Welcome back to our Triage Thursday blog series, where we go over any and all updates for our Triage sandbox from the last week.
We’ve got a bit of a mix of things for you today, with a couple of exciting announcements to go along with our usual news about configuration extractors and detection updates:
- Added support for Windows 11 VMs
- New integration with TheHive Cortex
- Added detection for new Chinese botnet
- New configuration extractor for CyberGate RAT
- Added family detection for recent ransomware families:
- Added family detection for VanillaRAT
Read on below for all the juicy details!
In other news we are still looking for a Go developer to join the Hatching team. If you’d like to be involved in the next steps of Triage’s journey - or know someone who might be - you can find the full job listing here. Feel free to reach out with any questions.
If you have any feedback on Triage or particular samples please do get in touch! You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Windows 11 Support
As most of you are likely aware, back in June Microsoft announced Windows 11 as the next entry in the Windows lineup. Although it is not expected to go to full release until the end of the year, we have been hard at work with the Insider builds getting initial support in place to ensure we can hit the ground running when release arrives.
We’re pleased to say that we’ve been able to make good progress with this, and as such today have released the first version of our Windows 11 support for you to play around with!

Our default platform for Windows analyses will continue to be Windows 10 for the foreseeable future, but you can now select Windows 11 from the submission options or using Profiles. Naturally as this is not the final commercial version the precise details/appearance may change before the OS releases later in the year, but we will continue to keep an eye on updates and will be ready with support for whenever it becomes publicly available.
In the meantime feel free to experiment with it and see what you think!
TheHive Cortex Integration
Also this week we have added a new integration to our list of supported products - you can now ingest data directly into TheHive from Triage!
If you haven’t come across it before, TheHive is an open source security incident response platform designed to help with swiftly investigating and acting on security incidents. It works closely with MISP to make recording and tracking IoCs as simple as possible. The project also includes Cortex, an active response engine which has prebuilt automated analysis pipelines for many different types of incident or indicator.
The new integration plugs Triage directly into the Cortex engine, enabling users to execute files in the sandbox, fetch the results, and begin initial analysis of them without ever leaving TheHive’s interface.
You can find the Triage plugin built in to the latest release of TheHive’s Cortex engine, and the source code is available on Github here.
Massive thanks are due to Mikael Keri for building out this integration for us.
Check out details of our existing integrations with Splunk Phantom and PaloAlto’s Cortex XSOAR on our blog.
New Chinese Botnet
We recently observed some botnet samples which we were unable to find existing identification for online. The family appears to be targeting users in China specifically, with a range of functionality covering aspects of a backdoor, stealer and remote access trojan.
On deeper inspection it would appear that the family is likely related to or based on the old Nitol family, another China-based malware family which has been around since at least 2012. However it is clearly more than just a simple clone/fork of the original, as we were able to identify a number of key differences and improvements in this new family:
- Nitol is designed to run as a service, including checks for this early in execution. If it finds this is not the case then it will copy itself to the appropriate location, create the relevant registry keys and immediately relaunch itself as a service.. The new version does not include this requirement - although it can still be run as a service depending on the values of certain global variables - and is distributed as a standard DLL with a DLLMain entry point (where Nitol is a normal PE executable).
- The main logic of the new family is included in the DLL exports of a 2nd binary downloaded by the initial DLL. The DLLMain function of the original executable only performs this download and nothing else, where Nitol’s functionality is all included in the base function.
- The new Chinese family includes checks for a wide range of running processes as an evasion technique, including a function to kill every existing rundll32 process on the system.
- For example, if it detects
RavMonD.exeit will create a new file at\\\\.\\killmdxthat will kill/crash the process
- For example, if it detects
- The new variant includes keylogger capabilities missing in its predecessor
- Nitol only includes support for ~5 commands where the new version has some new additions to that. However it does still include the original functions, meaning that many public Yara rules are detecting the new samples as Nitol.
- The new version’s botnet capabilities have also been expanded with some additional HTTP requests evident in the codebase. These are likely related to known exploits and DDoS attacks but we haven’t yet explored these fully.
We have so far not come across any public family names for these new samples, so we have added detection as simply “Generic Chinese Botnet” while we wait for the community to give it a proper name.
Thanks to Twitter user @benkow_ for reporting the sample to us initially.
Analysis:
Indicators of Compromise:
| Indicator | Description |
|---|---|
| 53b9a0465f0f42c412ba90058ed129e7e6c4c97f724f537a7e03c9931c8bbc60 | Sample SHA256 |
"C:\Program Files (x86)\Microsoft Egkgcm\Wakkeos.exe" Win7 |
Command-line used to launch the final payload (in Windows 7) |
207.148.120.98:8555:Rskeik iwmiqsio |
Mutex created by Wakkeos.exe |
CyberGate RAT
CyberGate is an old malware family with CitizenLab reporting that it goes all the way back to 2008.
The RAT is written in Delphi and shares a fair bit of its code with Xtreme RAT, another family from around the same time period (having been first observed for sale on forums in 2010). It boasts a fairly extensive list of features, but nothing out of the ordinary for this class of malware. Besides providing full manual remote access it can automatically steal browser credentials, download and execute additional files, capture the screen, and run a keylogger.
We added support for the family back in December last year, but have revisited it this week to implement a full configuration extractor which is able to dump a large number of settings fields including file and registry paths, keylogger settings and FTP credentials (where relevant).
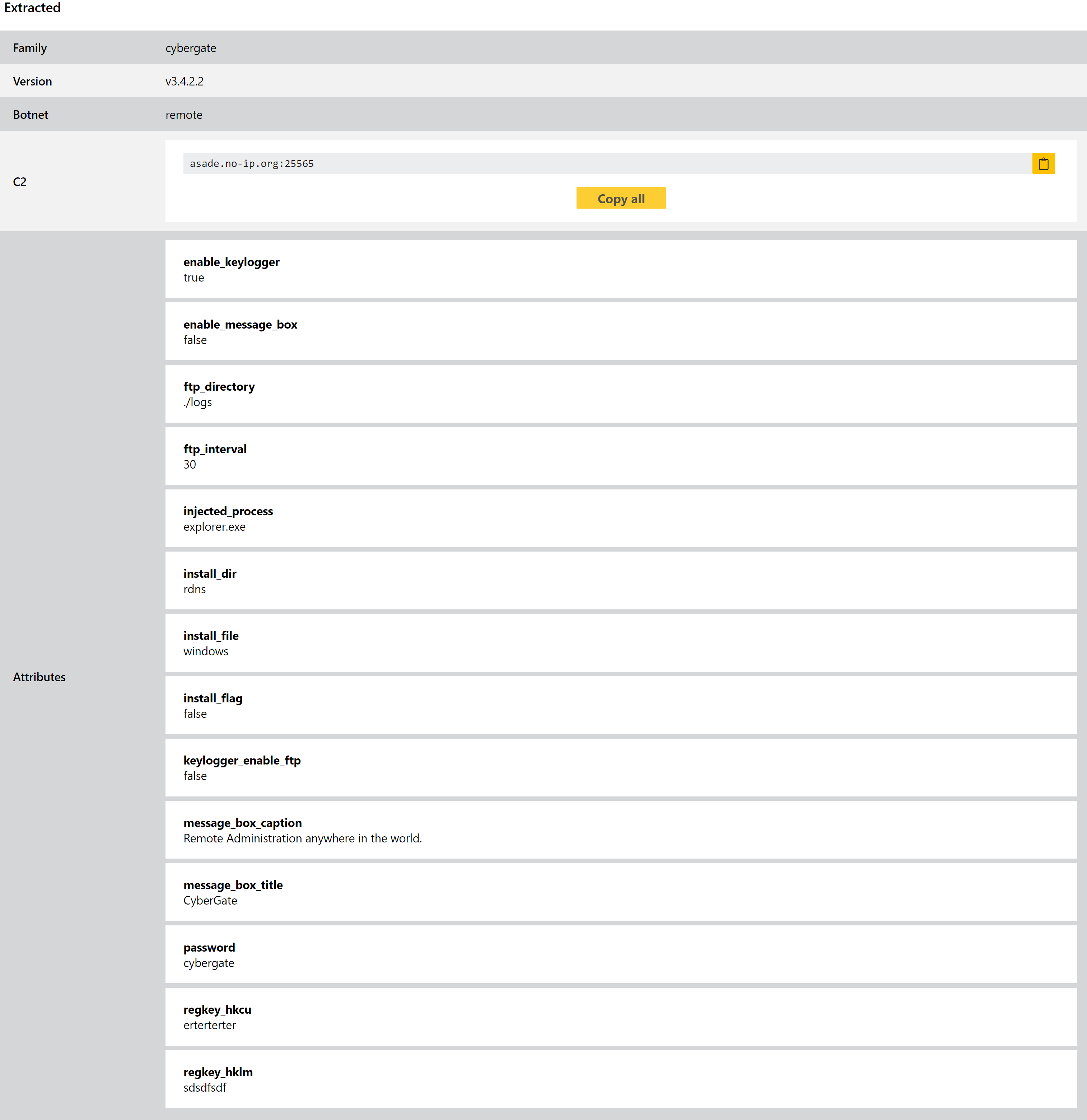
Analyses:
Indicators of Compromise:
| Indicator | Description |
|---|---|
| 2edc1d26a755fce3c36d97ee664473a24c09f653c38792118db34196cd638d06 | Sample SHA256 Hash |
| 9e0c6888bb6e17c927b7b52656b067562b7ef4607ca3963c8e13637235432c45 | Sample SHA256 Hash |
| 88ab0fb7aab828733d7fad8dd72ba73c7188803ed85c19d01a267ad7809cba44 | Sample SHA256 Hash |
| 7ef8a647eee5935219cea3f21cdc5a1fe28a53b177c6d3280e5ee8f2304b3e5c | Sample SHA256 Hash |
| asade[.]no-ip[.]org | C2 Domain |
| JOSE4[.]NO-IP[.]ORG | C2 Domain |
| pinguela[.]dnsd[.]me | C2 Domain |
| palotes12[.]chickenkiller[.]com | C2 Domain |
| matreto[.]system-ns[.]co | C2 Domain |
| narutao[.]duckdns[.]org | C2 Domain |
AvosLocker Ransomware
AvosLocker is a new ransomware which began operations around the end of June/start of July 2021. It was first reported on Twitter by @RakeshKrish12:
As with many modern ransomware families, the creators of AvosLocker have been actively recruiting affiliates through various forums rather than carrying out initial breaches themselves. Evidence suggests that they have already had multiple successes infecting companies.
As reported by MalwareBytes, the family does not attempt to be particularly stealthy during its infection as it is normally run manually by an operator with direct remote access to the compromised system. All encrypted files are renamed with a .avos file extension, and in each affected directory the malware creates a file called GET_YOUR_FILES_BACK.txt with the ransom instructions.
Check out the MalwareBytes blogpost for a very detailed breakdown of the family.
Analyses:
- 210719-85ryxybqhe(https://tria.ge/210719-85ryxybqhe)
- 210723-1f485ampc6(https://tria.ge/210723-1f485ampc6)
Indicators of Compromise:
| Indicator | Description |
|---|---|
| GET_YOUR_FILES_BACK.txt | Ransomnote file name |
| .avos | Encrypted file extension |
| ievah8eVki3Ho4oo | Mutex created (by both samples) |
| hxxp://avos2fuj6olp6x36[.]onion | Ransom payment URL |
| hxxp://avos53nnmi4u6amh[.]onion/ | Ransom payment URL |
MedusaLocker Ransomware
MedusaLocker was first seen in the wild during the 2nd half of September 2019 and quickly began to successfully infect victims. It is particularly potent due to a combination of robust methods to spread through a network and its persistence mechanisms.
SentinelOne reports that the family actively seeks to connect to networked resources, modifying the EnableLinkedConnections registry key as needed to ensure that mapped network drives are available for encryption. It also restarts the LanmanWorkstation service which handles network connections via SMB, ensuring maximum exposure for infection and lateral movement.
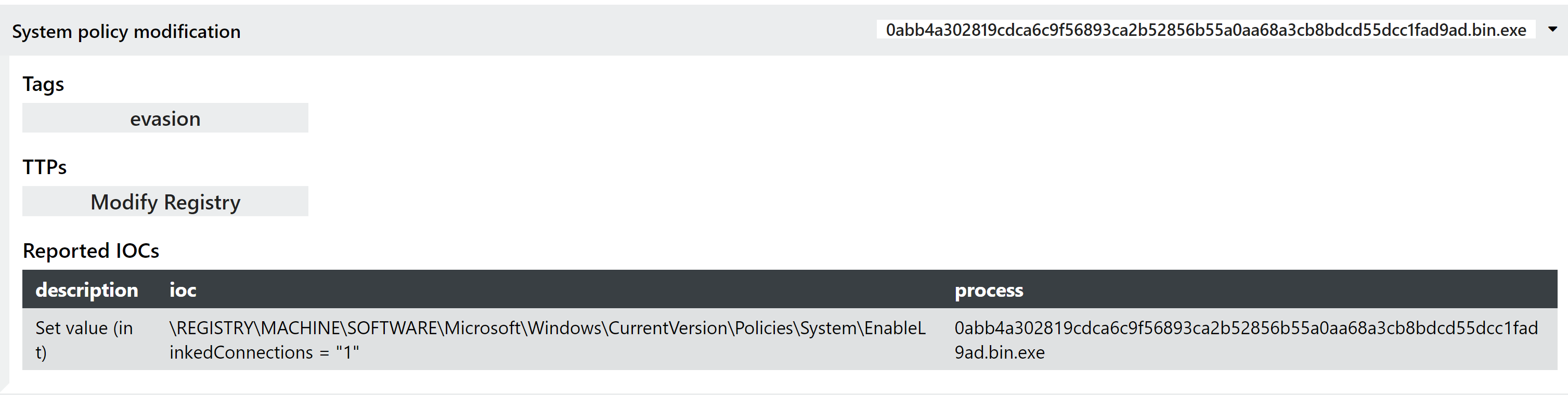
Over time the family has used a wide range of encrypted file extensions and ransom note file names/types. We have included below those we encountered during our investigation, but this list should not be considered complete for all versions and variants.
Analyses:
Indicators of Compromise:
| Indicator | Description |
|---|---|
| 0abb4a302819cdca6c9f56893ca2b52856b55a0aa68a3cb8bdcd55dcc1fad9ad | Sample SHA256 hash |
| 461f8a55ea2eecfcc26562326af4b56fbaf8e4957a4a6e0b75bec8ee90ace078 | Sample SHA256 hash |
| d595339cbbf415eca195eb3a0d9a8b6c9ff82a0cf36e4e867f5cef24503bb532 | Sample SHA256 hash |
| c5bef2a489740192a0b2c34cdc2fd954d0b8d5fabcbe0ecb8b78f9301e5a30a6 | Sample SHA256 hash |
| a25c0227728878c386ab6dba139976cb10e853dd3cd1eb3623f236ee8e1df212 | Sample SHA256 hash |
| !!!HOW_TO_DECRYPT!!!.mht | Ransomnote file name |
| HOW_TO_RECOVER_DATA.html | Ransomnote file name |
| Recovery_Instructions.html | Ransomnote file name |
| Recovery_Instructions.mht | Ransomnote file name |
| C:\Users\Admin\Desktop\README_LOCK.TXT | Ransomnote file name |
| C:\Users\Admin\AppData\Roaming\KEY.FILE | Dropped file |
| .gpay, .L54, .L16, .L47, .keversen, .Readinstruction, .grlock, .1btc | Observed encrypted file extensions |
| \REGISTRY\MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\EnableLinkedConnections = “1” | Registry write |
eCh0raix Ransomware
The eCh0raix family has been around since July 2019, gaining its name from a string observed within the early samples. It is a Linux-based ransomware specifically designed to target network-attached storage (NAS) devices, originally focussing on just those made by QNAP Systems Inc. and later expanding to also affect Synology products using a very similar method of infection.
The ransomware exploits vulnerabilities in the NAS devices to gain initial access. For example, PaloAlto recently reported that new variants were observed leveraging a CVE for QNAP devices (CVE-2021-28799) which had been covered in a security advisory from the manufacturers back in April this year.
The new version observed by PaloAlto also marks the first time that the family has targeted both QNAP and Synology devices with the same campaign, with previous iterations only being able to target one or the other at a time.
For a detailed writeup of the family check out PaloAlto’s writeup of the new variants from August this year or Anomali’s initial blogpost on the first versions seen in the wild.
Analyses:
Added Family Detection for VanillaRAT
VanillaRAT is yet another “for educational purposes only” piece of open-source malware which you can download freely from Github. The main project was ended in 2019 but as it’s open source anyone can feasibly create new variants without much effort.
The family is a fully featured RAT with the ability to gather signification information about an infected machine. According to the readme it includes features like:
- Process killer
- Microphone recording
- Clipboard interception
- Keylogging
- Remote shell access
- Privilege escalation techniques
We recently noticed a sample of the family being submitted to Triage, so we have taken a look at them and implemented relevant family detections to classify them correctly.
Analysis:
Indicators of Compromise:
| Indicator | Description |
|---|---|
| 92d129825bda8b18723026a90fcc19bed5614c7ba17b1a50e1ed91518fc93752 | Sample SHA256 hash |
