Welcome back to our Triage Thursday blog series! We’re sorry for the lack of communication in recent weeks - it’s been an unusually long gap for us as things have been a bit hectic and we’ve been short of time to publish these posts, so today we’ll go back over all the main changes since our previous post on May 12th to bring you up to speed.
Without further ado, let’s get into it:
- Updated Amadey detections to support credstealer module
- Added detections for BPFDoor Linux family
- Updated detections for Clop ransomware
- Added detections and a configuration extractor for the XorDdos family
- Added detections for Colibri loader
- Added support for Eternity Project samples
- Added detecions for Nerbian RAT
- Updated support for Netwire RAT
- Updated detections for Magniber ransomware
- Updated detections for DCRAT
We should be back to our regular schedule for the foreseeable future, but blogposts or not you can always reach out to us. If you have any comments, suggestions or other feedback about the platform and its detections we’d love to hear from you! You can find us through the website, on Twitter, or by using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Amadey Stealer
Amadey was first reported back in early 2019. It is a trojan/botnet which targets non-Russian users and is available for sale through online forums.
Infected machines are incorporated into a botnet which is then used for spam email campaigns and carrying out DDoS attacks. The family can also deploy additional payloads on a system - for example in May 2020 ZScaler reported that it was being used to push the Remcos RAT.
We most recently wrote about Amadey on this blog back in October 2021 when it added support for a couple of new software applications, including Microsoft Outlook and a GUI tool used to administer MikroTik routers and network devices.
We have recently noticed some examples of a credstealer module for the family being uploaded to Triage on their own, and these tend to get past the family naming we’ve previously implemented for the main payload. We’ve extended our rules to cover this as well.
Analyses:
BPFDoor
BPFDoor is a backdoor family first reported in early May 2022. However indications are that it has been actively used for at least 5 years to infect and access Linux and Solaris systems and had gone unnoticed until that point.
The family was initially openly reported by PwC in their annual cyber threat report for 2021 (available here), where they attribute its activity to a Chinese threat actor they refer to as Red Menshen. This group has mainly been targeting telecommunication providers and government entities in the Middle East and Asian regions over the course of 2021 and into 2022. BPFDoor is a small backdoor which just provides full remote access to the Linux shell.
The end result may be pretty standard for a backdoor but the family does have a couple of unusual tricks up its sleeve. Chief among these is the fact that it does not need to open any ports (and as such, does not need to modify firewall rules or similar protections). It is able to piggy-back off existing services, communicating over the same port(s) as web apps which are already running for both outgoing and incoming communications, which makes it extremely difficult to spot using standard network monitoring. To achieve this is uses a Berkeley Packet Filter (BPF) which gave the family its name.
We have reviewed the samples available to us and implemented initial detections for the family. For more reading on the technical details you can find an excellent writeup by Kevin Beaumont on his blog here.
Analyses:
Clop ransomware
Triage has supported Clop for a few years now, but as usual the family insists on making changes. We’ve revisited it the last couple of weeks to extend our support and ensure we have detection for the latest samples in the wild. We’ve also extended detection into the static analysis stage as well as based on system actions to try and make the rules a bit more resilient.
Clop has been one of the most heavily used ransomware variants over the last 3 years or so and has gained quite a bit of attention over time for some of its higher profile successes such as E-Land, the largest ecommerce company in South Korea. It follows the double extortion approach, with a leak website where confidential data stolen from the victims will be made public in the event of a refusal to pay the ransom.
The operators and developers of the family took a bit of a hit in mid-2021, when a law enforcement operation by the South Korea, United States, and Ukrainian police raided and arrested several people suspected of being part of the gang behind it. However it has not stopped operations, or even appreciably slowed them down - TrendMicro reports seeing pretty constant activity from January 2021 through to January 2022.
Analyses:
XorDdos
Going back to Linux again, XorDdos is an older trojan which was first reported back in 2014. It got its name from - probably unsurprisingly - the fact that it uses XOR-based encryption for its C2 traffic and was often used to carry out DDoS attacks from infected machines.
Among its arsenal is the ability to spread to other machines by bruteforcing SSH services - once access is gained it will use root permissions to download and deploy the main payload. It also includes quite a few features aimed at stealth and evasion (SSH bruteforcing aside), and multiple persistence mechanisms aimed at a range of different Linux distributions. You can find a full technical writeup in this blogpost by Microsoft.
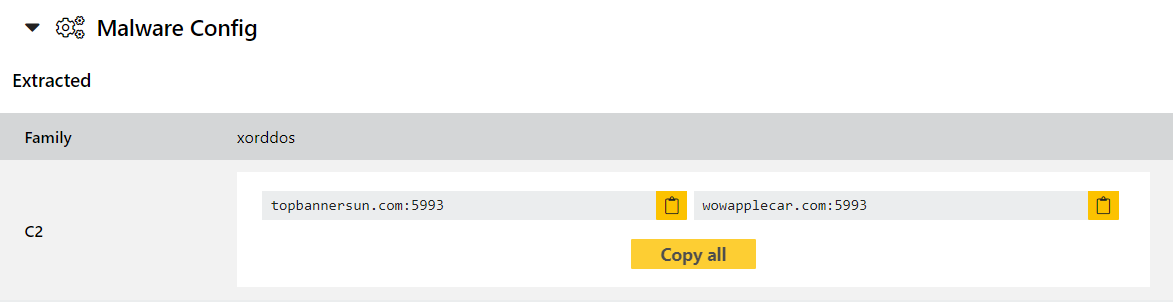
We have reviewed a number of available samples, and implemented standard detection and a configuration extractor for them. Some examples are provided below.
Analyses:
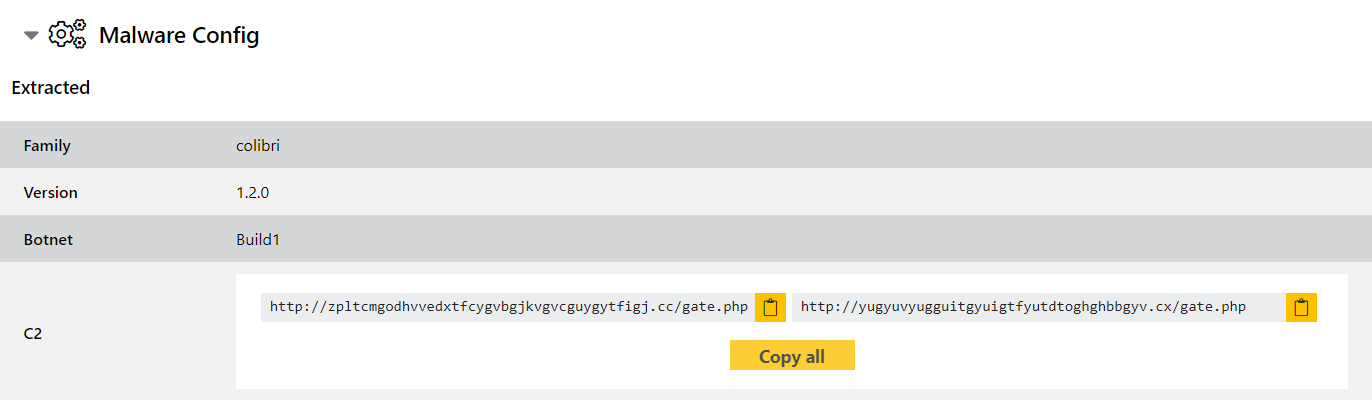
Colibri loader
Colibri Loader - not to be confused with the old Windows XP/7 tool for updating the bootloader and OS image which seems to be unrelated - was first seen appearing on forums in August 2021. MalwareBytes report that they have seen it being used to deliver Mars Stealer payloads in Q1 2022.
The malware consists of the loader component and a PHP-based web panel for the attacker to use to administer the implants. It is offered online as malware-as-a-service, with licenses provided on a weekly or monthly basis.
A detailed writeup of the family by Fr3d.hk can be found on their blog if you’d like more technical details. We have reviewed samples and added signatures and a configuration extractor, and of course will keep an eye on the family for any future changes which may require a revisit.
Analyses:
Eternity Project
The Eternity Project is a new malware-as-a-service with a bit of a twist. Instead of focusing on a single type of malware this team offers a customised toolkit with modules tailored to the specific attack(s) being carried out.
According to the report by BleepingComputer among the modules currently on offer is an info-stealer, a coin miner; a clipper, a fully functional ransomware, a worm spreader, and soon a bot for carrying out DDoS attacks. The modules are sold separately, with customers using a Telegram bot to automatically build their binaries based on the features they have selected.
We have got hold of samples of most of these components and developed detections for them, and if we come across any more we’ll add updates as needed.
Nerbian RAT
Nerbian is another new addition to the malware scene, first appearing in May 2022. It is written in Golang with a heavy reliance on open-source libraries to try and make its codebase look as generic as possible. It has so far been seen making significant use of lures related COVID-19 and the World Health Organization in its campaigns.
Code reuse is not this family’s only way to minimise its chances of detection. According to analysis by Proofpoint it leverages multiple anti-analysis techniques across several stages of the including multiple encryption routines for C2 traffic. For many of these it makes use of the open-source Chacal framework, which is promoted as a Golang anti-VM framework for redteamers and pentesters. A complete list can be found in their readme on Github, but it includes things from checking standard hypervisor strings to looking for signs of any hooks to monitor memory on the machine.
Analyses:
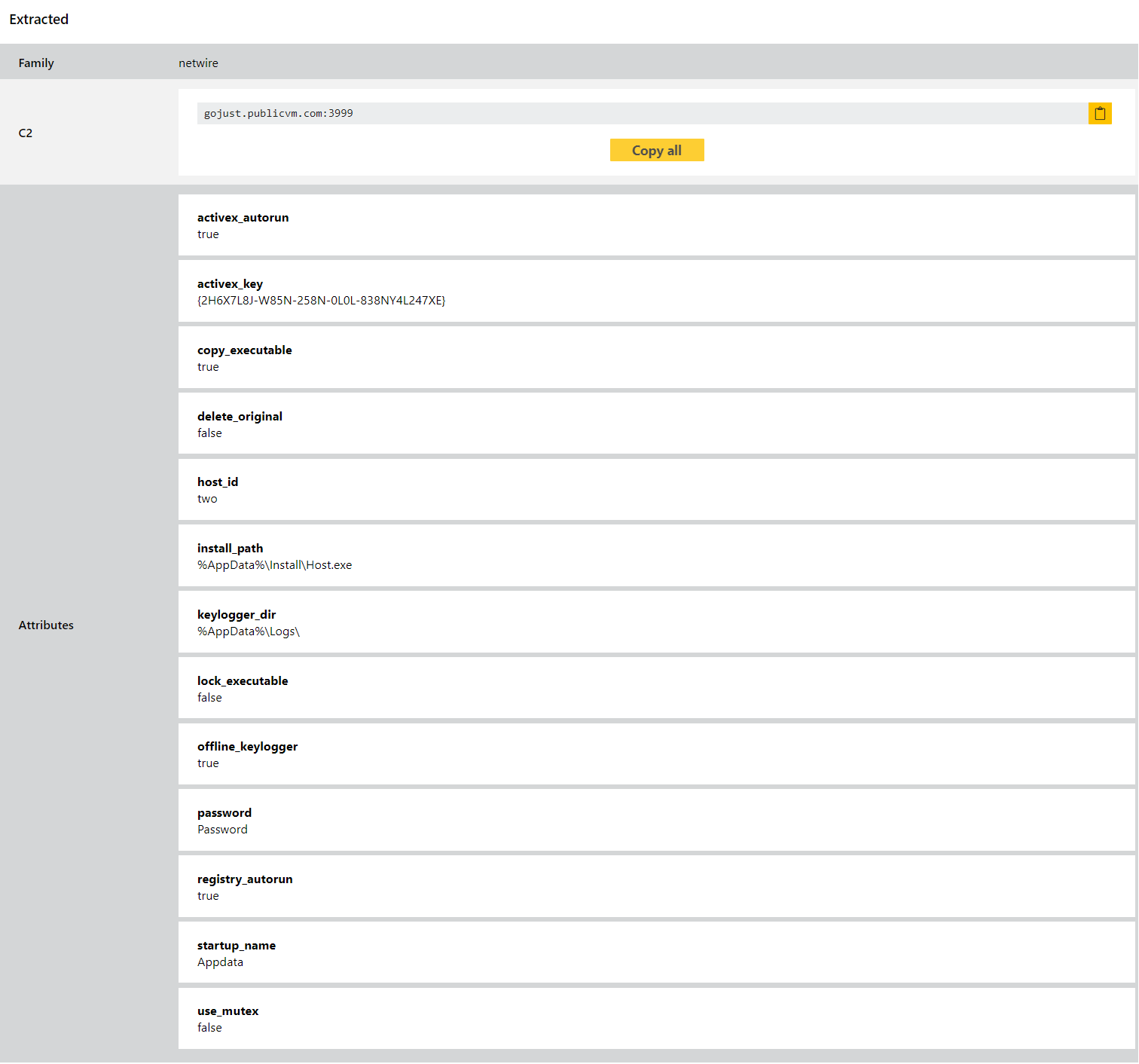
Netwire
Netwire is an old family which has been around since as far back as 2014. It is a file stealer which targets sensitive information stored by local applications. It has seen many versions over the years but remains an active and capable threat in 2021.
Triage has supported family detection for it for years, and we extended this with a configuration extractor back in April 2021. However we have recently started seeing some x64 versions of the family passing through Triage, so we have now revisited it to bring our detections up to date with this. At the same time we have reviewed many of the other latest variants and made a few tweaks to tighten things up in general.
Analyses:
- 220503-ahx2badag7 (64 bit version)
- 220505-vf8p9abahk
- 220505-vf8p9agdc5
- 220504-k56l3sdee7
- 220504-fx5ycsdba4
Magniber
Magniber ransomware has been around for a few years, initially solely targeting users in South Korea and then expanding to cover additional South-East Asian countries. The malware is traditionally spread via the Magnitude Exploit Kit which like many modern EKs also mainly operates in the APAC region. The ransomware itself also originally included extensive checks to ensure that it only ran on machines in that area, though it moved away from this last year.
The family’s name comes from this relation with the Magnitude EK, and some code similarities to the successful Cerber ransomware.
Our old detections for the family were mostly based around the ransomnotes, so to make the results more reliable we have revisited it to add more robust detections for the payload itself and carry out a general review of the available samples. You should find coverage for samples new and old is more reliable now.
DCRat
DarkCrystal RAT, or DCRat, was first reported in late 2019. It provides an extensive set of remote administration functions, triggered by specific commands received from the C2 server. These range from file transfer, keylogging, and data theft to opening and closing the CD drive or interacting with the Windows speech synthesizer. In addition to the builtin commands it can also run shell commands and pipe the output to the remote C2 server.
A detailed analysis of the family can be found in FireEye’s report from May 2020, in which they breakdown the samples and all supported commands.
This week doesn’t bring major changes to the family - after spotting some recent samples not being correctly identified we have taken a look at our old rules and made some improvements to provide better coverage. Some relevant examples are provided below.
Analyses:
