It’s Thursday again, and that means it’s time for another entry in our weekly update blog series. Today we’re mostly focussed on family signatures again, but we do also have a useful improvement for the Tor networking support we added last week. Check out the list below for this week’s content:
- Added support for handling .onion URLs with Tor networking
- New configuration extractor for Quasar RAT
- Added detections for BlackRock Android banking trojan
- New signatures for Gafgyt Linux IoT botnet
- Updated detection for WebMonitor
- Improvements to DCRat detection
If you missed it over the last few weeks, we are also currently hiring a Go developer to join the Hatching team and help build the future of Triage. If you think this might be of interest to you or someone you know, the full job listing can be found here - feel free to reach out with any questions.
You can also contact us with any feedback or suggestions about Triage or the analyses it produces - we’re always keen to hear from you. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Added Support for Onion URLs
Last week we added Tor network support to Triage, enabling you to route all traffic from the analysis VMs through the Tor network. We have now extended this slightly to better handle .onion URLs, i.e. URLs pointing to Onion services only accessible through the Tor network.
With this update, submitting a .onion URL with default analysis settings will automatically launch a Windows 10 VM with Tor networking enabled, and open the link in a relevant web browser.
You can of course force other options through Profiles or analysis settings, but you no longer need to do anything to make the submission work properly.
New Configuration Extractor for Quasar RAT
Quasar is a remote administration tool for Windows which is used maliciously by a wide range of attackers. The malware is open-source, being available to download from GitHub, and as such is a popular choice for those looking for an out-of-the-box solution or one which can be easily modified to a particular use-case.
The availability of the source code means that multiple variants have popped over the years such as Velgax, which we added detection for back in January this year.
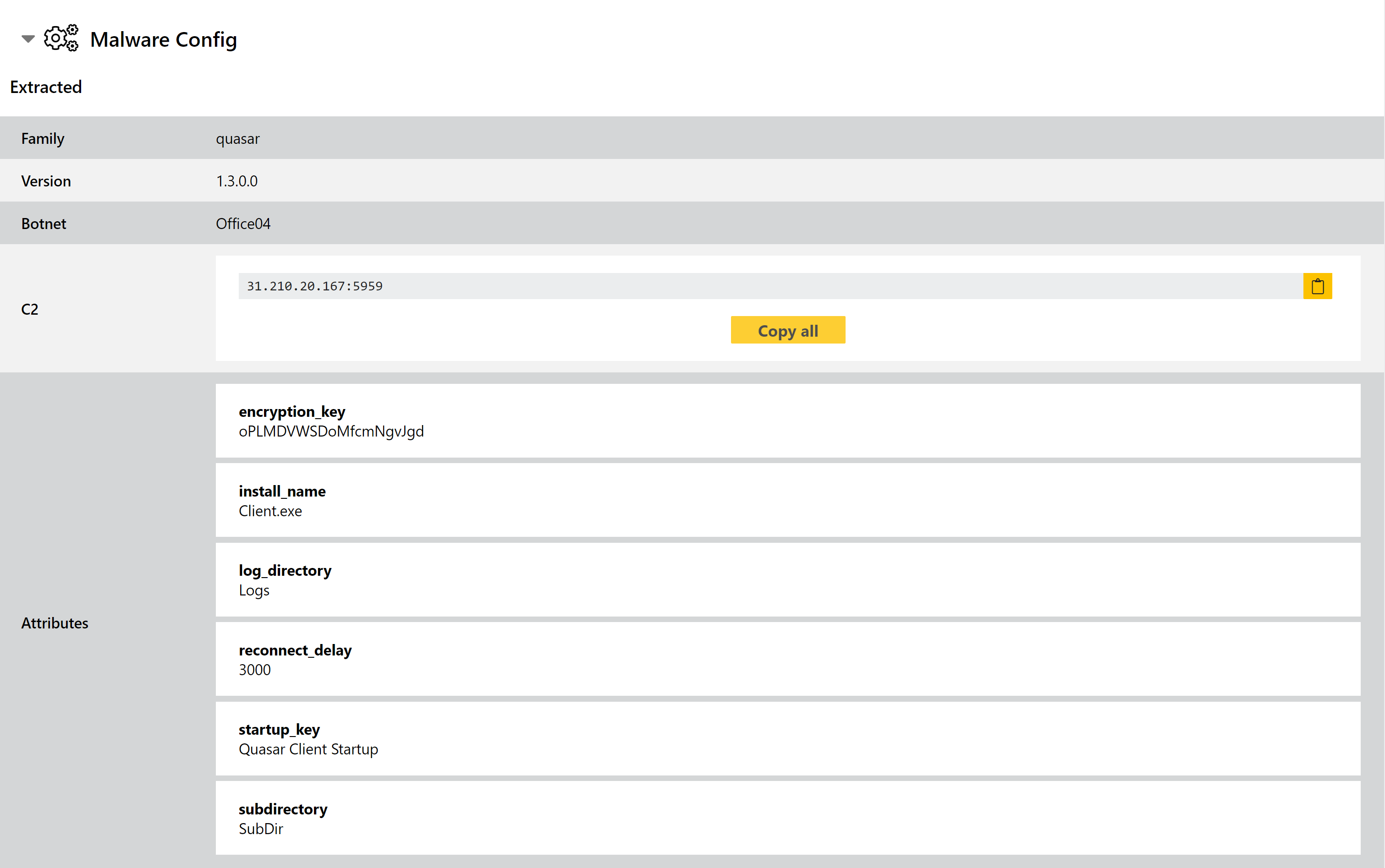
In this week’s updates we have deployed a new configuration extractor for the family, which dumps available settings from the binary - C2 addresses, file and registry names, encryption key etc. The extractor was developed based on current samples, and we will be carrying out reprocessing of the family over the next few days - if we identify variants not covered by the extractor then we shall make further tweaks as needed.
Analysis:
Added Detections for BlackRock Android Banking Trojan
BlackRock has been around for a year or so, with early reports going back to May 2020. However the codebase goes back further with strong links to the Xerxes banking trojan, the source code for which was leaked online in 2019. Xerxes itself is a fork of the even older LokiBot Android malware.
With its strong reliance on existing families there isn’t a lot unique about BlackRock - it is a full-featured Android RAT and stealer which can target data both at rest and during live interaction with various applications on the mobile device. Where it stands apart from many other Android families is its target list, which besides the usual banking and financial applications also includes a wide range of social, communication and dating apps. ThreatFabric suggests this is likely an attempt to cash in on the increase in use of such applications during the Covid-19 pandemic.
We have added signatures to detect the family and apply the relevant tag. You can find a couple of recent examples below.
Analyses:
New Signatures for Gafgyt Linux Malware
Gafgyt is an old threat for Linux, with early versions dating all the way back to 2014. Although it never achieved quite the same infamy as its younger relative Mirai, Gafgyt has been enormously successful over the years and now includes a vast range of variants and spinoffs.
The malware targets IoT devices such as routers to form a botnet which can then be used to carry out additional attacks, especially DDoS. Different versions leverage a wide array of exploits/CVEs from the last several years depending on their creation date and particular set of targets. It has continued to evolve to this day, adding new features and techniques as they become available.
We have reviewed the samples of Gafgyt available on Triage and have implemented signatures for the family. Some examples are below.
Analyses:
Updated detection for WebMonitor
We added basic detections for WebMonitor a couple of months back, and this week we’re applying some updates to improve and expand on these based on recent samples.
WebMonitor is another RAT openly sold through its own website as a legitimate administration tool. However as is common with these applications the feature set strongly suggests that it is designed for less legal use cases, including things like stealth installation and secure, robust C2 communication.
Based on recent samples, we have improved static detection for the family to make it more reliable.
Analyses:
Improved DCRat Detection
DCRat last popped up in one of these blogposts a couple of months ago, with a detection update based on samples from the first few months of 2021. We’ve been keeping an eye on the family since then, and this week pushed some more improvements to account for recent changes in the samples we’ve observed.
DarkCrystal RAT, more commonly known as DCRat, first appeared in late 2019 providing an extensive set of functionality to its users. A detailed breakdown of the family can be found in FireEye’s report from May 2020.
Analyses:
