It’s been a quieter week for updates but we still have a few things to introduce in this Triage Thursday blogpost.
- Danabot detection update
- XLoader Android signatures
- AlienBot Android signatures
- .xz archive support
- Email URL decoding
In less update-related news we have now added some basic integration with VirusTotal which will automatically submit details of analysed files to their entries on the website. Look out for our comments on VirusTotal samples in the future!
As usual if you have any comments, suggestions or other feedback about Triage feel free to get in touch with us. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
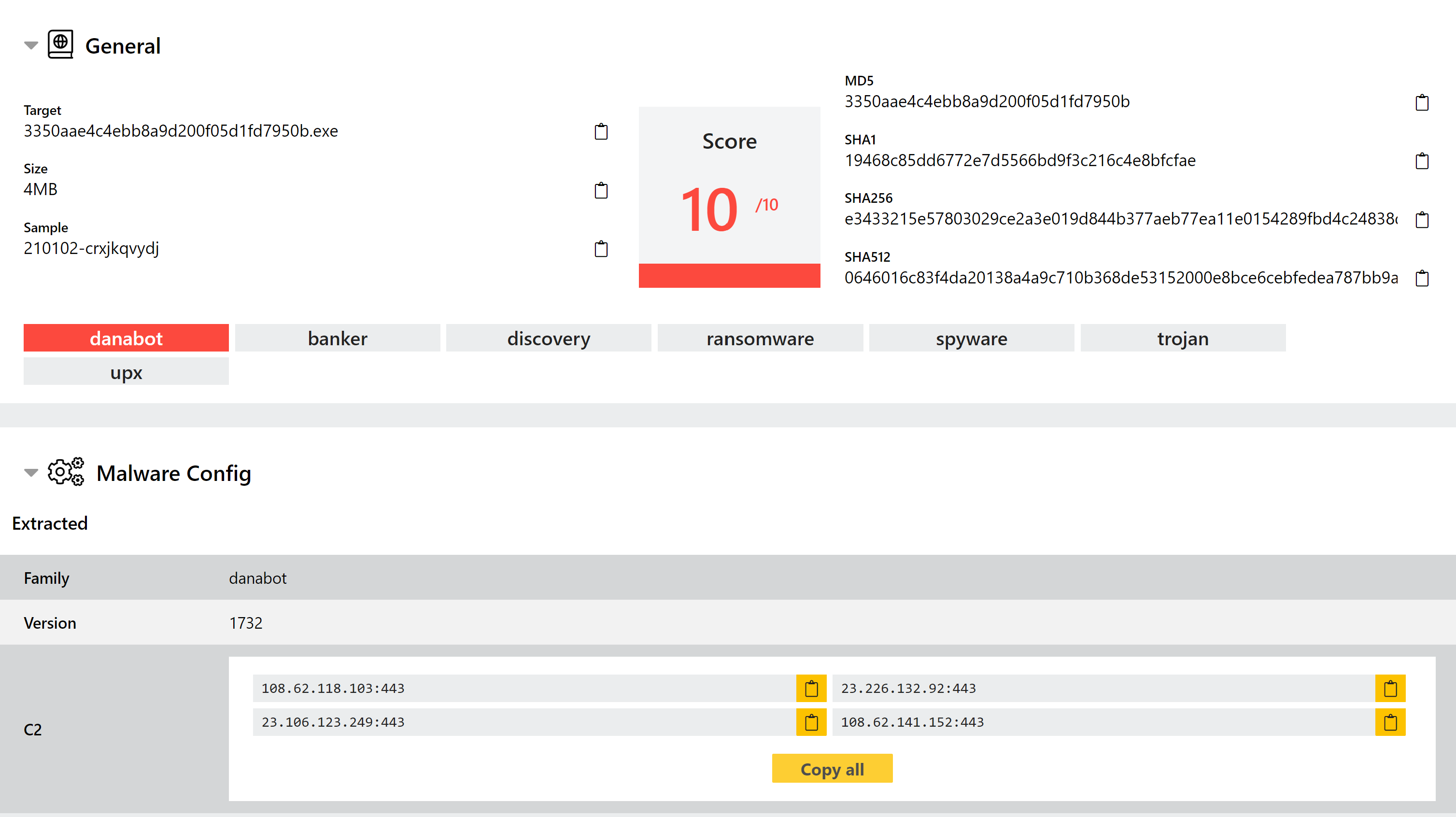
Danabot Detection Update
Danabot is a banking trojan/stealer which has been seen in widespread usage since mid-2018. The malware itself is modular including functions for browser injections/network sniffing, stealing credentials stored locally by a range of software, and remote access capability.
The family has gone through a few iterations since it first appeared, with Proofpoint recently publishing details of a new 4th version spotted at the start of 2021. This is a relatively large set of changes which has added some additional anti-analysis methods, as well as reworking the structure of several aspects.
We have now examined these samples and implemented new detections to ensure we are catching the latest versions of the family. During this review, we have also implemented a new configuration extractor for Danabot to make more information available on campaigns, version etc.
Analyses:
New XLoader Android Signatures
XLoader is a trojan which targets Android systems. It was first spotted in April 2018, infecting devices though compromised DNS services used for Push notifications.
The malware includes data gathering capability to harvest personal information from infected devices, as well as its main feature of downloading additional malware payloads.
According to Cyware the family’s distribution campaigns have mainly been aimed at South-East Asian countries, with the malware itself generally being attributed to a Chinese threat group.
Analyses:
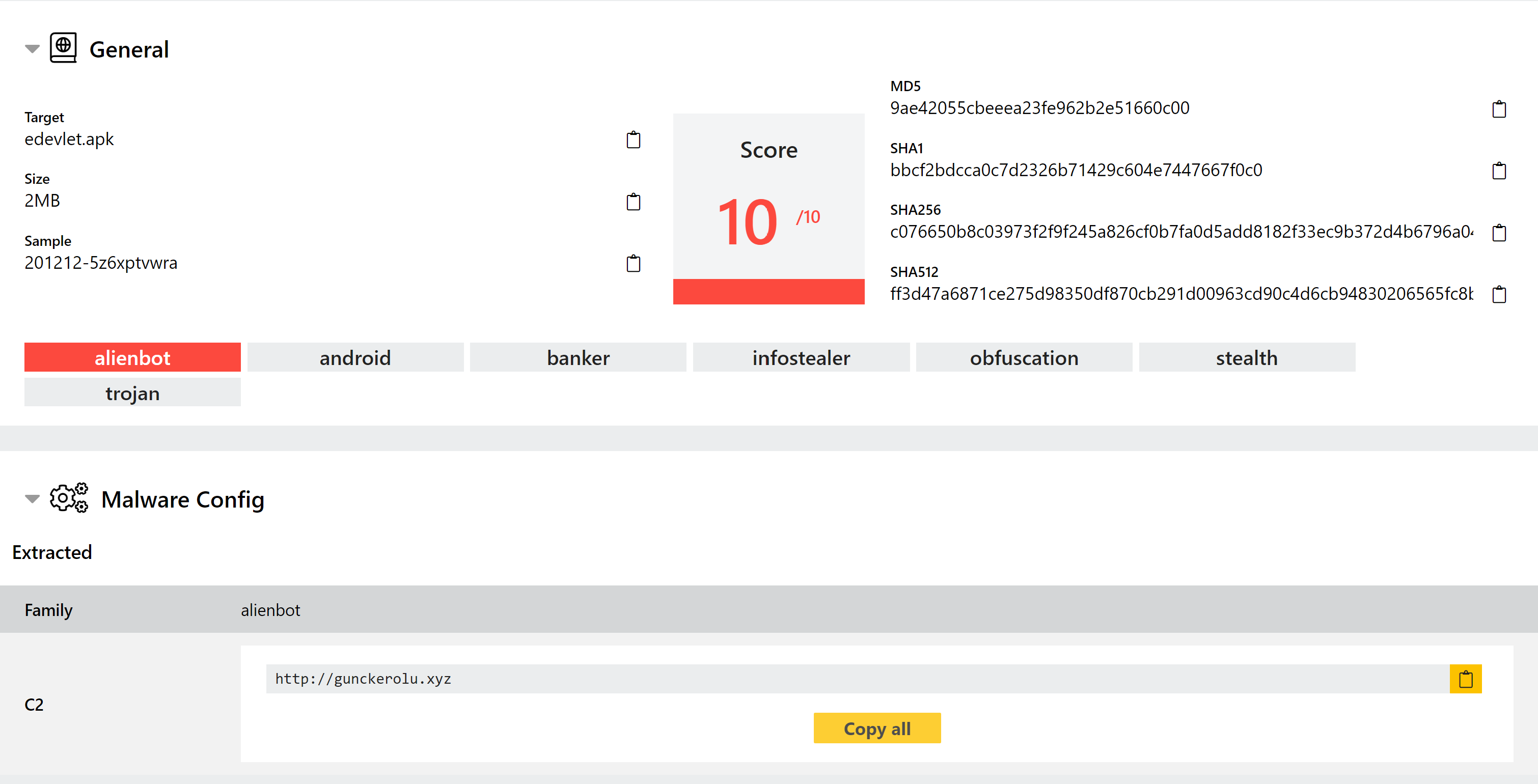
New AlienBot Android Signatures
AlienBot is an infostealer banking trojan, again targeting Android devices. It is a fork from the older and widely used Cerberus trojan, and was first spotted in January 2020.
The Alien family was built after the original Cerberus developers reportedly failed to provide updates to circumvent new detection methods on the Google Play Store, and as such now includes additional features as well as improved evasion. It is still actively being developed, and is sold through forums etc.
We have now implemented detection for this family, including an extractor to dump the C2 address for the sample.
Analyses:
XZ Archive Support
Triage now supports submission of .xz archives, common on Unix systems. This file type is handled like all other archive formats, and will be unpacked during static analysis as normal.
URL Decoding
We’re always looking at ways to refine the output produced by Triage and make it as relevant and useful as possible. This latest update includes a small tweak to the way in which email links are handled. For many enterprise systems, links will be wrapped in a proxy link, which generally shows a sanitised version of the webpage to the user to reduce the risk of phishing and drive-by infections. For example, a link to the Hatching website - https://hatching.io/ - might look like this after coming through the URLDefense email filter:
https://urldefense.proofpoint.com/v2/url?u=https-3A__hatching.io_&d=DwIDaQ&c=udBTRvFvXC...&r=lGPej0UJC...&m=9aUARg...&s=wPDpZ4...&e=
For obvious reasons however, when analysing these in a sandbox we want to run the original link and not the sanitised, wrapped version. We have now added decoding to automatically handle these and remove the need to manually submit the correct URL.
