Welcome to another Triage Thursday blogpost, where we go over all the main updates that have been deployed to the platform over the last week. Today we’ve got several additions and changes to configuration extractors, while also expanding our coverage to some new families:
- New signatures and configuration extractor for Erbium stealer
- New signatures and configuration extractor for BUGHATCH downloader
- New signatures and configuration extractor for Zanubis Android banker
- New signatures and configuration extractor for Irata Android RAT
- Updates for a new variant of Marsstealer
- Updates for a new version of Vidar
- Fixes for AgentTesla configuration extractor to avoid incorrect output
As always you can contact us any time directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Erbium Stealer
Erbium stealer was first reported publicly by @3xp0rtblog in August 2022 and was brought to our attention by Abuse.CH not long after.
There isn’t too much information about the malware available in the community currently, but as usual it shares many features with other stealers. It starts off by gathering system information like hardware specifications, OS version/license details, user account information, etc. The samples then proceed to gather information from a wide range of different applications - although its focus seems to be on cryptocurrency wallets (looking for resources related to over 50 different wallet products) it also goes after the usual selection of web browsers, communication software (like Telegram and Discord), and other sensitive applications like FTP clients or the Steam gaming platform.
Erbium is provided for sale on forums rather than being used by a single threat group, so actual attack vectors vary depending on the user and their preferred methods. Researchers have been able to find several web admin panels online for the family, and in some cases have been able to access these to see the contents.
We’ve built out detections based on a large number of available samples, and we have also added a configuration extractor which dumps out the hardcoded C2 information. Some examples are provided below.
Analyses:
BUGHATCH Downloader
BUGHATCH is a malware downloader which was detected by the Elastic security team during a ransomware investigation in early 2022. In September they issued a dedicated blogpost that brought the family to our attention - we won’t repeat all the technical details here, but their post includes a lot of useful information about the observed campaigns.
The family itself is a fileless implant that is loaded directly into memory by a Powershell script, and includes quite a bit of advanced functionality. It is capable of elevating its permissions (using SeDebugPrivilege), and gathers a lot of information from an infected system before trying to deploy its intended payload. This includes stuff like: uptime (used to generate an encryption key for network communications rather then being an anti-VM technique); network interfaces; domain, username and image path of the current process; and Windows authentication tokens.
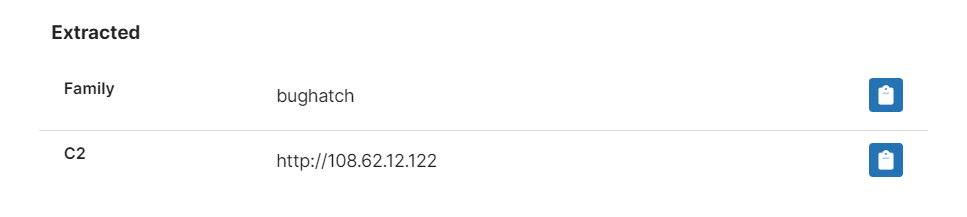
Based on the findings reported by Elastic we have built out detections and a configuration extractor to dump the C2 information.
Analyses:
Zanubis Android Banker
Zanubis is another recent addition to the threat landscape, being reported on in early September by Cyble (find their blogpost here). It is yet another banking trojan targeting Android devices, using overlay attacks to intercept and steal information being entered into legitimate applications.
According to Cyble’s analysis it mainly seems to focus on users in Peru, with the applications it tries to steal data from mainly relating to local banks and organisations (plus a couple of more general ones like WhatsApp and GMail). Notably the C2 commands they have identified are also in Spanish suggesting it was developed in the region.
Interestingly the list of targets is not hardcoded into the samples like many other Android bankers, and is instead fetched from the C2 during runtime. This presumably enables it to stay up to date and expand its options without needing to update the whole app.
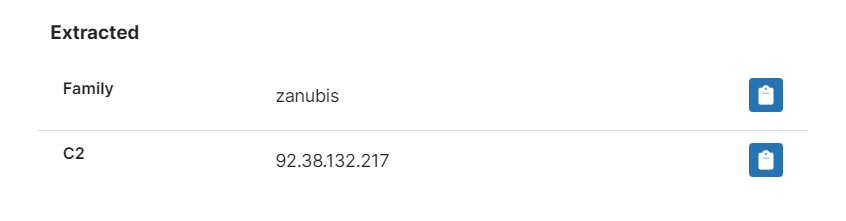
We’ve added general detections, plus a configuration extractor to dump out the C2 URL/IP in use. Some examples are below as usual.
Analyses:
Irata Android RAT
Irata is a RAT/stealer for Android devices which spreads via SMS phishing from other infected devices. It targets Iranian users, imitating government service websites to lure victims into downloading a malicious application which then hoovers up credit card information and 2FA authentication codes. As a cherry on top the fake government websites also try to trick visitors into paying a fee for the pleasure of being infected.
Once compromised the affected device is then turned into a bot which can further spread the infection using details received from the C2 server. According to analysis by OneCert in Iran it can also hide its icon from the device, making it hard for a general user to locate and remove it once infected.
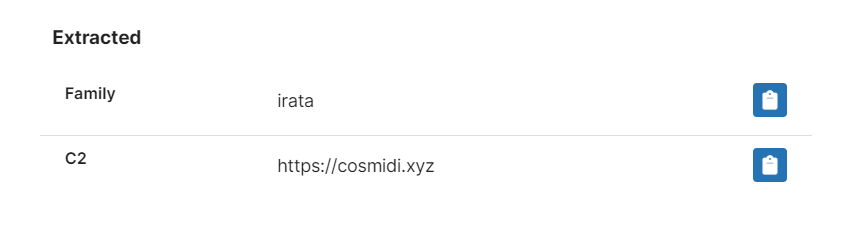
During our analysis we got hold of samples for several different versions, and have built out detection as fully as we can at this stage. As above we have also added a configuration extractor to dump the C2 information.
Analyses:
MarsStealer
We first added support for MarsStealer back in February this year, but it goes back a bit further into the middle of 2021. It is promoted as having the ability to steal credentials from a wide range of web browsers as well as a large number of cryptocurrency wallets.
The family leans heavily towards the cryptocurrency side if things - although it is not unusual to steal some of the more common wallets when available, Mars covers a significant number of products and can bypass some of the techniques used to secure them live on the infected machine.
According to a blogpost by the researcher 3xp0rt Mars Stealer is an updated version of the old Oski trojan which was shut down by the developers back in mid-2020. According to them the code base is very similar but with a few notable additions, like the extra cryptocurrency functionality and some more anti-debugging/anti-analysis checks.
We recently noticed a variant which was not being properly handled by our configuration extractor due to a difference in the way it stores C2 information versus the original samples we analysed. Where those used RC4 to encrypt it, this variant simply stores them in plaintext. We’ve updated our extractor to handle both approaches.
Analyses:
Vidar
The Vidar family continues to receive more updates, so we’re back with it again this week to update our rules to ensure the configuration extractor is properly triggered on the latest samples. The changes are fairly minor but should address the current issues.
If you’re not already familiar with Vidar we have covered it a few times on this blog, and there are many reports about it available online. You can find a brief overview from our blogpost from July 2021 where we initially introduced the configuration extractor.
Analyses:
AgentTesla
We recently received some feedback about our AgentTesla configuration extractor noting that in some cases C2 details were being incorrectly reported. AgentTesla has a few different options for exfiltrating data depending on the version, including FTP, SMTP and Telegram. In these particular cases the extractor was misidentifying one protocol for another and as such the actual output was invalid since it applied the wrong extraction algorithm.
Based on the samples reported to us we have taken a look at the extractor and made some improvements which should address the issue. However with a family like AgentTesla it can be hard to ensure every permutation is covered, so if you come across and other issues please do let us know.
Thanks to 0xToxin and others who reported the issue to us!
Analyses:
