Another week, another Triage Thursday blogpost! We’ve got our usual collection of detection and configuration extractor updates to go over, including the return of Raccoon and a couple of families new to Triage:
- Updated detections for Raccoon to support V2, and extended the configuration extractor
- Added signatures and a configuration extractor for PrivateLoader
- Added detections for IceXLoader
- Added signatures for the Symbiote Linux backdoor
- Updated rules for a variant of the SectopRAT family
As always if you find any problems with the Triage platform or the detections in it, please do let us know. Community input is a vital part of tracking and keeping up to date with the rapidly evolving malware landscape and is extremely helpful in making these updates possible. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account!
Raccoon V2
A couple of weeks back we included a family called RecordBreaker in our blogpost. Since then more analysis of it has become available and it seems that it was initially mis-identified, in reality being a new version of Raccoon stealer.
Raccoon was a well established family up until March 2022, when operations were shut down after a key developer was killed in the Russian invasion of Ukraine. It remained inactive until early June when the operators resumed posting on the underground forums and began to push a version 2 of the malware.
The new version appears to have involved rewriting significant sections of the malware but currently the overall flow and functionality is mostly unchanged. According to a post by S2W it claims some improvements like an expanded list of targets from which to harvest data, cross-compatibility with 32 and 64 bit systems, string encryption, and a fully automated payload builder.
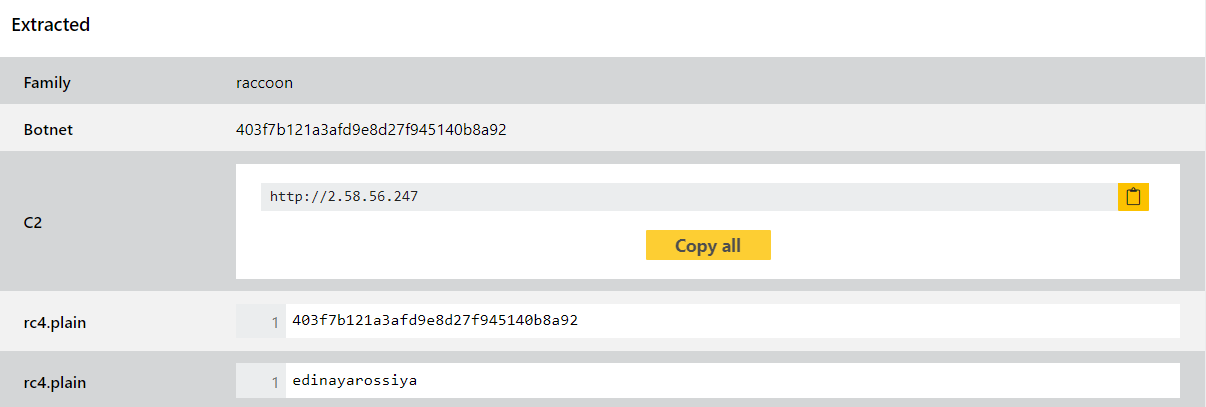
We have refactored our earlier RecordBreaker signatures and made some more improvements based on further analysis of these files. Since it seems like this is a new start for the project we expect to see further updates and variants in the future so will of course be keeping an eye on it and making adjustments as needed.
Analyses:
PrivateLoader
PrivateLoader has been around in some form since early 2021 but has largely slipped under the radar until earlier this year. It is not specific to one particular family or threat group, being offered online under a pay-per-install (PPI) model which has become increasingly common for loaders like this. It has been seen distributing ransomware, stealers, and other payloads - a couple of weeks back we reported on NetDooka which is a module framework often seen being delivered by PrivateLoader.
In order to hinder some common detection techniques the malware relies heavily on encrypting both the strings and API calls required - these are decrypted at runtime and in the case of the latter resolved dynamically. According to ZScaler’s report it also uses a lot of junk code to confuse reverse engineering attempts.
The malware uses a 2 stage C2 setup, where hardcoded URLs are used as a deaddrop address from which the malware can fetch the location of the actual C2 server. In turn the C2 server will then generally provide additional URLs which point to the final payload to be delivered. Interestingly PrivateLoader also includes some initial discovery functionality querying the presence of various file paths, registry keys and browser extensions commonly looked at by stealers - saved browser logins, cryptocurrency wallets, banking cookies etc. However it does not exfiltrate anything, it simply checks if they are present. ZScaler suggests this is to inform the choice of payload to be deployed based on the content identified.
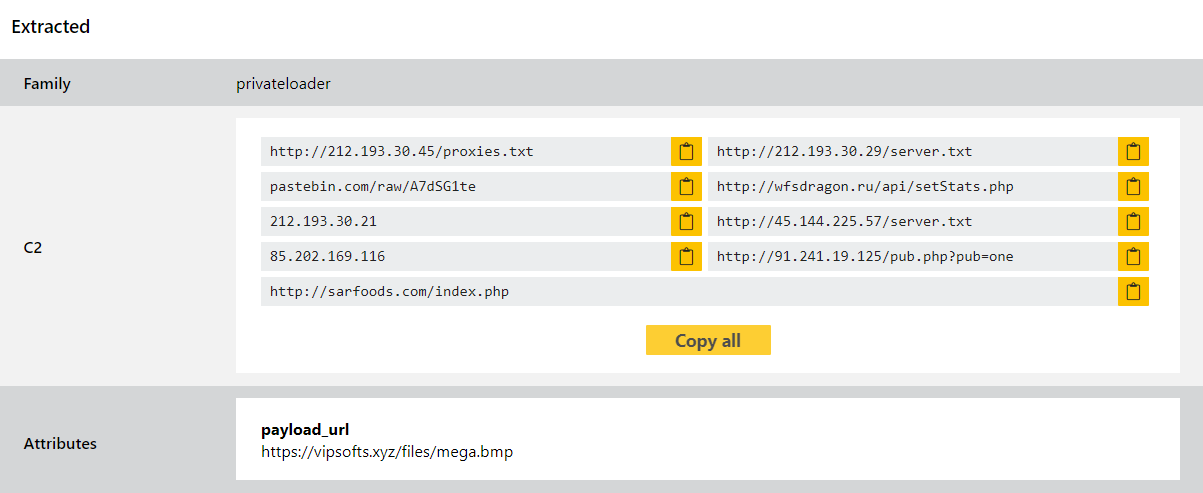
We have reviewed available samples and implemented detections and a configuration extractor to dump out the hardcoded URLs - these are the original ‘deaddrop’ URLs, plus the secondary backup that’s hardcoded in case the dynamic attempts fail.
Analyses:
IceXLoader
IceXLoader is another new loader family (no prizes for guessing that one), this one having popped up within the last few weeks. It is not related to the older XLoader family (which is itself an evolution of Formbook).
The exact age of the family is not currently clear, as the first copy to be reported widely appears to identify itself as version 3. Fortinet report that they have come across copies of the original version 1 by exploring the current C2 servers but little evidence has been reported of this appearing in the wild. Version 3 is written in the Nim programming language, an unusual choice but one that has increasingly been gaining popularity thanks to the fact that many detection solutions do not handle it well. Earlier versions appear to have been written in AutoIT but coverage for malware using this has improved a lot over recent years so that likely prompted the switch. The current version 3 payload seems to be something of a work in progress port as the previous version 1 payloads reportedly included more features, and some functionality such as mutex creation is clearly unfinished.
Once installed on a victim the malware establishes persistence via abusing both the startup folder and a Run registry key. It then carries out live patching of the amsi.dll file in memory which allows it to bypass the Windows Antimalware Scan Interface used by various security products to check content, signficantly reducing its detectability. It also uses Powershell to directly disable Windows Defender’s realtime scanning and to add directory exceptions which protect the malware’s install location.
A full writeup can be found by Fortinet here. We have implemented general detections for the family, and we expect to visit it again in future as the family develops beyond the current version 3.
Analyses:
Symbiote
Symbiote is a new Linux backdoor first reported in a joint effort by BlackBerry and Intezer - their report on it can be found here. It is an interesting threat because it is deployed not as a standalone executable but as a shared object library - this is loaded into all running processes and this infects the machine. However it cannot do anything on its own without being loaded by an existing process.
Once a machine is infected the malware will act like a rootkit, using its access to hide its own files, processes and network activity. It can then stealthily remain on the machine providing backdoor access to the attacker as needed, who can login using any account on the compromised system.
Another unusual feature is its use of Berkeley Packet Filter (BPF) hooking to communicate discretely with its C2 infrastructure. It is not the first malware to do so - an Equation Group payload has included this before, and at the start of the month we added detection for a backdoor which depends heavily on this - but it is still quite a rare sight. It’s also very effective, so we’ll likely be seeing more of this in future.
Analyses:
SectopRAT
SectopRAT dates back to 2019 when it was first discovered by MalwareHunterTeam. It is a remote access trojan written in .NET with a couple of unusual features that set it apart from similar threats.
Chief of these is its ability to create a 2nd desktop environment which is hidden from users. It can then launch and control processes here, especially web browsers that it can then use for other purposes. It can also directly stream the user’s desktop to the C2 server to facilitate spying and data collection.
The initial version was thought to be a testing build, as it did not include any particularly malicious behaviour besides basic profiling of an infected system. However in early 2020 a sample was observed which appeared to be a weaponised version of the family and that led us to implement some initial detections for the family. We have recently noticed a new variant in the wild which makes some attempt to evade detection by encrypting strings and function names so this week we have updated our rules to properly cover these samples - some examples are below.
Analyses:
