Welcome to this week’s Triage Thursday blogpost. In this weekly series we go over updates made in the last week to provide an overview of newly available features and family support.
In this post, we’ll give a brief overview of the following changes:
- Android Analysis
- New configuration extractors for Formbook and DiamondFox
- Improved configuration extractor for ZLoader
- Family classification for VenomRat samples
Android Analysis
This week saw the release of the first version of our new Android analysis sandbox, allowing full dynamic analysis of Android binaries on Triage.
- Interact in realtime with Android through our UI.
- Detect suspicious use of the Android APIs.
- Unpack dynamically loaded .dex files.
- Capture dropped payloads as well as monitor accesses to the filesystem.
- Analyze network traffic.
- Monitor application related processes and services.
For more information on this and a case study of the Anubis Android banking trojan, check out the full blogpost published earlier this week.
Example Android Analyses:
Configuration Extractors
We’re always updating and expanding our support for config extraction during analysis, and this week we have improved handling of a few families.
Formbook
This new extractor dumps all URLs for the sample and distinguishes between the real C2 and the fake domains included as decoys. These are all clearly reported after the analysis completes:
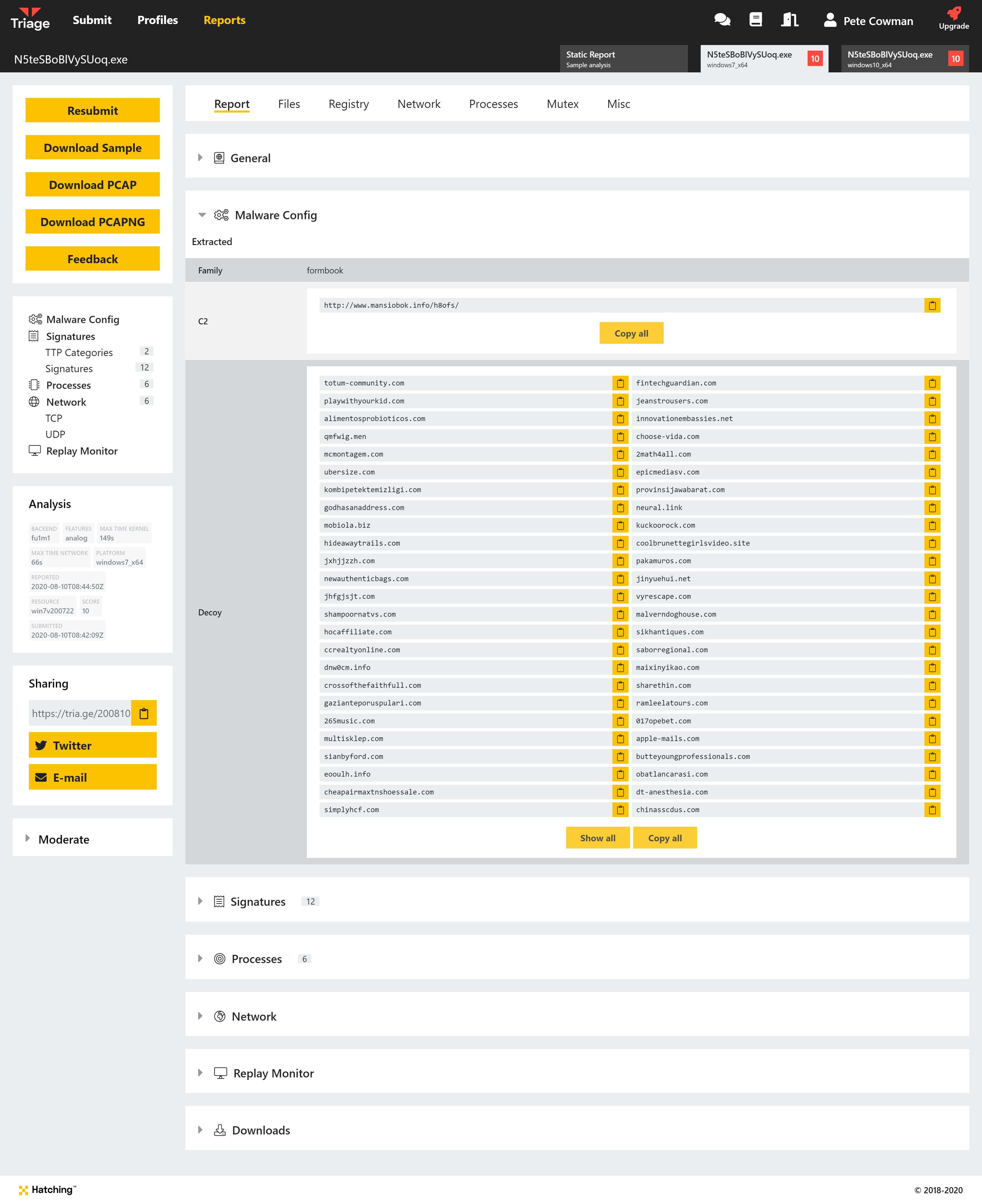
Example Formbook Analyses:
DiamondFox
A private researcher, @fr3dhk, passed us some DiamondFox Kettu samples while researching the family for their recent blogpost (which you can find here). To go along with the post, we released an automated config extractor for Triage which dumps C2 URLs and the XOR key used for communications.
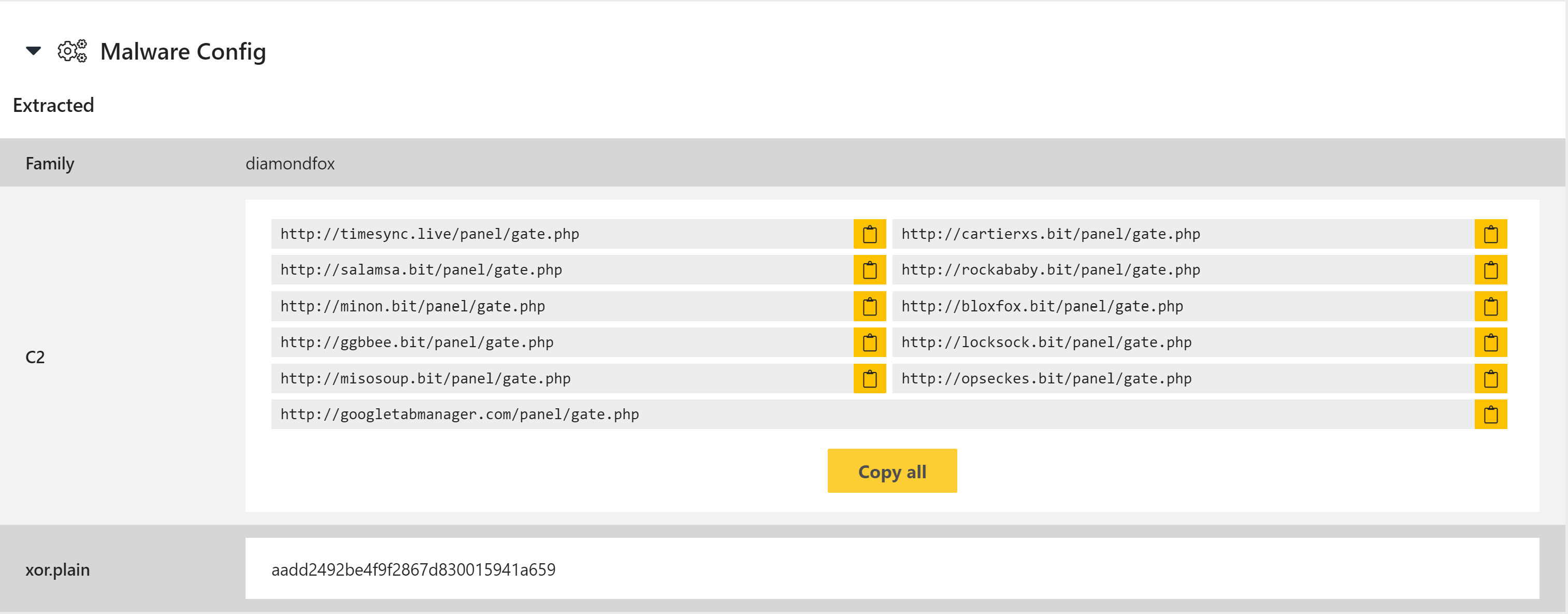
Example DiamondFox Kettu Analysis:
ZLoader
The ZLoader extractor has also received a small update, and now extracts the RSA public key when possible as well as the RC4 key used for C2 communications. As before it also extracts the botnet ID and all C2 URLs.
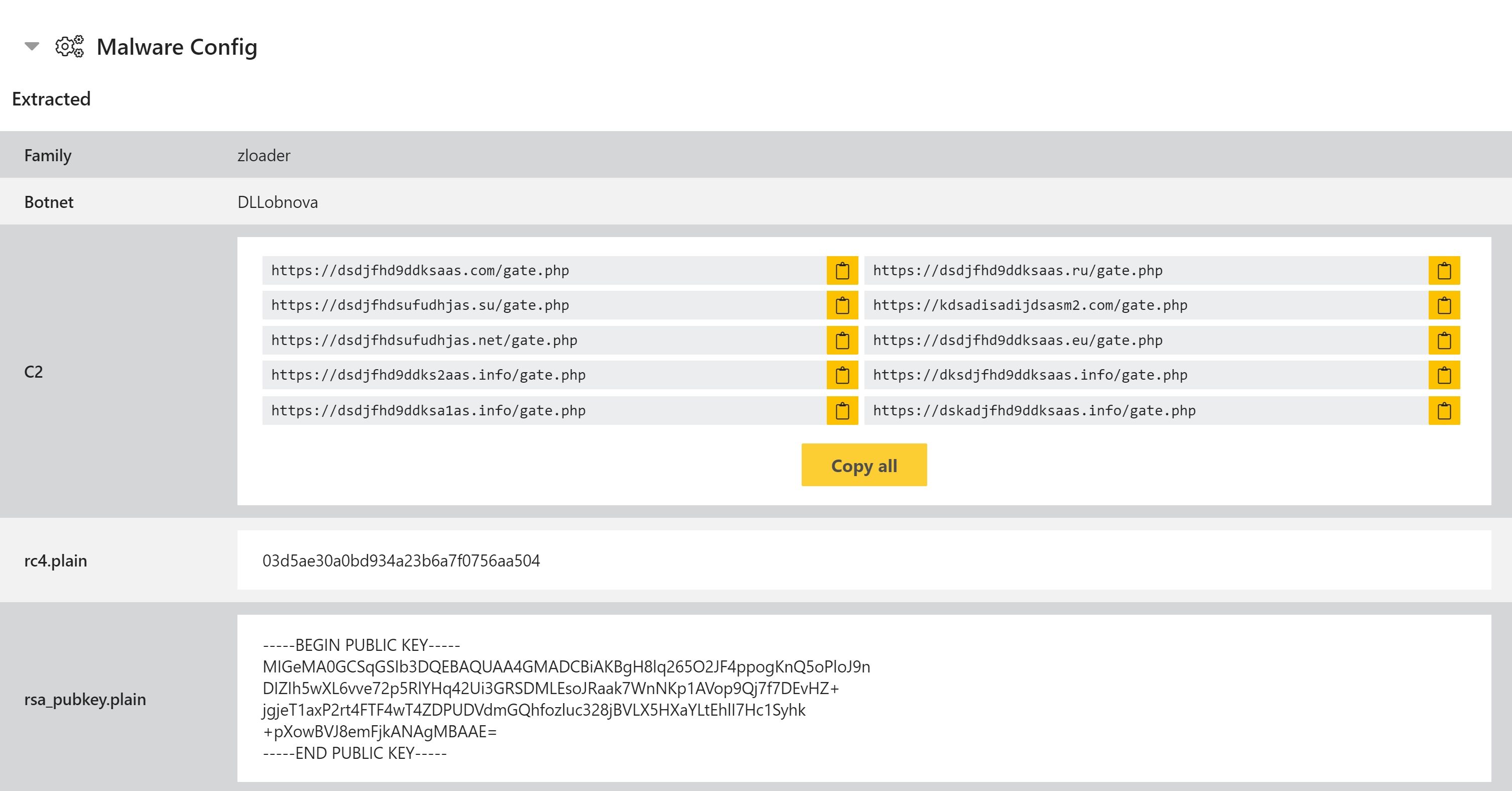
Updated ZLoader Analysis:
