Welcome back to our weekly Triage Thursday blog series! We’ve just got a quick update for you this week but don’t worry - we’re working on some exciting new things in the background which we’ll be able to share in the coming weeks.
Meanwhile in today’s update news:
- Added Oski configuration extractor
- Updated IcedID family signatures
- Added detection for DarkTrack RAT
- Tweaked detection for Darkside ransomware
As always, if you come across any shortfalls with our detections please do send us feedback. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Added Oski configuration extractor
Oski is an info-stealer which first appeared at the end of 2019, being sold to users through underground forums. The family includes standard stealer techniques like harvesting credentials from web browsers, email clients and FTP software; but also includes Man-in-the-Brower functionality to steal data in real time.
The malware is generally well made, including:
- Basic anti-analysis/anti-VM techniques
- Support for credential theft from over 30 browsers including different methods for those based on Chromium, Mozilla, Opera and Internet Explorer
- Theft of a wide range of different cryptocurrency wallets
- A downloader module to install additional malware via Oski
A detailed breakdown of an Oski sample can be found on the CyberArk blog here.
Triage has supported basic family identification for Oski for some time, but this week we have implemented a configuration extractor to expand on the existing information. This dumps out the C2 address from the sample itself, making it easily accessible in the report for further tracking.
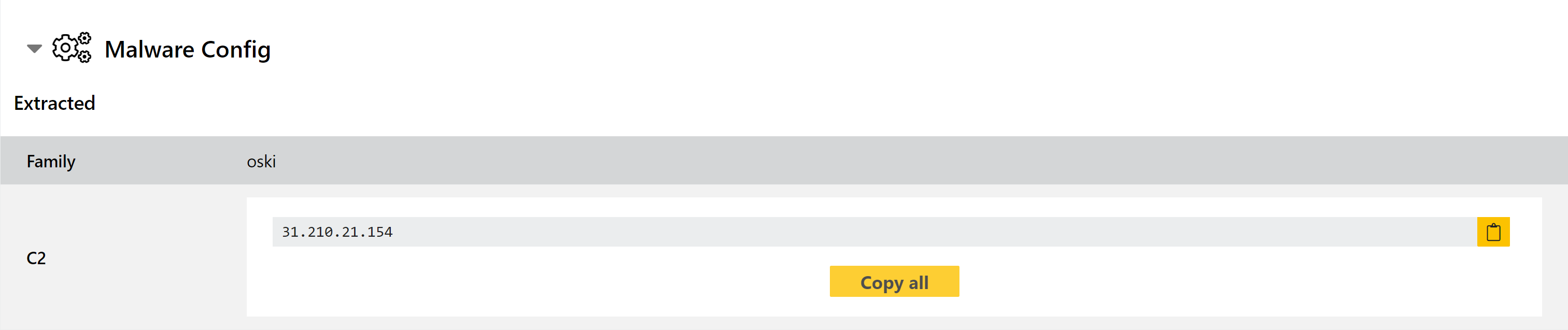
We are reprocessing all Oski samples on Triage, but some samples can be found below for reference.
Analyses:
Updated IcedID family signatures
After our tweak to the IcedID config extractor last week, it makes another appearance in our Triage Thursday blog today for a minor update to our general family signatures. These exist as fallbacks in case the extractor doesn’t work on a new variant, and this tweak more reliably covers recently observed samples.
Analysis:
Added detection for DarkTrack RAT
DarkTrack is a newcomer to Triage this week, with the addition of our first behavioural rules to identify the family.
This RAT has been around for some time, but we had noticed a number of samples submitted to Triage over recent months so decided to add a family tag for it. The family first popped up back in 2015, being advertised through a Facebook page apparently maintained by the creator as a communication channel with users. This page now appears to be inactive, and the latest versions of the family - dubbed DarkTrack Alien - is now sold through a forum for sharing cracked/malicious software.
The RAT boasts a wide range of functionality which provide full remote control of a victim machine, with many automated processes for various surveillance and management actions.
Analyses:
- 210504-51ky586x52
- 210429-dkr5gbkwg2
- 210407-w56yryyfhe
- 210328-gaxxf121gn
- 210228-j63dn4zxnj
- 210228-gnq4r12rle
- 210228-gg2156g8fe
Tweaked detection for Darkside ransomware
We added detection for Darkside, along with a few other relatively minor ransomware families, back in August last year. However a sample recently came to our attention which wasn’t being detected, so we have reviewed the signatures and made some small tweaks which should make the family more reliable (as well as properly extracting the ransomnote).
More information on the family can be found in this BleepingComputer article from last year.
Analysis:
