Today we’re proud to announce the release of a project that we’ve been working on for a long time. Triage now supports analysis of Linux samples! This means that Triage can now analyse malware on Windows, Linux and Android platforms.
In this blogpost we’ll briefly describe the various components that make up our new Linux capability, and showcase a few analyses for known Linux malware.
This is only the first version of this support and we will be expanding it over the coming months. It is now available to all users, so give it a try and let us know what you find! Feedback and more samples will be a great help with future development of the Linux platform.
Not signed up yet? Visit https://tria.ge/signup to register for a free account!
Linux Analysis Features
Custom Kernel Agent
Similar to our Windows analysis capability, we employ a custom kernel module to perform Linux malware analyses. This module, called stahp, is partially inspired by the STAP functionality in the Linux kernel.
Supports Multiple Architectures
In order to accommodate the different platforms on which the OS can be run, our Linux capability supports AMD64 (x86 and x64), ARM, and MIPS platforms (including big endian MIPS, MIPSBE). Upon request PowerPC and SPARC are possible too.
Live VM Interaction
We made sure that performing a Linux analysis feels similar to our Windows and Android analysis capabilities, therefore it’s possible to interact with the Linux VMs! During an analysis a root shell is provided, allowing one to run a number of commands. It should be noted that our VMs are not configured as a “desktop environment” and as such won’t have a graphical interface similar to what you’d expect during Windows analyses.
Varied Detection Techniques
Triage includes support for a wide range of detection techniques to identify malicious samples at multiple stages of their execution. As with our Windows support, the platform can dump memory, detect file system and commandline actions, and monitor network activity. We also support Yara analysis during static and dynamic phases. We will be continuing to expand and improve our detection support in the future.
Using Triage for Linux Analysis
Submitting a Linux file works in the same way as Windows or Android. Simply select/drag and drop a file into the Submit page. The Automatic profile will detect the file type and automatically launch the relevant virtual machines.
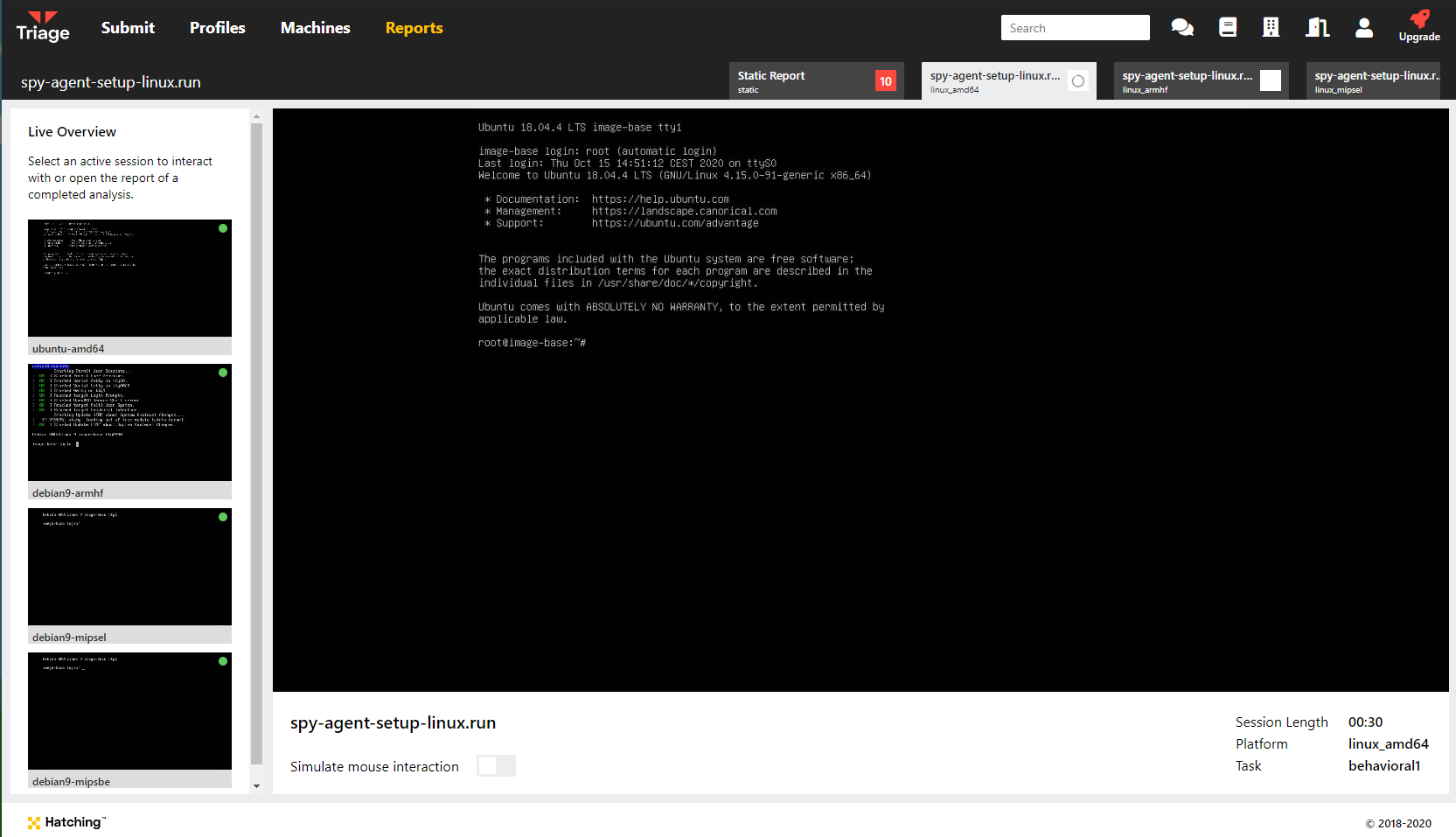
The architecture names are shown down the left of the Monitor view
During behavioural analysis you will be presented with a root terminal session on each VM which you can use for live interaction. Note that we do not include a graphical UI for the machines.
Fetching the Event Log via API
At the moment our signature detection for Linux is limited as this is an early version of the feature. If you want to investigate samples more closely yourself it is possible to access the entire event log which the kernel agent records during analysis. Similar to Windows analyses and the onemon.json file, Triage produces the stahp.json file which can be fetched through a new API - simply replace onemon.json with stahp.json in the request:
curl -H 'Authorization: Bearer <YOUR_ACCESS_KEY>' \
'https://api.tria.ge/v0/samples/{sampleID}/{taskID}/logs/stahp.json' \
--output log.json
Examples
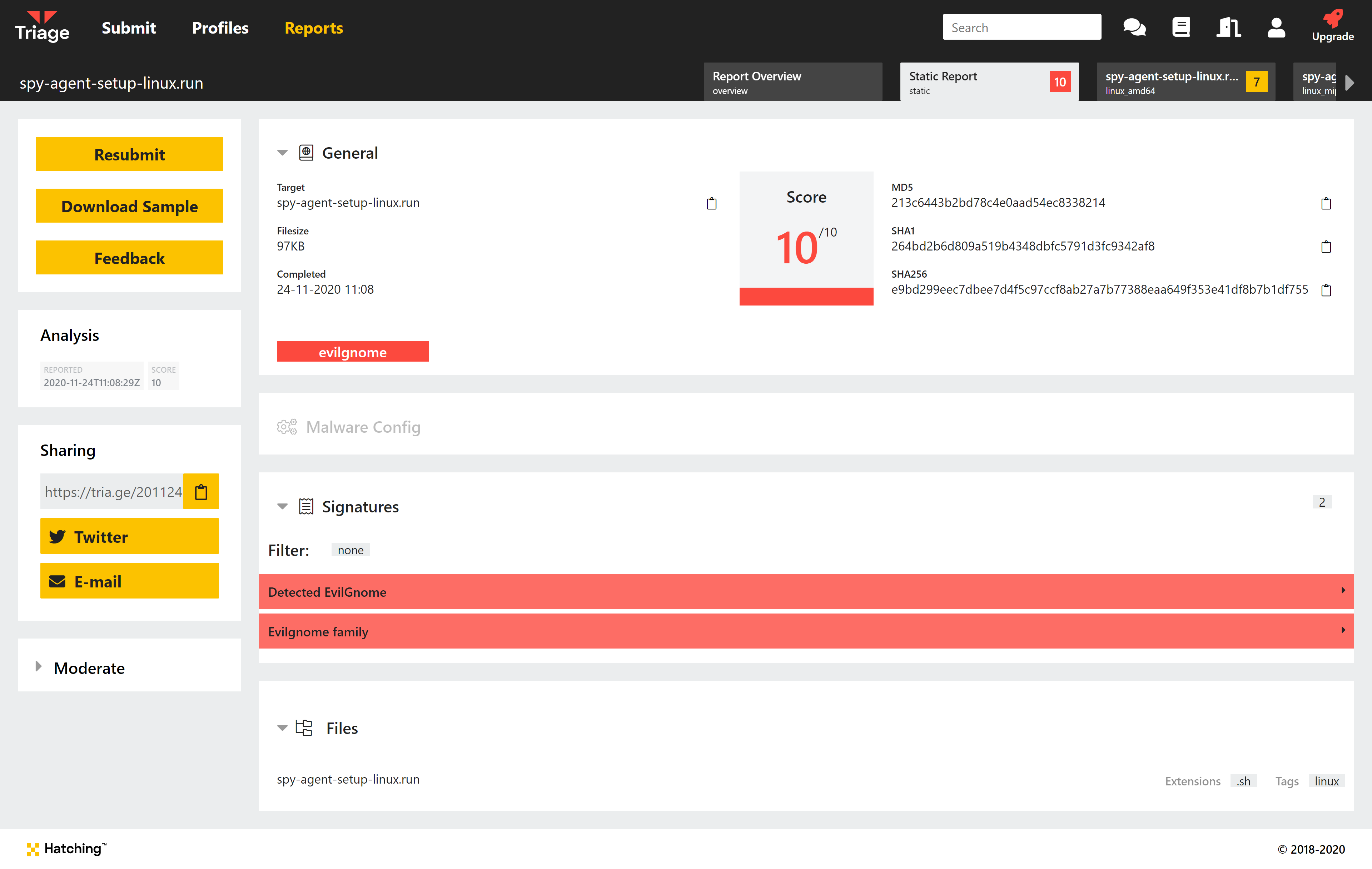
EvilGnome Installation Script
EvilGnome is unusual amongst Linux malware in that it targets desktop users rather than the more common server or embedded platforms. In terms of functionality it is a fairly typical stealer allowing taking screenshots, capturing microphone audio, and stealing local files. It also acts as a backdoor for further access to run additional modules or install further malware.
Analysis: 201124-yfsf7l7s3s
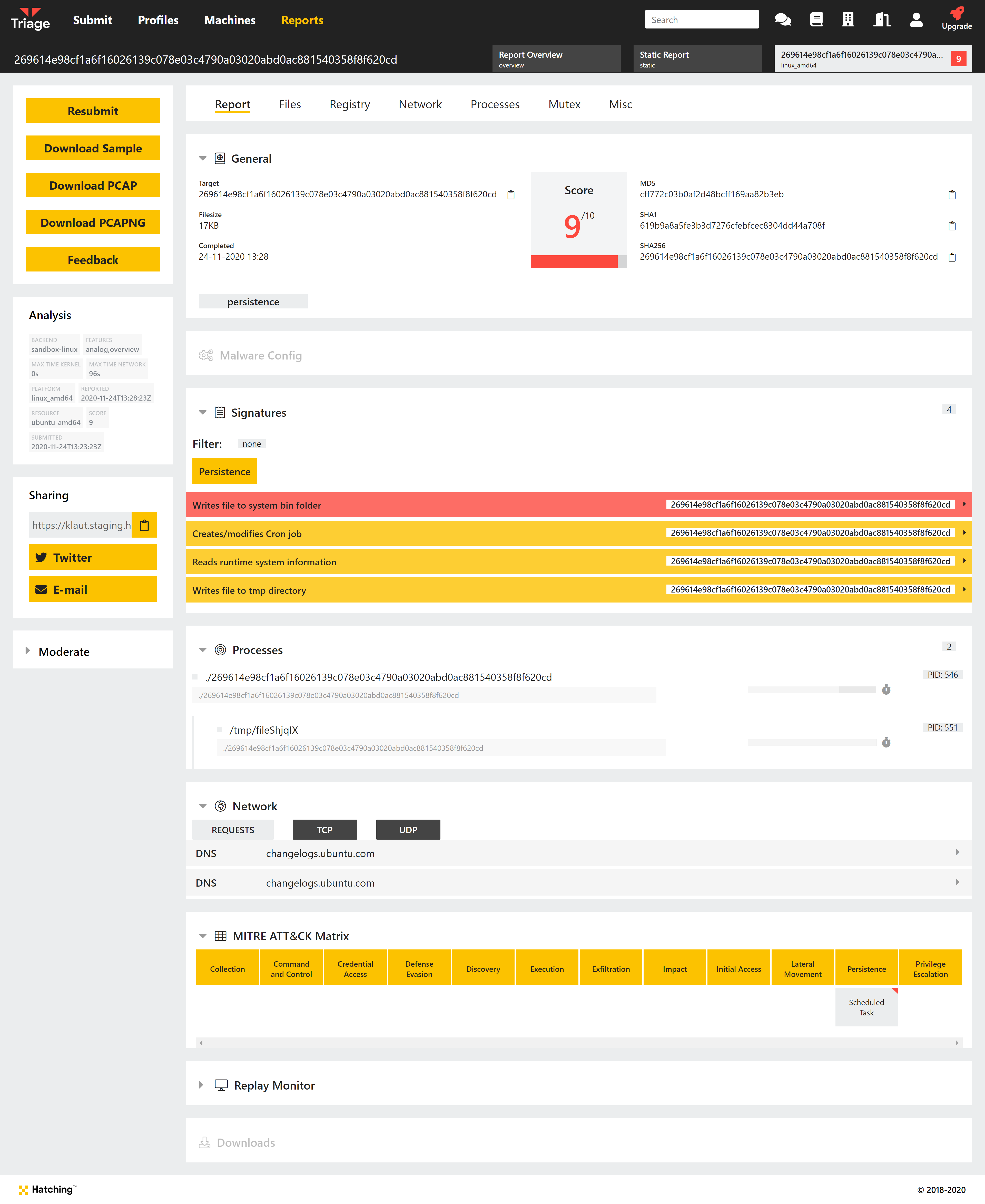
In Triage, the family has been detected during the static phase by a Yara rule.
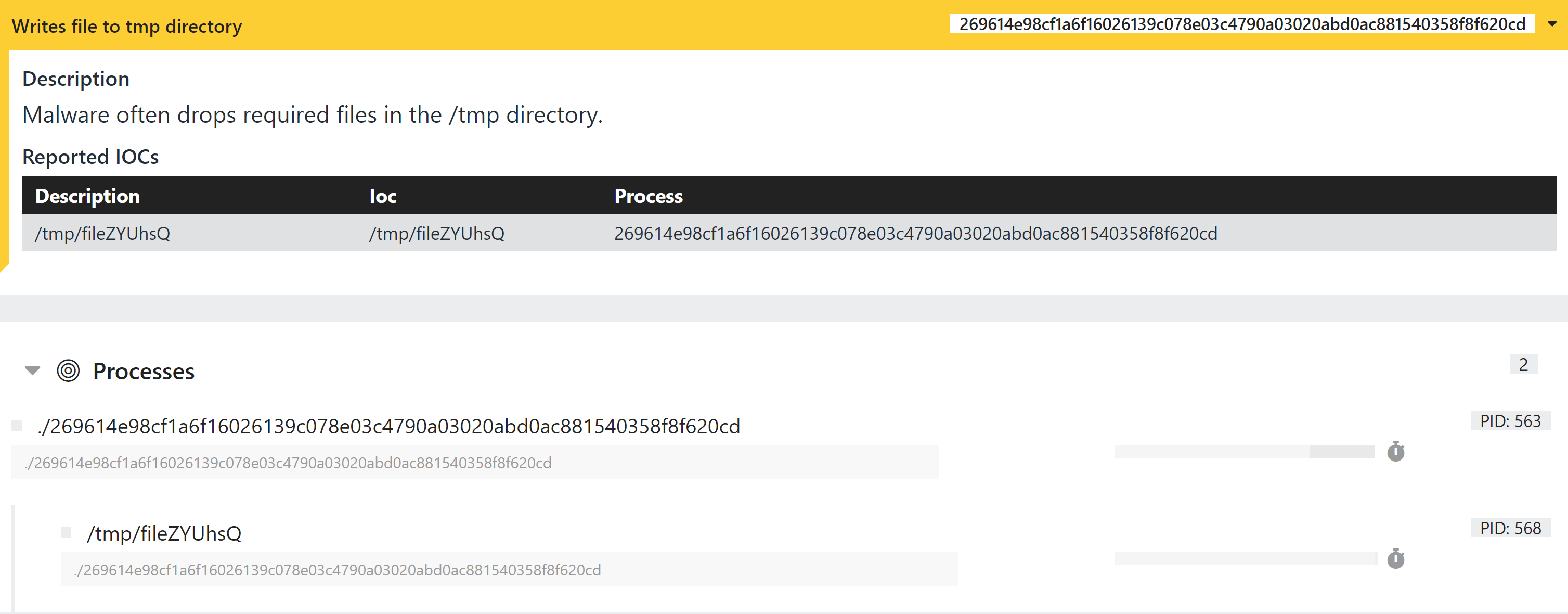
We can also see a number of signatures detecting file actions in the behavioural report.
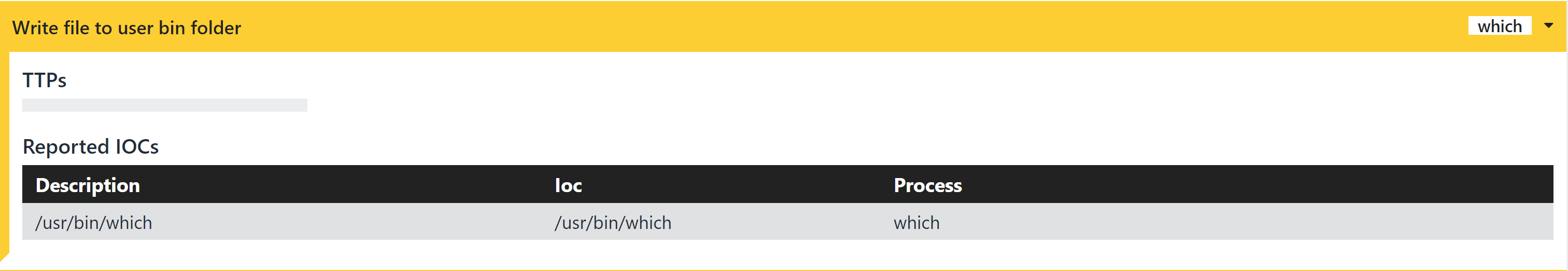
Writes executable to /usr/bin folder
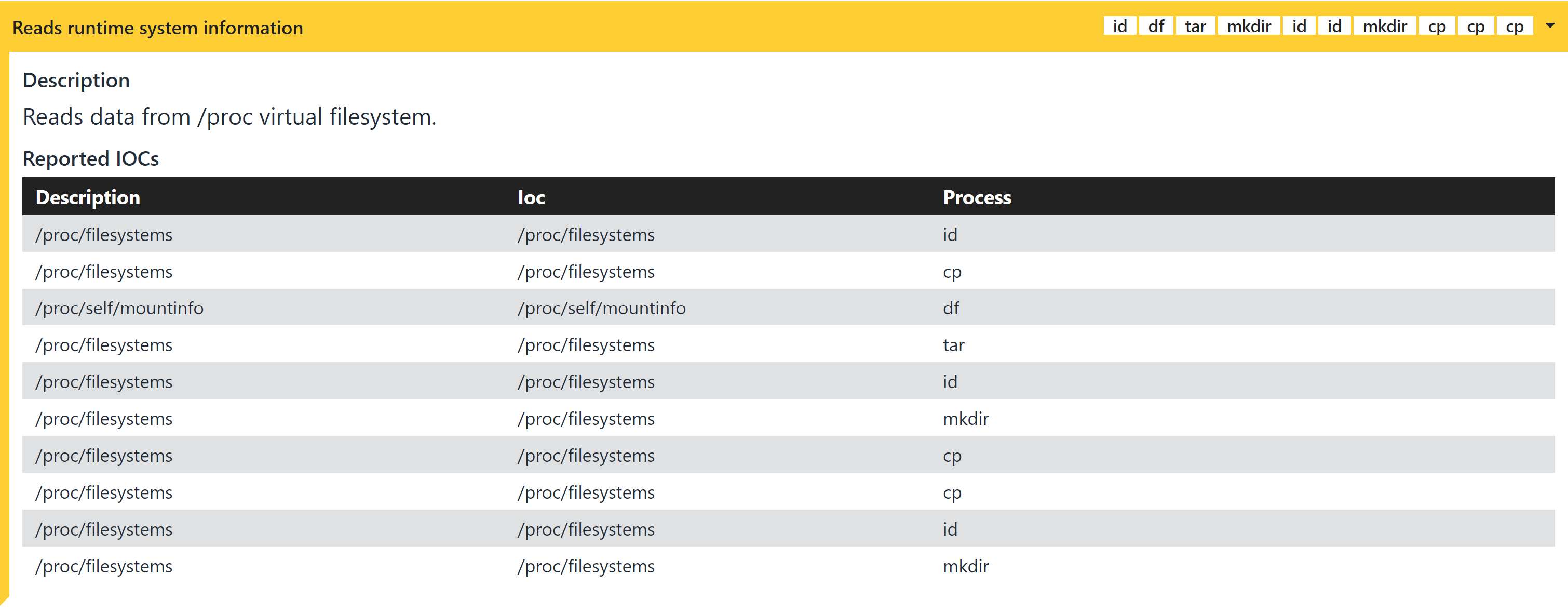
Enumerates filesystem resources
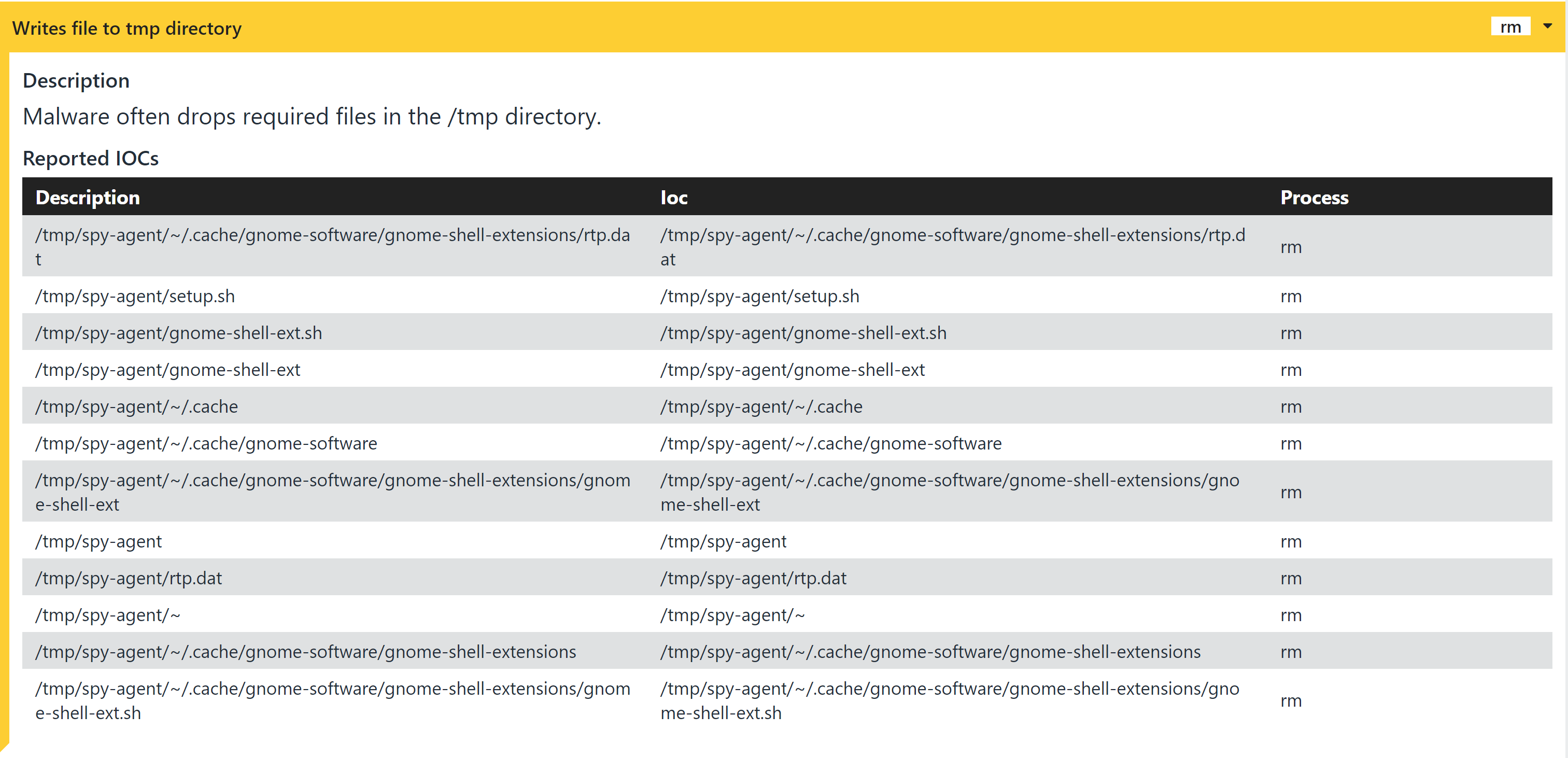
Writes files to system temp directory
EbolaChan File Injector
EbolaChan injects itself into various system files so that it is run any time they are opened or executed. It also uses cron to persist on the system and rerun the base script every hour.
Analysis: 201124-38cax1ssh2
In this example Triage has detected the specific architecture of the binary and selected the appropriate Linux VM - AMD64.S
We can see a signature reporting a file change caused by the new Cron task the malware adds.
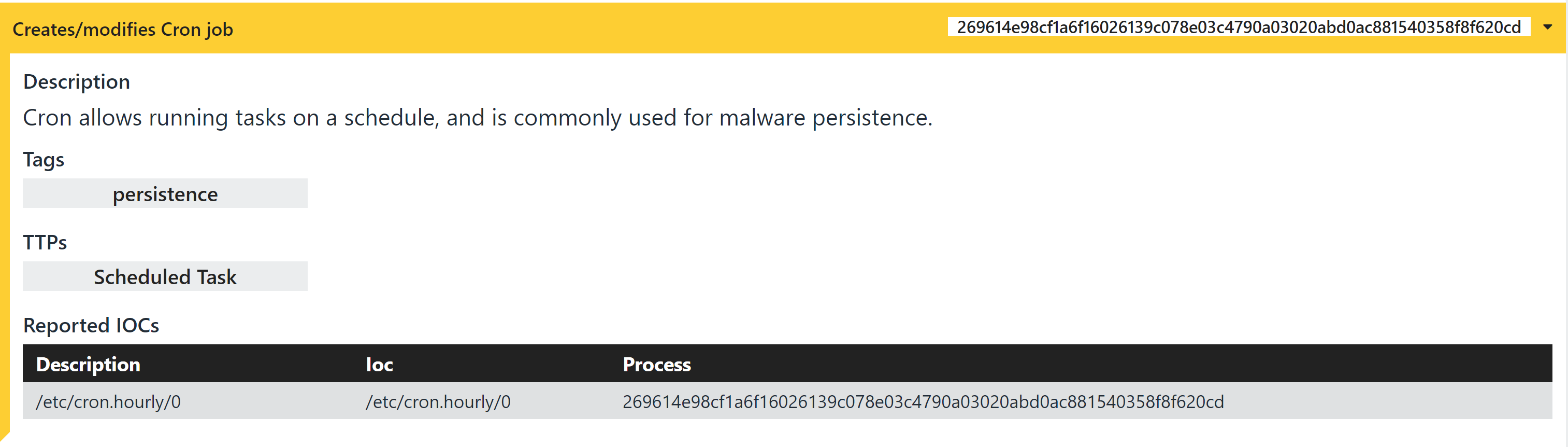
Registers new hourly Cron job
It’s also evident that it drops a file to the system temp directory and then executes it.