In Triage Thursday this week we take a look at the week’s detection updates for a range of families, and introduce a new feature: custom archive passwords
- Support for password-protected archive files
- DogeCrypt and Zhen ransomware signatures
- Updated Dridex configuration extractor
- New sLoad family signatures
- New Ratty family signatures
- New Matiex family signatures
As usual if you have feedback or suggestions about anything Triage-related don’t hesitate to reach out. You can get to us via the website or on Twitter.
Not signed up yet? Head over to tria.ge to sign up for a free account!
Password Protected Archive Files
Until now Triage has only supported encrypted archives (e.g. zip files) with common passwords - infected, malware etc. - which are often used when sharing samples with other analysts.
This update adds full support for encrypted archives, with the ability to specify the password at submission. Triage will then use this to extract the contents and process the files.
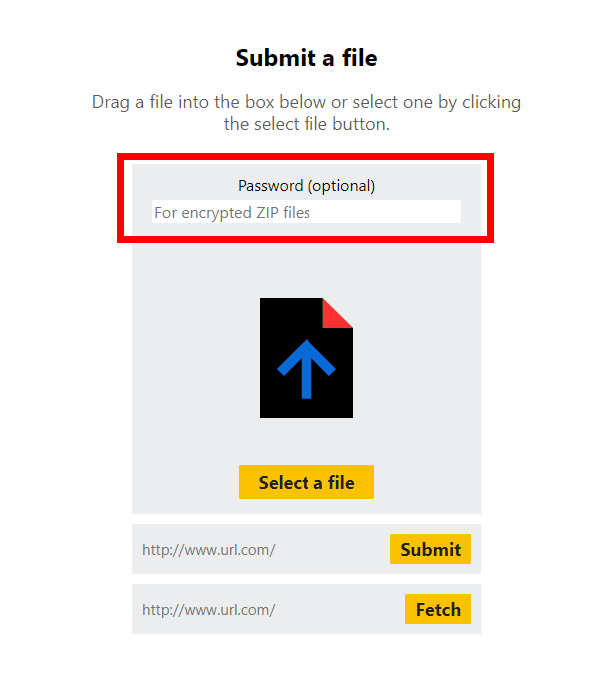
This option is also now supported by the API. Simply add a password field to the JSON data included with the submit request. For example:
curl -H 'Authorization: Bearer <YOUR_ACCESS_KEY>' \
-X POST \
-F 'file=@<YOUR_SAMPLE_FILE_PATH>' \
-F '_json={"kind":"file","password":"<ARCHIVE_PASSWORD>","interactive":false}' \
'https://api.tria.ge/v0/samples'
More information on using the API is available in the documentation.
Note: this password does not remain private - it is displayed on the static report output for all public analyses. This feature is intended for convenience, not submitting private/sensitive files.
Ransomware Updates
We have added coverage for a couple of new ransomware families seen in the wild.
DogeCrypt
DogeCrypt, based on the open-source ransomware desuCrypt, was reported on Twitter by a number of researchers earlier this month and a sample submitted to Triage.
The very brief ransomnote was avoiding our detection mechanism, so we’ve added a parser for the family to ensure it is extracted correctly.
Analysis:
Zhen Ransomware
Zhen is another new family that popped up this week. Unlike most ransomware which drop notes as either TXT or HTML/HTA format, this family writes it as read.ini in the C:\ProgramData directory. This seems like an odd choice considering that most users are extremely unlikely to discover the ransom instructions in this location, but apart from this it doesn’t have any particularly unusual features.
Files with the .ini extension are not handled by our ransomnote parser, so the note for this family is not extracted automatically. Note that manually renaming the file to .txt during analysis using Triage Monitor and opening it (e.g. in Notepad) will force dumping of the note.
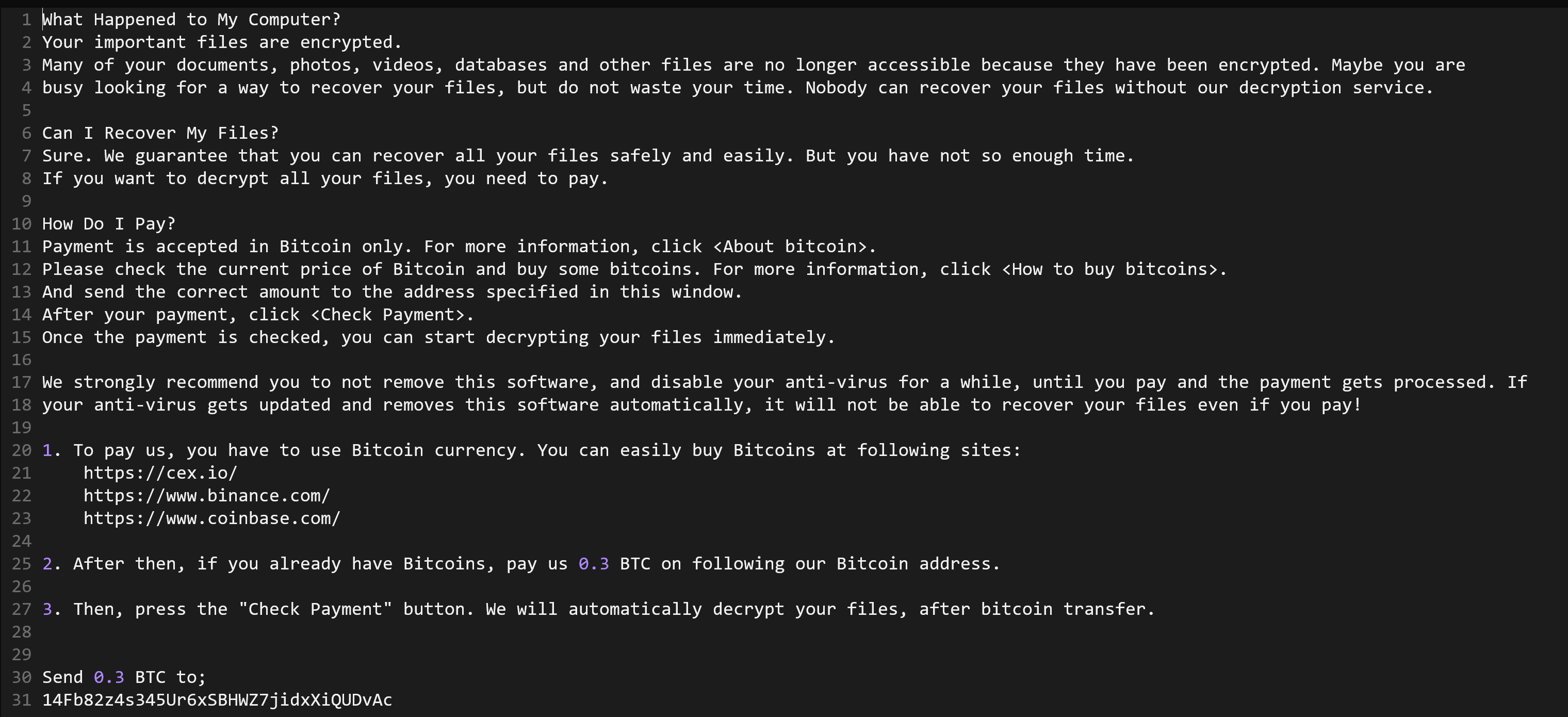
Contents of read.ini file
We have added general detection for the family. We will also be reviewing dumping triggers for examples like this in the future.
Analysis:
Updated Dridex Configuration Extractor
Dridex has been quite active lately, distributing a range of payloads. We recently observed that some samples of the family were no longer triggering our configuration extractor. Our yara rules have been tweaked to support the new version and extraction is working properly again.
Analyses:
- 200924-wfe8bfpfcx
- 200924-dbms9b5bsx
- 200924-wlea7y1aq6
- 200924-vga9ehvcke
- 200924-dhbsc5nbg2
- 200924-c9x67vtf3s
- 200924-yh1r3zmq62
New sLoad Family Signatures
sLoad is a malicious loader which has been around since 2018. However in early 2020 it saw a bit of a resurgence after releasing an updated and much improved version referred to as ‘sLoad 2.0’ or ‘StarsLord Loader’.
Initially written in Powershell, the family has evolved over time to make use of a range of different scripts. Early versions generally made use of VBS scripts as a wrapper or stager for the full loader, but the new 2.0 version tends to favour Windows Script Host (WSH) files.
We have added support for this family to Triage, and will expand this as needed in the future.
Analyses:
New Ratty Family Signatures
Ratty is a remote-access trojan (RAT) written in Java. It was open source prior to 2016/17 but multiple clones of the original repo exist.
The family makes use of an interesting trick to evade some automated detection methods. Although the malware is Java, by appending the Jar file to the end of an MSI file it can fool some static tools into thinking it is a different file type. However the way the Java runtime parses Jar files means that it still functions correctly when opened regardless of the attached MSI. A much more detailed explanation of this mechanism is available in the original writeup by Security-in-Bits.
Due to this trick, Triage recognises the file as MSI and attempts to run it as such. This means that automated analysis doesn’t yield behavioural results with default settings (although it is possible to submit the .jar alongside a script to launch it correctly - more info in our blogpost here). However we have added static detection to catch these samples regardless.
Analyses:
- JAR file launched correctly using BAT file - 200924-zxrhe9ncan
- 200628-4rx2t7sta6
- 200628-8f9kkdbne6
- 200628-ws5kwspvdj
New Matiex Family Signatures
Matiex is a keylogger with other infostealer capabilities such as capturing screenshots, recording video/audio, and stealing clipboard contents. It can also harvest stored credentials from a range of installed software.
The malware is sold openly through a website, operating on a subscription basis with 1 month costing $25.
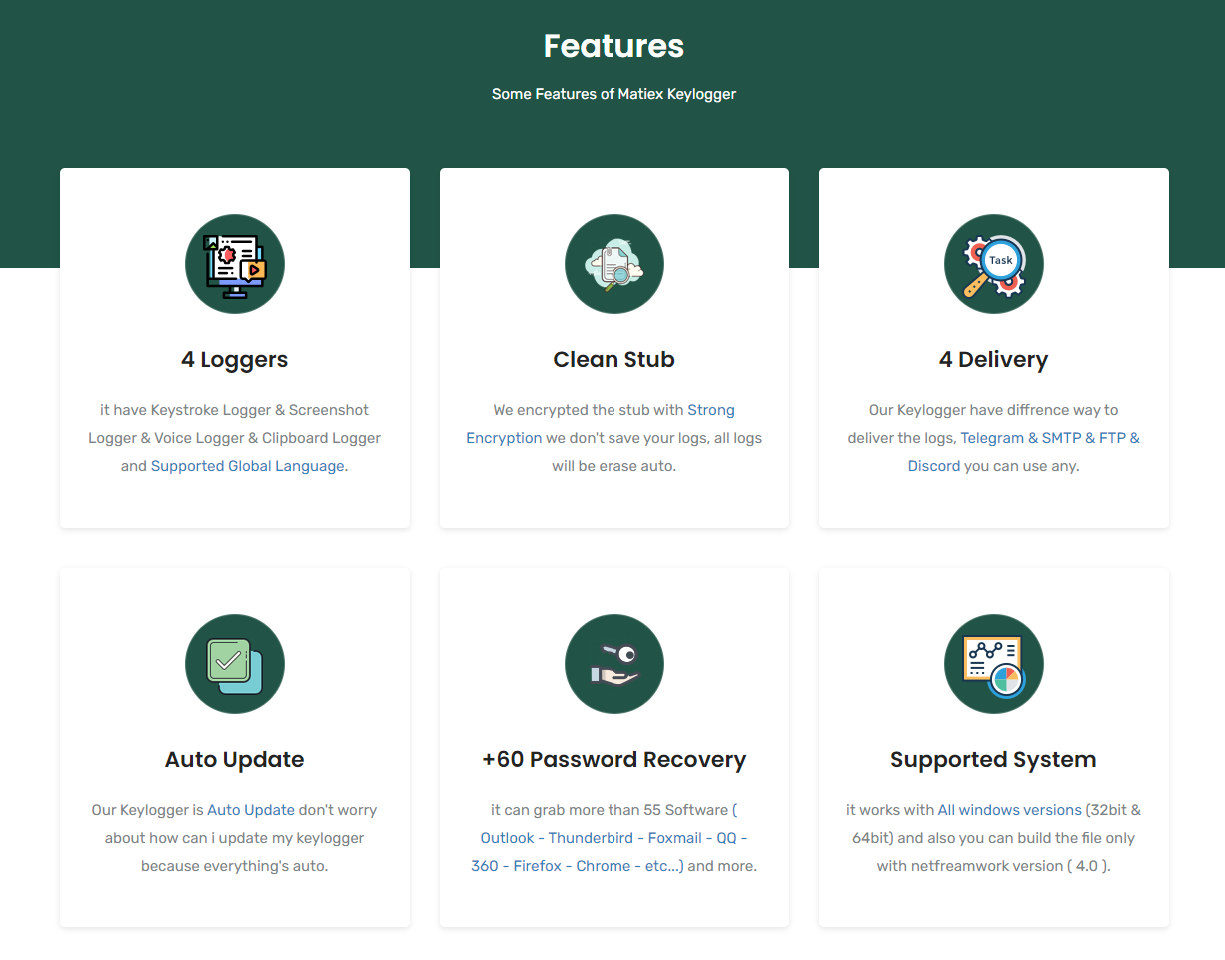
Features advertised on malware web page
We have added family detection for this family and will keep an eye on new versions as they appear in future.
Analyses:
