Welcome back to our Triage Thursday update blog series. We have a long list of new updates to introduce today which have been deployed recently. Last week’s post was dedicated to the new custom Yara feature, so we also have a few of the more minor things to cover that were deployed alongside.
- Improved URL search functionality
- Updated AgentTesla detections and extractor
- Added support for SOAP network protocol
- Updated Buer extractor
- Updated ransomnote parsing to catch Ryuk note variant
- Configuration extractor for PLEAD Linux-based backdoor
- Embedded network IoCs into report Overview for easy reference
- URLs extracted from PDFs, Office documents, etc. now displayed directly in report Overview
- Improved Yara support in Android analyses
- Added extraction of URLs from JNLP droppers
- Added extraction of URLs from .docx files using WebSettings to fetch payloads
- Added family detection for RemoteUtilitiesRAT (RuRAT)
- Added family detection for Sarbloh ransomware targeting users in India
- Added family detection for ServHelper backdoor
- Added family detection for TriumphLoader
- Added family detection for WebMonitor RAT
- Updated detection for Quasar RAT
- Added family detection for FickerStealer
Read on below for more details on some of the more significant updates of the week. As usual, if you have any feedback on Triage or particular samples please do get in touch! You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Improved URL Search Functionality
We’ve been receiving some feedback about the Search feature added back in October last year, and based on this we have made some tweaks which should make it easier to find analyses based on URL IoCs.
Originally only URLs extracted during analysis (e.g. from a configuration extractor) were searchable. We have now added support for also matching against URLs submitted to Triage, such as phishing URLs or download links.
We have also implemented a domain search feature, which will return all analyses containing URLs referencing the specified domain. This is helpful in finding related samples as URL searches only return exact matches. As with URLs, domains are also matched against all relevant data and will return both analyses that were initially submitted as URLs and those which reference them in network traffic. For example, to return all analyses which contain Google Drive links:
Updated AgentTesla Detection and Configuration Extractor
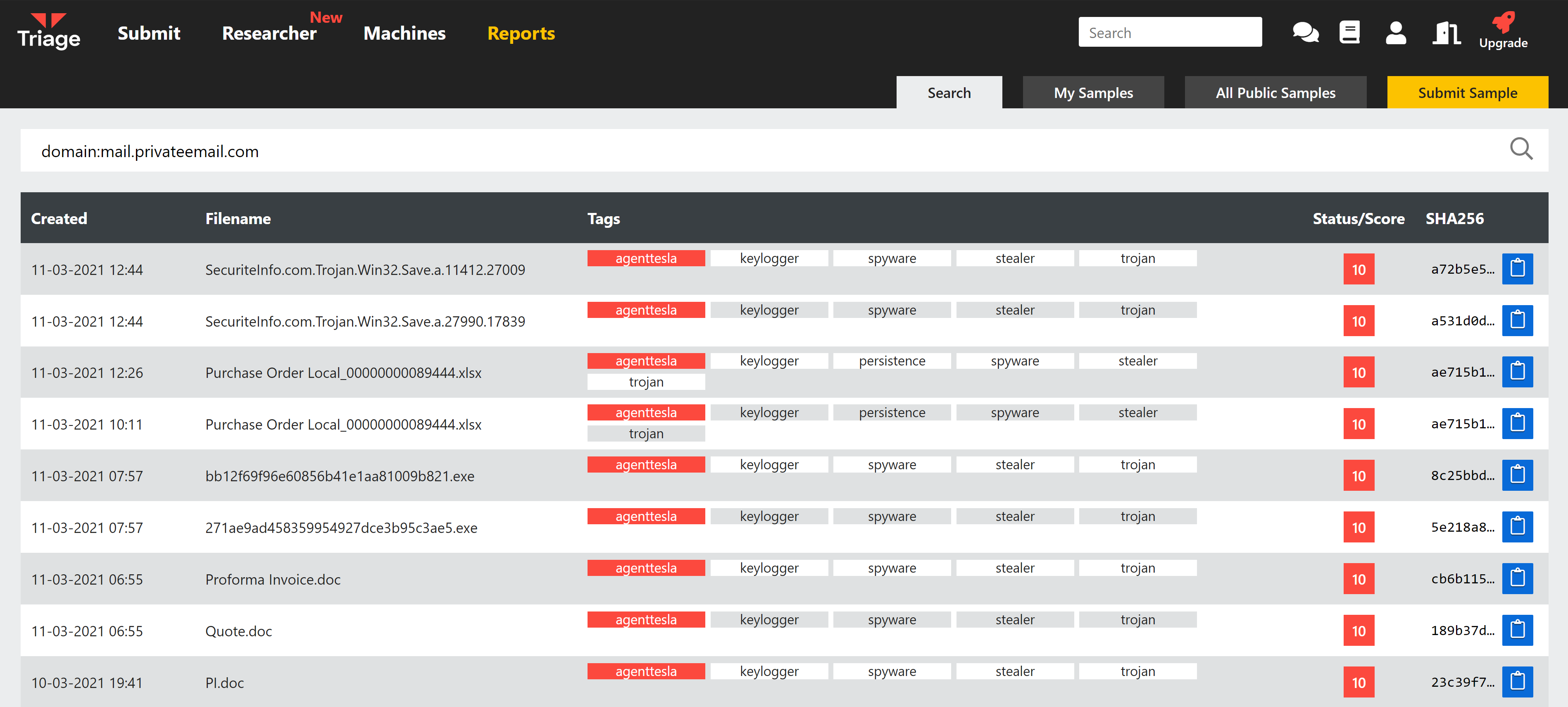
AgentTesla has been a consistent threat for years now, and continue to push new versions and features. It was one of the earliest families added to Triage’s detections, and recently we have been carrying out a thorough review of it to ensure our detection is accurate, especially taking into account the more recent versions 2 and 3.
We have reviewed a large set of samples from various points in AgentTesla’s development, and have completely reworked our signatures to provide better coverage while also reducing the chance for false-positives against other stealer families.
We have also implemented a new configuration extractor, which dumps the C2 information for the sample for easy access in the final report. The C2 infrastructure used depends on the version, but is generally done through some non-HTTP protocol or application. For example SMTP, FTP and Telegram are common C2 channels for the family.
After deploying the changes, we have also searched out existing AgentTesla analyses on the Triage server and reprocessed them - over 18,000 in all so far. As such all AgentTesla links should now be updated to reflect these changes.
Analyses:
Added Support for SOAP Network Protocol
We recently observed samples - mainly from the Redline stealer family - which were using SOAPAction HTTP header fields to obfuscate C2 communications.
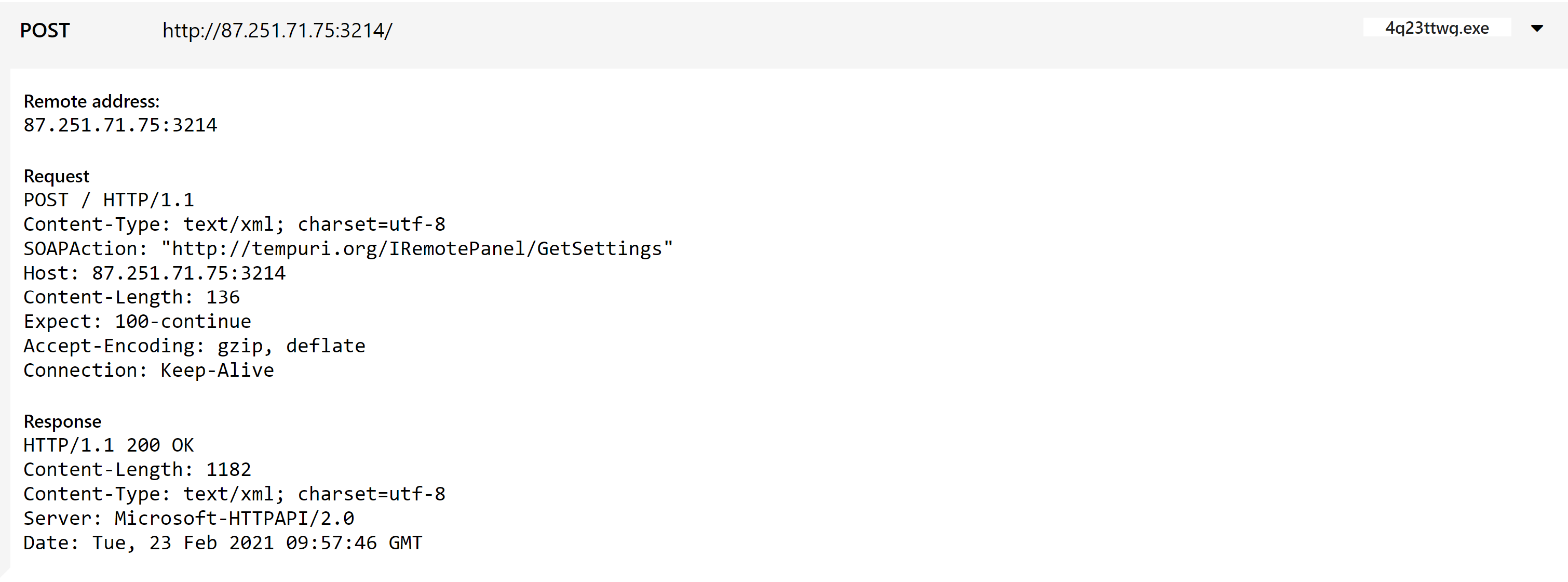
Triage’s network handling has now been updated to support parsing of these header fields, enabling us to use them in detections and/or extract the data they are used to transmit. This has enabled us to better support the Redline stealer family, and will find use elsewhere in future.
Analysis:
Updated Buer Extractor
Buer Loader is another recurring feature in our update blogs. We introduced a configuration extractor for it back in February, and this week we have a tweak to handle a change we’ve seen in samples since then.
In early versions, the encryption key used by the loader was hardcoded, making extraction relatively simple. This is no longer the case, so we have had to update our strategy to take this into account.
Thanks to @r0ny_123 for bringing this sample to our attention.
Analysis:
Updated Ransomnote Parsing
We recently noticed a sample of Ryuk ransomware on Triage which, although was being correctly identified as Ryuk, was not extracting any ransomnote. We took a look and realised that the note was HTML and showed the actual ransom text within a Javascript alert() function rather than the HTML body. As such, it was not being handled correctly by our HTML ransomnote parser which ignored script sections.
We have added support for this type of note to our extractors, which will now also check script sections and include parts which appear to be relevant in the ransomnote output.
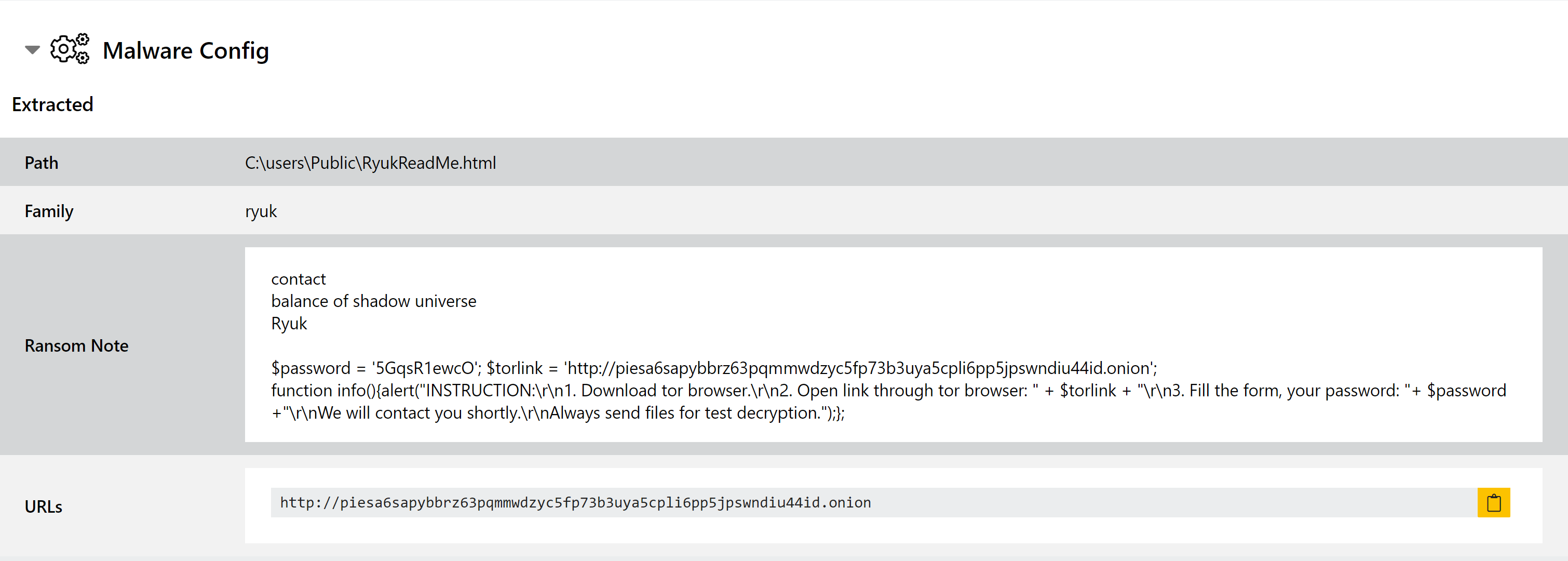
If you come across any incorrect or unexpected output from the ransomnote extractors please feel free to report it to us. We’re always looking to expand coverage.
Analysis:
Configuration Extractor for PLEAD Linux-based Malware
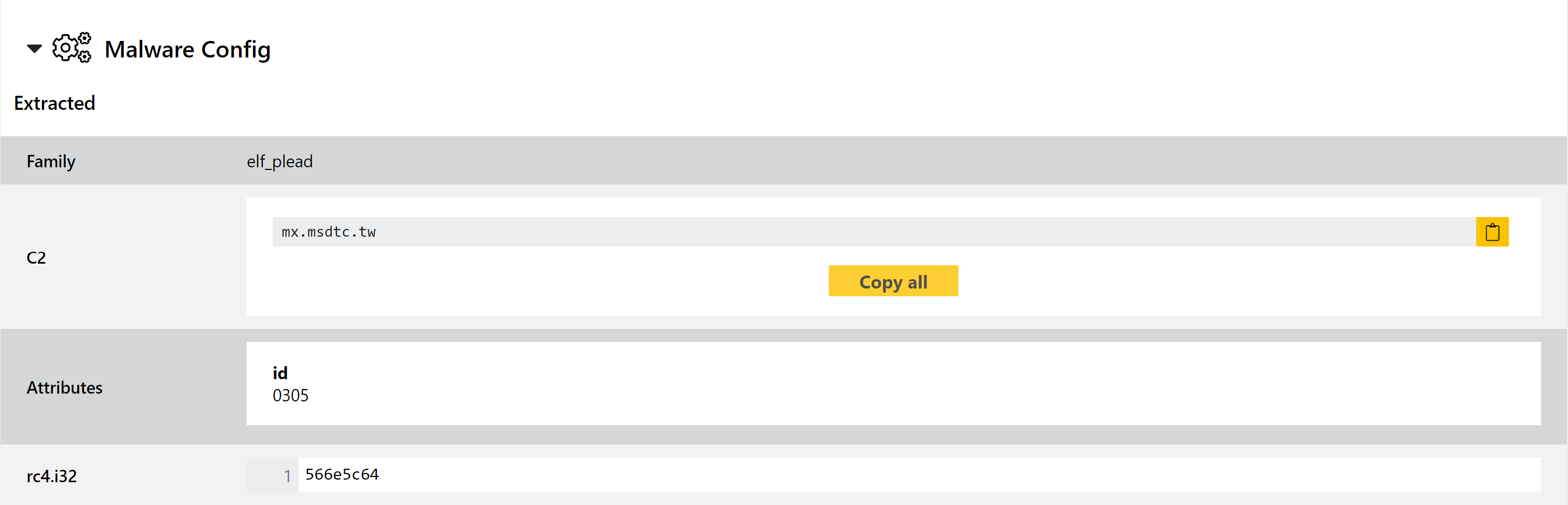
We are still working away on improving our support for analysis on non-Windows platforms, and this week have published our first configuration extractor for Linux malware! Triage now has an extractor for the ELF_PLEAD family, a backdoor which is generally associated with the BlackTech APT group.
Analyses:
