Welcome to another entry in our Triage Thursday update blog series! We’re back with a few updates today, after missing a blogpost last week to focus on work in progress.
We still aren’t quite ready to put our latest feature in your hands yet but we’re delighted to say that macOS analysis is almost ready and will be coming to Triage soon™! In today’s post we’ll give a bit of a preview of what’s coming for our macOS support.
There have also been a few detection updates since our last blogpost so we’ll briefly cover those below:
- CobaltStrike configuration extractor tweak
- Updated Gozi RM3 configuration extractor
- Improved handling for Hakbit ransomware
- New FickerStealer configuration extractor
- New Netwire configuration extractor
- Added family detection for Jormungand ransomware
- Added initial signatures for Beapy cryptocurrency miner
If you missed it earlier in the week, we also released a new feature for our Private Cloud customers. Magic Links are now available to make it easy to share analyses outside of registered Triage users. You can find more information on this in a Short Guide blogpost we published at the start of the week - Short Guide: Using Magic Links.
As always, a huge thank you to all those who send us feedback and suggestions - as a small team your comments are invaluable in helping us keep on top of an ever-changing malware landscape. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
macOS Support
Adding support for analysis in macOS environments has been a central aim for Triage since its initial design, and we are very excited to finally be bringing it to reality. macOS is the last of the core platforms Triage was designed to work with, having begun with Windows initially and adding Linux and Android support over the course of 2020. Although really it is only the beginning of our plans for Triage, it represents a major milestone for us and the platform.
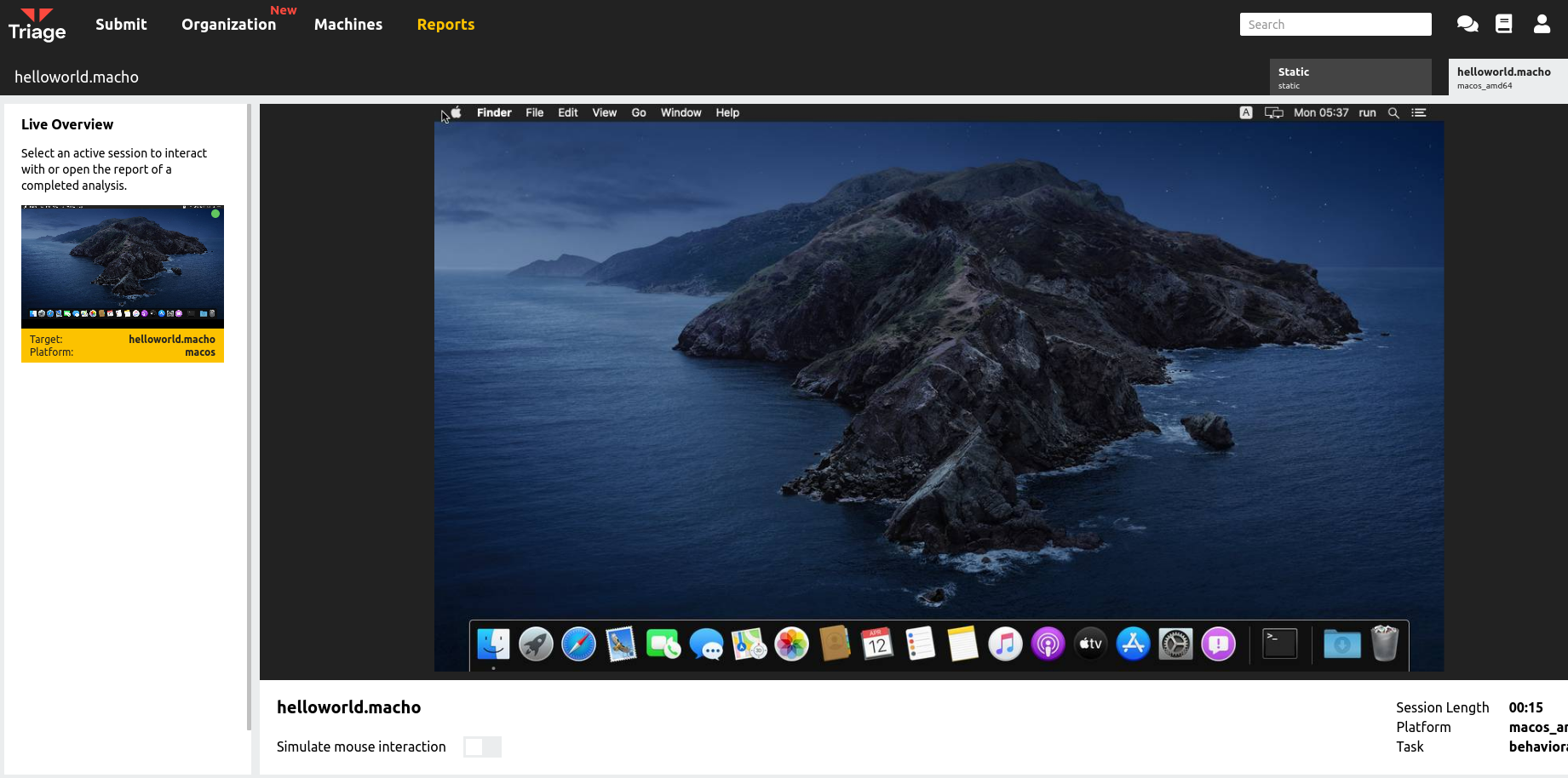
macOS VM running in Live Monitor
The initial release will support analysis machines running macOS 10.15 Catalina and, like our Windows VMs, will support most types of executables, scripts and files with embedded macros/code. They will also include common software, like Office, to support most malware delivery methods.
To provide visibility on the VM for analysis we have developed a custom kernel agent which monitors all relevant activity like file and network operations, new processes etc. These feed directly into our existing signature system for simple integration.
We’ll be sharing much more detailed information with you at the time of release. In the meantime, let’s take a look at some of the other updates which have been pushed this week.
CobaltStrike Configuration Extractor Update
CobaltStrike makes another appearance in the blog this week, with a tweak our end making it easier to track and identify campaigns using the malware.
We have recently observed users online sharing samples and using the watermark value from the config to identify samples.
To aid with tracking campaigns in this way, we have added a botnet ID tag to our CobaltStrike extractor which parses the watermark value and indexes it for searching within Triage. This should make it simple to quickly find additional samples using the same payload.
You can find some examples featuring the new tag below.
Analyses:
Updated Gozi RM3 Configuration Extractor
Gozi RM3 has been another regular on the blog recently, with us making a few improvements and updates in recent weeks. This week our update addresses the handling of loaders for the family based on a recent sample we observed which did not follow the usual pattern.
We have now expanded the config extractor to parse the PX structure within the samples and extract the primary loader. This resolves some issues with the family using multiple stages of loaders and causing them to not be processed properly.
An example is available below.
Analysis:
Improved Handling for Hakbit Ransomware
A version of Hakbit was recently brought to our attention which was incorrectly identified as Teslacrypt by Triage. We also observed that the ransomnote was not being detected and extracted as expected.
On investigation we identified some limitations in our ransomnote handling which were affecting this analysis due to the note being in Russian. We have deployed an update to address this issue and support for non-Latin characters should be more robust now.
In addition we have begun a review of our Teslacrypt signatures to prevent further false positives for the family. The signatures for this family are among the oldest on the platform and we have far more capabilities available now to improve detection. In the meantime we have removed weak signatures, as the family is not common these days.
Analysis:
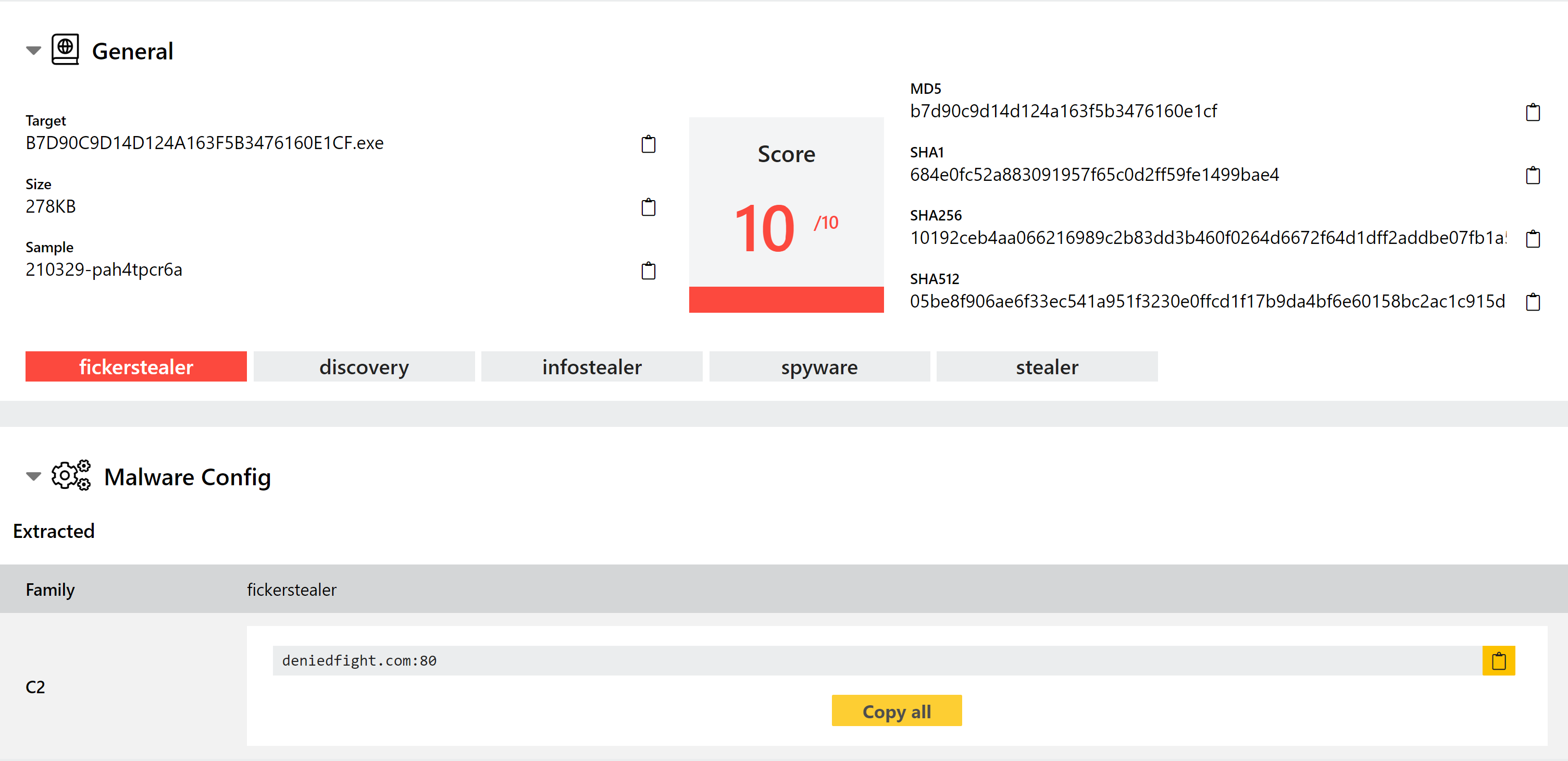
New FickerStealer Configuration Extractor
FickerStealer is a malware-as-a-service sold through underground forums since mid to late 2020. It has commonly been reported in campaigns also involved Hancitor, often spreading through malicious Office documents distributed via email.
We have observed samples being submitted to Triage but previously did not have dedicated family detection for them. We have now implemented family signatures and a configuration extractor to dump relevant C2 information.
Analyses:
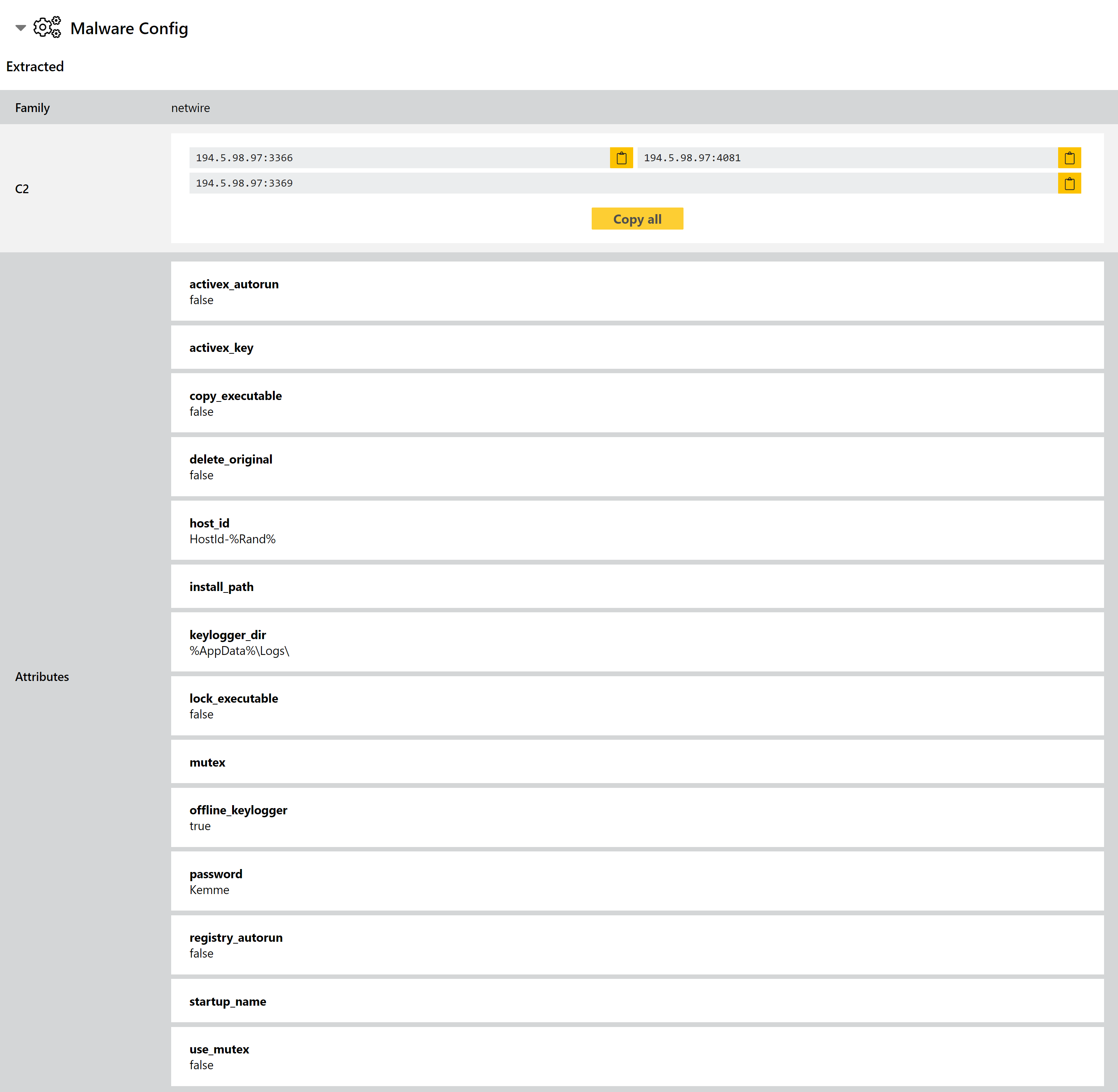
New Netwire Configuration Extractor
Netwire is an old family which has been around since as far back as 2014. It is a file stealer which targets sensitive information stored by local applications. It has seen many versions over the years but remains an active and capable threat in 2021.
Triage has supported family detection for it for a while, but we have reviewed available samples and implemented a new configuration extractor to dump the information available, including C2 settings and options like whether or not to deploy mutexes and persistence registry keys.
Analyses:
Added Family Detection for Jormungand Ransomware
We recently noticed a minor ransomware called Jormungand which was not being properly handled on Triage.
Based on the content of the note we made some updates to improve overall coverage for our matching mechanism which detects likely ransomnotes, and added some family detections to catch Jormungand itself.
Analysis:
Added Family Detection for Beapy Cryptocurrency Miner
Beapy is a cryptojacker malware which was first seen in the wild back in January 2019. It was reported by Symantec to be using the leaked NSA Eternal Blue exploit to spread rapidly, mostly targeting businesses in China (although it has also affected other Southeast Asian countries).
The malware is a fairly standard file-based cryptominer intended to covertly use infected machines to harvest the Monero currency.
In addition to the standard infection chains via malicious email, BitDefender reported that Beapy was involved as the payload in a supply-chain attack against Potentially Unwanted Applications (PUA) like DriveTheLife, a supposed 3rd party driver updater.
Analyses:
