We’re a bit late this week, but welcome to our Triage Thursday: Friday Edition update blogpost! Our main feature this week is the Beta release of our new Knowledge Base, intended as a central source for information on malware families, campaigns and threat groups observed in Triage submissions.
We also have a few family updates to cover as usual:
- Update to Qakbot configuration extractor
- Updated DCRat detection
- Added support for WarzoneRAT variant
- Updated Gozi RM3 extractor
- New SnakeKeylogger configuration extractor
Read on below for more on the Knowledge Base!
Triage Knowledge Base
The Knowledge Base is something we have been planning in the background for some time now, and we are pleased to finally be able to make an early version of it available. At this stage it consists of only a few articles, but over the coming weeks and months we will be improving and adding to these.
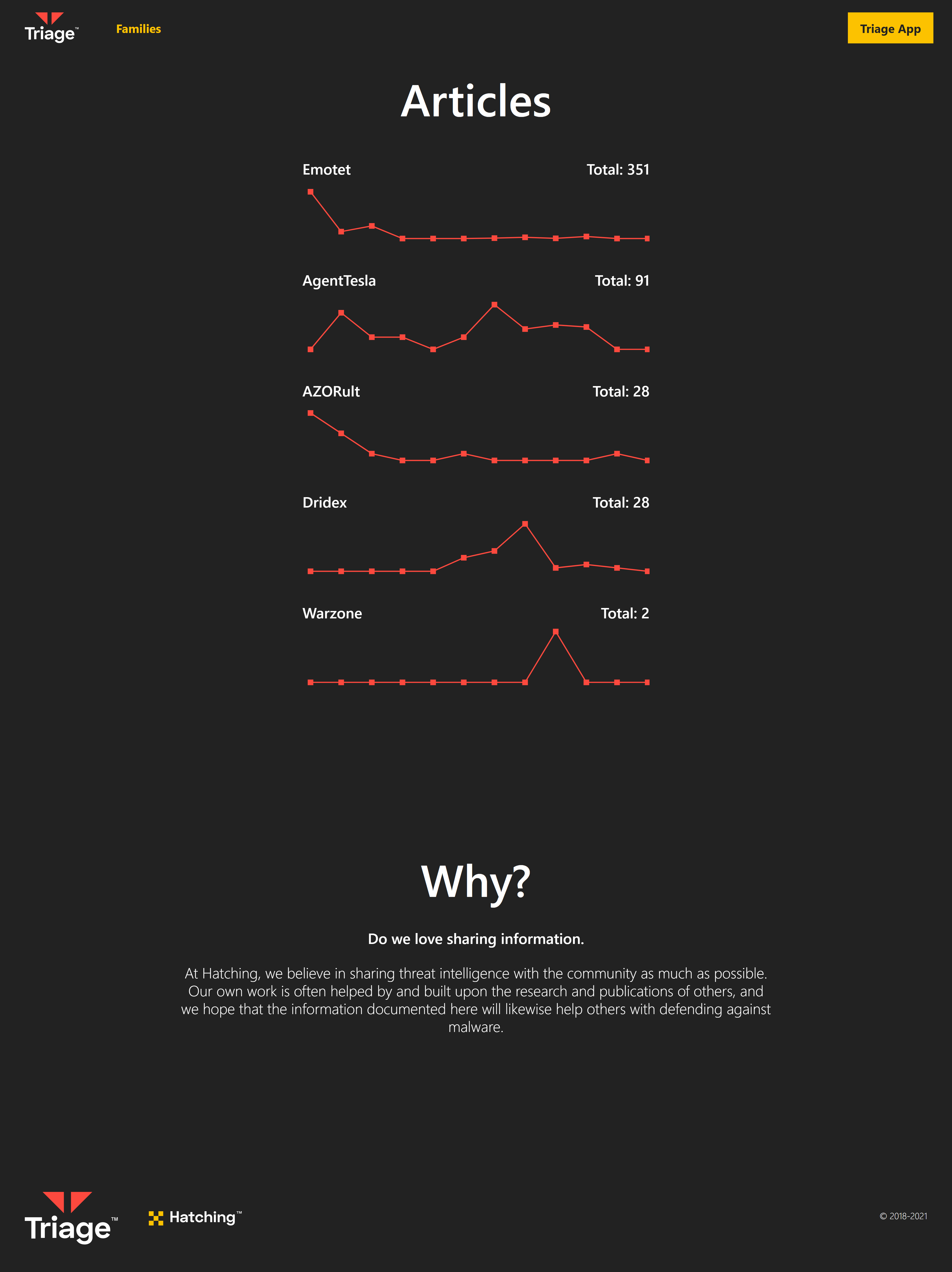
We hope that you find this useful in tracking and understanding threats as they develop over time. We plan to roll out new articles as often as we can, focusing on the most common current families. As usual though we are open to feedback if you have any particular suggestions or requests for topics to cover.
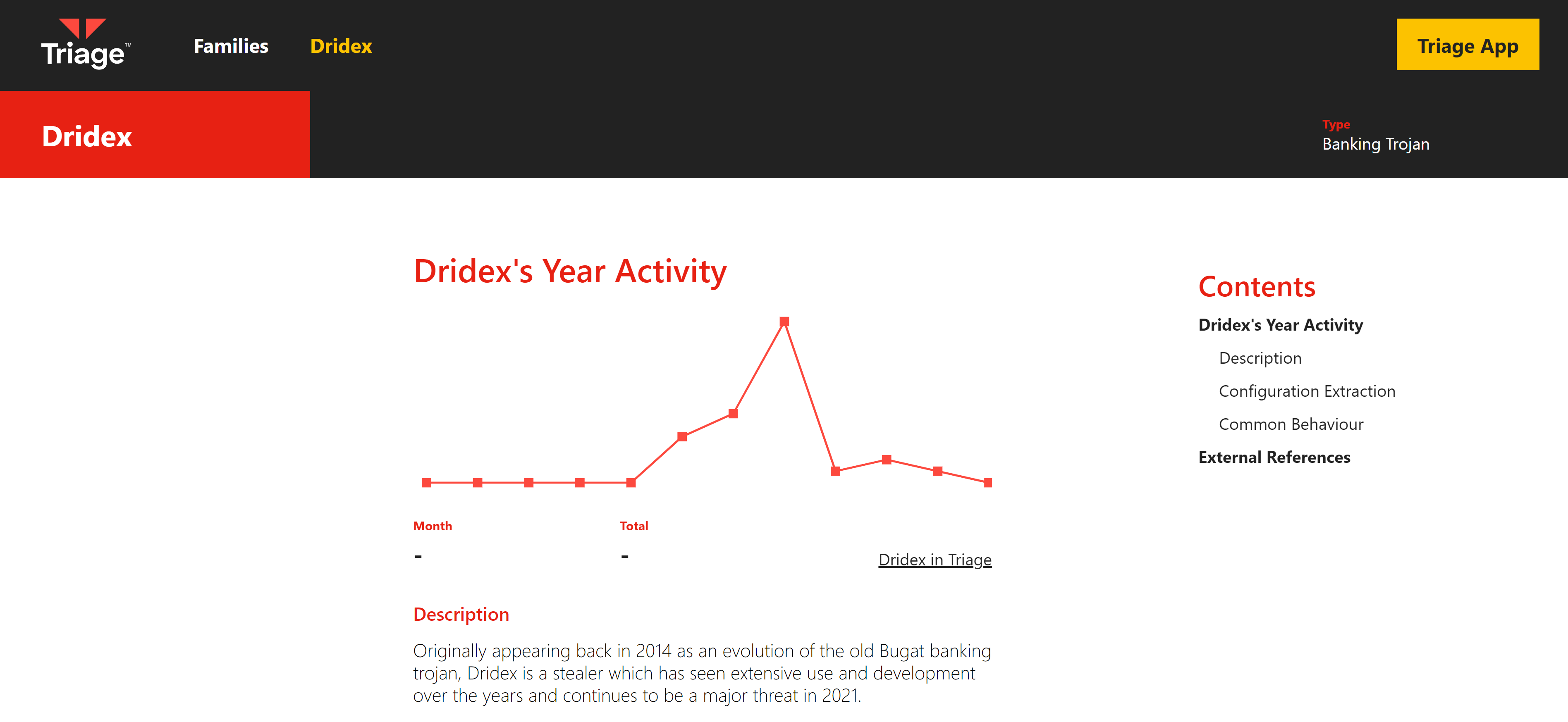
As well as documenting general information about families, campaigns and threat groups which has been gathered through Triage analyses, the Knowledge Base will also provide additional information from external sources. This includes an overview of Mitre ATT&CK TTPs in use by the family; details of the data dumped by Triage’s configuration extractors; tips for getting the most out of behavioural analysis of tricky or unusual samples; and more!
You can currently find initial articles for:
In the rest of this blogpost we’ll take a look at the main family updates which have been deployed this week. If you would like to reach out to us about anything covered here or with general questions and feedback you can find us through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Updated Qakbot Configuration Extractor
We recently observed some Qakbot analyses which were not successfully extracting the configurations. We investigated the issue and found that a change to a field of the config was letting it get past our trigger.
We’ve deployed an update and reprocessed relevant samples so that they display correctly.
Analyses:
Updated DCRat Signatures
DarkCrystal RAT, or DCRat, was first reported in late 2019. It provides an extensive set of remote administration functions, triggered by specific commands received from the C2 server. These range from file transfer, keylogging, and data theft to opening and closing the CD drive or interacting with the Windows speech synthesizer. In addition to the builtin commands it can also run shell commands and pipe the output to the remote C2 server.
A detailed analysis of the family can be found in FireEye’s report from May 2020, in which they breakdown the samples and all supported commands.
Triage has had behavioural detection in place for some time but we recently noticed some updated versions that weren’t triggering the signatures. We have reviewed samples and deployed an update to support them.
Analyses:
Added Support for WarzoneRAT Turbo Variant
Exactly 1 month ago we deployed a new configuration extractor for WarzoneRAT. It’s featuring again this week with a new variant, referred to in internal strings as WarzoneTURBO, which was evading our detection. We have updated our rules to support this version of the family and have reprocessed relevant analyses.
Analyses:
Updated Gozi RM3 Extraction
This week includes another small tweak to our support for the RM3 variant of the Gozi family. Our configuration extractor dumps the encryption key, but previously we had been dumping it as it is stored in the binary (i.e. encrypted) rather than the plaintext version. This is now updated and the value you see in the UI is the raw, unencrypted RSA public key.
Thanks to @xorsthingsv2 for bringing this to our attention.
Analyses:
New SnakeKeylogger Configuration Extractor
We implemented behavioural detection for SnakeKeylogger back in January and since then we have been seeing quite a number of samples appearing in Triage. As such this week we’ve taken another look at it and have implemented a configuration extractor to dump out the C2 settings for easy access.
Analyses:
