Welcome to another Triage Thursday blogpost, where we take a look at the week’s updates. It’s only a short one today but we hope you’ll find these useful in your analyses:
- Updated IcedID detections to handle new variant
- Added configuration extractor for Mercurial Grabber
- Added family detection for AllCome Clipbanker
- Tweaked Qakbot configuration extractor for new version
If you discover any issues or missing detections while using Triage, please do send us feedback. It’s a big help in deciding what we should be prioritising. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account!
IcedID
IcedID, otherwise known as Bokbot, is a banking trojan which targets financial information on infected machines. It’s a very active family, receiving regular updates to augment and improve its functionality since it first appeared back in late 2017. It is a relatively advanced stealer containing a wide range of functionality, including:
- Anti-VM/anti-debugging measures
- Web injection/man in the browser
- Full remote access
- VNC module for full UI control of the infected system
Most recently the family has been reported dropping CobaltStrike payloads.
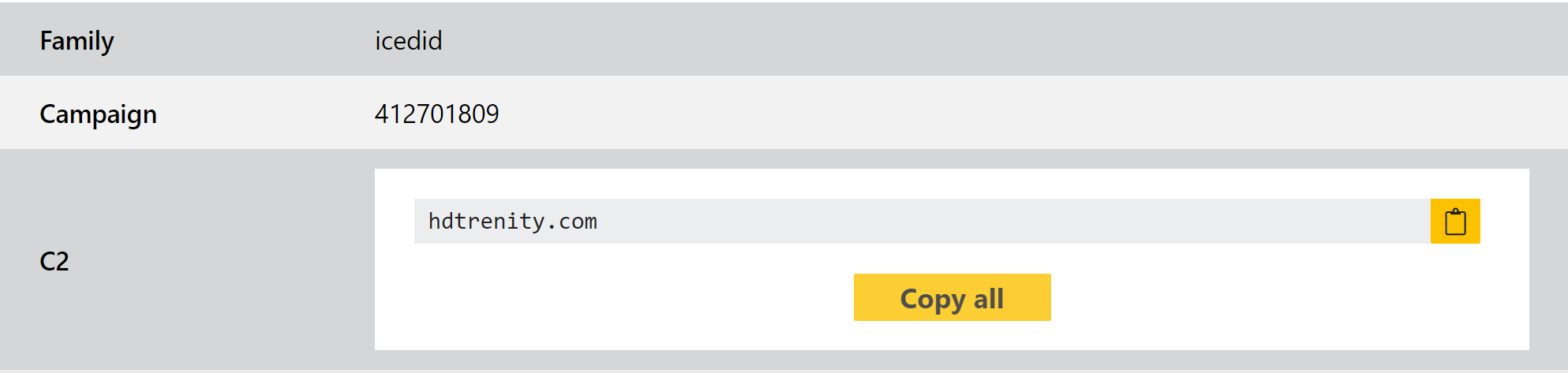
As part of the latest campaigns we noticed a new variant of the family which had some structural changes which prevented our configuration extractor from dumping out the C2 field. We have reviewed quite a few of these samples and updated our handling to work with them properly.
Analyses:
Mercurial Grabber
Mercurial is a stealer family available openly on Github, being promoted “for research purposes only”. It is written in C# and has a good range of features, including a couple of slightly unusual targets in that it attempts to steal user accounts for Roblox and Minecraft besides the usual web browsers/Discord. To take the feature list directly from the author’s readme:
- Grabs Roblox cookies from Roblox Studio
- Grabs Minecraft sessions
- Grabs Google Chrome passwords
- Grabs Google Chrome cookies
- Grabs Discord token
- Grabs victim machine info
- Grabs Windows product key
- Grabs IP address, geolocation
- Grabs screenshot
- Anti Virtual Machine
- Anti Debug
Discord generally serves as the C2 infrastructure for the family, with their webhook functionality being abused to provide a communication channel.
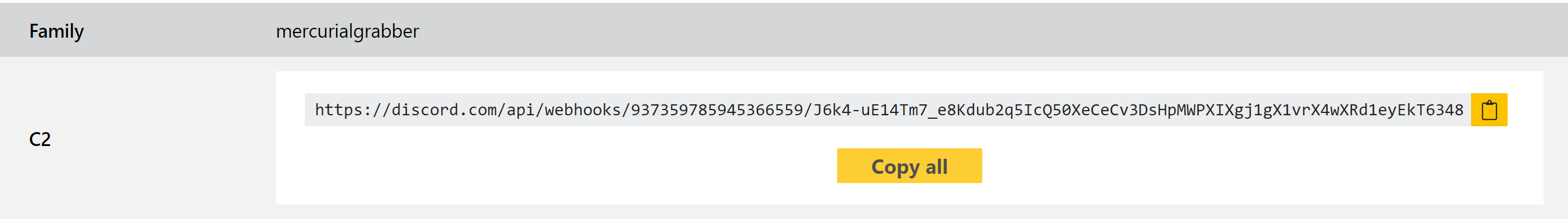
We added initial detection for Mercurial back in August last year, but as it has stuck around and continues to pop up regularly in the wild we have now revisited it to add a full configuration extractor too. This can dump out the URL being used for C2 communications.
Analyses:
AllCome Clipbanker
AllCome Clipbanker is a new stealer family discovered recently being advertised through cybercrime forums. It mainly targets financial assets with a heavy focus on cryptocurrency wallets, with users being able to customise it to go after additional currencies via a builder framework which can be purchased from the developers.
According to a report by GData all current versions use scheduled tasks for persistence, and leverage mutexes to ensure that only a single infection occurs on a machine.
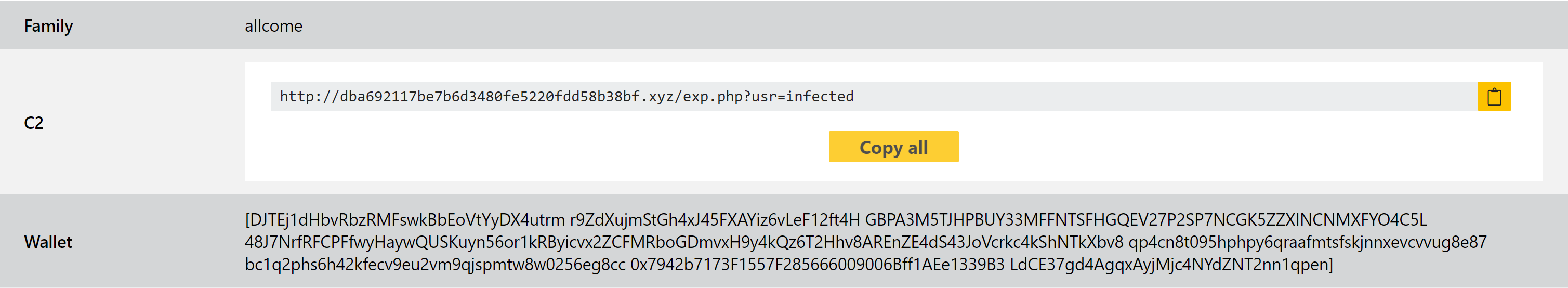
We have reviewed the samples made available by GData and @3xp0rtblog to implement behavioural detections and a configuration extractor. This can dump out the C2 URL being used for exfiltration, as well as the target wallet addresses where stolen cryptocurrencies are sent.
Analyses:
Qakbot
Qakbot likely needs no introduction, but if you’re not familiar with the family it is a powerful infostealer/trojan which has been in use in various forms since around 2009. It has been repurposed for a few different roles over the years, including a banking trojan attacking Active Directory servers and a stint as a ransomware dropper.
Triage has long supported both behavioural detection and configuration extraction for the Qakbot family, but as an active and advanced threat it regularly requires minor tweaks to keep our signatures up to date. A version that was evading our configuration extractor was recently reported to us by @ffforward so we have applied some changes to ensure it is properly handled.
