In a blogpost back in April we gave a bit of a teaser about our upcoming macOS support. Well, today we are delighted to announce the initial release of Triage macOS analysis!
This is a very exciting update for us, as it marks the last platform we planned to add support for when we began work on Triage a few years ago. With this we can now run analyses for most relevant file types from Windows, Linux, Android and macOS; all handled in a fully-automated manner with Triage by default recognising the file and launching the most relevant guest VM.
The new functionality has rolled out to the Public Cloud tria.ge today, and is available to all public users. We currently plan to deploy it to our Private Cloud customers in a couple of weeks, once it is thoroughly tested and detections have been expanded somewhat.
In this blogpost we’ll give a brief introduction to macOS analysis on Triage, and a brief overview of what you can expect in the future.
Contents
MacOS Analysis Features
Live VM Interaction
Direct mouse and keyboard control for the guest VM during analysis allowing you to run commands, run programs, check file directories, or anything else you may need to do when investigating a sample.
Custom Kernel Agent
As with our other supported platforms, we have developed an entirely custom kernel agent which is the central controller for analyses. It opens submitted files/URLs, logs all system activity (including tracking system calls), provides anti-VM countermeasures, and much more. Named bigmac, it has all the feature support also included in our original Windows agent.
Support for Multiple File Types
In this initial release, we support the most common file types leveraged in malicious campaigns. These are:
| Name | Extension | Description |
|---|---|---|
| Apple Disk Image file | .dmg | Wrapper/container for applications on macOS |
| Application Bundles | .app | Apple App bundle containing file/directories needed to run the program |
| Installation Package | .pkg | Installation files for macOS |
| Macho Object File | .o, .dylib, .bundle etc. | File format for executables, object code, shared libraries etc. |
We’ll be looking to expand on this list as required in the future. If you have specific requests or suggestions on this front feel free to reach out to us.
Dropped File Dumping
Many forms of malware will leverage multiple stages in their infection chain, downloading additional payloads or resources as required. To make analysis of these as simple as possible, Triage dumps these dropped files and makes them available for download and submission to Triage themselves, saving you the hassle of identifying and fetching them manually.
Network Analysis Support
An important aspect of any malware investigation, Triage includes full support for detecting threats via network activity. All network connections will also be displayed in the interface, and the PCAP can be downloaded as with our other platforms. We will be extending this functionality in future, to include more complex aspects like capturing TLS keys to automatically decrypt HTTPS traffic.
Getting Started With macOS Analyses
Submitting a macOS file for analysis with Triage doesn’t look any different than submitting one to Windows, Linux or Android. Just upload the file, click Analyze, and Triage will select the correct operating system based on file identification. Our standard timeout of 2.5 minutes also applies to macOS.
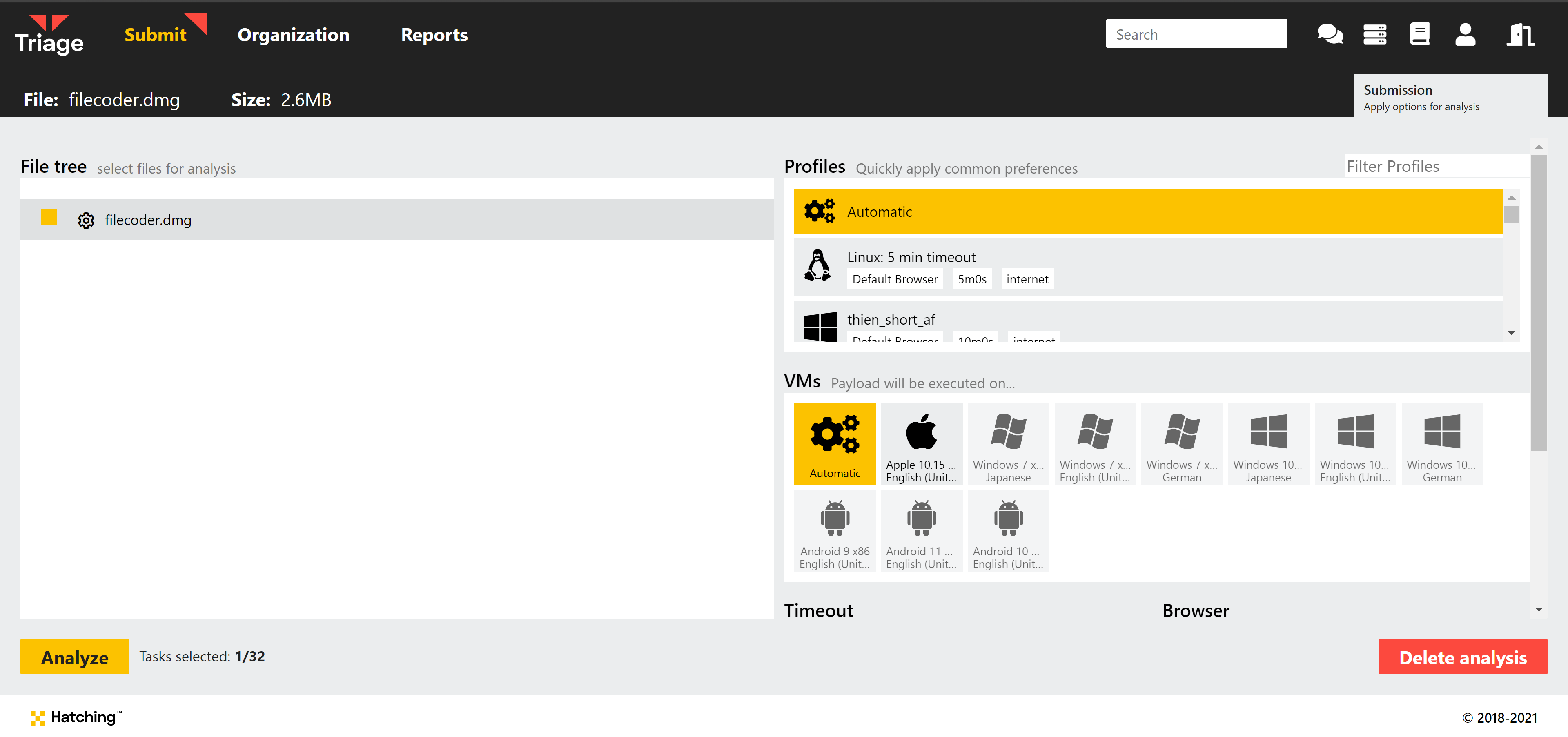
Of course, if you want to define the settings manually you can do this using Profiles (available to Researcher accounts or on the Private Cloud). Currently the only option for macOS guest VMs is 10.15 Catalina but this may be expanded in future. You can also choose the default browser, timeout, and network options as normal.
Fetching the Event Log via API
This initial release is fairly bare-bones in terms of signature detections for macOS events. Currently we have support for a number of families, and proof-of-concept extractors and ransomnote parsers for a couple of relevant examples. There are no general behaviour rules, but as already mentioned we’ll be adding these in the coming weeks.
In the meantime, you can still use Triage as an analysis platform for macOS samples - event logs and network activity are still available to you for further analysis even if it isn’t currently processed into results automatically. Some of these are available via the UI directly - for example PCAP/dropped file downloads - but you can also use the API to access the background event log which we will use to generate matches.
Following the same structure as the log files from other platforms (for example onemon.json in the case of Windows analyses), the bigmac.json file contains a record of all system events observed by our kernel agent during behavioural analysis. A new endpoint has been made available to fetch it:
curl -H 'Authorization: Bearer <YOUR_ACCESS_KEY>' \
'https://api.tria.ge/v0/samples/{sampleID}/{taskID}/logs/bigmac.json' \
--output bigmac.json
Examples
1. Dacls RAT
Dacls is an implant believed to be associated with the North Korean Lazarus APT. It has been infecting Windows and Linux systems since late 2019, but in May 2020 researchers from MalwareBytes identified a new macOS variant as well.
Analysis link: 210603-gxrvff2tan
In Triage as it currently stands, the family is detected through the static phase and by a family rule in the behavioural tasks.
The samples available are distributed as DMG files which act as containers much like the ISO format on Windows. They are effectively virtual versions of physical storage devices containing all the resources, files and subdirectories required by the application it wraps. If we look at the process listing presented by Triage, we can clearly see as the malware renames and relocates itself to resemble the MinaOTP software, a legitimate 2 factor authentication app for macOS systems.
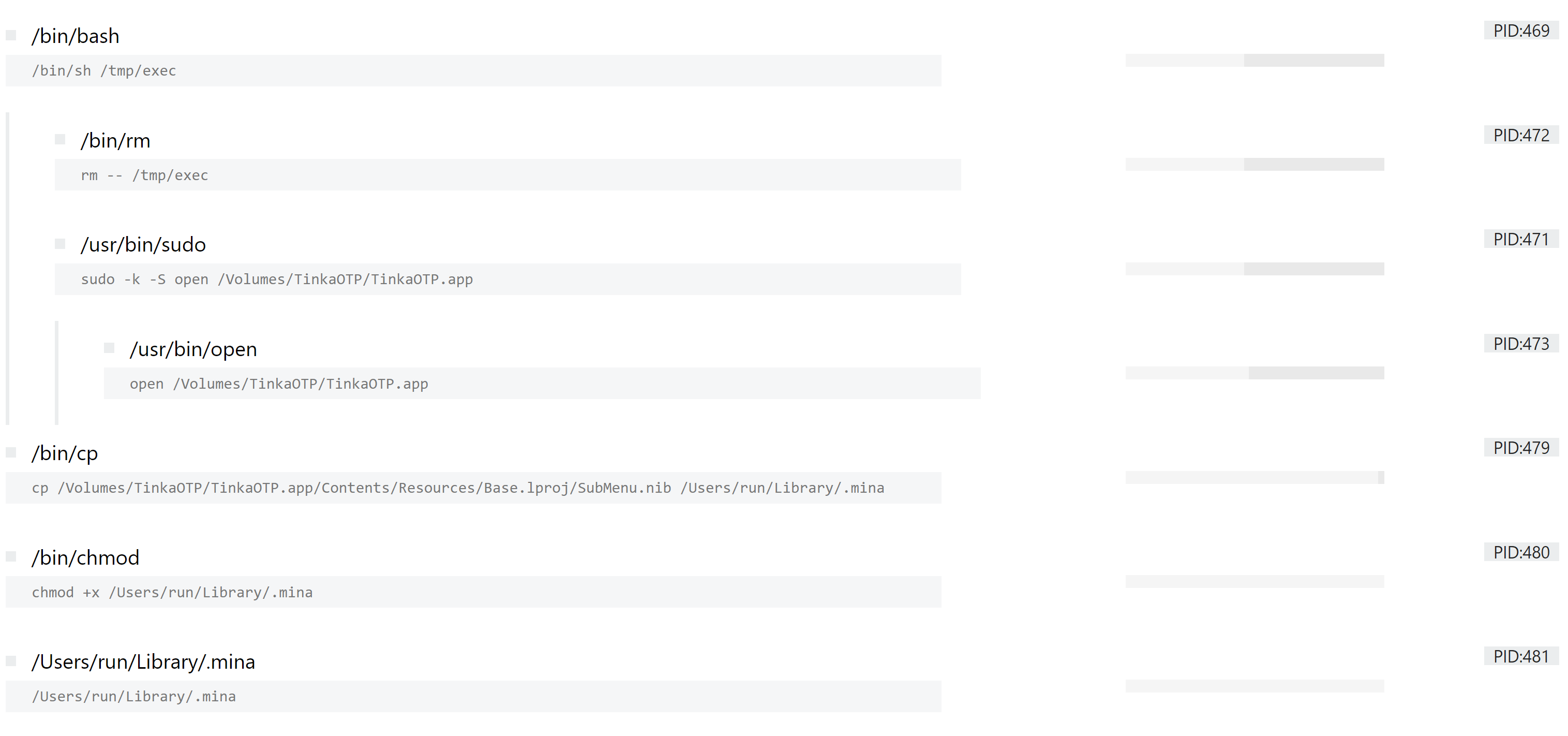
If we fetch the bigmac.json file and have a look at the background events, we can see additional signs of the family’s activity. For example file actions involving the malware configuration file, which masquerades as an App Store database file:
{"kind":"*bigmac.SyscallSI","event":{"arg0":"/Users/run/Library/Caches/com.apple.appstore.db","arg1":0,"kind":"access","pid":482,"procid":0,"ret":0,"ts":16306}}
{"kind":"*bigmac.SyscallSII","event":{"arg0":"/Users/run/Library/Caches/com.apple.appstore.db","arg1":1537,"arg2":438,"kind":"open_nocancel","pid":482,"procid":0,"ret":3,"ts":16307}}
Looking further we can also identify System Calls related to Dacls’ persistence method, which leverages the macOS LaunchDaemons/LaunchAgents functionality to start the ‘service’ after any system reboot.
{"kind":"*bigmac.SyscallSII","event":{"arg0":"/Users/run/Library/Info.plist","arg1":0,"arg2":0,"kind":"open","pid":481,"procid":0,"ret":0,"ts":16300}}
{"kind":"*bigmac.SyscallSII","event":{"arg0":"/Users/run/Library/LaunchAgents/com.aex-loop.agent.plist","arg1":1537,"arg2":438,"kind":"open_nocancel","pid":481,"procid":0,"ret":3,"ts":16301}}
{"kind":"*bigmac.SyscallISII","event":{"arg0":18446744073709551614,"arg1":"/Library/Preferences/Logging/com.apple.diagnosticd.filter.plist","arg2":16777476,"arg3":18446744073431466952,"kind":"openat","pid":482,"procid":0,"ret":0,"ts":16305}}
2. MacFileCoder Ransomware
MacFileCoder is an old ransomware originating all the way back in the halcyon days of 2014. At the time it was the first ransomware to be discovered targeting Mac systems, although it has turned out to not be the last by any means. A technical report by Securelist from the initial discovery can be found here.
Analysis link: 210603-ha3r6tyzpj
When initially discovered it seemed that the code was not complete, as they only encrypted a couple of files hard coded into the ransomware itself and did not interact with user files in any way. However later versions have appeared to fix this, adding the ability to enumerate and encrypt local files, although its simplistic implementation makes it relatively straightforward to reverse the process.
Taking a look at the process list again, we can see a large number of actions clearly related to the discovery and encryption of user files on the system. It appears to use the zip utility to encrypt the files using a set password. Once encrypted, the original files are then deleted from disk.
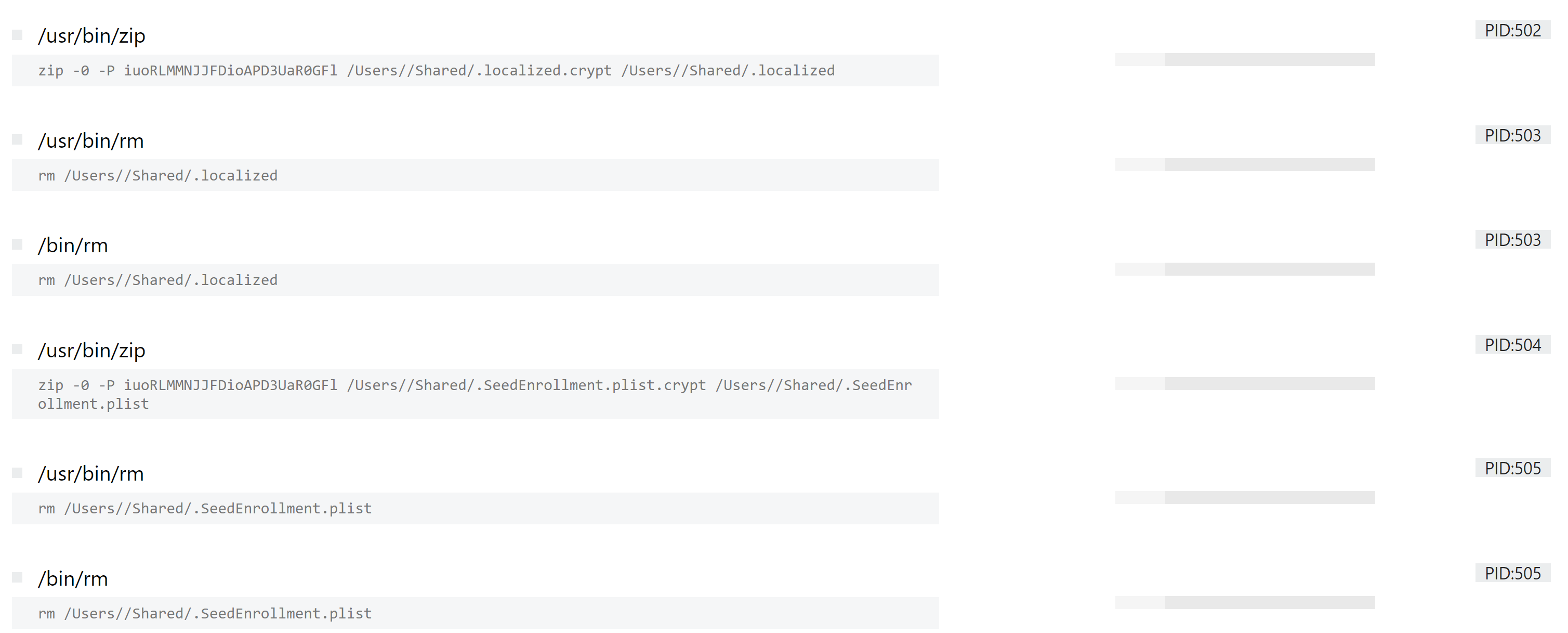
We can also clearly see the creation of the sample’s ransomnote, which is dropped to multiple directories using commands like the following:
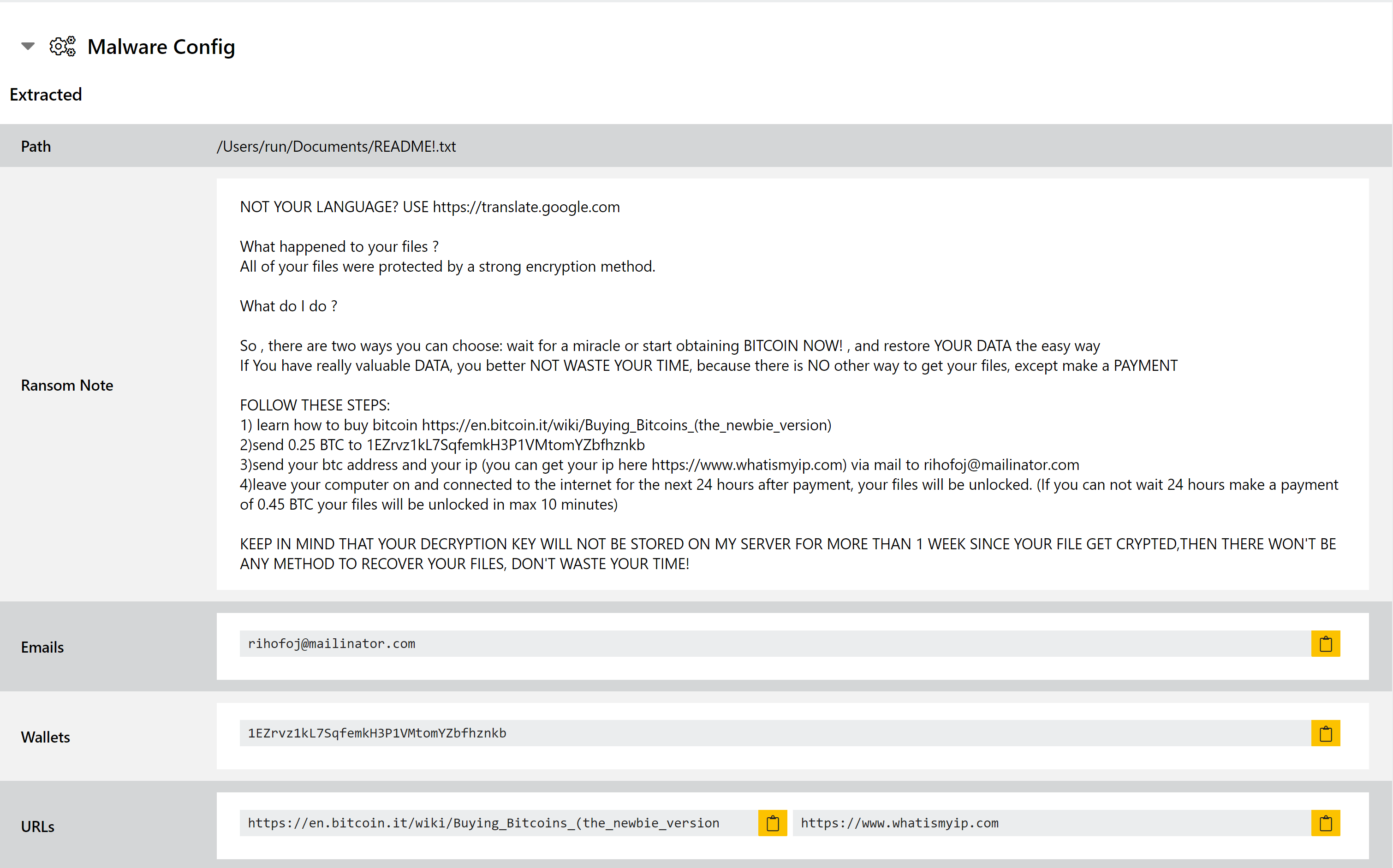
touch -mt 201002130000 "/Users/run/Documents/README!.txt"
As with Triage’s Windows support, the platform can detect and dump ransomnotes created during macOS analysis. These are presented under the Malware Configuration section at the top of the report, and contains relevant information like emails, cryptocurrency addresses etc.
3. HiddenLotus Backdoor
HiddenLotus is an evolution of the older OceanLotus malware, and was originally discovered in November 2017 after Apple added detection for it in a patch and alerted researchers to its existence. A full blogpost of the samples can be found from MalwareBytes here.
Analysis link: 210603-wqhytdhkea
The family has a somewhat unusual method of hiding itself which makes what would otherwise be a standard backdoor into a much more interesting specimen. It masquerades as a PDF document file but doesn’t use the normal, well documented tricks to hide its true extension. Instead it makes use of what was, at the time at least, a novel trick to manipulate macOS LaunchServices into running the file as an executable.
It is able to do this because the malware is distributed as a .app file bundle. These are basically folder structures a little like archives such as .zip, but specific to macOS. The d character in the .pdf extension is actually a non-Latin character, making the file extension invalid. When run by the user via double click etc. this causes LaunchServices to examine the app directory structure within the file instead of opening it with a PDF reader, which results in the malicious application being triggered.
In order to keep up the charade, the malicious app will actually open a fake PDF document at the start of its execution, to make the user believe the file has run as expected and not arouse their suspicions. We can see this during analysis through the Live Monitor/Replay:
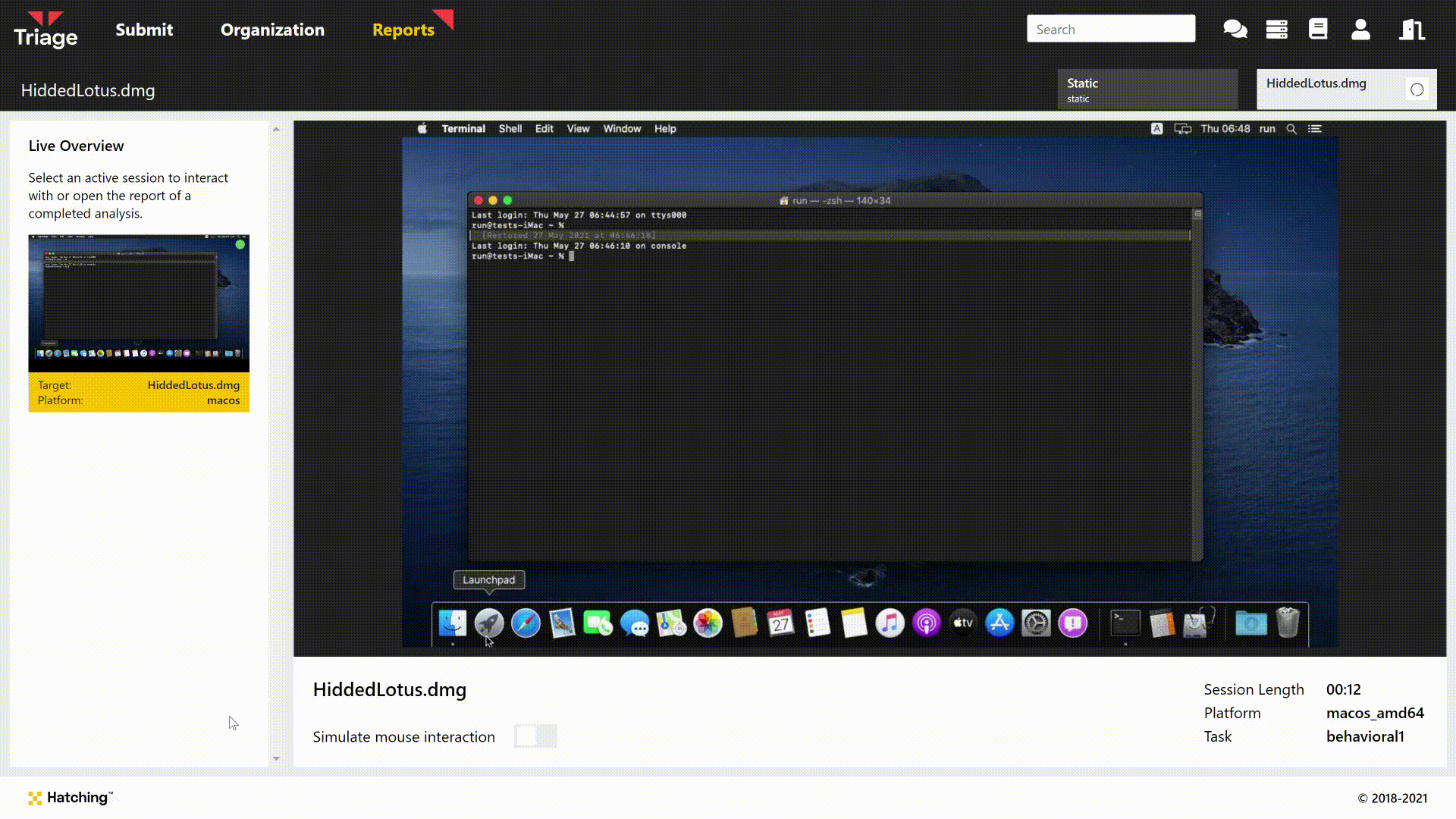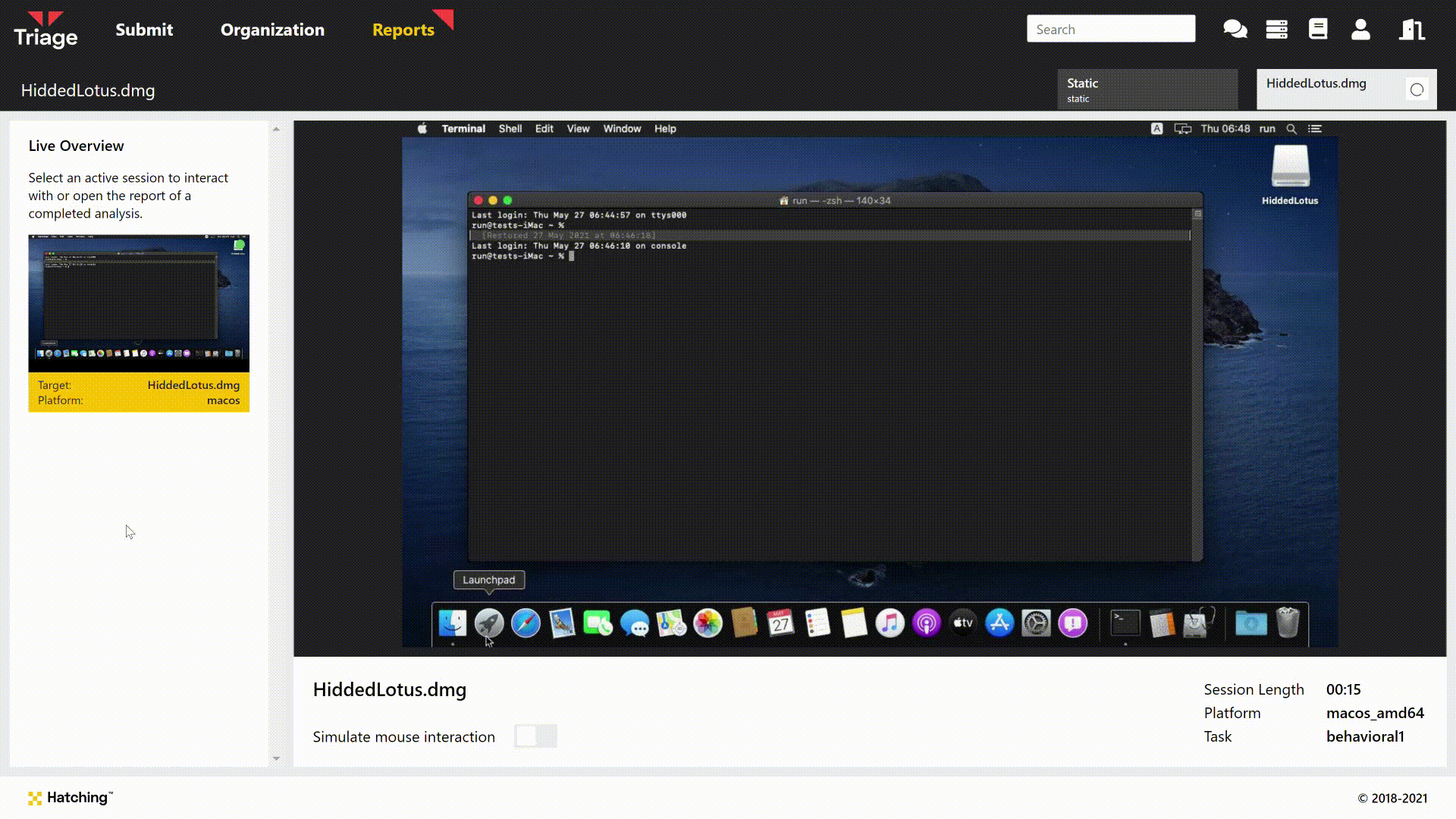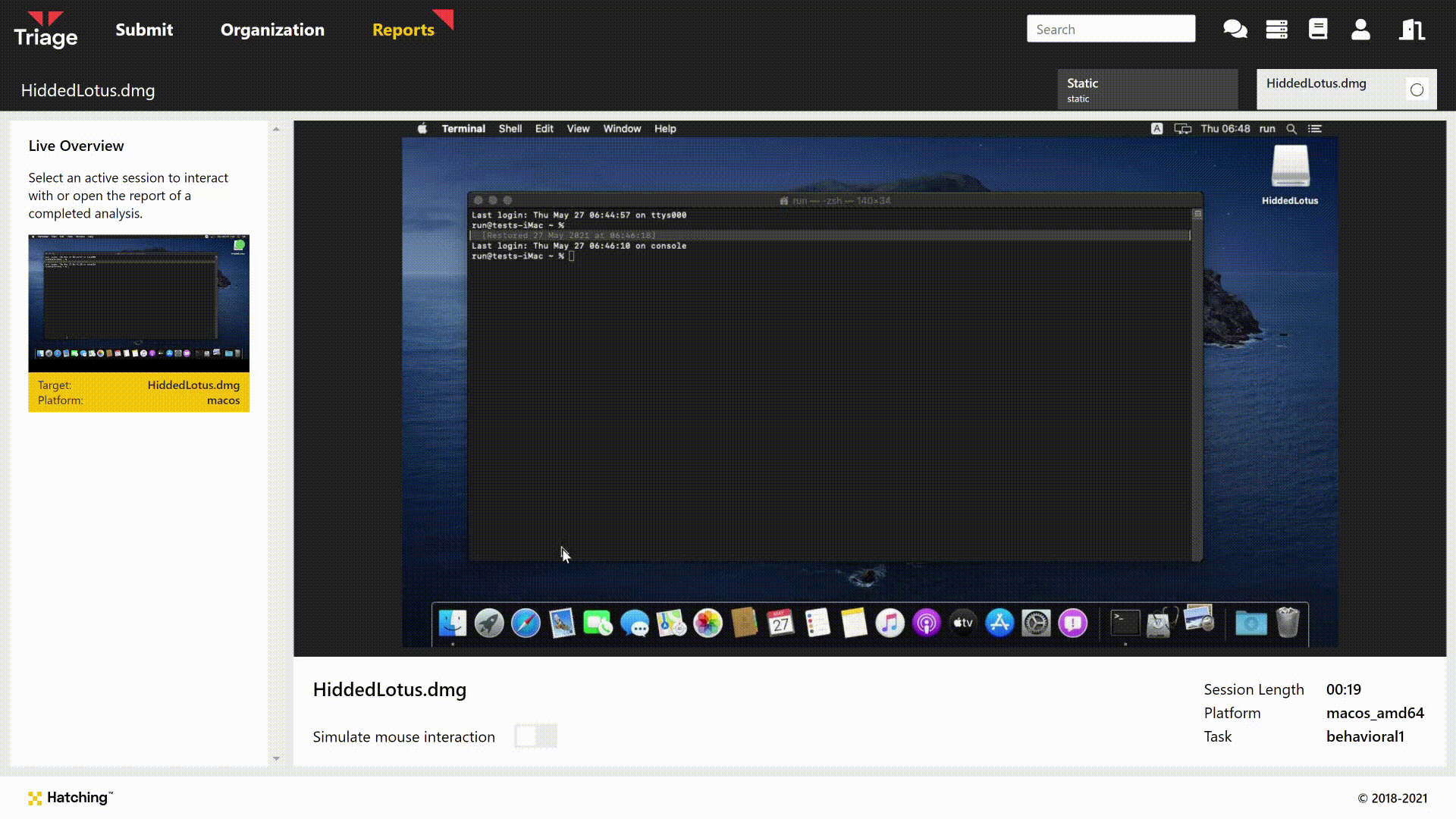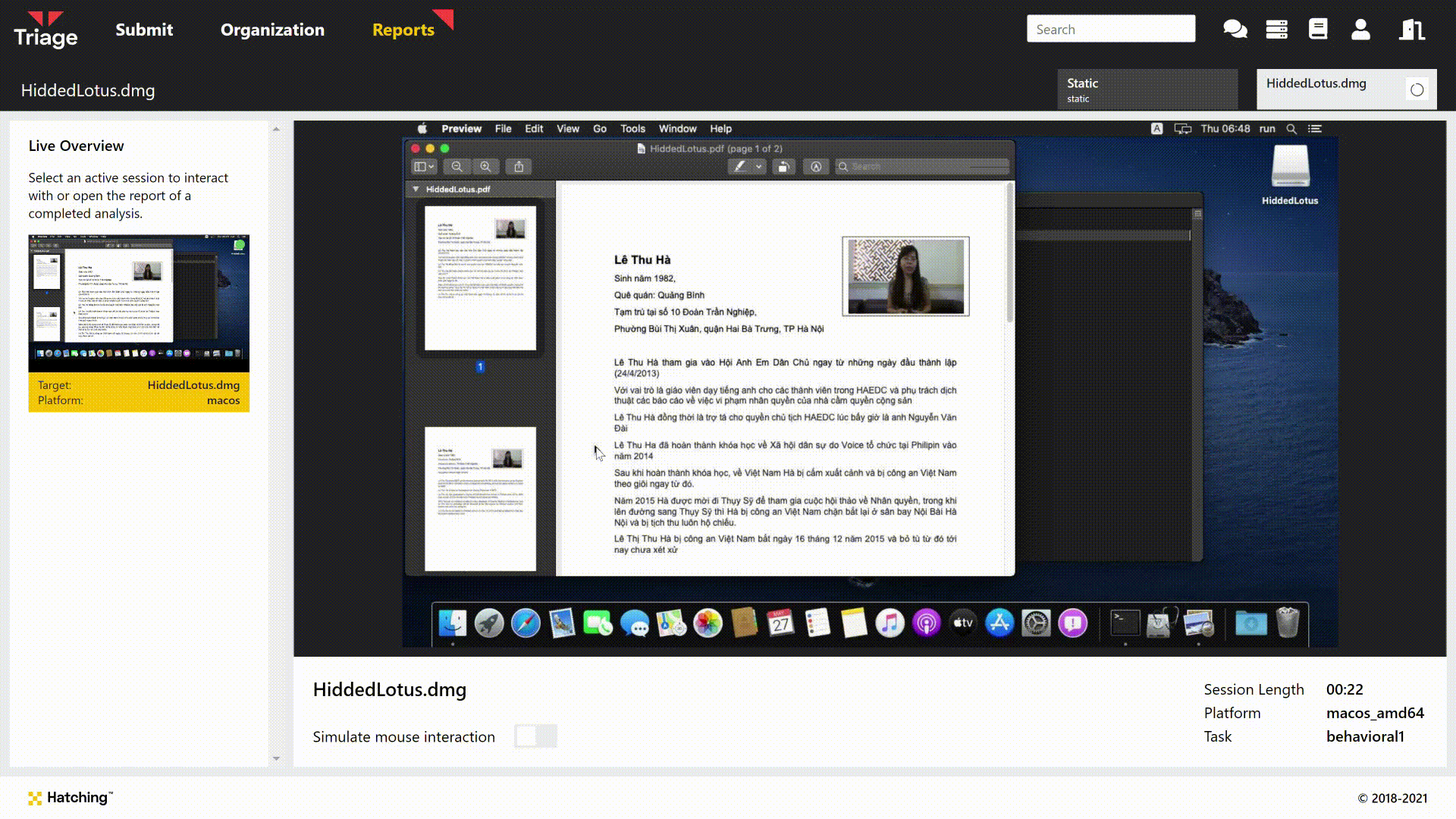
Triage bypasses this process as file identification recognises the structure as being an app file rather than a true PDF. However the end result is the same, as can be seen above.
Looking at the process listing, we can see a large number of actions related to the collection of information about the compromised system, including even things like Calendar contents. For example:
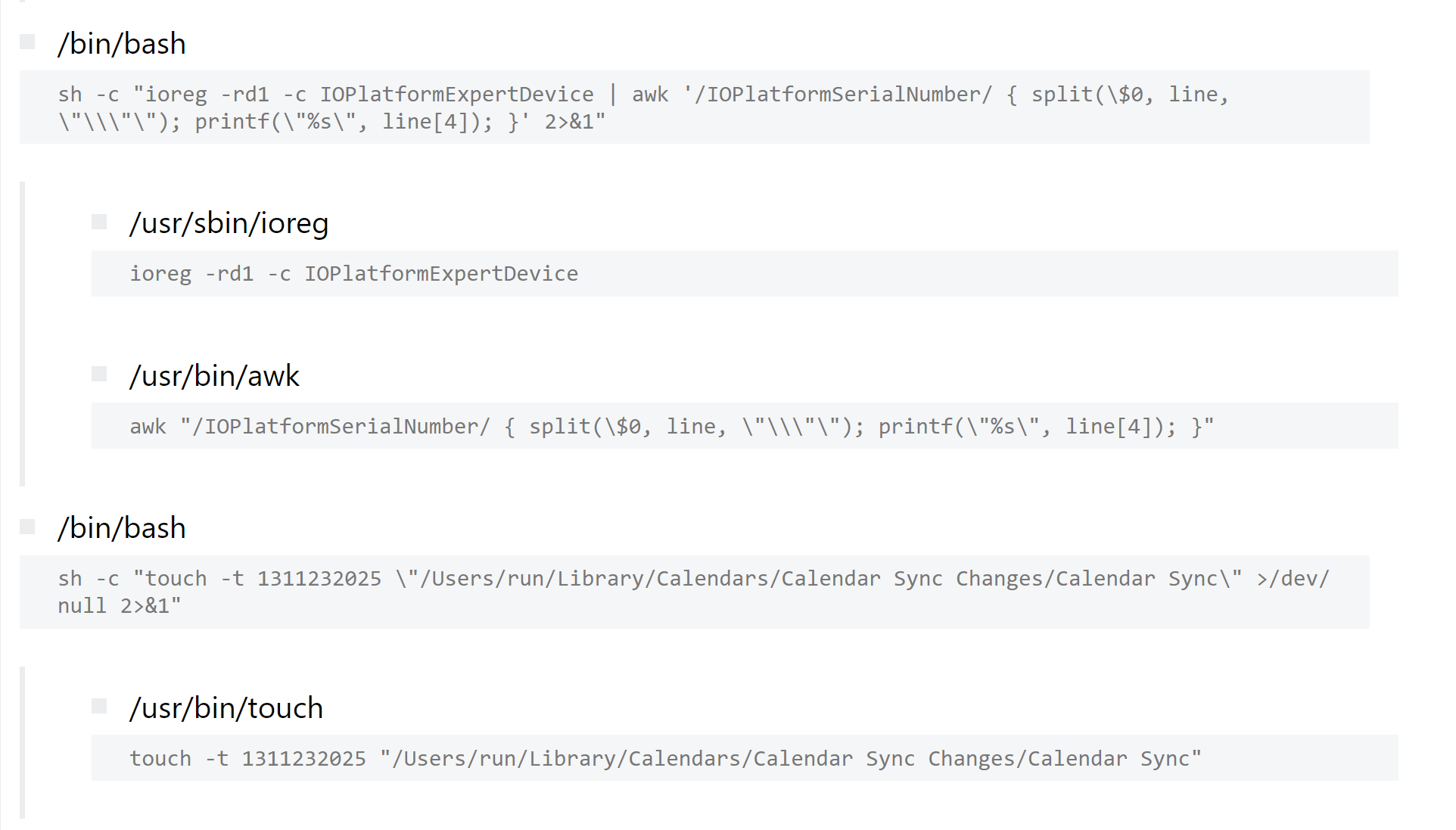
Conclusion
We hope this post has given you a good overview of Triage’s macOS analysis capabilities, and what you can expect from it as we move forwards.
As already mentioned, this is only the first version of the system we have planned out. We have a number of next steps already in mind, and the list of features will certainly expand as we receive feedback and identify areas which could benefit from improvements or additional support. Below you can find something of a basic roadmap for our macOS support, although the exact order might vary in practice.
Future Plans
- Flesh out detections, especially in terms of general behavioural detections not specifically linked to a single family.
- Extend file type support, initially targeting bash scripts and Office documents
- Add support for capture/dumping of TLS master secrets to enable decryption of HTTPS network traffic captured during analysis.
- Add ability to log and track Mach and Mig hooks, which are used to inter process communication within macOS.
- Implement human interaction module to allow automatic bypassing of popups, dialog windows etc. which can often be used as a rudimentary anti-sandbox technique.
We’ll be back next week with our usual Triage Thursday update roundup, and that will likely include the first set of detection updates as we work towards getting a good baseline in place for more exciting improvements to come. In the meantime, have a go, play around, and let us know what you think! We’re always interested in hearing your use cases and what features would be most valuable to you in getting the most out of the platform.
You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
