago we covered an update to the way in which Triage parses and cleans up the Powershell code used by Emotet in its deployment chain.
This week we’re revisiting it to account for some recent changes in the family which weren’t working right with the existing handling. We have reviewed the latest samples and applied some tweaks which should improve handling for these, and indeed the family as a whole.
If you have any suggestions for further improvements to our deobfuscation and handling of Emotet Powershell please feel free to reach out! Hearing which aspects of it matter to you is extremely important and useful for us.
Bitrat
Bitrat is a fairly simple infostealer which is sold through underground forums. It was first observed in the 2nd half of 2020, and although it is fairly simplistic in its design it appears to have gained some popularity in the community.
Its design and implementation are poor compared to many of its more high-profile competitors, but it is still a significant threat to anyone who doesn’t detect it before it is run on a machine. Its operation is very noisy, and it appears to include a lot of reused code and 3rd party tools to perform its functionality.
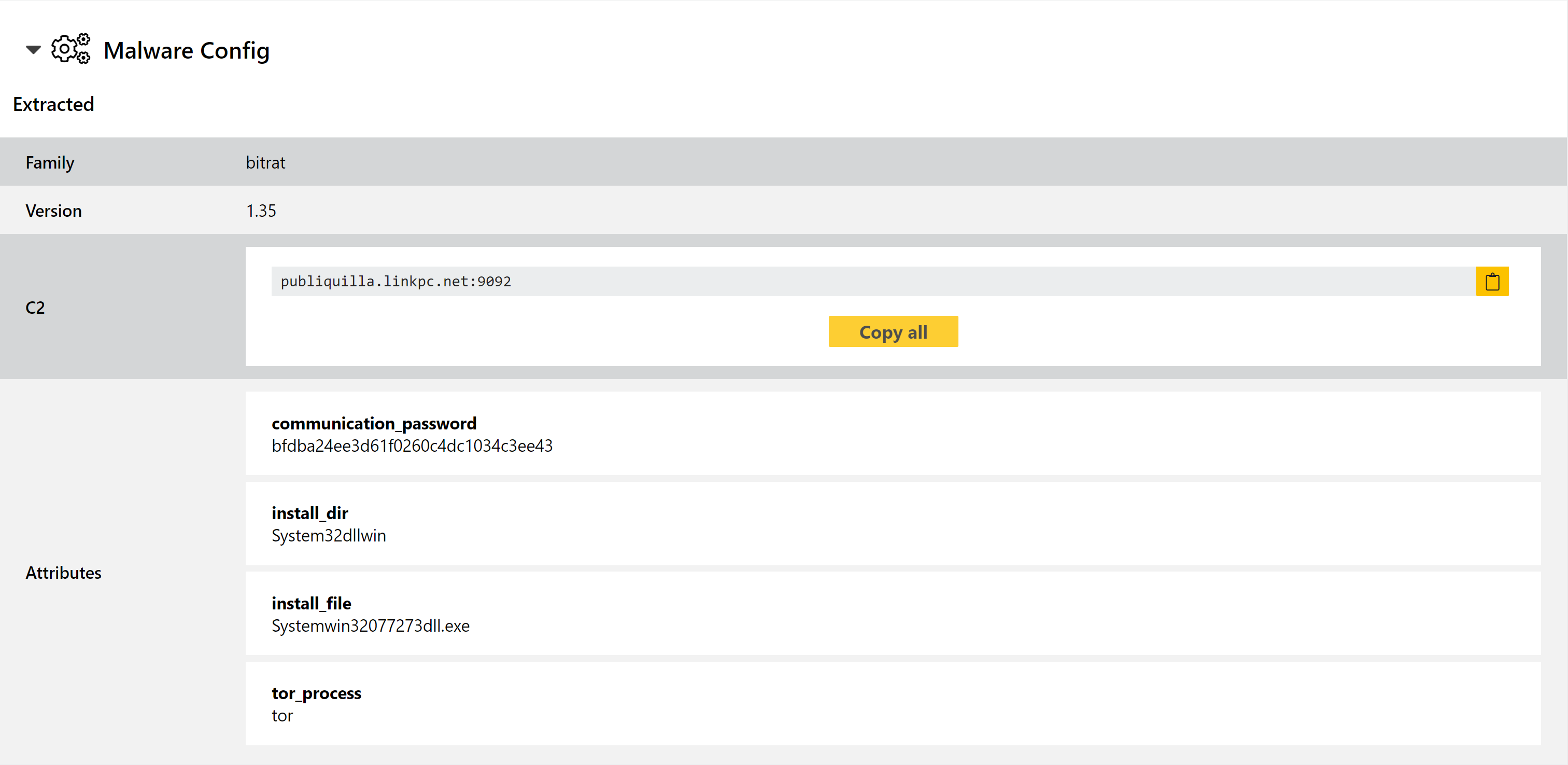
We added basic rules for the family back in January 2021, but since it continues to be a common sight on Triage we have revisited it to add a full configuration extractor.
Analyses:
XLoader
It’s been almost exactly 1 year since we added support for XLoader, separating it from our Formbook detections for the first time. Since then it has risen in popularity, largely (but certainly not entirely) replacing Formbook out in the wild.
For those not familiar with the name, XLoader is a ‘rebranding’ of the older Formbook family, reported by community researchers in late 2020.
Both families are stealers, with Formbook operating as a service since at least 2016. They include significant anti-VM and anti-analysis techniques which can present a unique challenge to automated analysis platforms like Triage.
The latest development in that direction has made it impossible for us to extract the legitimate C2 from the payloads. Since its creation XLoader has hidden its real C2 address among a large number of ‘dummy’ URLs, but thanks to our analysis we were able to get around that and identify which was the correct one.
Unfortunately the developers have taken the next step there, and all addresses included in the payload are now fake. The real C2 is only available at runtime by monitoring the responses to all of the domains checked meaning that we can’t now extract it using our current approach.
We’ll continue to look at ways to improve on this mechanism so that we can in future handle this, but for now we’ve decided to take the step to remove the old support for separating the real and fake URLs, meaning that the extractor now just provides all of them without differentiation.
Analyses:
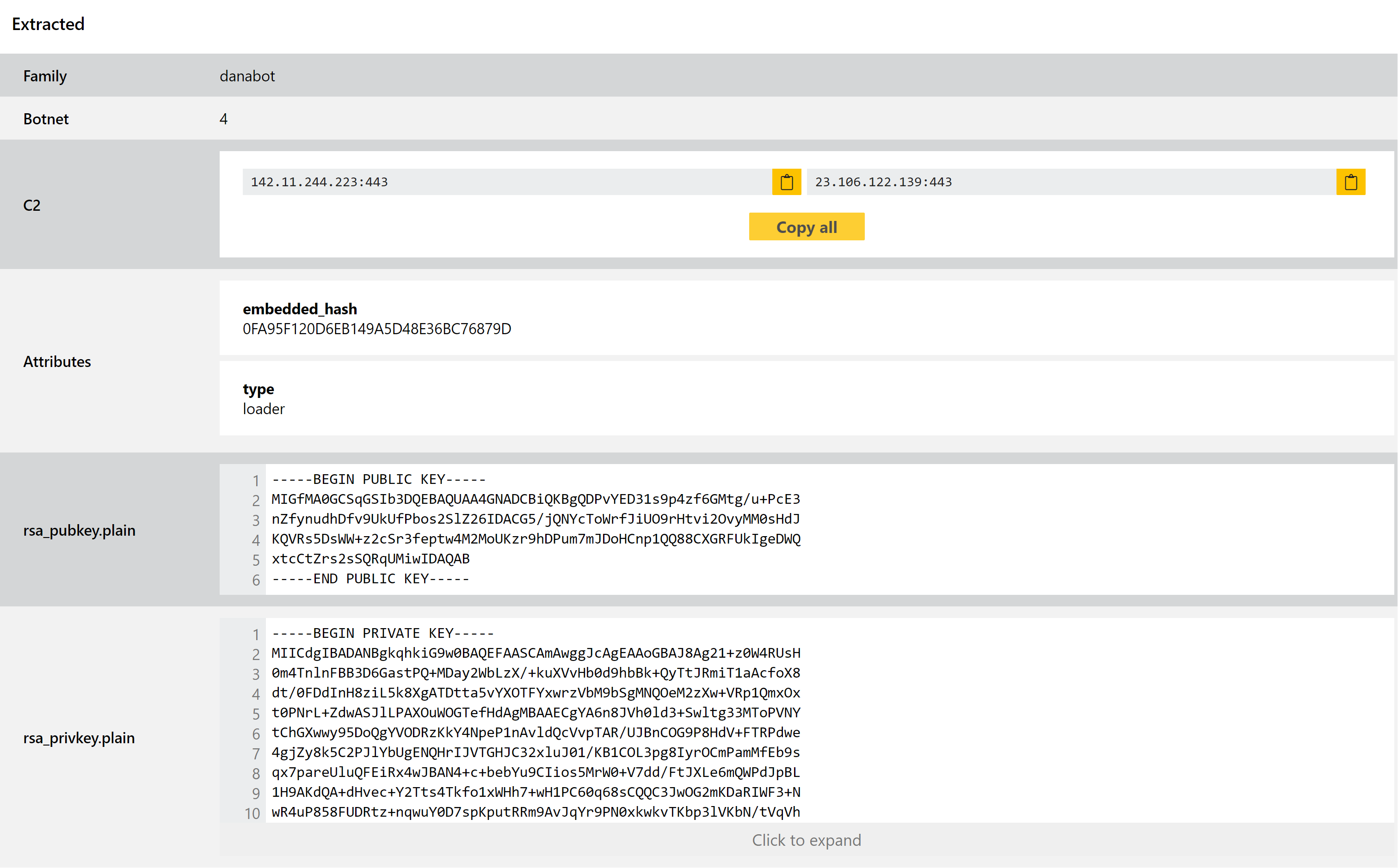
Danabot
Danabot is a banking trojan/infostealer which has been around in the wild since mid-2018. The family is modular with functionality for browser injections/network sniffing, stealing credentials stored locally by web browsers, FTP clients etc., and full remote access capability.
We have mentioned it a few times on this blog in 2021, first writing about it back in January after Proofpoint published research into a new variant that popped up around that time.
At that point we added a configuration extractor which dumped out C2 addresses and the payload version number. Some users of Triage have recently been requesting the addition of botnet/affiliate IDs to this output, so last week we revisited the family to add support for this. Now this information is also included, hopefully making it easier and quicker to track individual campaigns - as usual, this information is all searchable via Triage using the botnet: field.
Analyses:
Flubot
Flubot is an Android trojan/stealer first discovered in late 2020. Spread mainly via SMS phishing it gained attention earlier in 2021 after large scale spam campaigns against European users. The family was part of an overall trend with mobile malware, making use of lures related to delivery services like FedEx, DHL and Correos.
We recently observed some samples which were slipping past the detections we built back in May, so we have revisited the family to update it as needed. Some tweaks have been made to improve our coverage, and we’ll continue to keep an eye out for further variations.
Analyses:
Phorphiex
Phorphiex/Phorpiex is a worm and loader which infects systems and incorporates them into a botnet. It also often deploys additional payloads to infected systems such as cryptojackers, miners, or ransomware.
Until recently, a major aspect of the family was building a botnet which could be leveraged for other malicious actions. Using a payload all Tldr, it could take over machines and build them into a network controlled by the attacker from a central C2 server.
However that has now changed, after Phorphiex shut down its C2 infrastructure around mid-2021. As Checkpoint report in their recent blogpost, the family was inactive for around 2 months before one of the developers attempted to sell the source code through underground forums. The exact outcome of this is unknown, but shortly afterwards the C2 servers came back online at new addresses and began to distribute a completely new bot called Twizt, which replaces the original Tldr.
This new bot has changed a few things, chief among them being a P2P protocol which enables it to operate even when the central C2 is not available. To enable this to work it also has the ability to configure home routers to enable port mapping, ensuring that relevant traffic can make it in to the infected machine.
Based on the samples and findings reported by Checkpoint, we have reviewed the family and tweaked our detections to better catch this new version. Some examples are available below.
Analyses:
GlobeImposter Ransomware
GlobeImposter is a relatively minor ransomware family which has been around for a few years. It has never gained too much attention through the targets it has breached, but its long lifespan and regular usage mark it out as a legitimate threat and more than the skidware ransomware families that come and go all the time.
Unlike some of its more advanced peers it doesn’t appear to carry out exfiltration prior to encryption, apparently being designed more for generic attacks rather than targeted breaches against particular companies.
We have reviewed some samples observed recently, and implemented initial detections for the family and its ransomnotes. Some examples are provided below.
Analyses:
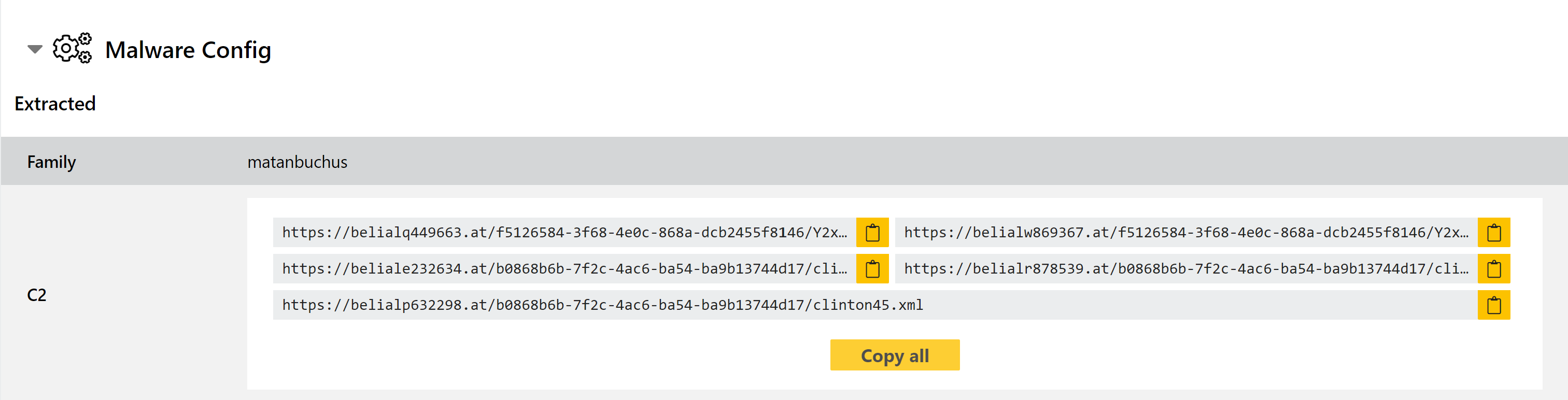
Matanbuchus Loader
Matanbuchus first popped up around February 2021 being advertised on underground forums. Advertised as malware-as-a-service, it can be rented out on a monthly basis by anyone looking to run their own campaigns.
The family includes fairly standard loader functionality including loading and running executables directly in memory; using schtasks to add or modify tasks on the machine; and PowerShell execution of commands/scripts. In addition, if the user has no existing infection chain in place the developer can provide a standalone launcher for the malware to get it started.
We have observed quite a few samples of this on Triage recently, and have now carried out a review to implement family detections. We have also been able to add a dedicated configuration extractor for it to dump relevant information.
Analyses:
