Another week has passed (somehow), and it’s time for some more updates! We’ve got some updates to a couple of familiar families like Emotet, but apart from that we have quite a few new additions to introduce across Windows and Linux (new to Triage at least). Let’s get into it!
- Updated key extraction for current Emotet samples (big thanks to everyone who reported samples to us)
- Added configuration extractor for Panda Stealer
- Added detections and a configuration extractor for NetDooka RAT
- Added detections for RecordBreaker family
- Added detections for SVCReady loader
- Added detections for WinDealer stealer
- Updated detections for Kaiten/Tsunami Linux botnet
- Added detection for AbstractEmu Android family
As always if you find any problems with the Triage platform or the detections in it, please do let us know. Community input is a vital part of tracking and keeping up to date with the rapidly evolving malware landscape and is extremely helpful in making these updates possible. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account!
Panda Stealer
Panda Stealer has been around for about a year now but for whatever reason has not really come onto our radar until recently. It was reported on in May 2021 by TrendMicro who had initially picked up on it during April of that year - it reportedly involved fairly typical email spam campaigns primarily going after targets in the US, Australia, Japan and Germany. It appears to be a fork of the DCStealer/Collector Stealer family, a similar trojan of Russian origin.
Samples tend to make use of macros and Powershell to carry out an initial fileless infection, fetching the end Panda payload from web-based sources - early examples reported by TrendMicro in their report made use of the paste.ee service for this purpose.
It mainly goes after cryptocurrency and related data stored locally - Dash, Bytecoin, Litecoin and Ethereum wallets have been reported as targets among others. However it also has the common stealer functionality of dumping out passwords and stored data from browsers, and stealing credentials from applications like Telegram, Discord, Steam or NordVPN.
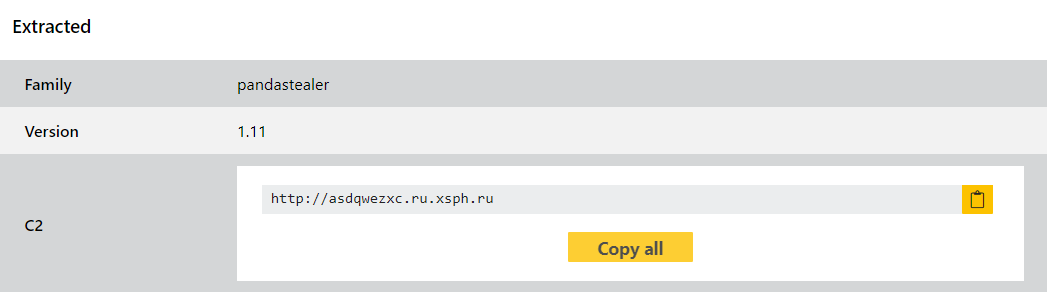
We had added some early behavioural signatures around the time the family first appeared but these were based on a fairly limited sample set. This week we have revisited it with more information available, and have built out a full configuration extractor as well as improving our other detections. This can dump out the C2 information and version number for quick reference.
Analyses:
NetDooka Loader and RAT
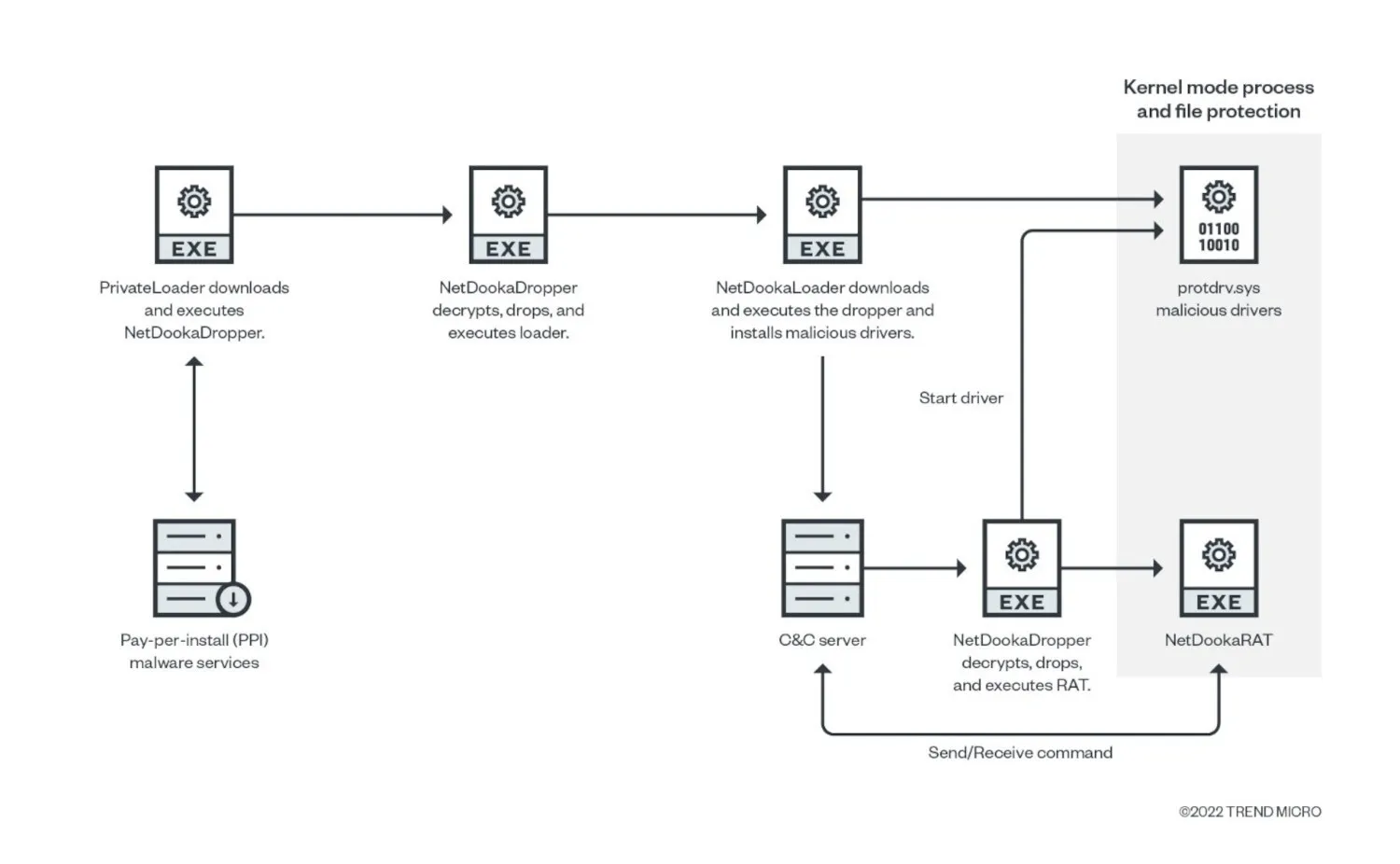
NetDooka is a new malware framework reported on in May 2022, again by TrendMicro. The family seems to work on a pay-per-install model where the developers pay others to get them into systems using existing channels, and is a full framework with multiple parts besides the RAT itself - for example a loader, dropper and a kernel-mode protection driver have also been observed.
Its initial access so far has made use of the existing PrivateLoader family which has been used with a number of other malware over time such as SmokeLoader and Redline, and has well established infection methods. We are still working on analysis and detection for PrivateLoader but we hope to bring those out shortly too - watch this space!
Going back to NetDooka though, its infections go through multiple stages even after PrivateLoader’s role has ended. The first component to be executed is the NetDooka dropper which decrypts, drops and executes the next loader phase. This installs the relevant protection drivers and fetches the next stage from the C2 server, which then leads to the final payload - this process is shown in TrendMicro’s diagram below (taken from their blogpost here).
The RAT itself is quite capable, being able to respond to commands issued by the remote C2 server effectively giving an attacker full control over the infected machine. It does not appear to specifically go after things like browser data in this case, being generally more interested in using the system as part of a botnet for actions like DDoS attacks. Of course it does include some stealer aspects though - it can extract files from a victim, record the microphone/webcam, and log keystrokes among other things.
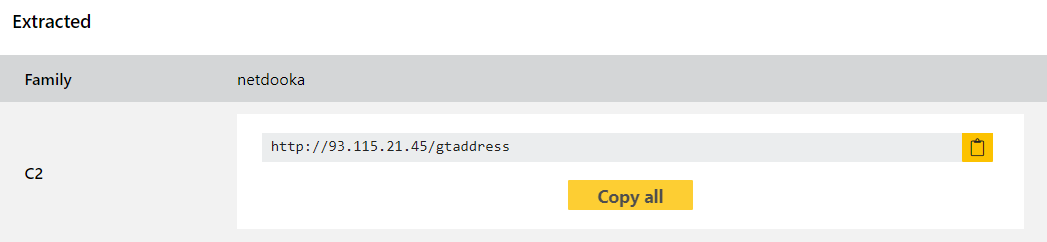
We have analysed available samples of the loader and RAT components and implemented both standard detections and a configuration extractor. Examples of each are provided below for reference.
Analyses:
| Loader | RAT |
|---|---|
| 220610-s2xtrshbb2 | 220610-qvz97sbehp |
| 220610-s2x5jacfgq | 220610-qvxjbabehm |
| 220610-s2wxgahba9 | 220610-qvx5vabehn |
| 220610-s2wlpshba8 | 220610-qvw8jsgac3 |
| 220610-s2wayahba7 | 220610-qv4mmabfaj |
RecordBreaker Stealer
RecordBreaker is another new family which reportedly popped up around mid-May 2022.
Besides the standard stealer functionality it also supports downloading and executing additional files on the infected machine, meaning that it can be a stepping stone to additional infections besides its own operations.
So far it seems to have mainly spreading via malicious cracks and keygens for legitimate software which are distributed via shareware sites.
There is limited information available about it online at this time but we have examined samples shared by @_FirehaK above and others, and implemented initial detections and a configuration extractor - this just dumps the C2 URL/domain for quick access.
Analyses:
SVCReady Loader
SVCReady is another new addition to the threat landscape, having been first seen in the wild during April 2022. It was first reported on fully earlier this month by HP’s threat research team, who published a detailed blogpost which you can read here.
In general the family is a pretty standard loader, albeit one of the more professional examples. However it sets itself apart with an unusual initial infection technique based around Office macros - instead of leveraging VBA to launch into Powershell or some other script handler for the next stage, SVCReady uses macros to run shellcode that is embedded directly into the initial Office document. This approach is not unique by any means but is fairly unusual in the wild.
Once a system has been infected the malware will seek to gather useful information about it, establish persistence, and take steps to check for the presence of analysis tools or virtualisation in general. It will exfiltrate all collected information to its C2 server, and then beacon out at regular intervals to monitor for any new instructions or payloads to install. HP report that they have so far mainly seen RedLine stealer as the final payload.
We have taken a look at some available samples and implemented static detection for the samples. As always we’ll keep an eye on it going forwards and make any necessary alterations or improvements as we find more examples.
Analyses:
WinDealer Stealer
WinDealer is a stealer family aimed at Windows system which is associated with the LuoYu threat actor. This group has been active since around 2008 but without the high profile of some other groups, and are believed to be Chinese in origin. They seem to mainly target users within the SE Asia region covering China, Hong Kong, Japan, Korea and Taiwan with implants for multiple operating systems including Android phones.
TeamT5 published research into the threat group in January 2021 and suggested that, based on the type of malware being used and the targets seen, the LuoYu group is likely attempting to track and collect information on dissidents against the Chinese government.
According to a report by Kaspersky earlier this month, WinDealer itself has a range of capabilities intended to give control of an infected device and gather useful, sensitive information:
- File and file system manipulation: reading, writing and deleting files, listing directories, obtaining disk information
- Information gathering: collecting hardware details, network configuration and/or keyboard layout, listing running processes, installed applications and configuration files of popular messaging applications (Skype, QQ, WeChat and Wangwang)
- Download and upload of arbitrary files
- Arbitrary command execution
- System-wide search across text files and Microsoft Word documents
- Screenshot capture
- Network discovery via ping scan
- Backdoor maintenance: set up or remove persistence (via the registry’s RUN key), configuration updates
We have reviewed several recent samples seen on Triage and implemented some detections for them - examples are below.
Analyses:
Tsunami
Tsunami is a Linux botnet that has been around in some form or another for a few years now. We implemented detections for some earlier samples under the name Kaiten but recently it seems to be more commonly referred to under the Tsunami moniker - however to avoid breaking search functionality for old samples we have decided to stick with the Kaiten name for now, so if you’re looking for this family in Triage reports that will be the one to use.
The family itself is very similar to other IoT/Linux botnets like Mirai (in fact in some cases the payloads are so similar we have some overlap in detections that we’ve been unable to separate so far). It uses IRC for C2 communications and can directly receive commands to execute - this basically makes it a full backdoor capable of running shell commands, downloading additional files or performing external actions like DDoS attacks.
As with many of these botnets detection for all the different variants and samples is quite a tricky task. We’ve gone over all the samples we’ve managed to get our hands on and have built out appropriate detections, but some future updates may well be needed if we come across other outliers.
Analyses:
AbstractEmu
AbstractEmu popped up in the second half of 2021, gaining attention in October when Lookout Threat Labs identified it in 19 apps available on the Google Play and other third party appstores. All of the apps it was bundled with also included legitimate functionality as stated in order to make the downloads look more legitimate.
The family gets its name based on its focus on anti-emulation checks to try and get around analysis tools. It is somewhat unusual in the modern mobile malware landscape as it is designed to provide rooting functionality for devices, something which has become quite rare over the last 5 years according to the report by Lookout. As the Android ecosystem has matured exploits like this have become less useful, replaced with more targeted attacks against legitimate apps like mobile banking. However that is not to say that AbstractEmu has much of a different end goal - it seems that many of the permissions it grants itself after gaining root access are most likely aimed at gathering financial information.
The app can receive commands over its C2 infrastructure with the functions being hardcoded into the malware. At the start of the infection - assuming the emulation checks passed - it will gather up a lot of device information and send this back to its C2, and these will then likely inform the next steps to be taken.
We have now added static detection for the family to Triage based on the samples made available by Lookout.
Analyses:
