Welcome back to another entry in our Triage Thursday blog series. We have a few more things to cover this week - mostly updated and improved family support and configuration extraction.
- Updates to handling of InfinityLock, Chimera, Ouroboros and SunCrypt ransomware
- TrickBot Update
- Emotet Detection Update
- RevengeRAT Static Detection
First though, our highlight this week is a new Overview report section which summarises the results of all tasks, both static and dynamic.
Analysis Overview
The Overview section brings together the findings from each task of an analysis to a single, easy-to-reference location
Overview for InfinityLock sample (200831-tnfgvzw7da)
This overview is backed up by a new overview.json file which is available via the API. Like the UI version it contains summary information on all tasks and files submitted for a single analysis. A new endpoint has been added, GET /samples/{sampleID}/overview.json, to allow fetching of this file directly. More information and request examples can be found in the API documentation.
Below we will quickly go over each section of the new overview and summarise the data available there.
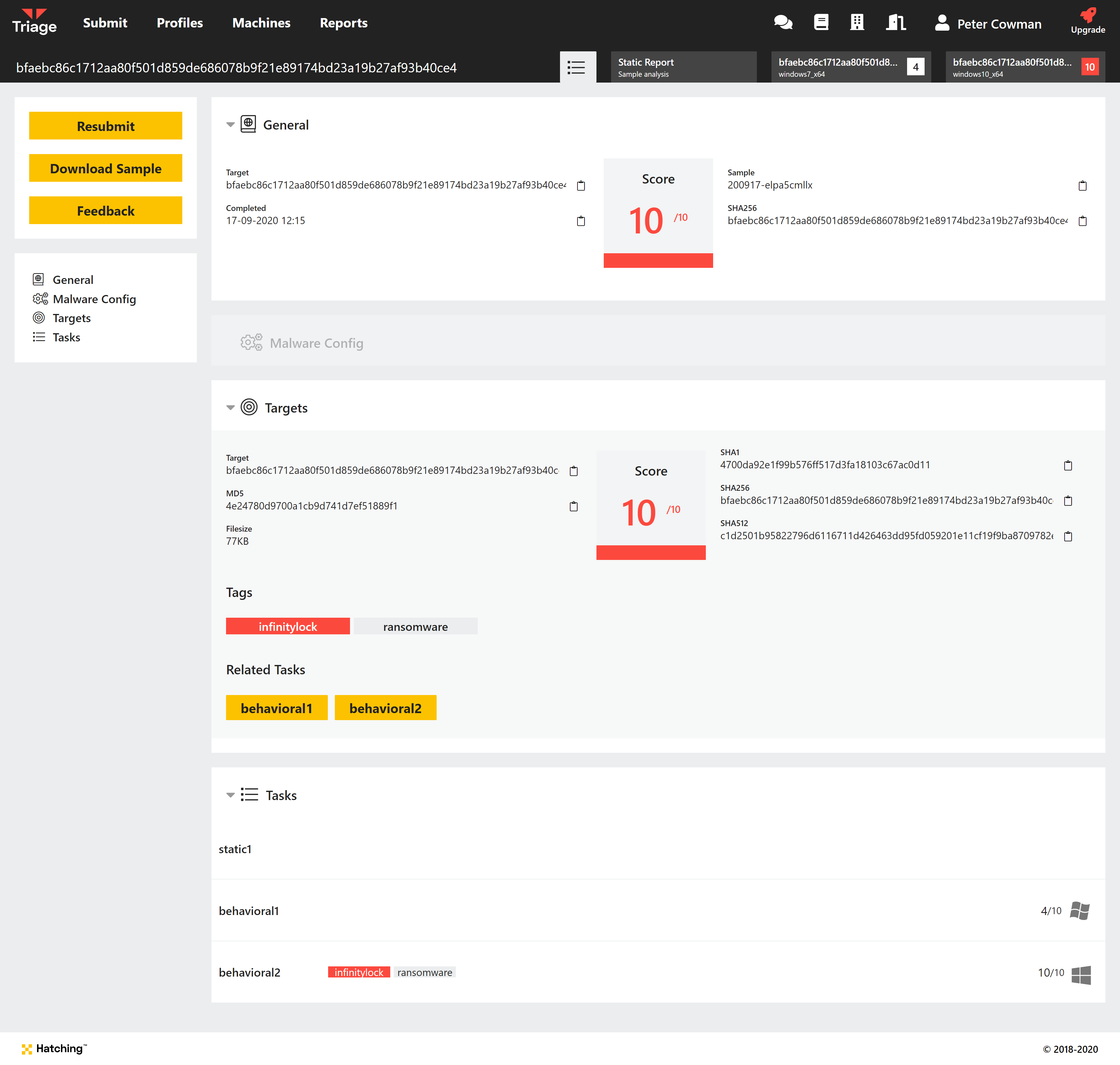
General Tab
Under General is listed basic information about the file that was submitted to Triage. For ZIP/archive files, this will be the archive itself - SHA256 hash, sample ID etc.
Note also that the score value shown here is the highest score across the analysis tasks - static, behavioural, etc.
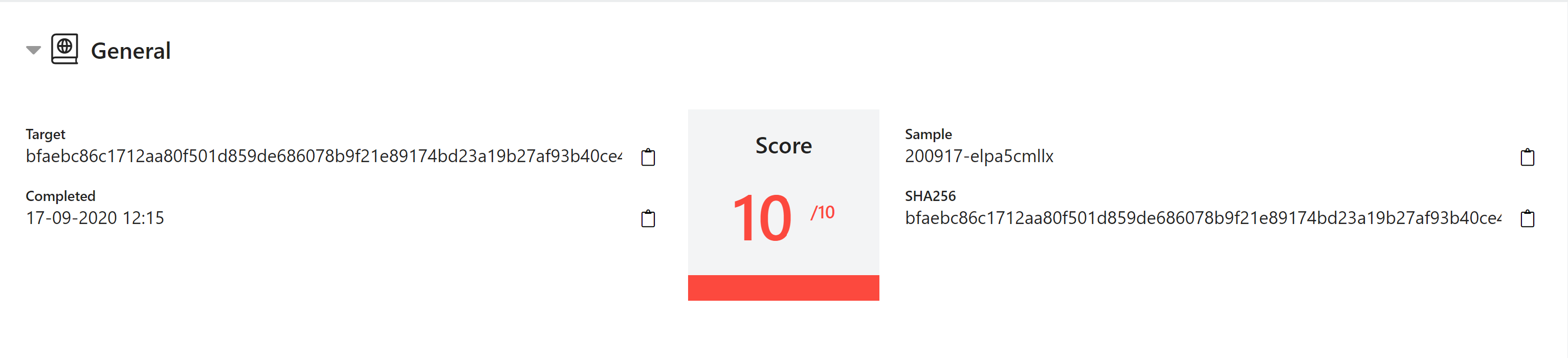
Malware Config Tab
This section shows any extracted configurations, C2 addresses or ransom notes from all of the analysis tasks.
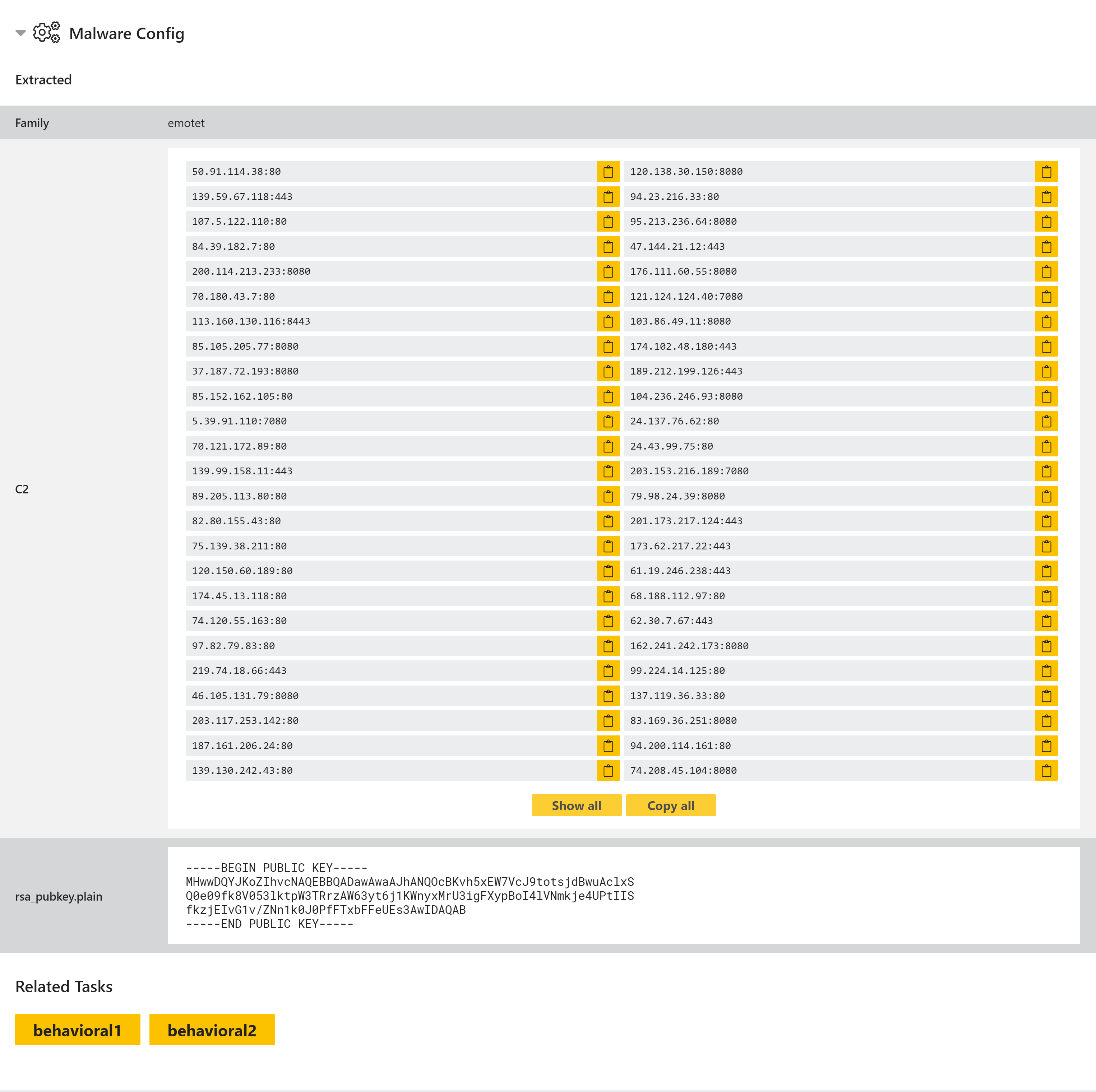
Example Emotet Config
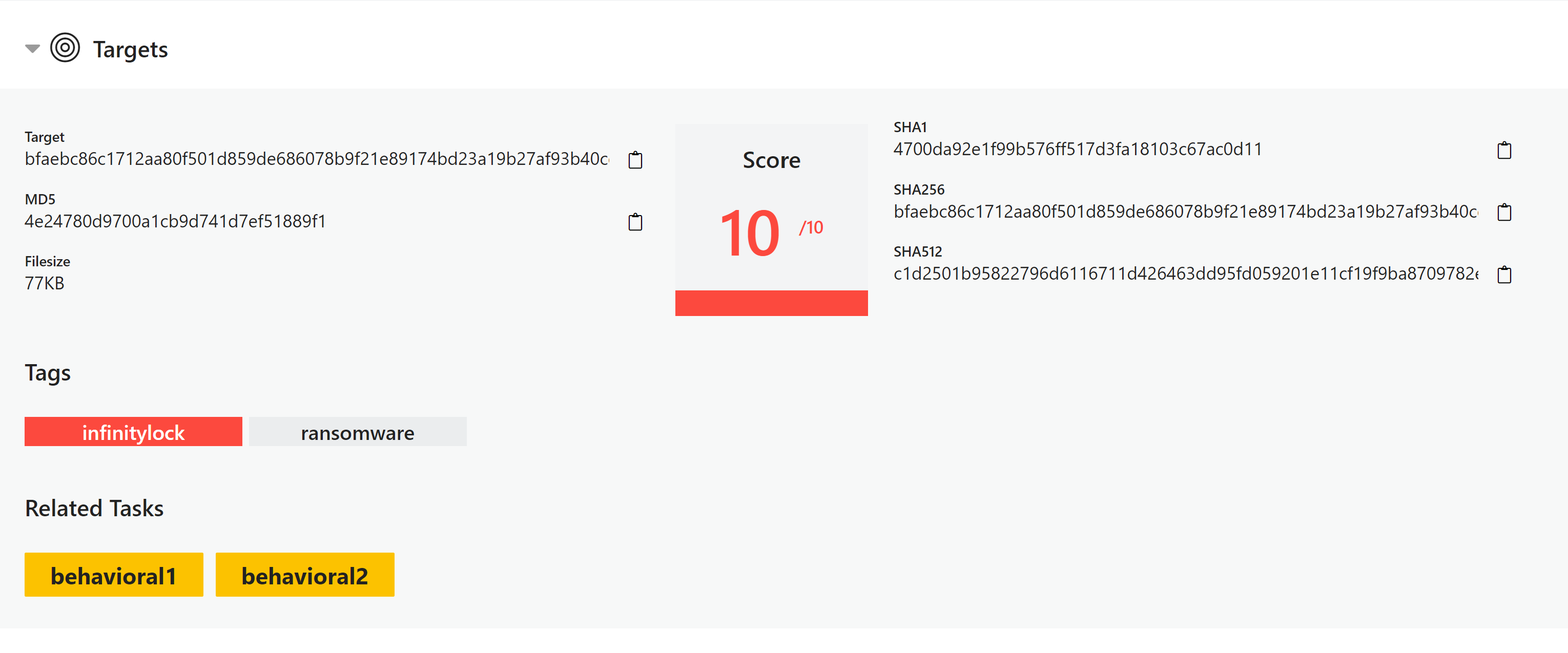
Targets Tab
Here you can find a summary of all files run for analysis and a summary of the findings for each such as hashes, score and tags. For an analysis with multiple files, such as an archive, this will have multiple entries and references the relevant tasks for each one.
Ransomware Updates
As usual there is no shortage of new ransomware samples to look at currently. We have added classifications for a few more families that have received attention recently.
InfinityLock
InfinityLock, also known as InfinityCrypt, has been around for some years but is still seeing active use in the wild. A sample was reported on Twitter at the end of August which caught our attention, and we have now added support based on the samples we were able to gather.
More information on the family can be found on the ID Ransomware blog.
Analysis:
Chimera
Chimera is another family which has been around for some time, with MalwareBytes first reporting on it back in December 2015. It is still around in the wild and saw a new version appear in August this year. We have added support based on a couple of recent samples on Triage.
Analyses:
Ouroboros
This family has been active for years too, constantly releasing new versions and with other families branching off from it over time. The main Ouroboros family, also known as ZeroPadypt, has gone through multiple iterations over the years. At the start of September we noticed a variant of the family which was evading our rules and have now extended coverage.
Analyses: New sample seen in Sept. 2020:
Older Family Samples:
SunCrypt
SunCrypt has been around for a bit under a year, thought to have first begun operations in October 2019 according to BleepingComputer. The operators have also claimed to be associated with the Maze ransomware group, although this is something the Maze developers have since denied. Regardless it does share some characteristics with the Maze group, including reusing C2 addresses previously associated with Maze campaigns and in the way it steals data to use as leverage in the ransom demands.
It appears to have stepped up operations in the second half to 2020, and has reportedly had successful infections at several organisations such as University Hospital New Jersey and a North Carolina school district.
Not that to get the analysis below to run correctly, it required a longer timeout than usual. This was run with 5 minutes instead of our default 2.5.
Analyses:
TrickBot Configuration Extractor Update
TrickBot saw another minor tweak this week, with a change to its packer opcodes. We have extended our detection and configuration extraction to handle the update.
Analysis:
Emotet Update
Emotet also received a minor update earlier in the week. A change in the opcode pattern used to parse the malware’s list of C2 IP addresses caused it to slip through our yara rules. This has now been fixed.
Analysis:
RevengeRAT
RevengeRAT is an extremely popular remote access tool used in the wild, which has been around since 2016. The source code was leaked some time ago, so there are many different versions and variants floating around. We recently observed a few samples which were not triggering signatures due to inactive C2, so we have improved static detection for this group.
Analyses:
