Welcome back to our Triage Thursday update blog series! It’s been another busy week here and we have a bunch of new detection updates to go over today, including a couple of quite familiar faces:
- Updated configuration extractor for AsyncRAT
- Updated key extraction for Emotet Epoch 4/5 samples
- Added configuration extractor for some EternityProject components
- Added support for EnemyBot family on Linux
- Updated detections for some Vidar samples
As always if you find any problems with the Triage platform or the detections in it, please do let us know. Community input is a vital part of tracking and keeping up to date with the rapidly evolving malware landscape and is extremely helpful in making these updates possible. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account!
AsyncRAT
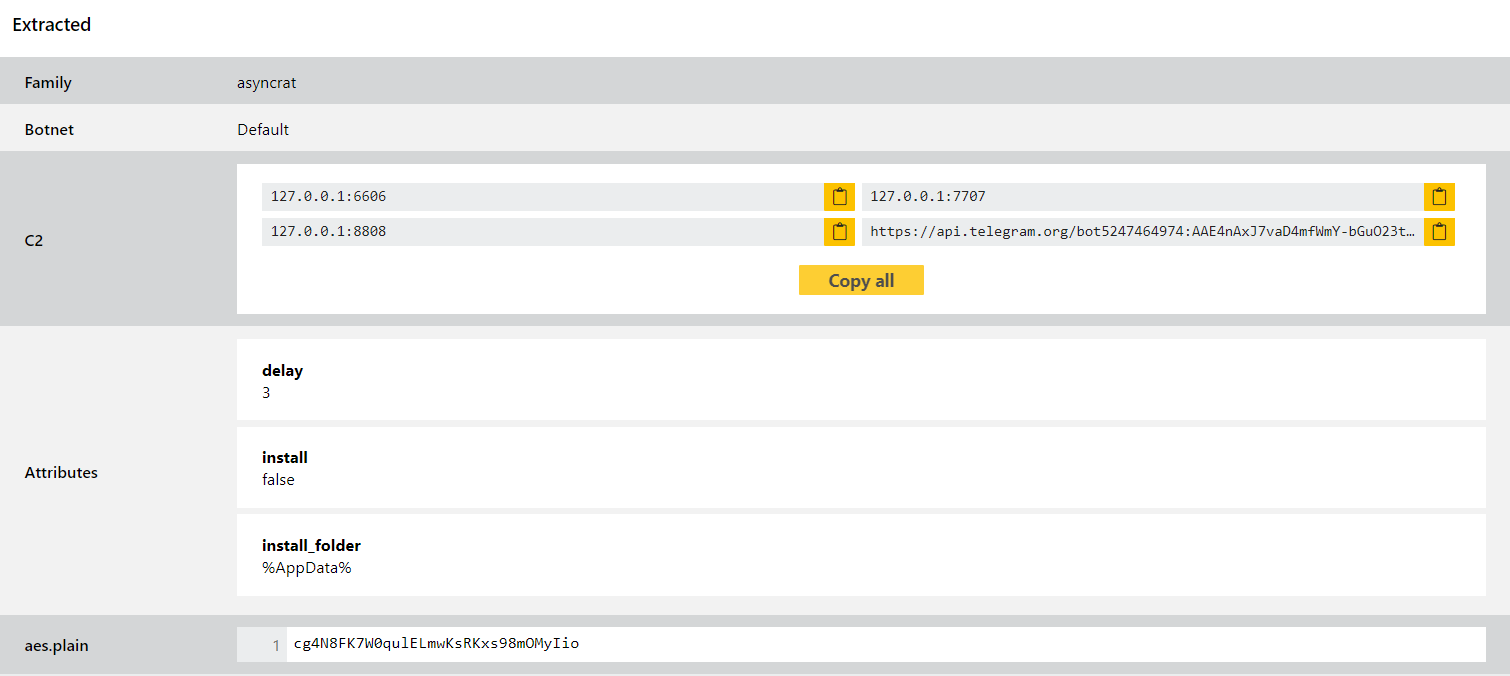
AsyncRAT is an open-source RAT available on Github. It claims to be for legitimate remote administration purposes only, but is of course commonly used by criminals looking for an easy to use, adaptable RAT. It is written using C# and has a wide variety of functionality including screen recording, file upload/download via SFTP, local password recovery, and techniques to disable anti-virus software (for a full list see the readme on Github).
We recently started seeing samples which are using Telegram for their C2 communications, so this update improves our configuration extractor for be able to handle these variants. We’ve also done a bit of refactoring of the extractor overall to make it more robust - AsyncRAT is created by the same developer as another trojan called StormKitty, and in many areas they share quite a bit of code. We’ve limited this as much as we can currently but in some cases you may see an overlap in the detections on Triage.
Analyses:
Emotet
The Epoch 5 botnet has been active since the start of 2022, following on from Epoch 4 which was active towards the end of 2021. Both have remained active alongside each other, with a few changes being made to the samples for both since they initially appeared.
We were recently made aware of a couple of issues with our configuration extractor not properly dumping the keys - some samples were missing the key altogether, and in other cases the output was being duplicated unintentionally.
We have now fixed these issues so you should find performance for the Epoch 4 and 5 samples has improved. If you come across any more irregularities please feel free to let us know.
Analyses:
EternityProject
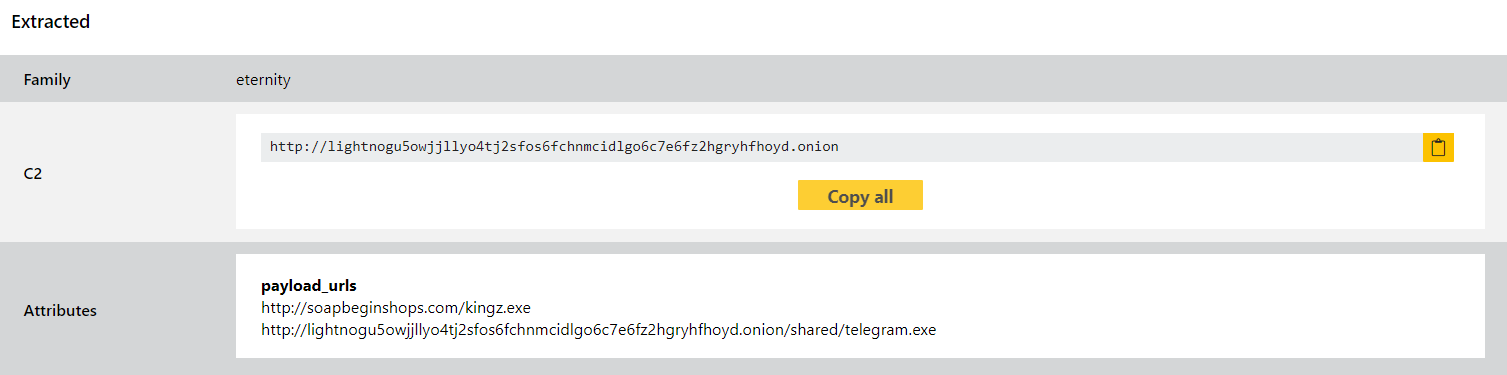
In our blogpost last week we introduced detections for the Eternity Project, a new malware-as-a-service with a whole range of different components which can be mixed and matched to suit a particular scenario or campaign.
According to the report by BleepingComputer among the modules currently on offer are an info-stealer; a coin miner; a clipper; a fully functional ransomware; a worm spreader; and soon a bot for carrying out DDoS attacks. The modules are sold separately, with customers using a Telegram bot to automatically build their binaries based on the features they have selected. Based on the results observed from the sandbox it seems that most samples use .onion URLs as part of their C2 communications.
We added basic detections last week for each of the components we were able to get hold of, and today we are widening that to include a full configuration extractor for a few of them. Examples of the worm, clipper and stealer components will now have relevant information dumped out directly, as well as the existing static signatures.
Analyses:
EnemyBot
EnemyBot is a fairly new DDoS botnet targeting Linux systems, reported on in early April by Fortinet. It is attributed to a threat group called Keksec who specialise in attacks around cryptomining and DDoS.
It mainly goes after routers, sometimes exploiting specific vulnerabilities to spread - it can support a wide range of architectures for both IoT and desktop devices however including ARM, MIPS, BSD, and x86/x64. It can also spread via misconfigured Android devices with an exposed Android Debug Bridge port, or just by trying common default passwords against login services. In terms of origins it’s a bit of chimera with a significant portion of its codebase being taken from Gafgyt, but with clear signs of some sections being borrowed from Mirai.
We have now added detections for the family and will update if and when needed. We’ve been looking a bit more at Linux lately to fill in some gaps in our detections, so if you have interesting samples there you’d like us to add detections for then let us know!
Analyses:
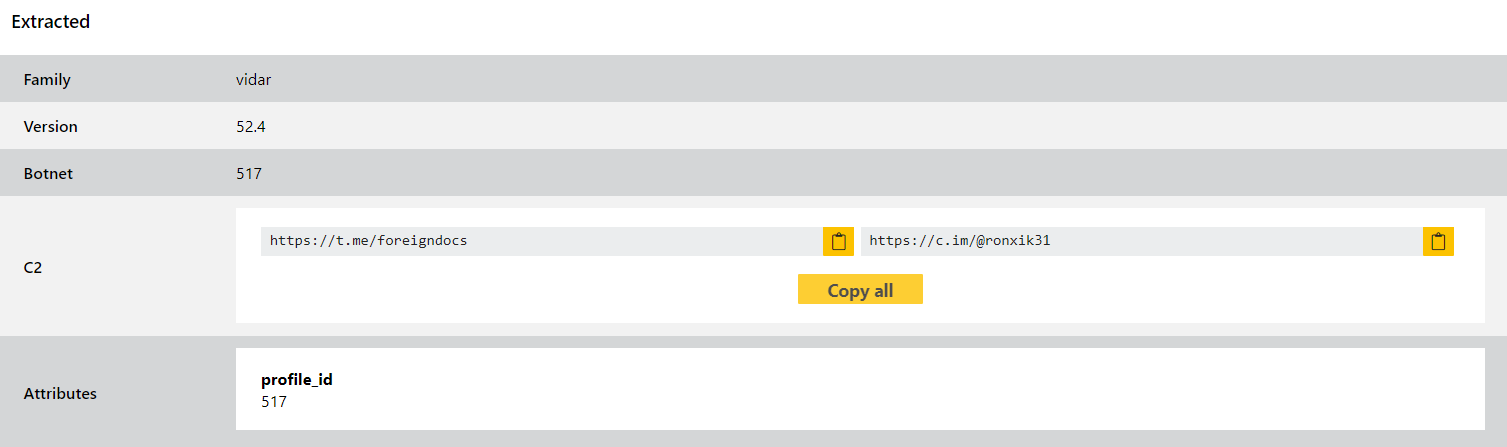
Vidar
Vidar is back in the blog again this week with some updates to handle a few samples we came across recently. It’s a pretty regular visitor here so we won’t go into details on the background again - if you’re not familiar with the family you can check out our blogpost from July 2021 where we initially added the configuration extractor.
This week’s changes aren’t for a new variant - we just found a few samples which were not covered by our existing rules so wanted to make sure to cover them. As always if we spot any others in future we’ll make sure to make any other required changes - for big, sprawling families like Vidar accounting for every variation can be quite a challenge.
Analyses:
