Welcome to today’s Triage Thursday update blogpost. We’ve been carrying out a bit of a review of past samples on the public server this week, as we’ve made some improvements to our indexing and search abilities for the public Triage server which have made it easier to identify samples which aren’t behaving as expected.
Below are brief descriptions of several small updates and tweaks we’ve made, aimed at improving our configuration extractors’ coverage of several families.
- Added new AZORult extractor
- Updated Trickbot extractor
- Updated Dridex extractor
- Updated Smokeloader URL parsing
- Updated Remcos RAT C2 extraction
Stay tuned here and on Twitter for all the latest updates and changes - we’ve got some cool new things in the pipeline which we can’t wait to get out to you.
Not signed up yet? Visit https://tria.ge/signup to sign up for a free account!
Splunk Phantom and Cortex XSOAR Integration
We are always looking for new ways to make the information generated by Triage more accessible and useful to organisations. As such we are pleased to share that Triage integration is now available for Splunk Phantom and Cortex XSOAR.
We will publish a blogpost covering these integrations in more detail in the next few days, so keep an eye on our Twitter and blog for more information!
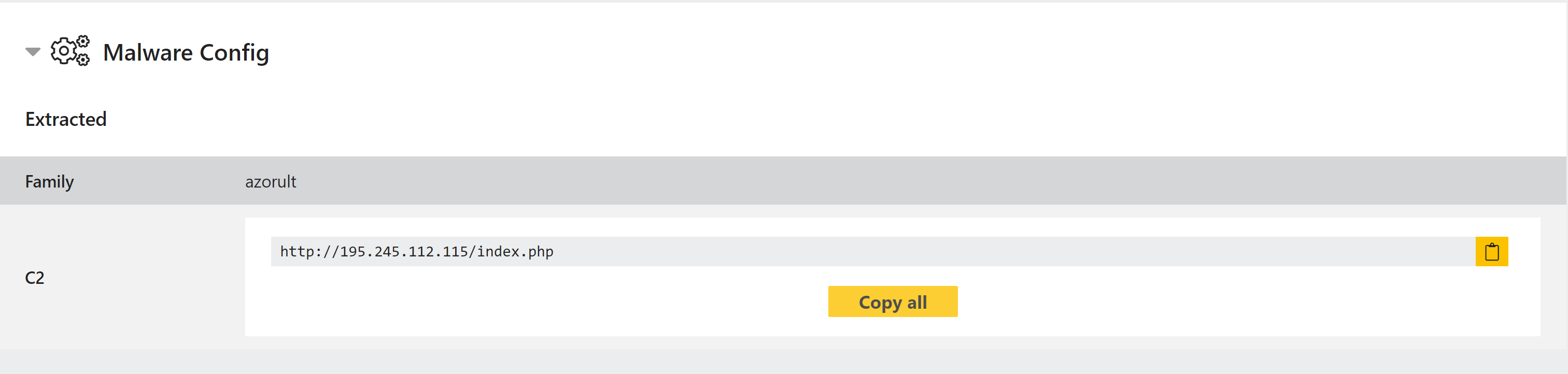
New AZORult Configuration Extractor
AZORult is a stealer which has been around in some form since 2016. It has the capability to harvest information from a wide range of applications, such as browsers, email clients and messaging platforms like Skype, cryptocurrency wallets, and the Steam gaming platform. It also enables remote access for an attacker, and can act as a dropper for other malware.
Triage has supported family identification of AZORult since very early in development, but we have recently revisited it to implement a configuration extractor based on samples we recently observed. This will extract the C2 IP/URL regardless of whether or not the sample ran successfully or the C2 is still active.
Analyses:
Trickbot Extractor Update
Trickbot has once again made its way into our todo list, with another update that interfered with our configuration extractor. This change introduced a fake C2 IP/port combination intended to throw off analysis. We’ve updated the extractor to account for this and only report the legitimate C2 addresses.
Some specific examples are listed below, but you can find more using the search query botnet:tar2.
Analyses:
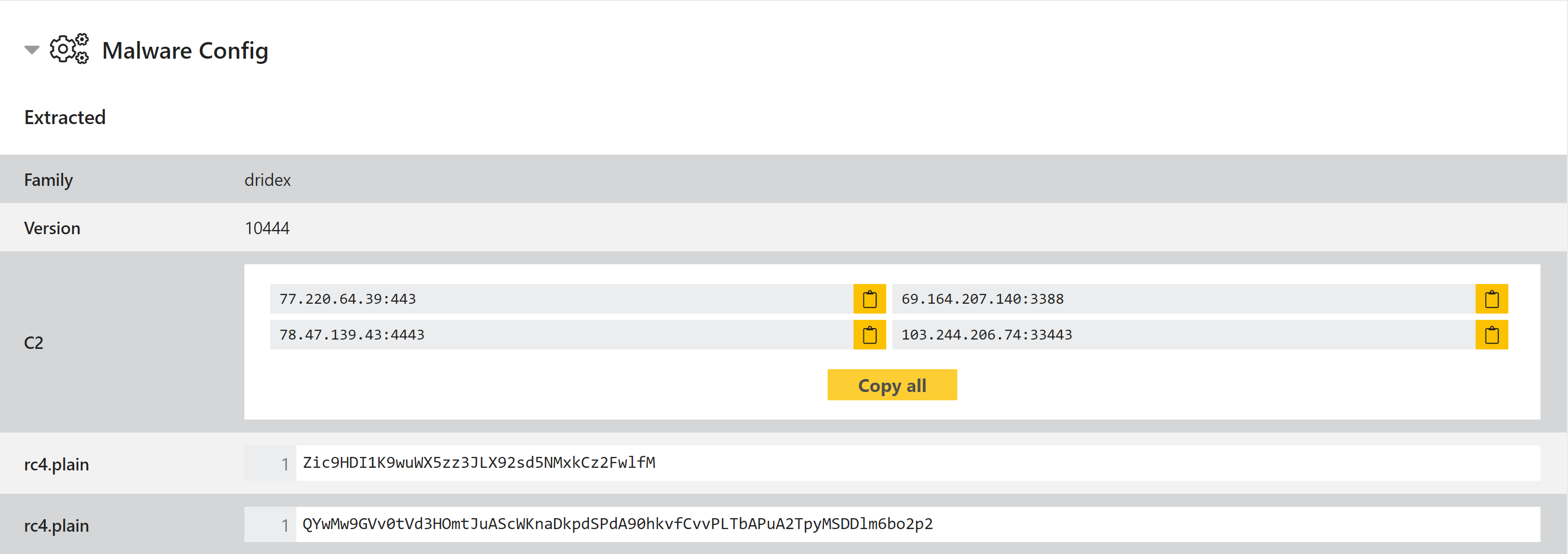
Dridex Extractor Update
While reviewing older samples we came across some Dridex versions which were not being processed by our configuration extractor. Most of these were not recent, but we have updated our Yara rules to make the extractor support a wider range of samples.
Analyses:
Smokeloader Update
Smokeloader continues to be highly active, and we have observed a number of different campaigns over recent weeks. A new version seen in the last few days changed up the URL decryption function and evaded the extractor, so we’ve reviewed the samples and pushed an update to correct this.
We’ve also noticed that in many cases Smokeloader is deploying several different payloads in a single analysis. However this is not always completed in the default 2 minute timeout, so it is recommended to submit these for 5 minutes or longer to get the full report.
Analysis:
- 201107-lxpdbv9h4n (2 minute timeout)
- 201110-tjrd82d9ee (5 minute timeout)
Remcos Extractor Update
Remcos RAT is a remote administration tool available for purchase through a company called BreakingSecurity. It is a highly customisable and fully featured RAT which provides backdoor and stealer functionality.
We have pushed a small update to our existing Remcos configuration extractor to handle some samples we identified which were previously slipping through. Some of these samples are listed below.
Analyses:
