We’re back today with another Triage Thursday update blogpost, this time covering updates for the last couple of weeks. Here is the full list of changes, with links to background writeups for the main additions:
Deployed November 24th:
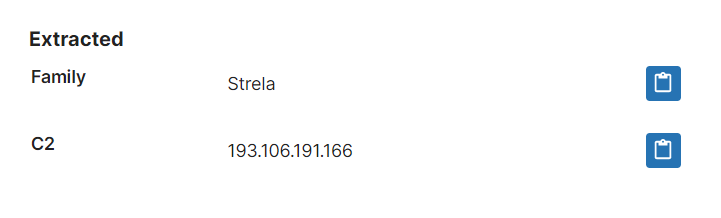
- New signatures and configuration extractor for Strela stealer
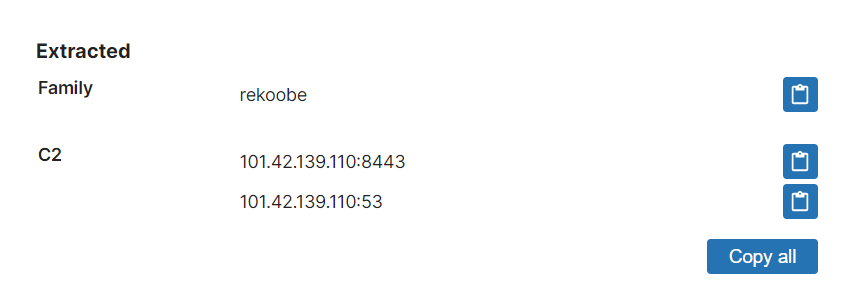
- Improved signatures and configuration extractor for Rekoobe Linux trojan
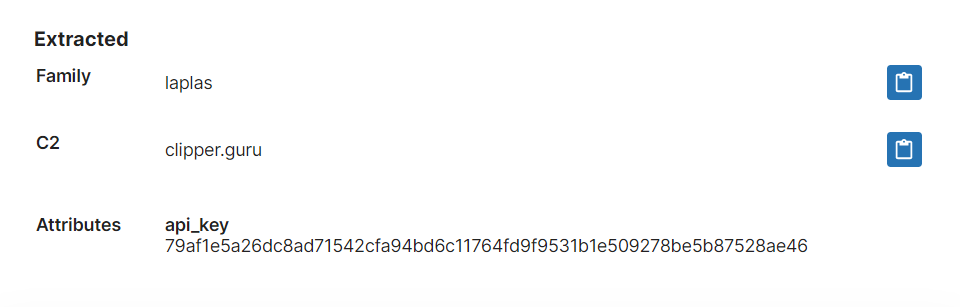
- Added support for Laplas x86 variant
- Small fix for Gozi configuration extraction
- Small fix for njRAT configuration extraction to properly display multiple C2s as a list
- Updated Colibri configuration extractor handle embedded RC4 key
- Update for AgentTesla to extract Discord details when used as exfiltration channel (Note: External link to Twitter)
- Update for Phorphiex configuration extractor for recent samples
- Updated Redline stealer fallback rules to improve coverage
Deployed November 17th:
- New signatures for Bluefox stealer
- New signatures for Tianyspy Android malware
- New signatures for Zeon ransomware
- New signatures for Royal ransomware
- New signatures for Venus ransomware
- New signatures and configuration extractor for Laplas clipper
- Updates for Vidar rules to detect recent samples
- Updates for IcedID rules to detect recent samples
- Updates for Amadey extractor to handle new string decryption algorithm
- Updates for Joker android malware to avoid false-positives and improve coverage
As always you can contact us any time directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Strela Stealer
Earlier this month researchers at DCSO in Germany published a report on a previously undocumented stealer malware which they have named ‘Strela’ based on the label of the main export function.
It seems to have a narrower selection of targets than most modern infostealers, focusing entirely on data stored by the Outlook and Thunderbird email clients (text below is taken from the DCSO blogpost):
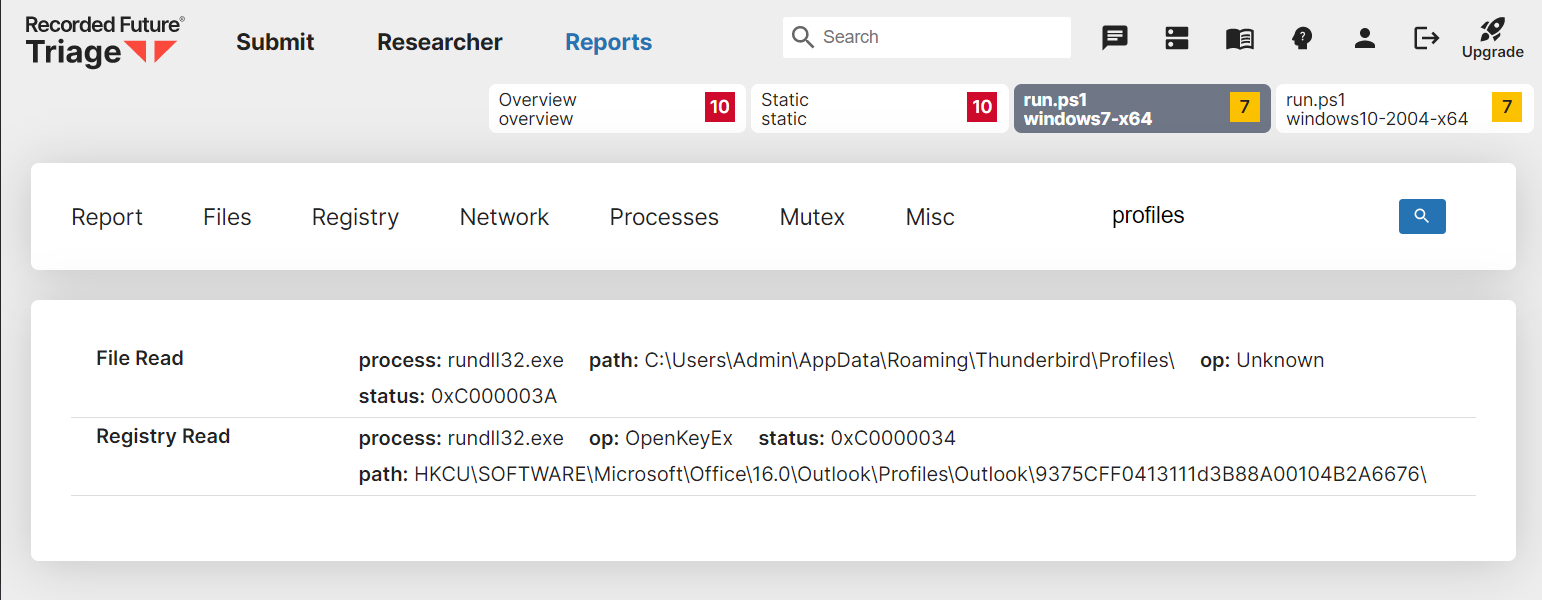
For Thunderbird, StrelaStealer searches for
logins.jsonandkey4.dbin the ``%APPDATA%\Thunderbird\Profiles` directory and sends the file contents to its C2.For Outlook, StrelaStealer enumerates the registry key
HKCU\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\in order to find the valuesIMAP User,IMAP ServerandIMAP Password. StrelaStealer then decrypts the IMAP Password usingCryptUnprotectDatabefore sending the triple to its C2.
The samples themselves are not obfuscated, but do use simple XOR encryption for strings within them based on a hardcoded key.
Unfortunately due to the DLLs using a specific named export function Triage will not automatically manage to run samples of this family. However we have added static detection and configuration extraction (to dump the C2 domain) to get around this and ensure appropriate scores are assigned.
To make the files run properly it would be necessary to use a custom script alongside the DLL, with the correct launch parameters defined. An example of this can be seen in this analysis where we use a PowerShell script to call the s entry function. In the events we can then see the attempts to access Thunderbird and Outlook data. For more information on how to use scripts to manipulate launch conditions like this check out our old blogpost on Submitting ZIP files.
Analyses:
- 221124-s79eragg91 (with script to launch
sfunction) - 221124-s2dqwsgd7y
- 221124-s2eyysgd71
- 221124-s2g4bagd8t
- 221124-s2jbdagd8w
Rekoobe Linux Trojan
Rekoobe is an older Linux trojan/backdoor which has been around since at least 2015. It is generally associated with China’s APT31 threat group (also known as RedBravo and Zirconium) who have used it as part of their attack chains for a number of different campaigns. Most recently it has been seen in use alongside a new Linux rootkit called Syslogk.
The malware is a fairly bare-bones trojan which provide a C2 channel and little else. Early versions had an embedded configuration file but from around 2020 it seems that this has been replaced by simply hardcoding required values into the binaries directly.
The malware is thought to be a fork of the older Tiny SHell trojan, which has been available open-source since around 2012. Improvements since the initial version mostly seem to relate to helping minimise detection, for example by removing a lot of the strings which were clear markers used for detection and by adding a function to rewrite argv[0] in an attempt to change the process name (reportedly used as an indicator by some forensics tools).
We have added standard detections and an extractor to dump out the C2 IP and port numbers in use.
Analyses:
Laplas Clipper
Laplas was reported by Cyble at the start of November as a new stealer being distributed by the Smokeloader family. It is specifically targeted at theft of cryptocurrency and doesn’t include the usual browser and email features, but does have an interested secondary function of intercepting Steam Trade URLs.
The family is a clipper rather than a standard infostealer, meaning that it monitors the clipboard for copied text and if it detects cryptocurrency wallet addresses or Steam Trade URLs it will swap them out for predefined data set by the attacker. Thus if a user was copy/pasting the string to make a transaction the transfer will instead be made to the attacker and not the user’s intended destination.
Initial samples observed were based on .NET but according to the Tweet thread above it seems that there is also a Golang build which has been seen in some cases. The malware can be bought on a subscription model with options as low as $29 for a single day of use.
Last week we added initial detections and configuration extraction for a couple of versions of the family, and then revisited it again this week to extend those rules to also cover x86 builds that we have seen since then.
Analyses:
BlueFox Stealer
BlueFox first appeared on forums in December 2021 but reportedly did not seem to gain a lot of traction with users at first. However according to our friends over at Sekoia in September this year version 2 of the family was released which seems to have attracted a lot more attention. The developer has published a few minor updates since then indicating that they are currently quite active and we should expect to see additional changes in future.
The family is specifically aimed at traffer teams (centralised groups who monetise access via botnets/initial access brokers) with features intended to help with tracking team members activity in much the same way a sales team would want to track leads generated by each individual.
According to Sekoia’s analysis the family includes the following main features:
- Stealing passwords, cookies and autocomplete data from common browsers (Chromium and Firefox based browsers: Chrome, Edge, Opera, Mozilla, etc.)
- Targeting of almost all desktop cryptocurrency wallets and cryptocurrency wallets (MetaMask, TronLink, BinanceChain, Yoroi, Coinbase, Jaxx, Ethereum, Electrum, Exodus, etc.)
- Stealing data stored locally by password managers (Bitwarden, 1Password)
- File download and execution
- Exfiltration of files from the infected machine
- Screenshot capture
- System fingerprinting
Analyses:
TianySpy Mobile Stealer
TianySpy was spotted in September 2021 being used in smishing campaigns, seemingly trying to steal credentials for customers of Japanese telecommunications services. Interestingly the campaign was seen causing malware infections on both iPhones and Android devices which makes it an unusual family, as most mobile malware just sticks to the more vulnerable Android ecosystem. TianySpy was the family being deployed to Apple devices (though it does also have an Android version), with KeepSpy generally being used to Android victims.
According to TrendMicro the family has the ability to read WiFi settings; injecting into specific webpages to falsify and weaponise legitimate websites for telecommunications providers; steal web data via malicious JavaScript; exfiltrate stolen data; and load malicious websites directly.
We have reviewed a number of Android samples and implemented initial detection for the family.
Analyses:
