Welcome back to our Triage Thursday blog series! We’ve missed a few weeks due to holidays and other things going on but we’re pleased to be back again this week with the normal set of update notes.
Of course just because there hasn’t been a blog doesn’t mean there have been no updates over the last few weeks! There has been new support added for many different stealers, ransomware and Android banker families including the addition of configuration extractors for Sharkbot, IceXLoader, Gandcrab, and a few different Mirai variants. We have also updated and improved existing coverage for Nymaim, Raccoon, PandaStealer, and BluStealer based on recent samples and feedback.
Moving on to the news from this week, we have made the following detection changes:
- New signatures for Moisha ransomware
- New signatures for BlackBasta ransomware
- New signatures and configuration extractor for Asbit RAT
- New configuration extractor for FFDroider stealer
- Update for Bumblebee rules and configuration extractor
- New signatures for more Mirai architectures and cleaned up some old rules causing false-positives
- Improvements for ransomnote handling to reduce false-positives
Something else you’ll likely have noticed by now is that we’ve deployed a new UI update which significantly changes the appearance of Triage. This is mostly cosmetic and does not affect functionality, and is meant to bring the styling inline with Recorded Future’s other products - we’ll be continuing to tweak and improve on it over the coming weeks and months. If you come across any issues with the new UI or have any feedback please feel free to reach out!
As always you can contact us any time directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Moisha ransomware
Moisha is a new ransomware family which was first reported on Twitter in August 2022, by MalwareHunterTeam.
The family is a fairly standard ransomware which uses the double-extortion approach to pressure victims into paying. Like many similar threats it will initially go through a predefined list of processes and try to kill them - this generally includes security software like Windows Defender as well as applications which may have a lock on important files that would prevent their encryption.
Interestingly it does not actually rename files or change their extensions, unlike the vast majority of other ransomware. It does however drop .txt ransomnotes to the system - these include a company name in the header suggesting the family is used in targeted attacks rather than more generalised campaigns.
We have limited samples available currently but have built out initial detections and will make any necessary tweaks in future as we come across more.
Analysis:
BlackBasta Ransomware
Like Moisha, the Black Basta family also uses the double-extortion technique and exfiltrates sensitive data before beginning file encryption. It first appeared in April 2022 and has been very active since then, with Unit42 reporting over 75 compromised companies as of late August 2022.
It has a large focus on speed of encryption to try and make sure it can accomplish its purpose before triggering any defences. As part of this it uses an unusual technique where it only encrypts segments of 64 bytes and leaves gaps of 128 bytes, to minimise the time needed while still rendering the files unusable.
The family is written in C++ and has versions for both Windows and Linux. Unit42 also report that a version specifically targeting VMware ESXi virtual machines was observed in June 2022. We’ve built out detections for both platforms.
Analyses:
- Windows samples:
- Linux samples:
Asbit RAT
At the end of August Juniper reported a new Chinese RAT they were increasingly seeing in the wild. Called Asbit, the earliest samples they could fine go back to May 2021 suggesting it has been active for some time while escaping mainstream attention.
The family includes a few evasion techniques including using DNS-over-HTTPS (DOH) to try and evade network monitoring. It also sets up a proxy to enable it to man-in-the-middle all browser traffic. Infection generally involves a few stages, going from a malicious installer to a DLL that then downloads and deploys the final payload. Downloaded files are named and stored in a way meant to resemble .NET libraries to reduce suspicion.
The RAT itself provides full remote control of the infected system including directly controlling it via a remote desktop, as well as prebuilt functions for things like screenshot capture, file download, and command execution. It is still in active development and has seen several versions since the initial release discovered by Juniper - it seems likely it will continue to evolve in the future so we’ll keep an eye open and update detections as needed.
Analysis:
FFDroider
FFDroider first popped up around April 2022 and we quickly added basic support for the family to Triage. However we have continued to see samples hitting the public and private clouds so this week decided to revisit it and build out a full configuration extractor which can dump the hardcoded C2 address.
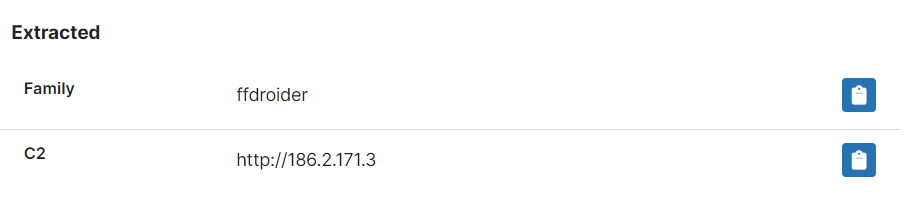
The family’s base functionality is pretty familiar and in fact more limited than many of its competitors in the infostealer space - it seems to restrict itself to stealing credentials stored on the infected machine by web browsers like Chrome, Firefox and Edge rather than the much more extensive target lists common in other stealers. However its end goal is a bit different to most.
Rather than just directly monetising data stolen from the victim, like stealing cryptocurrency wallets, this family is going after social media accounts specifically. These accounts are then accessed to extract information about them, with a focus on relevant advertising networks on those platforms which can then be used to run malicious ad campaigns using accounts already verified and setup to do so. Interestingly this process is mostly automated with the malware itself carrying out checks of credentials in real time from the victim’s PC, and extracting personal and financial information from any successful login attempts which is sent back to the C2 server for further use.
According to ZScaler’s report on the family FFDroider goes after credentials for the following websites:
- www[.]facebook[.]com
- www[.]instagram[.]com
- www[.]amazon[.]ca/cn/eg/fr/de/in/it.co.jp/nl/pl/sa/sg/es/se/ae/co.uk/com/com.au/com.br/mx/tr
- www[.]all-access.wax[.]io
- www[.]ebay[.]com
- www[.]etsy[.]com
- www[.]twitter[.]com
Analyses:
BumbleBee
BumbleBee is a loader which quickly rose to prominence back in April 2022 - we’ve written about it a few times on this blog since then as it has been actively developed and has seen a few updates since release which affected our detections or configuration extractor.
So far it has formed part of the toolkit of an Initial Access Broker group called EXOTIC LILY, who gain access to systems and networks which they can then sell on to other groups like ransomware gangs rather than directly exploiting it themselves. For example BumbleBee was seen early on distributing Conti ransomware and CobaltStrike payloads.
On a technical level it is a fairly typical example of its type, using WMI to harvest general information about the system and report it back to the C2 infrastructure which then issues commands for the next steps. This task can vary but mainly revolves around deploying code and payloads onto the system. You can find a full writeup of the family from Google’s Threat Analysis Group here.
In our update this week we have tweaked our configuration extractor to handle a new variant we’ve started seeing in the wild. These samples appear to include fake/decoy C2 addresses within the configuration to throw off analysis so we’ve improved handling to filter these out and only return the real C2s.
Analyses:
Mirai
As probably the most widespread IoT malware ever Mirai probably doesn’t need much introduction. The family was one of the first Linux-based threats we added support for, but the family is huge and sprawling with an amazing number of different versions, variants and spinoffs out there in the wild. Over the last few weeks we’ve been reviewing the family and trying to tidy up our many different detection rules, including addressing some which were incorrectly identifying samples as other IoT threats based on shared codebase/functionality.
This detection update is aimed at providing support for a number of variants aimed at different CPU architectures. We do not have VM images for all of these but even if the file doesn’t run properly there is generally something we can do with static techniques to return a result anyway, so that is the focus here. The list of analyses below includes a few for each of the newly supported architectures for reference.
Analyses:
- SPARC
- PowerPC
- Renesas
- Motorola
- ARC
