Welcome to the latest entry in our Triage Thursday blog series! We weren’t able to publish a post last week so we have a bit to cover today, with changes to a range of families and some under-the-hood improvements to our macOS handling.
Contents:
- macOS improvements
- Added new configuration extractor for Socelars
- Updated detections for version 3 of Blackmatter ransomware
- Added new detection for Chaos ransomware
- New family signatures for Unicorn stealer and Blustealer
- Added classification for TA505 families FlawedGrace RAT, MirrorBlast, and ReflectiveGnome
- Added signatures for ConnectBack Linux reverse shell
As usual, if you have any feedback on Triage or particular samples please do get in touch! You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
macOS Improvements
Support for macOS analysis is our most recent platform addition to Triage, having been made available in June this year. We still have a lot of things we want to add to bring it up to the same kind of standard as our Windows support, and this week we have taken a step along that path with a couple of nice additions which should help you get more out of your analyses.
This set of improvements is all about network processing and web browsers. The most significant change is that TLS/SSL sessions are now decrypted by Triage. This has long been supported for Windows but up until now was not possible on macOS. Triage is now able to dump the master key at generation, meaning that all HTTPS traffic can be parsed and analysed in plaintext. Also, like Windows, this is bundled into the PCAPNG file which is available for download on each analysis - open it in Wireshark 3.0 or later and you’ll have access to the plaintext traffic just as we do internally.
Related to this, besides the Safari default we have also added full support for Chrome and Firefox browsers within our macOS analyses.
Blackmatter Ransomware
Blackmatter has already appeared on this blog a couple of times recently, when we added initial detection for the family and again when we created a dedicated configuration extractor.
However a new version recently appeared - tagged as version 3 - which was slipping past our extractor due to some tweaks in its payload. We have now reviewed this and updated our signatures to handle it properly.
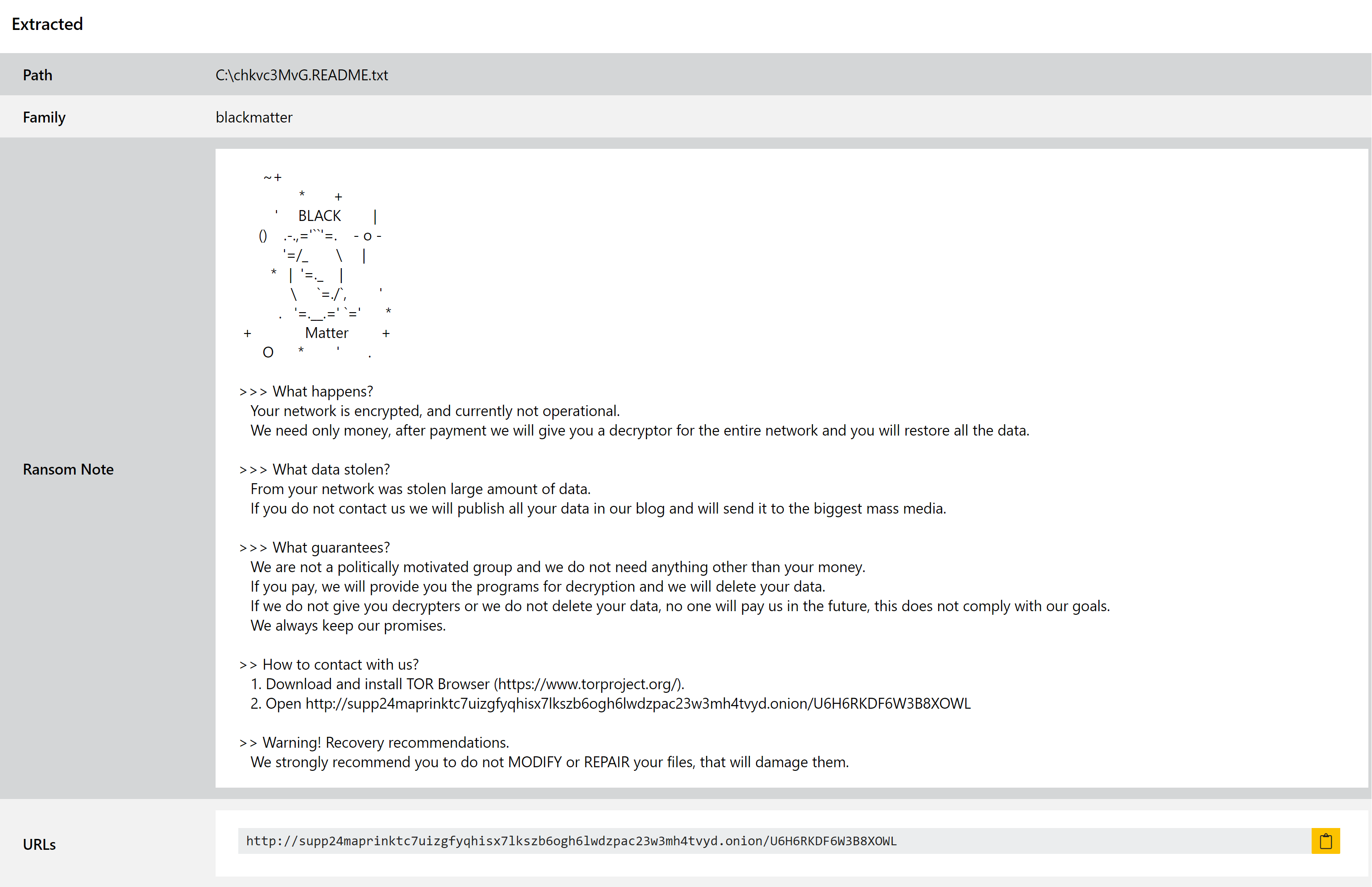
Of course, since this change was pushed internally it would appear that Blackmatter may be stepping back from the ransomware business. Researchers over at vx-underground reported yesterday that the developers of the malware have announced they are shutting down the operation, offering decryptors to affiliates to enable them to carry out ongoing extortion efforts on their own.
Whether or not this really is the end of the family only time will tell, but if new versions do pop up in future we’ll be sure to add support for those too.
Analyses:
Chaos Ransomware
The Chaos ransomware family is a slightly unusual case. Reported by TrendMicro to have first appeared in June 2021, its initial versions weren’t really a ransomware at all. Seemingly acting as a test for future improvements, the first couple of releases simply overwrote all affected files in a way that completely prevented any form of recovery. Although it did drop notes and make ransom demands in a way recognisable from any other campaigns, there would have been very little incentive for victims to pay up when there was no way for them to recover their files having done so.
Interestingly the first version also claimed to be a .NET port of the Ryuk family, although analysis suggests that it actually shares very little in terms of implementation.
However since release additional versions have been made available which do actually encrypt files. The family also now comes with a framework for building decryptors easily, suggesting that it is becoming more mature and nearing the point where it could actually be used in infections.
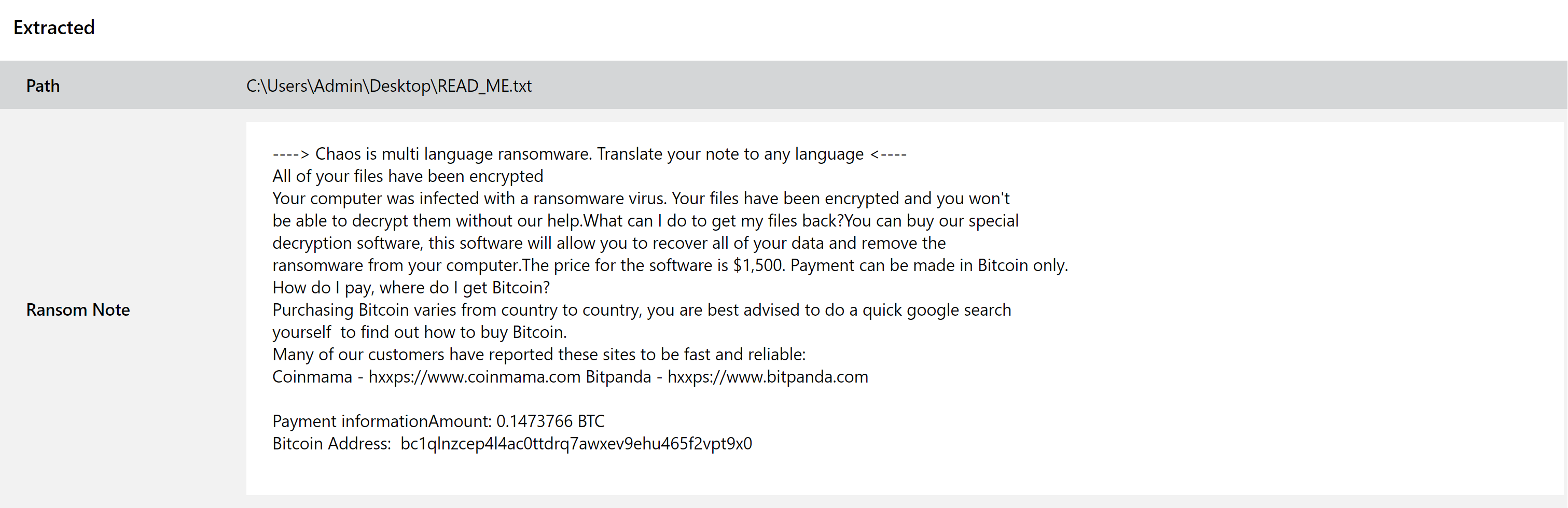
We have taken a look at available samples and implemented detections as needed. Examples are provided below.
Analyses:
Unicorn Stealer
Unicorn stealer is a small group of samples which were identified by Proofpoint in their Emerging Threats Suricata ruleset. The family takes its name from a log file written to a hardcoded path with the name Unicorn.txt.
Not much information is available online for this one, but according to our own analysis it appears to be a fairly straightforward stealer. As might be expected, it extracts information stored by local web browsers like Chrome and Firefox and checks for the presence of cryptocurrency wallets at common file paths. Based on the configuration, this includes a good range of browsers including the likes of Brave, Firefox, Chrome and Opera plus several spinoffs from those like Waterfox. In terms of cryptocurrency we observed it targeting Bitcoin, Electrum, Exodus, Coinomi, Jaxx and Atomic wallet files.
Slightly more unusually it also includes the ability to hook browser DLLs in order to steal information live during use, as well as some form of web injection technique to man-in-the-middle active sessions.
Finally, it also appears to leverage the Tor network for its C2 communications, proxying its traffic through a number of endpoints around the world.
Analysis:
TA505 Families
TA505 is one of the most prolific and technically advanced APTs out there in the wild. Involved in both financial crime and seemingly state-sponsored activity, the group has built up a formidable toolkit over time which often makes use of ground-breaking techniques to bypass defences and evade detection.
This week we have been reviewing a new attack chain in use by the gang, including new and/or updated versions of a few different families. We’ll cover them all together here as it can be rather hard to separate them out without a lot of repetition.
First up is MirrorBlast, a loader which forms the core of many current campaigns being operated by the group. It generally falls in the middle of their execution chain, not dropping the end payload itself but another stage of loaders. Based on research by Proofpoint it normally leads on to our second family for today, ReflectiveGnome.
ReflectiveGnome is, as the name suggests, a shellcode loader. This forms almost the final part of the ‘standard’ TA505 infection process, deploying and executing shellcode which then starts the final payload. It is quite simple in terms of functionality, performing its highly specialised role and nothing more.
In the recent campaigns reported by Proofpoint in their blogpost, this final loader has been deploying a new variant of the FlawedGrace RAT. This family was first observed by Proofpoint back in 2017, but has seen a bit of a revival with this new variant. The main changes of note are based around stealth and evasion, with the addition of string encryption, obfuscated API calls, and a change to the storage and handling of the configuration data.
We have reviewed a number of samples which have come to our attention through Triage, and have deployed some initial detections. There are still some improvements to come in future, but this should provide coverage for a considerable number of the samples.
Analyses:
BluStealer
BluStealer is a relatively new family which first popped up around the middle of 2021. Reported on Twitter by @cocaman it was initially called a310Logger and mostly dismissed as just one of the many low-quality RATs that come and go on underground forums.
However it seems to have stuck around and has recently been reported on again, this time identified as BluStealer. Its main targets are the theft of data stored by web browsers and cryptocurrency wallets, with quite an extensive list of paths defined for the various software packages from the common Chrome, Firefox and Brave all the way down to the unusual 7Star, Chedot and Cent browsers.
Exfiltration for the family occurs via SMTP connection and/or the Telegram Bot API.
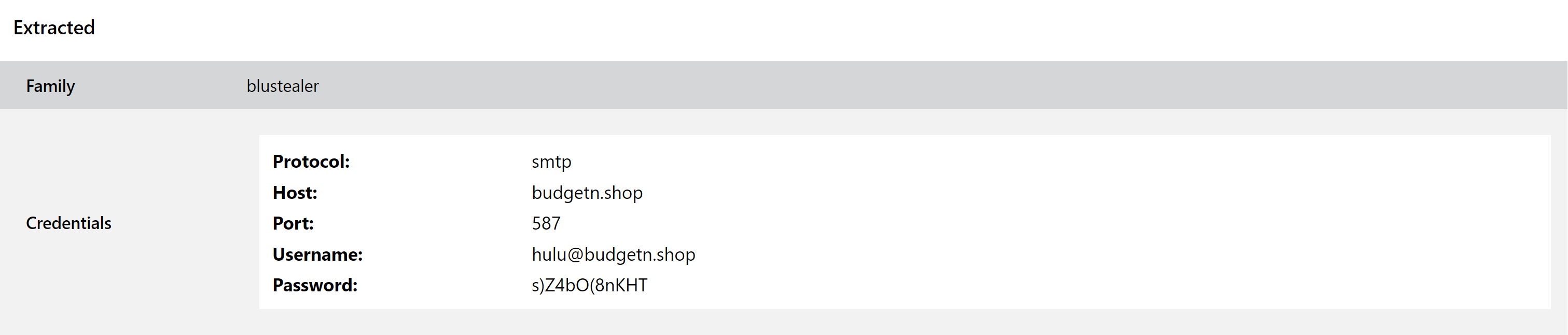
We have taken a look at a large number of samples for the family, and have implemented both standard signatures and a dedicated configuration extractor. This can dump out the C2 URL, and in the SMTP cases will also provide the details used for exfiltration including the host, port, username and password.
Analyses:
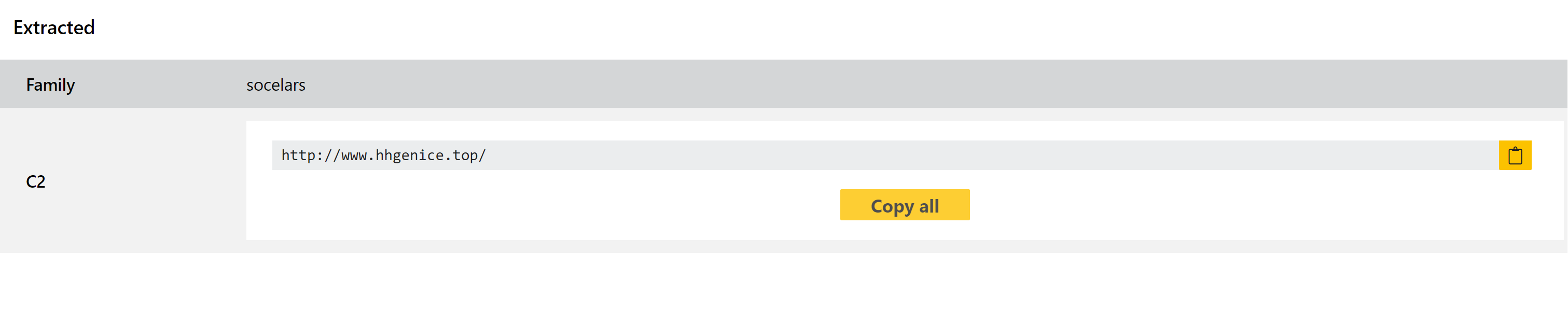
Socelars cfgextr
Socelars is a stealer family which has been around since at least late 2019. It is slightly unusual in its functionality, as it doesn’t target many of the standard data sources focused on by most other stealers. Rather than going after passwords and profile data stored on disk, Socelars is more interested in cookie data with a specific focus on Facebook and Amazon.
We added detection for the family in July this year, but have revisited it this week to add a dedicated extractor to augment the output. This dumps the full list of C2 IPs or domains which are hardcoded into the sample, to make it easy to pass these into additional tools etc.
Analyses:
ConnectBack Reverse Shell
The ConnectBack family is a fairly simple set of backdoors/reverse shells available for Linux. They include almost no in-built functionality, simply opening a remote connection to the attacker so that they have full access to and control of an infected system.
We have been noticing quite a few of these appearing in our public submissions, so decided it was time to implement some dedicated signatures for them. We have also developed a basic extractor which can dump the remote C2 IP from the payload.
Analyses:
