Welcome to another week of update news in our Triage Thursday blogpost! As usual we have several detection updates to go over, as well as a few brand new family detections:
- New Warzone RAT configuration extractor
- Buer detection update and new configuration extractor
- Further CobaltStrike updates
- Updated AgentTesla family detection
- Updated Remcos RAT detection
- Updated LimeRAT detection
- New Elysium Stealer signatures
- Balaclava ransomware support
We have also been working on some background changes to Triage itself to give a smoother user experience. Some analyses with large amounts of data were taking a noticeable amount of time to load when accessed through the web UI, with some extreme cases taking that to unusable levels. We have implemented some changes and you should now get much faster load times in general when accessing tasks.
We have some features coming up that we are looking forward to sharing with you, but that’s all from us for this week’s post. As usual you can find us on Twitter to keep up with the latest changes throughout the week, and be sure to send us feedback there or using the Feedback buttons in Triage.
Not signed up yet? Head over to tria.ge to register for a free account.
Warzone RAT Configuration Extractor
Warzone is operated as a service, sold to actors to carry out their own campaigns. We added detection for it back in October, but in today’s update we have expanded on this by adding a new configuration extractor for the family. This dumps the C2 URL directly from the sample to help with tracking campaigns.
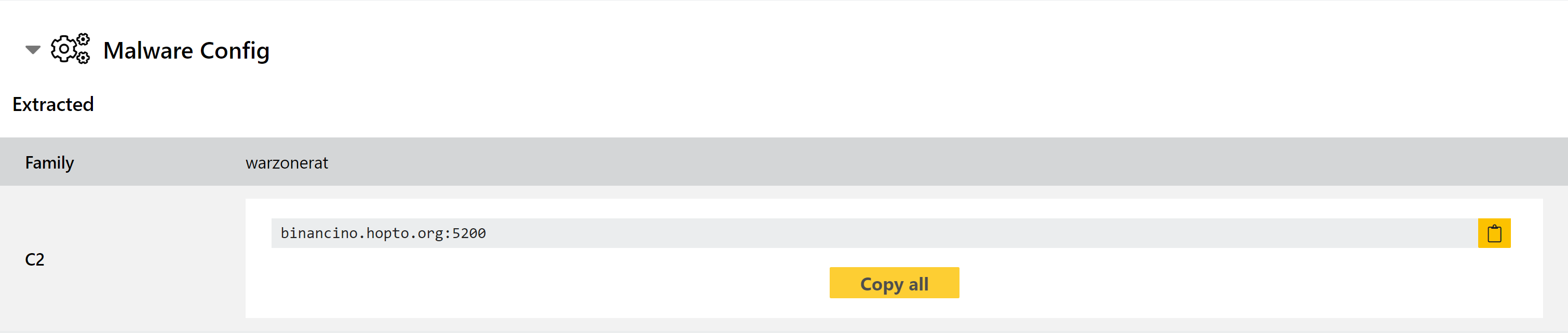
Analyses:
Updated Buer Detection and Configuration Extractor
We first added detection for Buer Loader back in October last year, and pushed some updates in December.
Buer has continued to gain in popularity in the weeks since, and we have been monitoring samples to see where we can make improvements. Based on this we have now implemented a configuration extractor for the family to augment the behavioural results, as well as tweaking some beahvioural rules to better support the newer samples.
Analyses:
Further CobaltStrike Updates
We introduced some updates for CobaltStrike samples last week which included a new configuration extractor. This week’s update extends this to also support extraction of the x86 reflective DLL loader used by CobaltStrike.
Some examples of x86 loader samples are listed below.
Analyses:
Updated AgentTesla Detection
AgentTesla is an infostealer which first appeared in 2014 and has seen widespread usage over the last few years. Written using .NET, it is a full featured stealer which can:
- Steal saved credentials from a wide range of web browsers and email clients
- Collect keys from various SSH/FTP clients
- Log keystrokes
- Harvest data from the clipboard
- Take screenshots and video
- Carry out form-grabbing attacks against login pages for common websites
- Gather saved credentials for known WiFi networks (first seen in early 2020)
It is openly sold through its own website (the name and location of which has changed over the years) claiming to be a legitimate monitoring program for personal computers, although user guides detailing malicious scenarios and the numerous evasion techniques implemented over the years mean this is clearly not the real intention.
Triage has supported signatures for AgentTesla for some time, but regular changes to the malware mean that variants have popped up over time which evade our detections. We have been carrying out a review of recent submissions and have implemented changes to improve coverage. We’ll be continuing to test these over the coming weeks and will push further updates as required.
Analyses:
Updated Remcos RAT Detection
Remcos is a remote administration tool sold online. Triage has supported family detection and configuration extraction for some time, but as is often the case the family has introduced some changes over time which have made our signatures less effective since we last covered it on the blog.
We have reviewed recent samples and updated our behavioural detection and configuration extractor to provide more complete coverage.
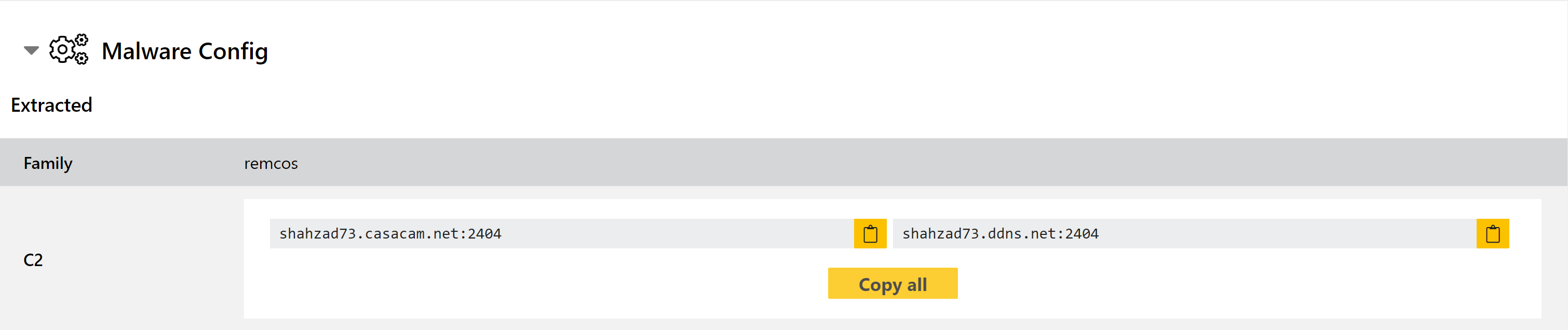
Analyses:
Updated LimeRAT Detection
LimeRAT is an open-source remote administration tool which is available on Github. It has an extensive list of supported features and is able to operate as a typical stealer, ransomware, cryptocurrency miner, or a bot for DDoS attacks etc. It also includes some anti-VM and anti-virus evasion techniques to help it remain undetected.
We have been reviewing observed samples related to the family, and have updated our signatures to better detect them.
Analyses:
New Elysium Stealer Detection
Elysium Stealer - previously known as Zeromax - was reported on Twitter in July 2020 by @3xp0rtblog:
It is mainly oriented towards financial information theft, targeting web logins for common banking and ecommerce sites.
We have taken a look at available samples and implemented detections for the family.
Analyses:
Balaclava Ransomware
Balaclava was brought to our attention back in October 2020 by ReversingLabs.
The family drops .txt ransomnotes to encrypted directories, and adds a custom extension to files - this often follows the pattern .[word]_New, e.g. .dave_New.
Analyses:
