We didn’t publish a Triage Thursday blog last week, but we’re back today with another set of updates to show you. We’ve made changes to a few different areas this week. As usual we’ll briefly go over the changes and link to some examples in this blogpost.
Also, in case you missed it, we released Linux analysis support earlier this week.
- Search feature updates
- Updated Qakbot handling
- Updated IcedID detection
- Hancitor family detection and configuration extractor
- Static PyInstaller detection
- XMRig cryptocurrency miner detection
- Updated FakeAV detection
- General PDF dropper techniques
- Updated detection of CryptOne packer
If you find any issues or come across samples which aren’t behaving the way you expect, please do send us feedback! You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Search Term Updates
Over recent weeks have been deploying minor tweaks and updates to the Triage Search function, and today we have pushed another which adds some new filter options.
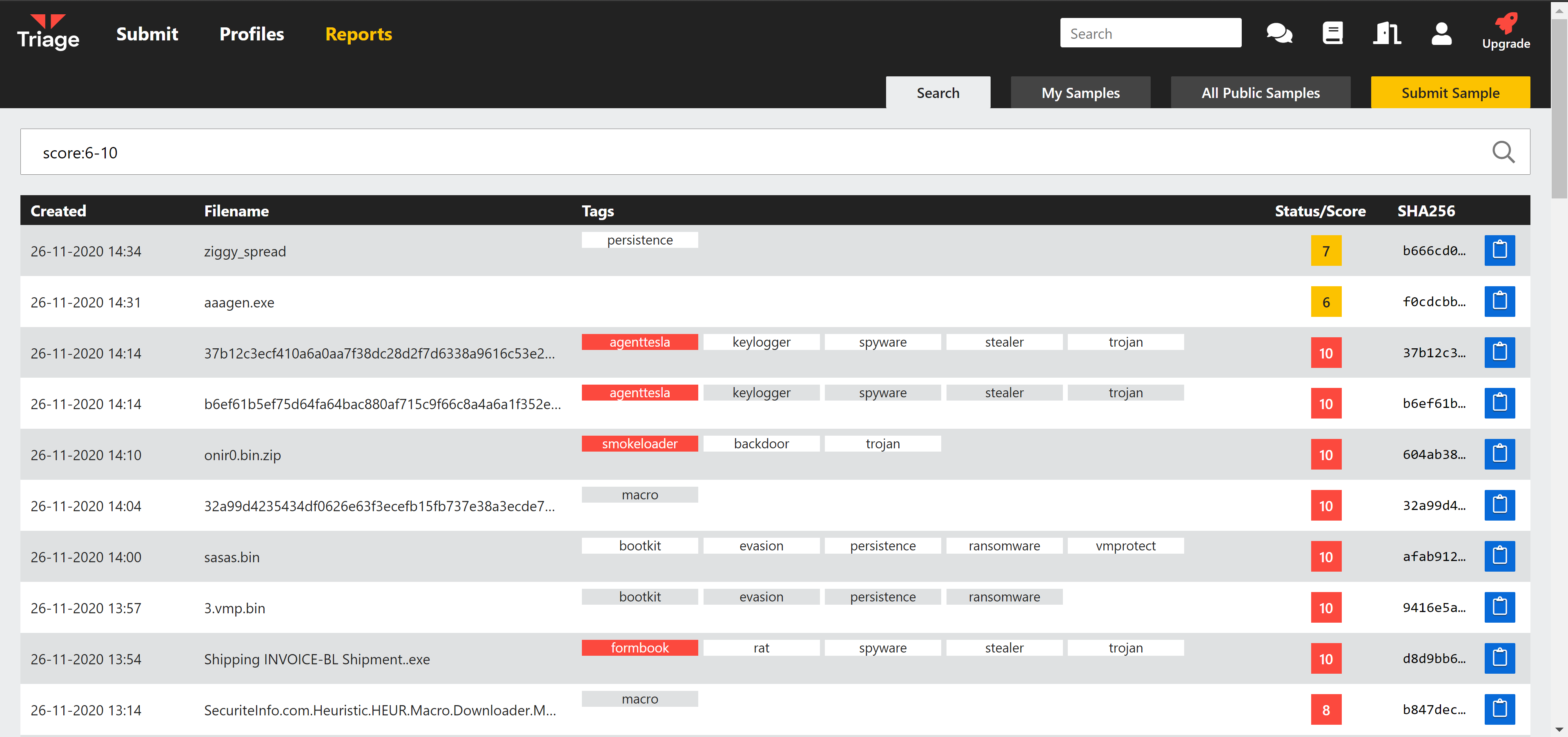
Filter by analysis score
Previously a search for analyses which have scores within a range of values required a chain of AND score: filters. To simplify this we have updated it to also support a range value. For example score:6-10.
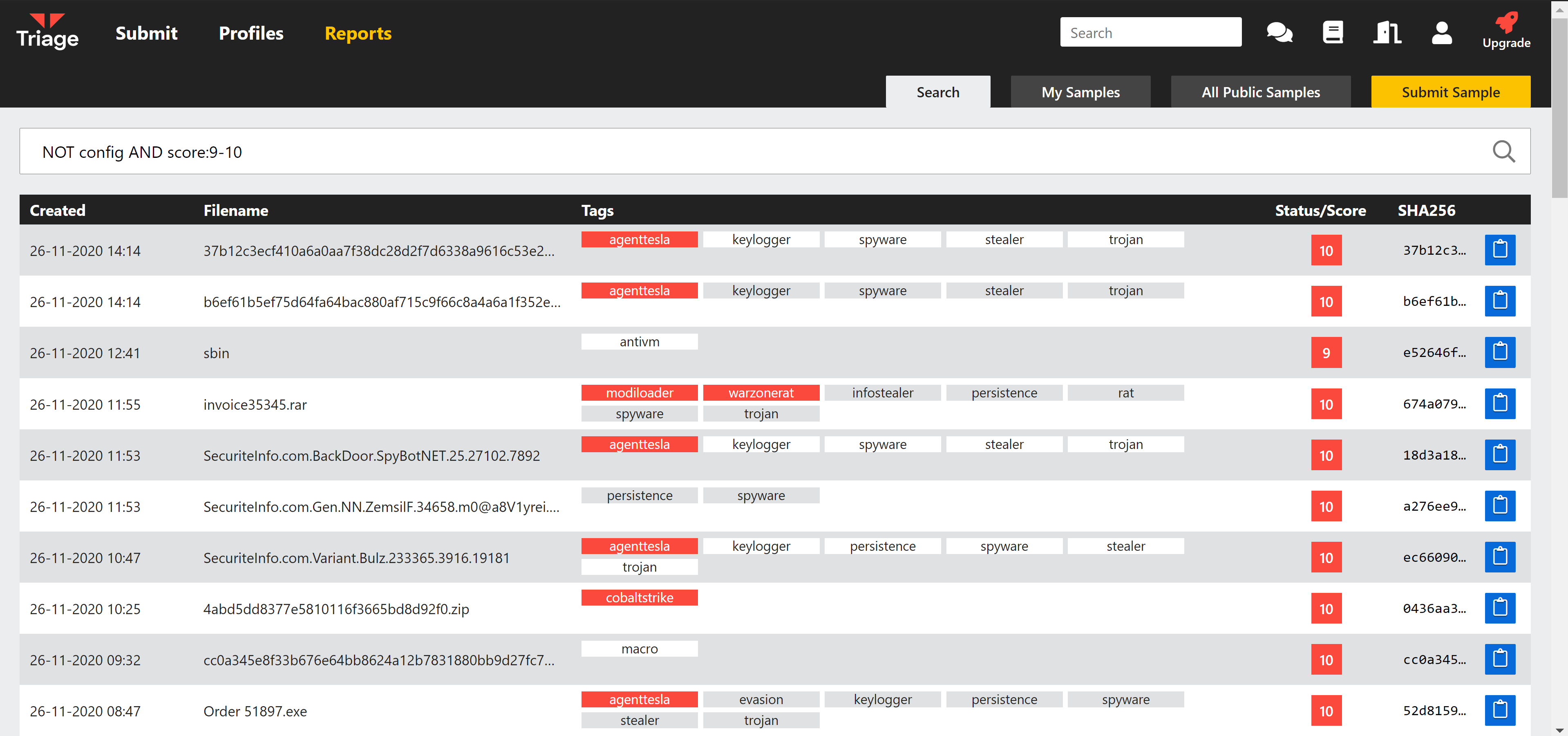
Filter samples with extracted configurations
For some families our configuration extractors do not cover all variants, especially older ones. To help find only those analyses which have a configuration associated we have added the boolean filter config. This can be used in conjunction with logic operators like AND or NOT to combine it with other filters. For example
family:emotet AND config
NOT config AND score:9-10
Updated Qakbot Handling
Yesterday we observed some new Qakbot samples which were not being handled correctly by our signatures and configuration extractor. Some minor changes to the binary structure were causing issues with the parser and returning no results. We have taken a look at them over the last 24 hours and extended our extractor to dump them correctly. A few examples can be found below.
Analyses:
Updated IcedID Signatures
IcedID, often known as Bokbot, is a banking trojan which steals financial information from infected machines. It has been around in the wild since 2017, and has consistently targeted business users in North America in industries associated with finance and ecommerce.
The malware includes the ability to carry out Man-In-The-Middle attacks against browsers to intercept banking credentials, and can also be a dropper for additional modules and payloads.
We recently updated Triage to support executing DLL files with regsvr32.exe instead of rundll32.exe, and IcedID was one of the families affected by this change. We have now added identification for the family itself, using behavioural and static detections.
Analyses:
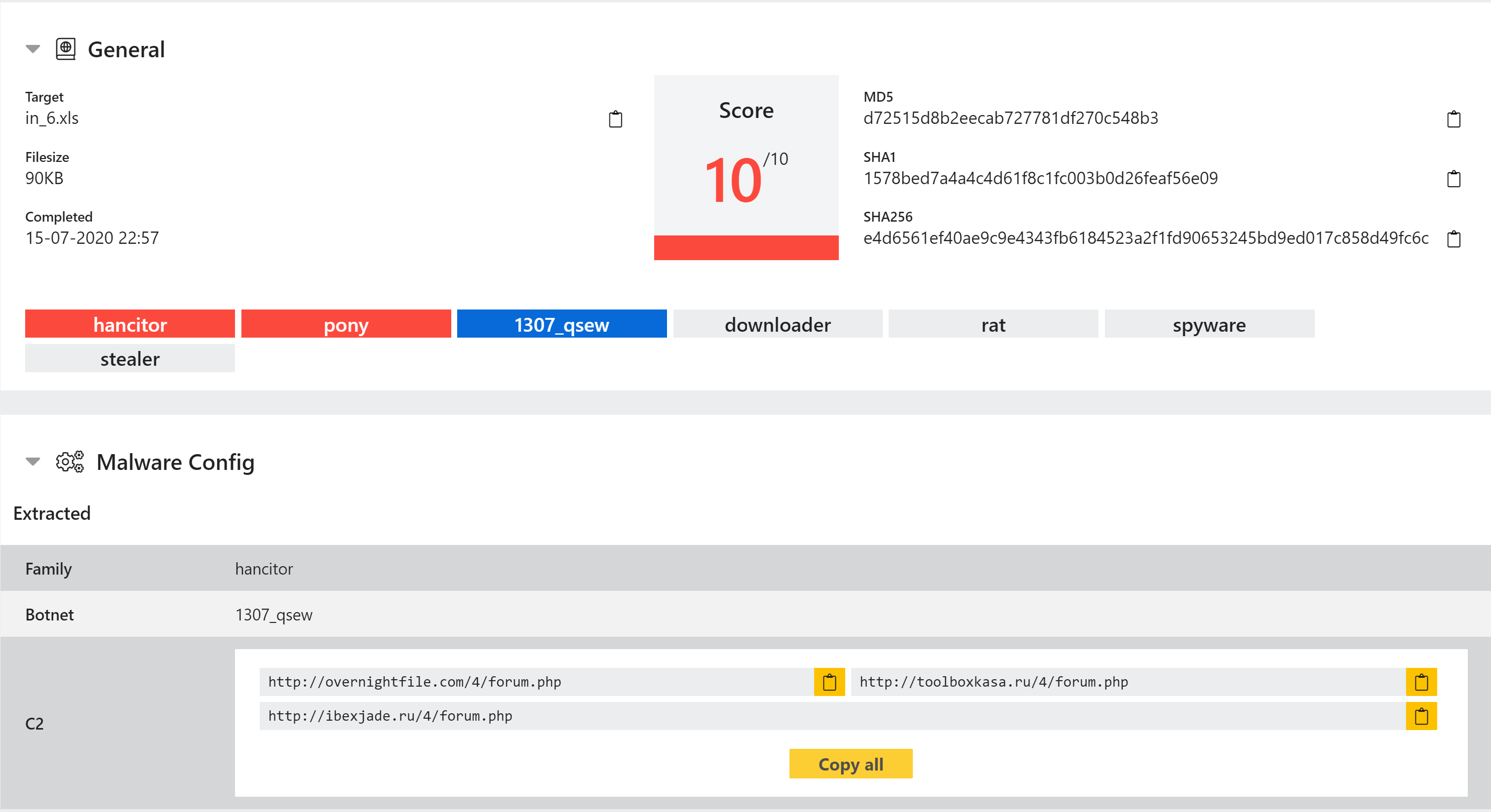
Hancitor Configuration Extractor
Hancitor is a dropper/loader which has been around since 2014. It is sold by the developers for others to use in their campaigns, and is generally deployed through phishing emails.
We have added detection for the family to Triage. Some variants of the family also now have a configuration extractor which dumps the botnet campaign ID and C2 information.
Analyses:
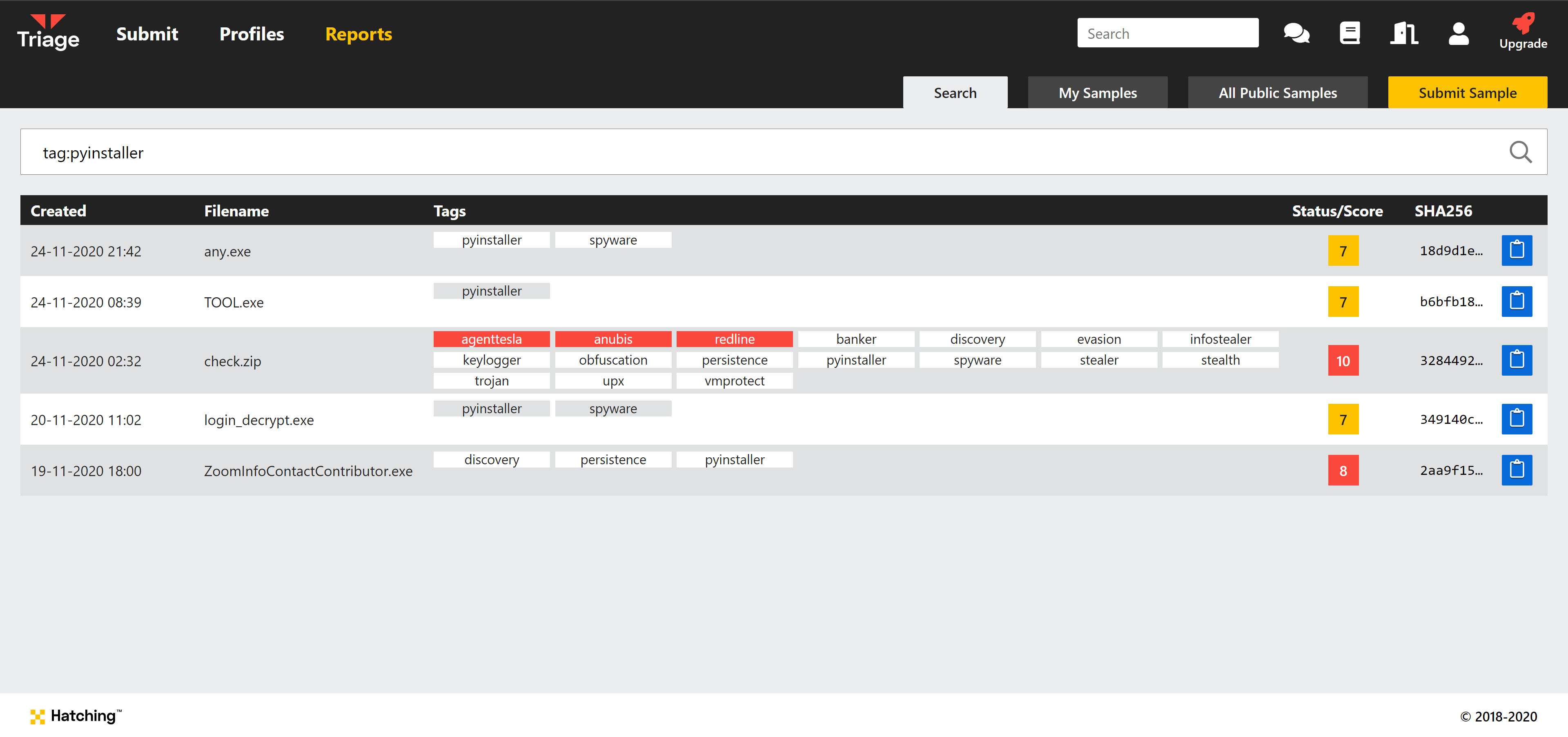
Static PyInstaller Detection
PyInstaller is a legitimate packaging program for Python executables. It is designed to ensure cross-platform compatibility and to minimise file sizes with compression.
These features make it a useful tool for malware authors trying to get their software past detection, and ensure it runs on as many systems as possible. We have added static Yara detection for PyInstaller to mark samples which make use of it. We do not consider it to be an indicator of malicious intent on its own as it is primarily used in a wide range of legitimate software, but it will show a low-score result in the static report and assign the analysis with a tag which can be used in Search queries.
Analyses:
XMRig Cryptocurreny Miners
XMRig is an open-source cryptocurrency miner which is widely used legitimately. It is cross-platform and can make use of the CPU and/or GPU, making it also appealing to malware authors looking for a robust miner to install onto infected machines.
Again, this is not something we consider malicious on its own but we have added static detection of the tool so that it is easier to identify and find analyses which involve it. These will be assigned miner tag to help with finding similar analyses through Search (this will also be assigned by any other miners we add detection for), and they will also be marked with the XMRig family tag.
Analyses:
Improved FAKEAV Detection
FAKEAV, also known as RogueAntivirus, is more of a PUP than true malware. It spams fake anti-virus notifications to the victim trying to panic them into paying for supposed anti-virus software to fix their PC, but it doesn’t exhibit other behaviour beyond its persistence mechanisms and various registry modifications to access the Windows notifications system.
Triage has previously supported detection of FAKEAV, but we have recently reviewed some additional samples and updated our rules to cover more variations.
Analyses:
General PDF Dropper Techniques
Based on our reviews on recent samples we have added some static detection methods for PDFs, intended to catch general behaviours which are generally associated with droppers.
These are not linked to particular families, and are intended to provide users with more useful information in the report. In general these are not associated with high scores, as they are all legitimate components of the PDF format, but we believe them to be worth reporting during analysis. Some basic examples can be seen below.
Analyses:
Updated CryptOne Packer Detection
Back in October we added static detection for the CryptOne packer, which has been used in conjunction with families such as WastedLocker and ZLoader.
We recently noticed some new samples of the family which had small differences in their code which evaded our original rules. Updated signatures have now been deployed to cover these variations.
Analyses:
