Welcome back to our Triage Thursday blog series, where we go over the week’s updates and changes on the platform.
This week is all about detection tweaks with some new and updated configuration extractors, and general family signatures for some older bots and RATs. Check out the full contents list:
- Updated detection and configuration extractor for Blackmatter ransomware
- New configuration extractor for DarkComet RAT
- Family detection for StealthWorker bot
- Added detection for SendSafe malware
- Added detection for macOS variant of XLoader
- Added additional rules for Mirai family and variants
- Updated Danabot detection
In other news we are still looking for a Go developer to join the Hatching team. If you’d like to be involved in the next steps of Triage’s journey - or know someone who might be - you can find the full job listing here. Feel free to reach out with any questions.
As usual if you have any comments, suggestions or other feedback about Triage feel free to get in touch with us. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
BlackMatter Ransomware
BlackMatter first appeared in July 2021 in the aftermath of the Colonial Pipeline attack in the USA. Following that incident some major ransomware families appear to be taking a step back and BlackMatter is attempting to fill the gap left behind.
The developers of BlackMatter claim to incorporate elements of the likes of Darkside, Lockbit and REvil/Sodinokibi but whether there is actually a significant overlap in the teams for these projects or if they are just attempting to use the names to gain attention is not currently clear.
We added detection for BlackMatter earlier in the month, but we are revisiting it this week with the addition of a full configuration extractor on top of the default ransom note handling. This covers both Windows and Linux variants of the family, and dumps out C2 information, version numbers, a botnet ID and the configured RSA public key for C2 communications.
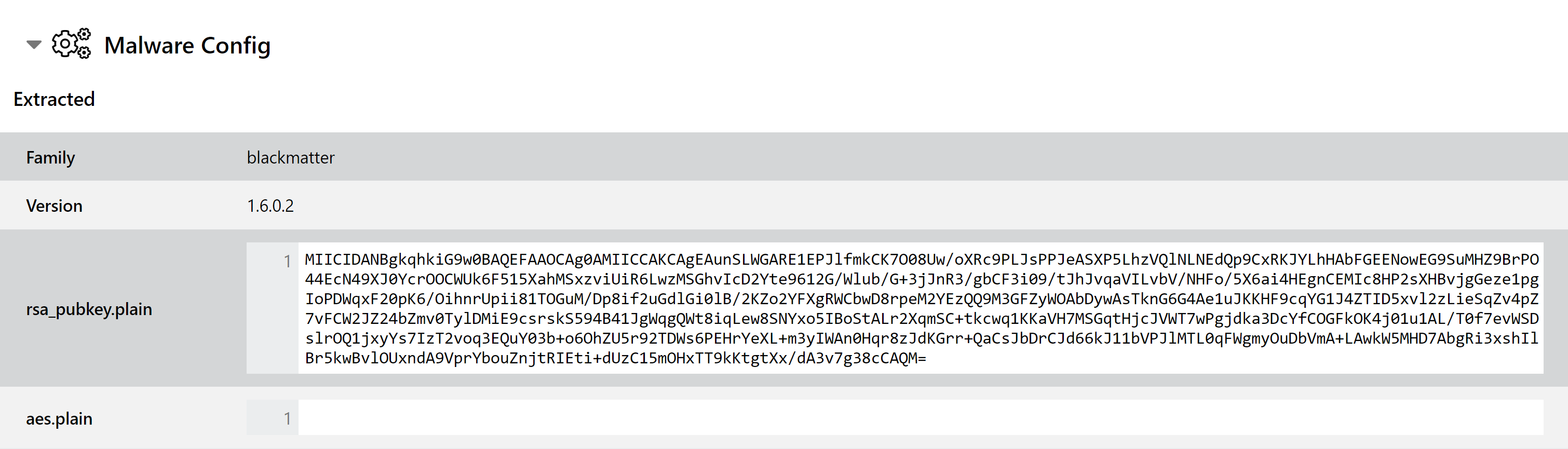
Analyses:
Indicators of Compromise:
| Indicator |
|---|
| hxxp://mojobiden[.]com/?vqnjhucsosfuvs=wlixpzuchrileu&xxsflqvvcvgdcbaaej=ktdunhgnwzhxqdzdlx&rdrkpk=xcqkxx&ngmxjegoobnfz=nrrgyndlucbmr |
DarkComet RAT
DarkComet has a fairly long history in the wild, first being developed back in 2008 as a supposedly legitimate remote administration tool. However after it came to light in 2011/2012 that the family was being used by the Syrian government to spy on dissidents and activists during the early days of the civil war the developer ended the project, apparently unwilling to see it used in this way (or to bear the potential consequences of this kind of use).
This burst of conscience was short-lived however, with the original creator returning in late 2012 with a new and improved version of DarkComet. Although he apparently made efforts to realign the software as a genuine remote administration tool, the functionality and capabilities still lent themselves well to malicious use, and indeed it has continued to see widespread use ever since.
In 2021 DarkComet is still a popular choice for attackers with low technical ability. Its professional user interface and easy setup makes it extremely accessible for anyone looking to run a malicious campaign.
Triage has long had signatures for DarkComet RAT but this week we have reviewed these as well as adding a new configuration extractor, able to pull out various bits of information like the install path, persistence registry key name, module settings etc.
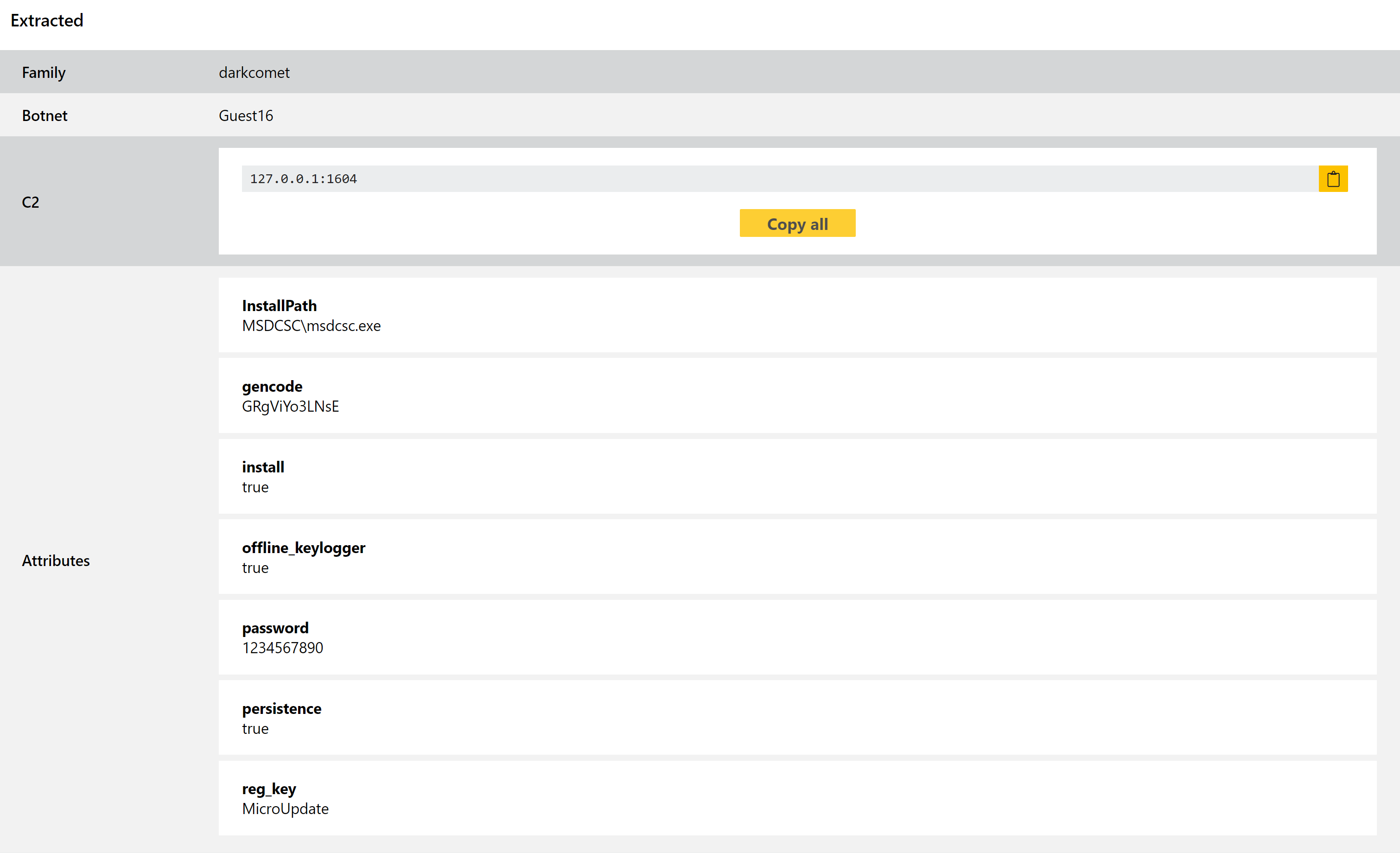
Analyses:
StealthWorker Bot
A couple of weeks ago we added detection for the eCh0raix ransomware, which targets NAS devices produced by QNAP and Synology. StealthWorker is another family which specifically targets Synology NAS devices, seeking to infect them and incorporate them into a botnet which can then be leveraged for a range of purposes.
The family itself began in early 2019 as a brute force toolkit targeting various ecommerce platforms commonly used in website design. Since then it has expanded to cover more platforms, devices and server types including the recent addition of Synology NAS devices.
We have taken a look at some samples available on Triage and created initial rules to detect the family. As usual, we’ll keep an eye on future submissions and if we spot any getting past our signatures then we’ll make changes as required.
Analyses:
SendSafe Botnet
SendSafe is perhaps the oldest malware family we’ve included in this blog so far, with initial versions going all the way back to 2002.
It is a fairly standard spambot, capable of distributing email spam or carrying out DDoS attacks using the network of infected machines. Its core functionality has really changed remarkably little in the nearly 2 decades since it appeared, and it is still seeing use alongside families like Hancitor. Based on findings by CERT Poland it is likely that the version currently in use was created sometime around 2016 as a reboot of the original malware, with a slight pivot to be a more automated spam bot than simply a manual spam toolkit.
Analysis:
XLoader macOS Variant
Back in December 2020 a new variant of Formbook appeared calling itself XLoader. Like the original family, XLoader is a fairly advanced infostealer which can include a number of anti-VM and anti-analysis techniques.
Formbook and the initial XLoader versions were specific to Windows systems, but recently the developers have branched out with a new version for macOS devices. We have examined a sample that was reported to us and extended our existing signatures to also support this variant. We will be deploying a configuration extractor for the macOS version in the next couple of weeks after some background work is in place to support it.
Analysis:
Indicators of Compromise:
| Indicator |
|---|
| hxxp://www[.]dutythrow[.]com/09rb/?GzZD-=O5eC9V+IVojJG6flBvKbN71kBBTBb7n/AHYvObDliNk8aHY/fp+4ebe0WjUTe50=&Fl9p=74Qlc |
| hxxp://www[.]thedoubletwelve[.]com/09rb/?GzZD-=GIvT/+9TB3vsnUciAHiIc8jOUJ1xZe7VzpTrx7NK9ttm/8E6WzPoOcznua9m9Mk=&Fl9p=74Qlc |
| hxxp://www[.]siderplan[.]com/09rb/?GzZD-=RBiF2b4g20Ou1ICz01vDQvr3oe1uRzoL6trCHGV5Cc8UwQuI08oSkFrhqlI42Zo=&Fl9p=74Qlc |
| hxxp://www[.]iregentos[.]info/09rb/?GzZD-=KB/hGxQILa9NChNKV0HkIMiUmhqlwDPOM0f+2bu5OzbpvkPK+TUML8DKgH4JU0M=&Fl9p=74Qlc |
Mirai Botnet
Mirai likely needs no introduction, but if you’re not familiar with the family it is a huge, sprawling mess of different variants and payloads which target a range of Linux-based IoT devices. It was first identified in 2016 and quickly gained notoriety for carrying out large scale, high profile attacks against large companies like Dyn and the news website KrebsonSecurity.
Devices infected by Mirai constantly scan the internet for vulnerable IoT devices, using a large list of known default login credentials to infect poorly configured hardware. Over the years numerous versions have popped up utilising various CVEs to target a particular subset of devices, such as Huawei or D-Link routers.
Once infected, devices are generally used for large scale DDoS attacks with the family wracking up some of the highest traffic volume attacks ever seen, such as the Dyn attack which reportedly passed a total traffic rate 1 Tbps.
The malware is open source and has been for some years, meaning that the code is available for anyone with coding knowledge to modify and redistribute. This has led to an incredibly confusing landscape of minor variants which it is very hard to comprehensively cover with signatures. Triage has long had support for a number of the major ones, but we’ve recently observed a couple of others which we did not support. We have improved our detections, and as usual if we spot any new ones we’ll update accordingly.
Analyses:
Danabot
Danabot is a banking trojan/stealer which has been in regular use since mid-2018. The malware is modular, with a range of functionality for browser injection/man-in-the-middle, network interception, theft of locally stored credentials, and full remote access support.
The family has seen a few changes since it released, with Proofpoint reporting a new version in early 2021 which included some additional anti-analysis methods.
We recently noticed a new version which was evading our configuration extractors, so we have taken a look and made the necessary changes to ensure that detection continues to work as expected.
Analyses:
