Welcome back to our Triage Thursday blog series! It’s a short one this week, as we’re currently working on a lot of things which aren’t quite ready just yet, but we still have a few things to introduce so let’s dive in!
- Temporary Onemon tweak to bypass certain domain checks
- Added signatures for new AtomSilo ransomware
- Improved detections for STRRAT
Before anything else though, we’d like to give a shout out to our partners over at Sekoia.io. They’ve today published a new intelligence report on Bazarloader and its C2 infrastructure which heavily draws on the results generated by Triage for its IoCs. It is only available to subscribers but you can sign up for a free month of their FLINT reports - which provide concise, accessible information on current threats - on their website here: sekoia.fr/flint.
As always, if you come across anything unexpected while using Triage please do send us feedback - it’s very valuable in letting us know what’s currently important to users. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Onemon Update for Domain Checks
In recent weeks customers have passed us a few samples which have been failing to run in our VMs due to a simple check failing. The samples shared with us are VBScript which, once deobfuscated, essentially check %LOGONSERVER% against %USERDOMAIN% and only execute the malicious code if this is the case. Note that on a regular VM, these will be mostly similar, but on an AD-connected machine they will be different.
Due to the configuration of our VMs, this check was actually failing and resulting in no results from the analyses.
In future we plan to have full AD simulation options which will make this irrelevant, but of course that is a fairly large feature which will take some time to come to fruition. As such we wanted to implement a temporary workaround to ensure that these samples run correctly in future.
We have made a small change to Onemon - our kernel agent which manages analyses, collects results etc. - so that fake values are returned for these environment variables which better resemble a machine which is not totally isolated. Hopefully this should ensure more reliable execution for loaders like this.
If you come across any other mechanisms like this which Triage does not handle well, please do let us know! We’re always on the lookout for new ways in which malware is detecting and/or evading the sandbox and are keen to deploy fixes if any exist.
AtomSilo Ransomware
AtomSilo is a new ransomware family which was first observed in late September 2021, taking its name from the threat group behind its development which is referenced in the ransomnote.
The family seems to have drawn inspiration from a few existing sources with a ransomnote that closely resembles that of Cerber; an extortion/data leak site which is copied from BlackMatter; and code and general behaviour very similar to LockBit. As with most ransomwares these days it also leverages the double-extortion technique of exfiltrating files before also encrypting them, so that they can use the threat of leaking information to encourage ransom payment.
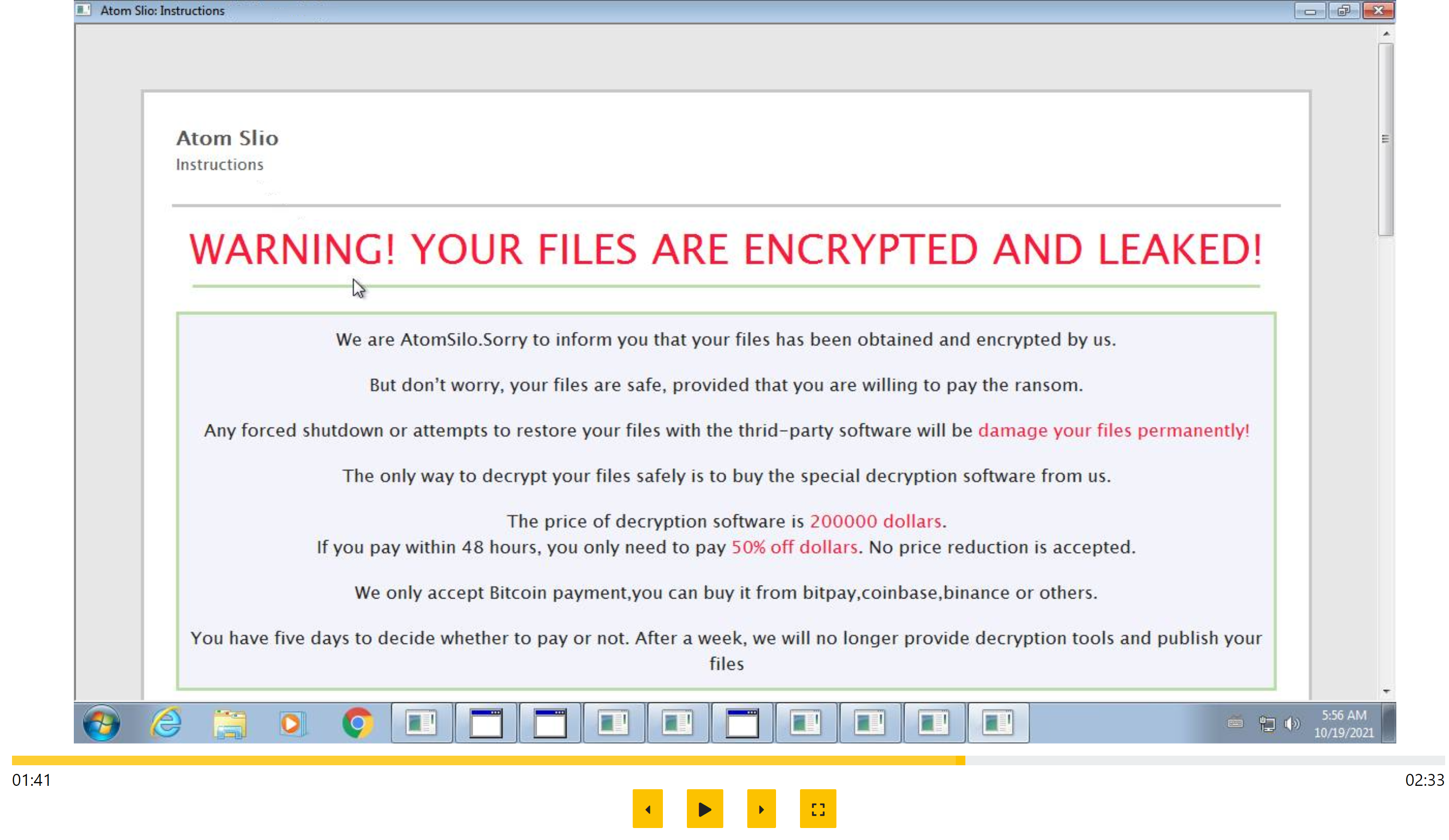
Although its history is currently short, based on the first reported breach it appears that the family is intended to be used in more targeted attacks where initial access has already been gained through other means. Sophos reports that a vulnerability in Atlassian’s Confluence software enabled attackers to gain access to the network, whereupon AtomSilo was later deployed to the affected systems. Notably the gap between initial access and deployment of the ransomware was 11 days long, perhaps implying that the operators are using other groups as access brokers.
We have taken a look at the samples and implemented some initial detections for the family to ensure it is tagged correctly. We’ll review our ransomnote strategy in the near future since this family seems to be causing Triage to dump the note multiple times, but in the meantime your samples will be correctly identified.
Analyses:
STRRAT
STRRAT is a Java-based stealer and remote backdoor which was first observed in the wild around mid-2020, although it has seen far more activity in 2021.
It generally carries out credential theft by extracting data from local files related to browsers etc. and by installing a keylogger. It has also been previously reported to include a fake ransomware module, which appends file extensions but without actually encrypting any data.
More recently Brad Duncan at Malware Traffic Analysis published a blog which reports that the family does not even need Java to be installed on the victim machine now - it can also come bundled with its own envrironment. To steal from his blogpost:
During this infection, STRRAT was installed with its own JRE environment. It was part of a zip archive that contained JRE version 8 update 261, a .jar file for STRRAT, and a command script to run STRRAT using JRE from the zip archive.
So much for stealth!
We added initial detection for the family back in February 2021, and this week have improved on that to better handle some of the newer variants as well as providing more robust handling of some of the older ones. You can find examples below.
Analyses:
