Welcome back to another week of our Triage Thursday update blogposts! We’ve got several new updates and tweaks to introduce - some of them you may have seen go live earlier in the week as we felt it was important to get them into your hands as soon as possible. However we’ll be going over them in a bit more detail below.
In this week’s changes:
- Added family detection and configuration extraction for SquirrelWaffle family
- Updated configuration extractor for Raccoon
- Updated Qakbot handling
- Added new configuration extractor for Webmonitor RAT
- Added new family detection for Numando LATAM banking trojan
As always, a huge thank you to all those who send us feedback and suggestions - as a small team your comments are invaluable in helping us keep on top of an ever-changing malware landscape. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
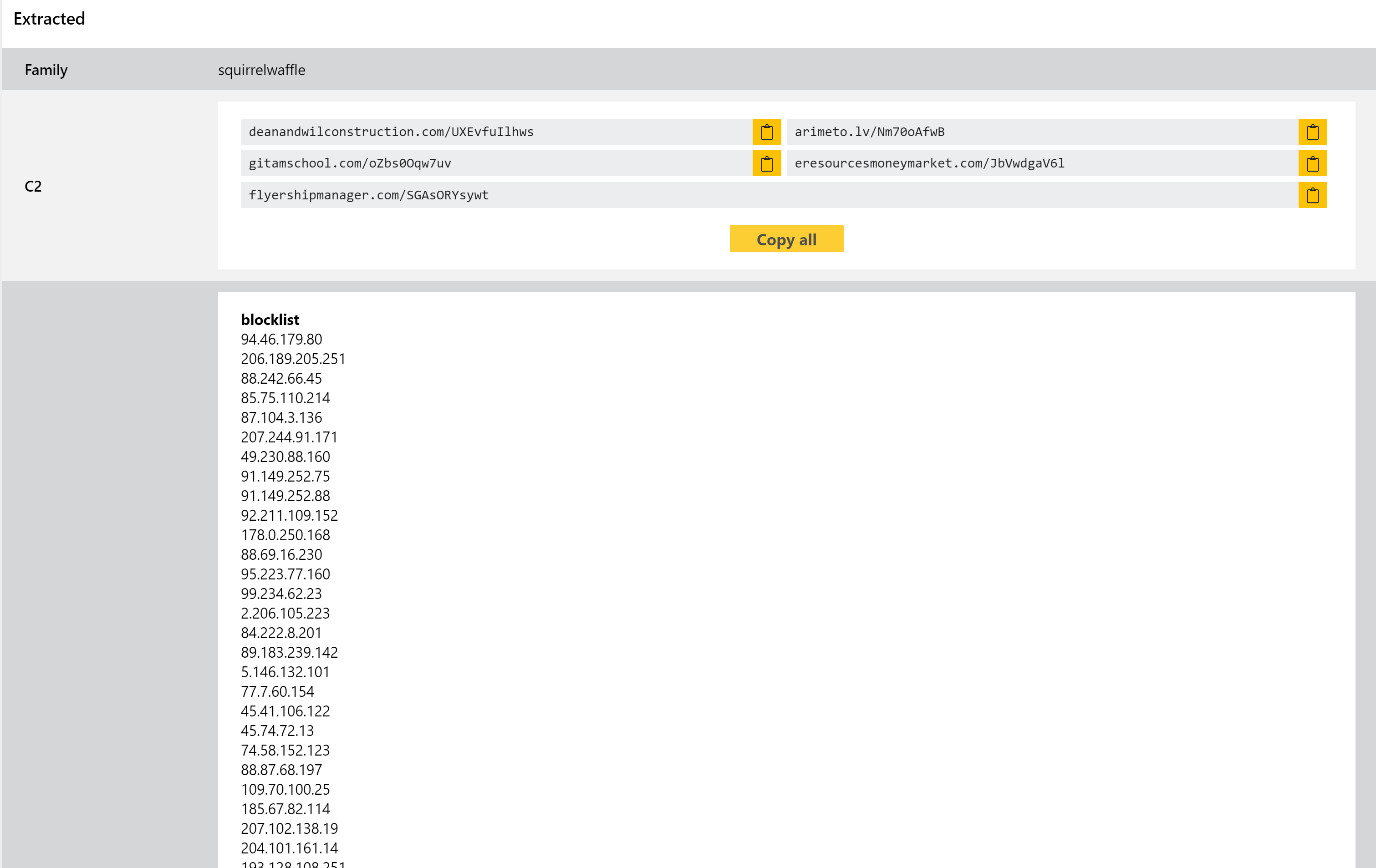
SquirrelWaffle Configuration Extractor
SquirrelWaffle is a new loader observed in the wild delivering mainly CobaltStrike payloads. First publicly reported by @ffforward on September 13th, it is being widely distributed by the TR botnet which has previously been known for running campaigns distributing Qakbot, CobaltStrike and IcedID.
So far the family is distributed via malicious Office documents, generally leveraging AutoOpen functionality, cscript.exe and VBS scripts to fetch and install the loader ready to deliver its own payloads - a more detailed breakdown of this infection process can be found in Security Soup’s writeup here. A 2nd approach has also been observed making use of Excel 4 macros, an old version of VBA support which has long since been replaced but still lingers in most Office products for backwards compatibility (more details can be found here)
SquirrelWaffle itself is a binary executable file which also includes an encrypted configuration defining C2 information for the campaign. Alongside the standard URLs/domains to be used to fetch further instructions and payloads, it also includes an extensive IP blocklist which appears to target various analysis platforms in an attempt to prevent automated detection. Indeed, the list includes our own IP ranges used for the public Triage servers (although you can easily bypass this by using the Tor Routing network option at submission).
In order to reliably classify the family and extract all available information, we have implemented general detections for it as well as a brand new configuration extractor which can dump the data mentioned above. As a new family we’ll of course also be keeping an eye on developments in the coming days and weeks to see if we need to make any tweaks as the samples mature.
Analyses:
Raccoon Updates
Raccoon is a fairly standard infostealer which was first reported in the wild in April 2019. Although relatively simple in its implementation and functionality compared to many of its competitors, it has proved to be popular with threat actors due to its low cost and high reliability. It has been used very widely since it released and remains active in 2021, regularly being among the most common submissions to Triage.
In terms of functionality it mostly limits itself to just harvesting credentials stored by local web browsers and stealing any cryptocurrency wallets available on the victim machine. It is most often distributed via phishing emails leveraging malicious Office documents for initial infection.
We’ve had to make some updates in the past as the family has released new versions, and we again noticed some slipping by our configuration extractor recently. We have now reviewed these and updated our detection accordingly.
Analyses:
New Qakbot Variant
Qakbot likely needs no introduction, but if you’re not familiar with the family it is a powerful infostealer/trojan which has been in use in various forms since around 2009. It has been repurposed for a few different roles over the years, including a banking trojan attacking Active Directory servers and a stint as a ransomware dropper.
Triage has long supported both behavioural detection and configuration extraction for the Qakbot family, but as an active and advanced threat it regularly requires minor tweaks to keep our signatures up to date. We recently observed another new variant which was having some issues, so we have made the required changes and reprocessed a few of the available samples.
Analyses:
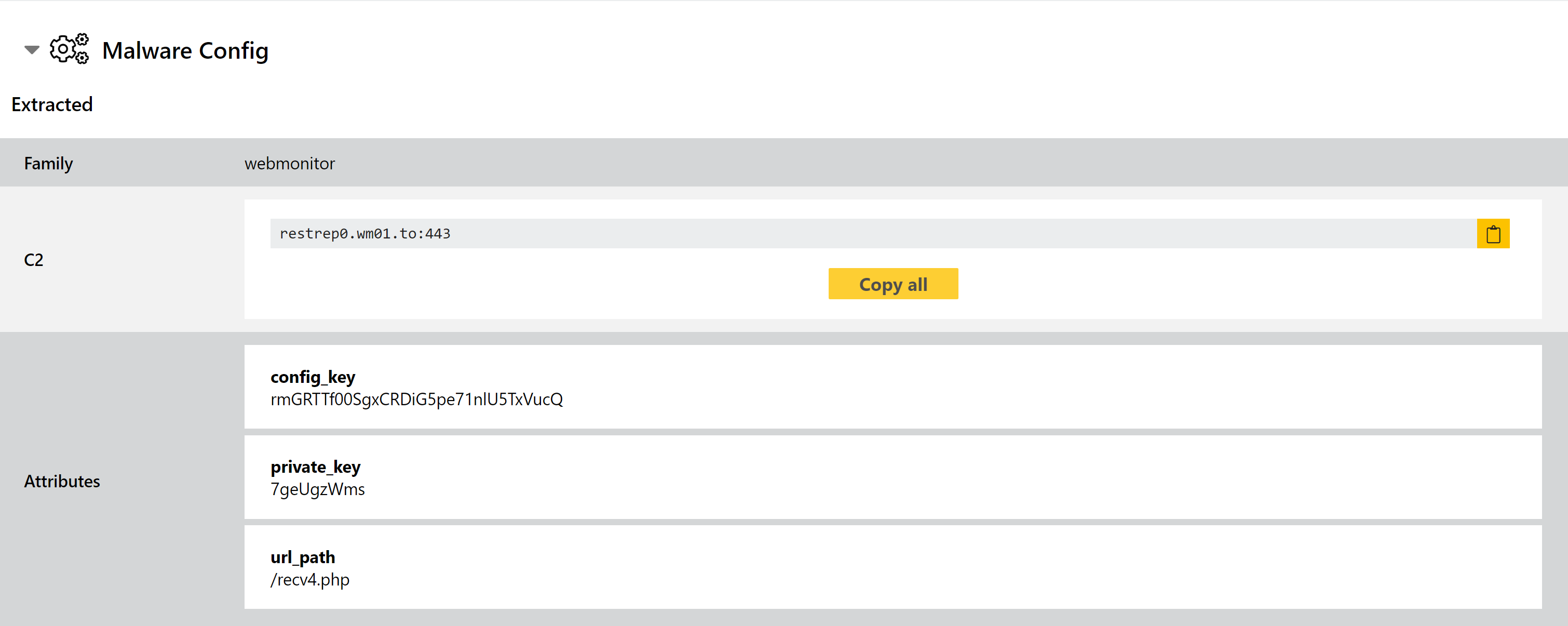
Webmonitor Configuration Extractor
WebMonitor is another piece of malware which can be bought online as a legitimate remote administration tool. Published by a Swedish company called RevCode, they claim it is only for legal usage in network administration but fail to account for why that requires it to include built-in functions like dumping live memory; extracting passwords from email software and web browsers; stealing saved Wi-Fi credentials; or intercepting clipboard contents - all of which are advertised on the software’s web page.
Interestingly, Krebsonsecurity wrote in 2019 that the owner of Revcode appeared to be an individual who had previously pleaded guilty to the co-creation of the Blackshades RAT in 2015.
The family itself is very full-featured and well put together, but although it sees regular usage it has never achieved the success of some of its competitors. We added initial detection for it back in March 2021, and as we have continued to see samples since then we have this week added a new configuration extractor to augment the available data.
Example of the features advertised through WebMonitor's website
We have included a couple of examples below, and you can find additional ones using Search: family:webmonitor
Analyses:
Numando Banker
Numando is a recent banking trojan which mainly targets the Latin American region - though it has also been observed infecting some targets in Spain as well. ESET report that it is operated by a threat actor with a history of using similar threats to target the same region, such as Mekotio and Grandoreiro. Numando has not achieved the same level of success as these families however, affecting a much smaller number of victims.
Samples are written in Delphi and leverage fake overlays to trick users into entering sensitive information. In addition to automated stealer functionality, the family also acts as a backdoor providing manual interaction with the infected machine such as screenshot capture, process termination, machine shutdown/reboot, and simulated mouse and keyboard activity. Some versions are fully self-contained, whereas others include an additional DLL which holds resources such as the images used when generating the fake overlays.
We have reviewed some initial samples and implemented static detection to classify the family correctly. Some examples are available below.
Analyses:
