Welcome back to our Triage Thursday blog series, where we introduce all the new updates that have been made to the platform over the last week. As usual we’ve got a mix of improvements to existing detections as well as a few new additions to our family support - let’s get straight into it:
- New signatures for Zingo stealer
- New signatures and configuration extractor for Lumma stealer
- New signatures and configuration extractor for NullMixer dropper
- Updated rules and configuration extractor for new Cryptbot version
- Tweak for Bumblebee detections to handle new undetected samples
- Updated rules for Allcome family
As always you can contact us any time directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Zingo Stealer
Back in April 2022 Talos published a blogpost detailing the new ZingoStealer family. First seen in March they reported that it appeared to be in active development with multiple versions observed even in just the few intervening weeks.
The malware was released free of charge by a threat group known as ‘Haskers Gang’ who have been active since the start of 2020, developing various tools like stealers, cryptocurrency miners, RATs, and crypters to help others hide their payloads from detection. The developers manage a community of users via Discord and Telegram channels, using the latter to collect logs from infected systems and push announcements to users of ZingoStealer specifically. Their Discord server is more generalised for sharing their different tools and updates with their supporters.
Unlike many similar families ZingoStealer seems to actively target Russian-speaking users with payloads often being concealed as game cheats, key generators and pirated software downloads (though the group themselves also seem to primarily communicate in Russian). Since it has been made openly available to their Discord community the malware is likely being used by a wide variety of different threat actors for their own campaigns, rather than any centralised effort.
The actual functionality is pretty familiar from similar threats. It dumps credentials from common web browsers, steals cryptocurrency wallets, and enumerates general system information. In some cases it has also been seen dropping cryptocurrency miners to infected systems. You can find a detailed writeup in Talos’ blogpost.
We have reviewed a number of the samples made available by Talos, and implemented general detections for the family. Examples are provided below.
Analyses:
Lumma Stealer
Last week our friends over at Sekoia.io released some information about a new stealer they’d observed called Lumma. A brief summary of it and its capabilities can be found in their Twitter thread linked here:
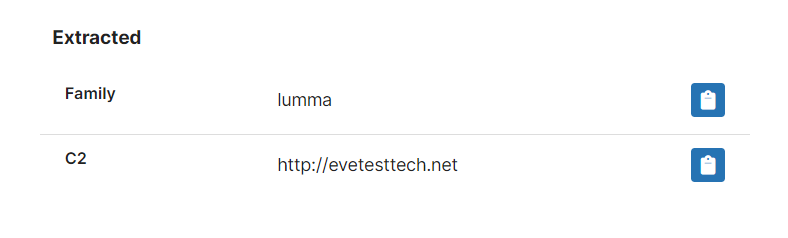
It is a fairly straightforward stealer written in C, and bearing a strong resemblance to the older Arkei and Vidar families. Its focus seems to be primarily on cryptocurrency wallets though it also targets other data sources as well.
Based on the samples we were able to identify we have implemented detections and an initial configuration extractor for the family. This is able to dump out the C2 information that’s hardcoded into the samples.
Analyses:
NullMixer Dropper
NullMixer is a new threat reported by Kaspersky earlier this week. It is a dropper used to deploy a range of other malware families, generally all at the same time - a typical infection seems to lead to several payloads being delivered to an infected machine rather than just a single campaign. These are generally stealers like Redline, ColdStealer and Fabookie but has also been seen to include other droppers like Smokeloader.
The family is generally distributed via malicious websites offering various software cracks, keygens and activators. A fair bit of effort seems to be put into keeping these sites at the top of search results for these kinds of applications to ensure they lure in new victims.
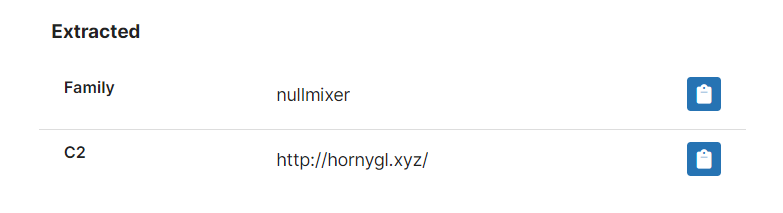
We have analysed a number of samples and implemented a basic configuration extractor to dump the C2 information, as well as more general detections.
Analyses:
CryptBot
CryptBot is an infostealer which has been active in the wild since early 2019. Although its use has expanded over time it is regularly distributed alongside legitimate software which acts as its lure, often affecting users installing cracked versions of software downloaded from torrent sites.
The family has been quite active throughout 2021 and 2022 with a few new updates and variants appearing over that time. We released a couple of set of updates earlier in the year, but have recently seen a new set of samples generally being referred to as version 2. This was brought to our attention by this tweet from abuse.ch.
While digging into the new version we also came across some samples from recent months which, while they weren’t part of the newest batch, were not being properly handled by Triage. We’ve taken the opportunity to also review these and apply the necessary updates - for reference we’ve provided some examples of both below.
Analyses:
-
Version 2:
-
Older samples:
BumbleBee
BumbleBee is becoming a fairly regular visitor to this blog, so we won’t go into too much detail on the background again here. If you’re interested you can find some more information in our blogpost from a couple of weeks ago when we applied some more minor updates for it.
The latest set of samples had some small changes which were getting past our extractor so we’ve made some updates to fix this. These were mostly related to examples with the botnet ID 2309.
Note that to run properly BumbleBee requires that a specific DLL export function is called so they generally need a custom script to execute automatically - you can do this by bundling them as an archive as described in our archive submission blogpost. The command can vary for some samples but generally looks like this:
rundll32.exe %TEMP%\sample.dll,maincase
The example below is an exception and can run on its own using default settings.
Analyses:
AllCome
AllCome Clipbanker is was first seen in early 2022 being advertised through cybercrime forums. It mainly targets financial assets with a heavy focus on cryptocurrency wallets, with users being able to customise it to go after additional currencies via a builder framework which can be purchased from the developers.
According to a report by GData all current versions use scheduled tasks for persistence, and leverage mutexes to ensure that only a single infection occurs on a machine.
We added detection for the family back in February 2022 but recently noticed some samples slipping past our detection rules. We’ve now tweaked these to properly handle them and trigger configuration extraction.
Analyses:
