Welcome back to another week of Triage Thursday updates! We had a bit of a break from the blogging last week due to summer holidays but we’re back and ready with a bunch more updates for you.
This week we’d also like to give a big shout out to the team over at Sekoia.io, who have been working hard the last few weeks to integrate Triage with their Cyber Threat Intelligence platform. They have published a blogpost on their own site today which you can find here which you should check out for more information.
With regard to Triage updates, we have several things to take a look at from the last couple of weeks:
- Suricata integration
- New configuration extractors for XpertRAT and OrcusRAT families
- New behavioural detections for Biopass RAT
- Updated detection for new Cryptbot variant
- Updates for Darkside ransomware detection
- New detection for the Linux variant of the HelloKitty ransomware
In other news, we are also still looking to add a new Go developer to the Hatching team. If you’d like to be involved in the next steps of Triage’s journey - or know someone who might be - you can find the full job listing here. Feel free to reach out with any questions.
As always we also welcome any feedback or questions about our changes or just samples you come across during your analysis. If you notice anything not behaving as expected please do reach out and report it to us. You can contact us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Suricata Integration
Suricata is an open source IDS/IPS widely used across the IT industry. It focuses on network monitoring, detecting threats via signatures and heuristics within internet traffic passing through the IDS. It is a powerful tool and something which we believe can add a lot of value in terms of detecting and identifying malware families in a dynamic sandbox setting.
For some time we have been working on integrating Suricata into Triage to enable us to implement more advanced network rules and leverage the significant pool of existing knowledge around the product. Today we are pleased to announce that version 1 of our integration is now live for use by all Public Cloud users. For Private Cloud users this feature will be available in a few weeks once we have thoroughly tested the feature and fleshed out the signature support.
Suricata rules are run against the PCAPs Triage generates during analysis, including the fully decrypted SSL/TLS HTTPS traffic, giving us excellent visibility into the malware’s network communications.
An example analysis with a Suricata result can be seen here for reference: 210722-3rszfk8km6.
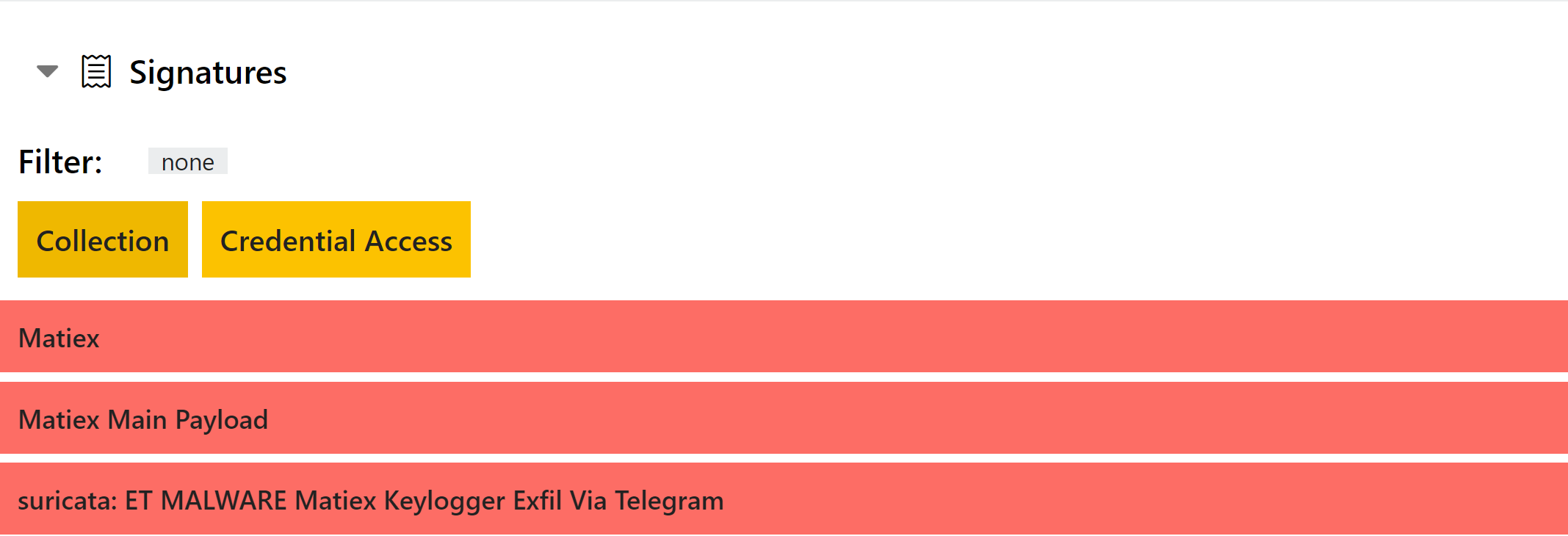
New XpertRAT Configuration Extractor
XpertRAT is a stealer family written in Delphi which has been around for a quite a few years, dating back to around 2011. It features fairly standard stealer functionality, while also working as a direct backdoor into compromised systems which the attacker can exploit to carry out any additional actions they wish.
The malware is modular, and generally includes a core loader component with additional functions added as needed.
We added basic detection for the family back in August last year, but we have recently reviewed samples to expand this into a full configuration extractor. Some examples are available below.
Analyses:
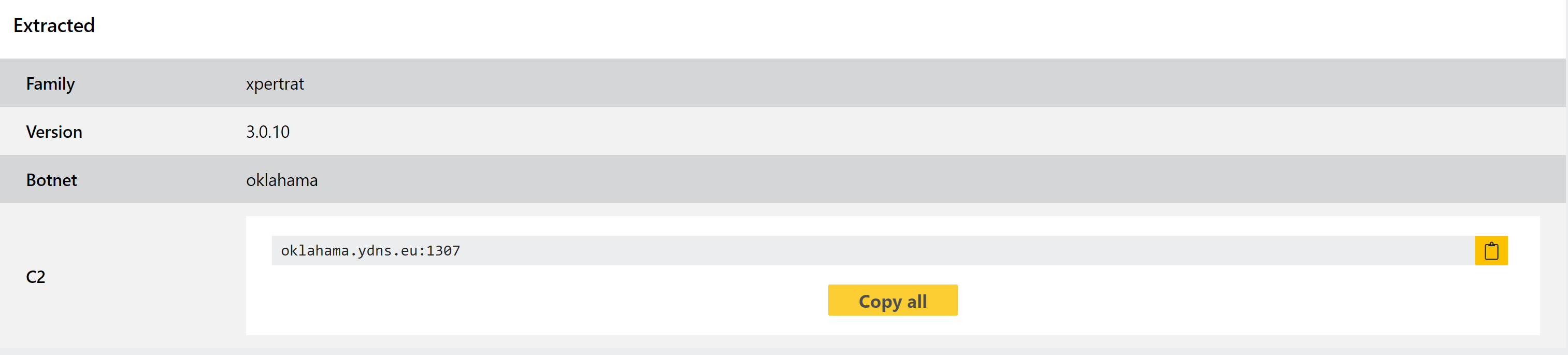
New OrcusRAT Configuration Extractor
Orcus is a fairly advanced remote access trojan with an extensive feature set targeted towards data theft and remote control. It has been available for purchase through forums since at least 2016, and includes support for custom plugins enabling end users to easily extend or target its abilities to their use case.
Triage has featured support for the family for some time, but this week sees the implementation of a full configuration extractor for the family. As usual we’ll be monitoring the results and making tweaks as needed for any outlying versions.
Analyses:
Detection for New Biopass RAT Family
BioPassRAT is a new malware family reported earlier in July by TrendMicro. It has mainly been observed targeting Chinese online gambling companies via watering hole attack, masquerading as an installer/updated for common software applications like Flash.
It follows many of the patterns typical of general stealers/RATs, including backdoor access and several tactics for harvesting information from local software like browser passwords etc. Where it sets itself apart from others is the addition of a screen recording feature which abuses the widely used OBS (Open Broadcaster Software) to capture the screen contents and stream it to the attacker’s infrastructure in real time.
For full details on the family, check out Trend Micro’s blogpost here.
We have taken a look at initial samples reported and implemented behavioural signatures to classify it correctly. Some examples are available below, and you can use the family:biopass search query to locate additional samples.
Analyses:
Updated Signatures for New CryptBot Variant
CryptBot is an info-stealer which has been active in the wild since early 2019. It is often distributed alongside legitimate software which acts as its lure, often affecting users installing cracked versions of software downloaded from torrent sites.
The family has featured on this blog a few times this year already, as it is still actively developed and regularly pushes updated versions. We recently observed another such variant which we have now tweaked our signatures to properly detect.
Analyses:
- 210715-21y5jt3x16
- 210715-3jq5yv8dr2
- 210715-hm11l7wxv2
- 210715-jxbafj4kxn
- 210714-kylez5326j
- 210712-b4g536k7ka
Updated Darkside Ransomware Detection
Darkside first appeared on the scene in late 2020. It is a ransomware family primarily used in targeted attacks rather than being distributed indiscriminately. Since it’s appearance we have observed several versions in the wild, likely relating to individual campaigns. More information is available in the BleepingComputer article from just after the family’s first appearance which can be found here.
Ransom demands and exact deployment techniques generally vary from organisation to organisation, but like many modern ransomwares the deployment generally follows a previous breach whereby attackers were able to extract sensitive information about the company to use as leverage to pay the ransom.
Analyses:
New Signatures for Linux Variant of HelloKitty Ransomware
HelloKitty burst onto the scene at the start of 2021 when they successfully breached the well-known game developer CD Projekt Red - the creators of the (at the time) highly anticipated Cyberpunk 2077 and the popular Witcher franchise.
Although so far they haven’t risen to front page news again since then, the family has continued to be very active (and successful) in the wild. Now they seem to be following the example set by REvil/Sodinokibi and have released Linux variants of their ransomware. This was recently reported on twitter by @MalwareHunterTeam, and it seems that the samples likely date back at least to March 2021.
We have added some rules to cover these Linux versions, and you can find reports for some examples below.
Analyses:
- 210719-5znrb7htha
- 210719-8ywefz9qwj
- 210719-ba83bb78xx
- [210719-sedwsye5le](https://tria.ge/210719-sedwsye5le
